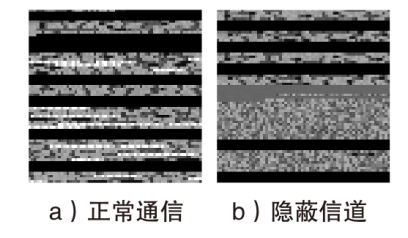
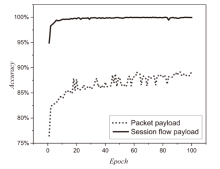
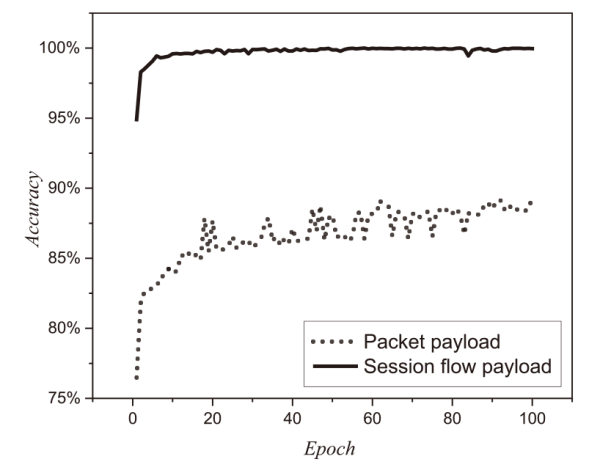
信息网络安全 ›› 2023, Vol. 23 ›› Issue (7): 53-63.doi: 10.3969/j.issn.1671-1122.2023.07.006
基于深度学习的HTTP负载隐蔽信道检测方法
- 1.四川大学网络空间安全学院,成都 610065
2.四川大学网络空间安全研究院,成都 610207
-
收稿日期:2023-03-30出版日期:2023-07-10发布日期:2023-07-14 -
通讯作者:陈兴蜀 chenxsh@scu.edu.cn -
作者简介:苑文昕(1997—),男,陕西,硕士研究生,主要研究方向为网络威胁检测|陈兴蜀(1968—),女,四川,教授,博士,主要研究方向为云计算、数据安全体系、威胁检测、开源情报分析|朱毅(1991—),男,四川,博士研究生,主要研究方向为网络行为与威胁识别|曾雪梅(1976—),女,四川,工程师,博士,主要研究方向为网络流量识别、网络行为分析、IPv6网络安全 -
基金资助:国家自然科学基金(U19A2081);中央高校基本科研业务费专项资金(SCU2021D048);四川大学工科特色团队项目(2020SCUNG129)
HTTP Payload Covert Channel Detection Method Based on Deep Learning
YUAN Wenxin1,2, CHEN Xingshu1,2( ), ZHU Yi1,2, ZENG Xuemei2
), ZHU Yi1,2, ZENG Xuemei2
- 1. School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
