信息网络安全 ›› 2023, Vol. 23 ›› Issue (1): 93-102.doi: 10.3969/j.issn.1671-1122.2023.01.011
• 理论研究 • 上一篇
一种基于跨域对抗适应的图像信息隐藏算法
- 1.南京信息工程大学数字取证教育部工程研究中心,南京 210044
2.西安电子科技大学综合业务网理论及关键技术国家重点实验室,西安 710126
3.渤海大学数学科学学院,锦州 121013
-
收稿日期:2022-10-21出版日期:2023-01-10发布日期:2023-01-19 -
通讯作者:付章杰 E-mail:fzj@nuist.edu.cn -
作者简介:李季瑀(1995—),男,山东,硕士研究生,主要研究方向为信息隐藏、深度学习|付章杰(1983—),男,河南,教授,博士,主要研究方向为数字取证、人工智能|张玉斌(1965—),女,辽宁,副教授,本科,主要研究方向为应用数学 -
基金资助:国家自然科学基金(62172232);国家重点研发计划(2021YFB2700900);江苏省杰出青年基金(BK20200039)
An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation
LI Jiyu1, FU Zhangjie1,2( ), ZHANG Yubin3
), ZHANG Yubin3
- 1. Engineering Research Center of Digital Forensics, Ministry of Education, Nanjing University of Information Science and Technology, Nanjing 210044, China
2. State Key Laboratory of Integrated Services Networks, Xidian University, Xi’an 710126, China