2. Cyber Science Research Institute, Sichuan University, Chengdu 610207, China
-
Received:2023-03-30Online:2023-07-10Published:2023-07-14
摘要:
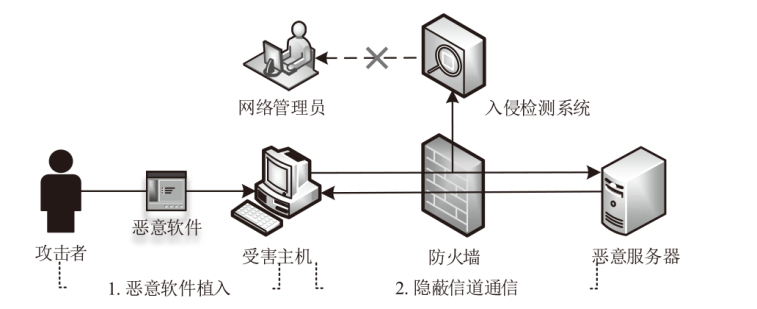
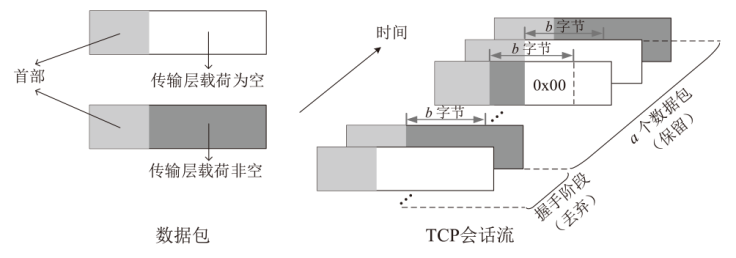
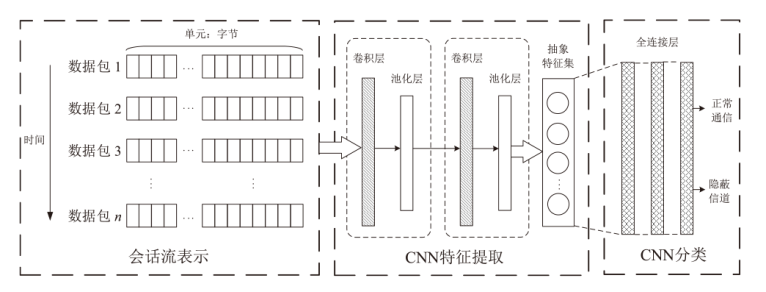
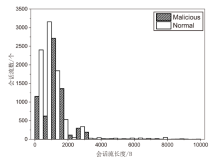
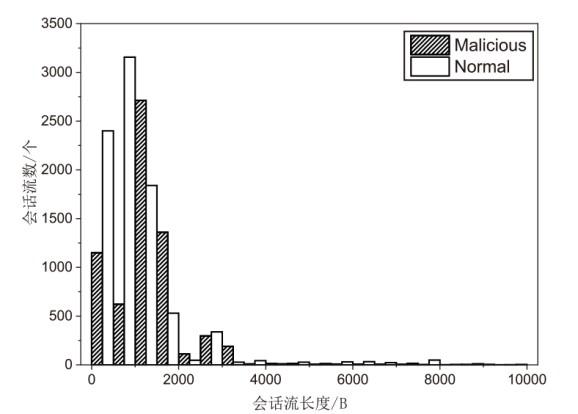
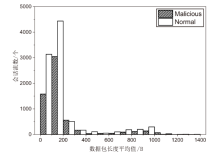
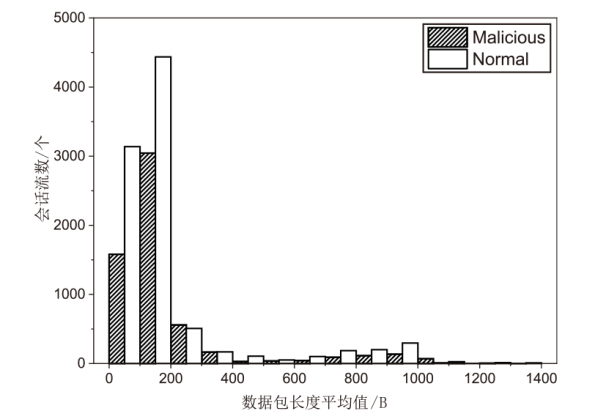
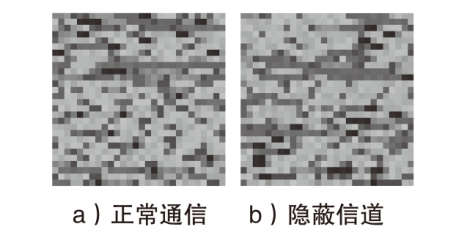
针对现有的网络流量统计特征和网络数据包负载特征无法有效检测HTTP负载隐蔽信道的问题,文章提出了一种基于会话流负载表示方式的卷积神经网络检测方法。首先,根据五元组和过期时间条件将HTTP通信产生的数据包聚合为双向会话流;然后,选择能反映通信交互行为和会话流结构的一组数据包,提取其传输层载荷原始字节序列,形成表示每一条HTTP会话流的会话流负载;最后,采用能够充分挖掘字节序列中时间与空间维度信息的2D-CNN构建检测模型。实验结果表明,提出的会话流负载表示方法相较于会话流数据包负载表示方法可以从更多的角度刻画HTTP通信,从而为检测任务提供更多有用信息。所提方法的检测准确率高达99%,效果优于基于网络流行为统计特征的传统机器学习检测方法。
中图分类号:
引用本文
苑文昕, 陈兴蜀, 朱毅, 曾雪梅. 基于深度学习的HTTP负载隐蔽信道检测方法[J]. 信息网络安全, 2023, 23(7): 53-63.
YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning[J]. Netinfo Security, 2023, 23(7): 53-63.
| [1] |
LAMPSON BW. A Note on the Confinement Problem[J]. Communications of the ACM, 1973, 16(10): 613-615.
doi: 10.1145/362375.362389 URL |
| [2] | MITRE ATT&CK. Application Layer Protocol: Web Protocols[EB/OL]. (2020-03-26) [2023-03-20]. https://attack.mitre.org/techniques/T1071/001/. |
| [3] | LIU Fang, LI Dongdong, ZHAO Yuntao, et al. The Covert Communication Detection Model Based on Key Field of Header in HTTP Protocol[J]. Fire Control & Command Control, 2018, 43(11): 38-43. |
| 刘芳, 李东东, 赵运弢, 等. HTTP 协议报文头域关键字段的隐蔽通信检测模型[J]. 火力与指挥控制, 2018, 43(11): 38-43. | |
| [4] |
SHEN Guoliang, ZHAI Jiangtao, DAI Yuewei. HTTP Parameter Sorting Covert Channel Detection Method Based on Markov Model[J]. Computer Engineering, 2020, 46(2): 154-158, 169.
doi: 10.19678/j.issn.1000-3428.0053783 |
|
沈国良, 翟江涛, 戴跃伟. 基于Markov模型的HTTP参数排序隐蔽信道检测方法[J]. 计算机工程, 2020, 46(2): 154-158,169.
doi: 10.19678/j.issn.1000-3428.0053783 |
|
| [5] | WU Jiahong, YANG Zhenguo, LIU Wenyin. Multiscale Feature Fusion for Malicious HTTP Request Detection[J]. Application Research of Computers, 2021, 38(3): 871-874+880. |
| 巫家宏, 杨振国, 刘文印. 基于多尺度特征融合的恶意HTTP请求检测方法[J]. 计算机应用研究, 2021, 38(3):871-874,880. | |
| [6] | DARWISH O, Al-FUQAHA A, BRAHIM G B, et al. Using Hierarchical Statistical Analysis and Deep Neural Networks to Detect Covert Timing Channels[EB/OL]. (2019-09-20) [2023-03-20]. https://doi.org/10.1016/j.asoc.2019.105546. |
| [7] |
Al-EIDI S, DARWISH O, CHEN Yuanzhu. Covert Timing Channel Analysis Either as Cyber Attacks or Confidential Applications[J]. Sensors, 2020, 20(8): 2417-2431.
doi: 10.3390/s20082417 URL |
| [8] |
AL-EIDI S, DARWISH O, CHEN Yuanzhu, et al. SnapCatch: Automatic Detection of Covert Timing Channels Using Image Processing and Machine Learning[J]. IEEE Access, 2020, 9: 177-191.
doi: 10.1109/Access.6287639 URL |
| [9] | WANG Yifei, YANG Yalei, RAO Mengliang. Research of HTTP Tunnel Detecting Technique Based on C4.5[J]. Computer Engineering and Design, 2012, 33(2): 493-497. |
| 王宜菲, 杨亚磊, 饶孟良. 基于C4.5的HTTP隧道检测技术研究[J]. 计算机工程与设计, 2012, 33(2):493-497. | |
| [10] | LI Wei, LI Lihui, LI Jia, et al. Characteristics Analysis of Traffic Behavior of Remote Access Trojan in Three Communication Phases[J]. Netinfo Security, 2015, 15(5): 10-15. |
| 李巍, 李丽辉, 李佳, 等. 远控型木马通信三阶段流量行为特征分析[J]. 信息网络安全, 2015, 15(5): 10-15. | |
| [11] | CHEN Xingshu, CHEN Jinghan, SHAO Guolin, et al. A Covert Communication Behavior Detection Method Based on Session Flow Aggregation[J]. Journal of University of Electronic Science and Technology of China, 2019, 48(3): 388-396. |
| 陈兴蜀, 陈敬涵, 邵国林, 等. 基于会话流聚合的隐蔽性通信行为检测方法[J]. 电子科技大学学报, 2019, 48(3): 388-396. | |
| [12] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking (ICOIN). New York: IEEE, 2017: 712-717. |
| [13] | LIN S Z, SHI Yong, XUE Zhi. Character-Level Intrusion Detection Based On Convolutional Neural Networks[C]// IEEE. 2018 International Joint Conference on Neural Networks (IJCNN). New York: IEEE, 2018: 1-8. |
| [14] | MARÍN G, CAASAS P, CAPDEHOURAT G. Deepmal-Deep Learning Models for Malware Traffic Detection and Classification[C]// Springer. Data Science-Analytics and Applications:Proceedings of the 3rd International Data Science Conference-IDSC2020. Berlin:Springer, 2021: 105-112. |
| [15] |
WANG Shanshan, YAN Qiben, CHEN Zhenxiang, et al. Detecting Android Malware Leveraging Text Semantics of Network Flows[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(5): 1096-1109.
doi: 10.1109/TIFS.2017.2771228 URL |
| [16] | NIU Weina, XIE Jiao, ZHANG Xiaosong, et al. HTTP-Based APT Malware Infection Detection Using URL Correlation Analysis[J]. Security and Communication Networks, 2021, 21: 1-12. |
| [17] | YUN Xiaochun, XIE Jiang, LI Shuhao, et al. Detecting Unknown HTTP-Based Malicious Communication Behavior via Generated Adversarial Flows and Hierarchical Traffic Features[EB/OL]. (2022-07-16) [2023-03-20]. https://doi.org/10.1016/j.cose.2022.102834. |
| [18] | FIELDING R, RESCHKE J. Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing[R]. New York: Internet Engineering Task Force (IETF), ISSN: 2070-1721, 2014. |
| [19] | KASUYA M. Threat Spotlight: Amadey Bot Targets Non-Russian Users[EB/OL]. (2020-01-08) [2023-03-20]. https://blogs.blackberry.com/en/2020/01/threat-spotlight-amadey-bot. |
| [20] | DUNCAN B. Evolution of Valak, from Its Beginnings to Mass Distribution[EB/OL]. (2020-07-24) [2023-03-20]. https://unit42. paloaltonetworks.com/valak-evolution/. |
| [21] | SHANNON C E. A Mathematical Theory of Communication[J]. ACM SIGMOBILE Mobile Computing and Communications Review, 2001, 5(1): 3-55. |
| [22] | SUN Zhongjun, ZHAI Jiangtao, DAI Yuewei. An Encrypted Traffic Identification Method Based on DPI and Load Randomness[J]. Journal of Applied Sciences, 2019, 37(5): 711-720. |
| 孙中军, 翟江涛, 戴跃伟. 一种基于DPI和负载随机性的加密流量识别方法[J]. 应用科学学报, 2019, 37(5): 711-720. | |
| [23] | AOUINI Z, PEKAR A. NFStream: A Flexible Network Data Analysis Framework[EB/OL]. (2022-02-26) [2023-03-20]. https://doi.org/10.1016/j.comnet.2021.108719. |
| [24] |
SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al. Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374.
doi: 10.1016/j.cose.2011.12.012 URL |
| [25] | WRAD D. Malware-Traffic-Analysis.net[EB/OL]. [2023-03-20]. https://malware-traffic-analysis.net/. |
| [26] | MONTAZERISHATOORI M, DAVIDSON L, KAUR G, et al. Detection of DoH Tunnels Using Time-Series Classification of Encrypted Traffic[C]// IEEE. IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC). New York: IEEE, 2020: 17-22. |
| [1] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [2] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [3] | 赵小林, 王琪瑶, 赵斌, 薛静锋. 基于机器学习的匿名流量分类方法研究[J]. 信息网络安全, 2023, 23(5): 1-10. |
| [4] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [5] | 沈传鑫, 王永杰, 熊鑫立. 基于图注意力网络的DNS隐蔽信道检测[J]. 信息网络安全, 2023, 23(1): 73-83. |
| [6] | 刘光杰, 段锟, 翟江涛, 秦佳禹. 基于多特征融合的移动流量应用识别[J]. 信息网络安全, 2022, 22(7): 18-26. |
| [7] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [8] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [9] | 林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67. |
| [10] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [11] | 高昌锋, 肖延辉, 田华伟. 基于多阶段渐进式神经网络的图像相机指纹提取算法[J]. 信息网络安全, 2022, 22(10): 15-23. |
| [12] | 刘家银, 李馥娟, 马卓, 夏玲玲. 基于多尺度卷积神经网络的恶意代码分类方法[J]. 信息网络安全, 2022, 22(10): 31-38. |
| [13] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [14] | 李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66. |
| [15] | 杨铭, 张健. 基于图像识别的恶意软件静态检测模型[J]. 信息网络安全, 2021, 21(10): 25-32. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||