3. College of Mathematical Sciences, Bohai University, Jinzhou 121013, China
-
Received:2022-10-21Online:2023-01-10Published:2023-01-19 -
Contact:FU Zhangjie E-mail:fzj@nuist.edu.cn
摘要:
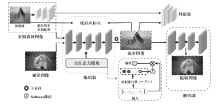
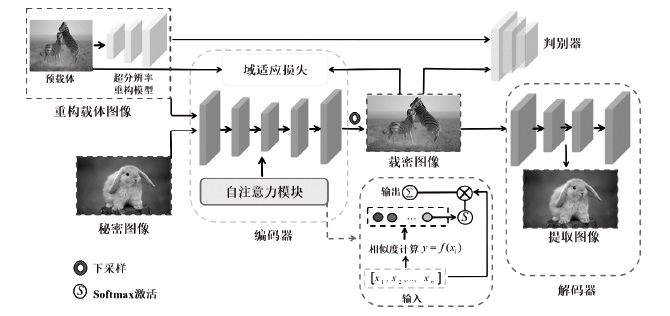
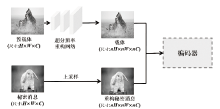
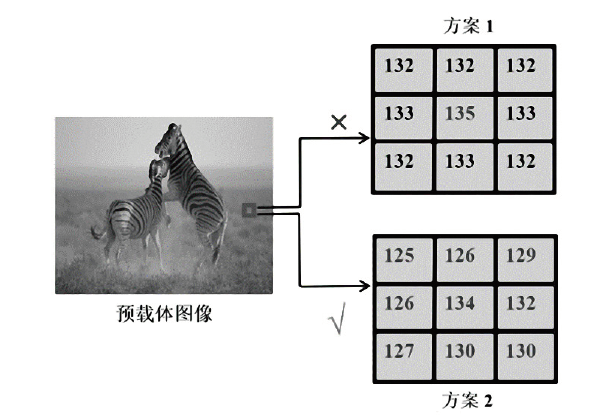
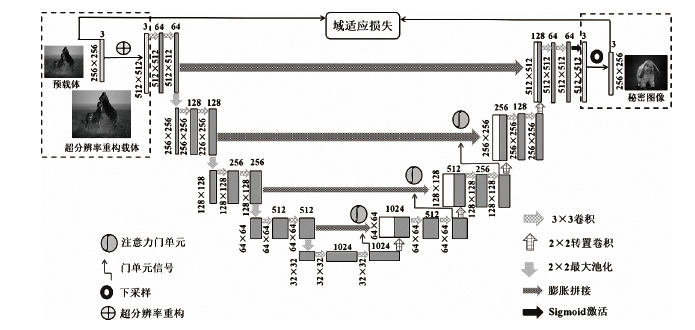
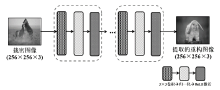
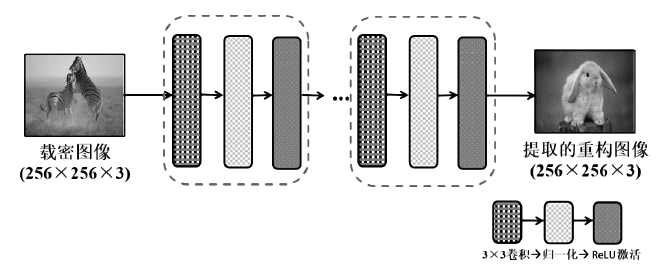
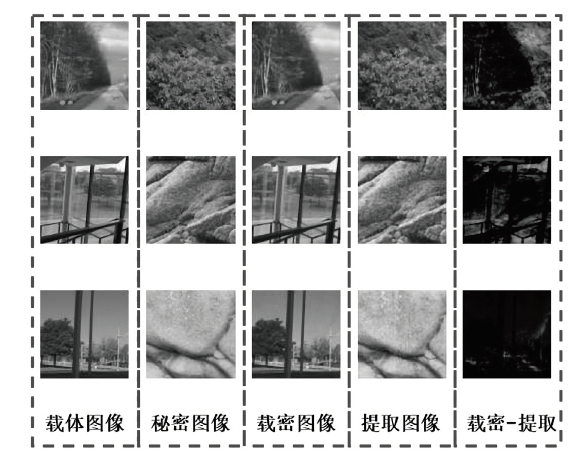
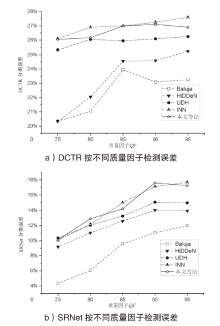
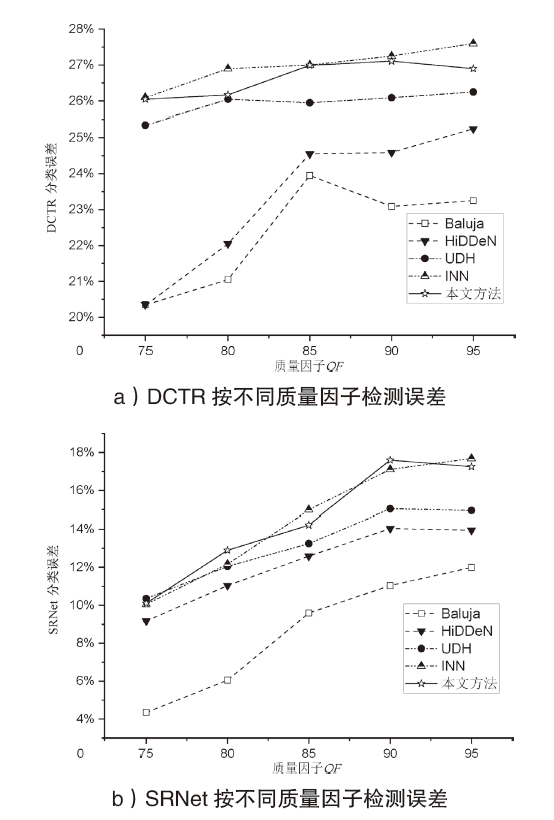
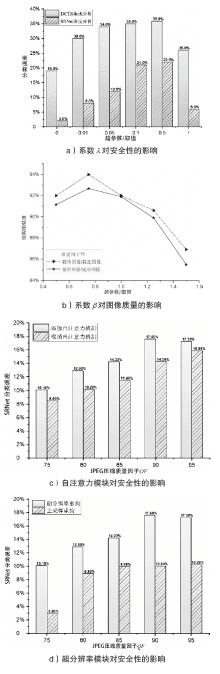
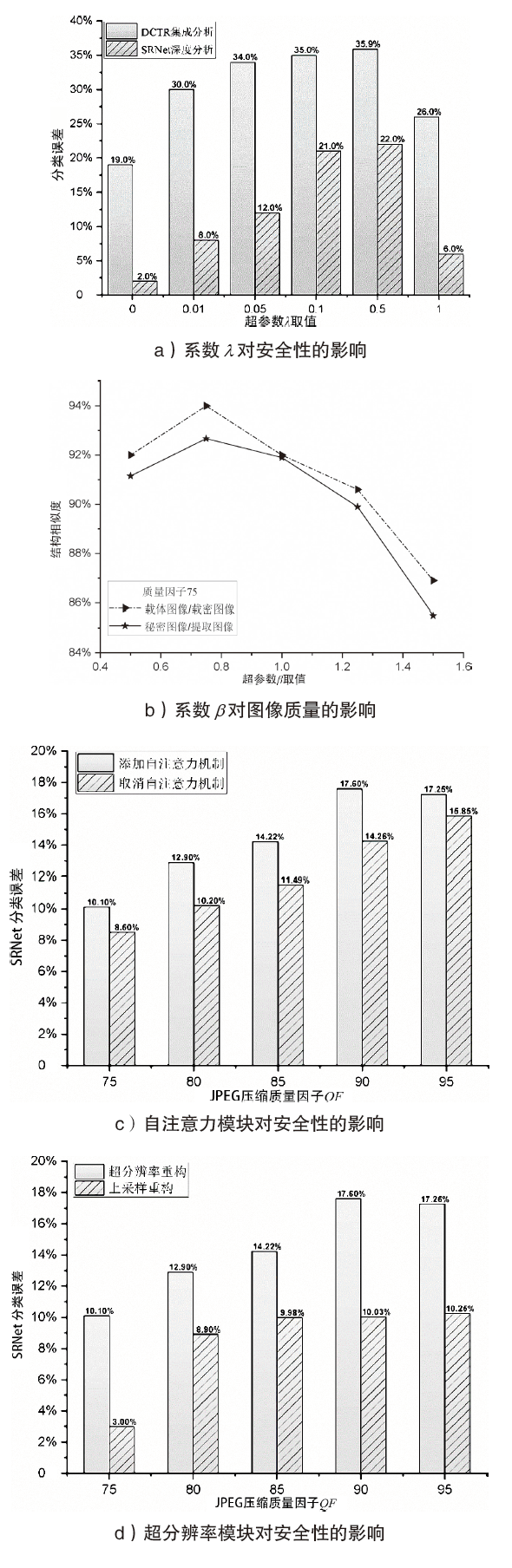
图像信息隐藏是保障信息安全的重要手段。随着深度学习的快速发展,各类基于该技术的以图藏图式隐写算法被提出,它们大多在图像质量、隐藏安全性或嵌入容量等方面的均衡性上存在不足。针对该问题,文章提出了一种基于跨域对抗适应的图像信息隐藏算法,首先,设计超分辨率网络,将秘密信息藏入放大和缩小后不变的图像内容中,提高秘密信息的嵌入容量;然后,在编码网络中加入注意力机制,使编码网络能够关注主要特征并抑制冗余特征,提高生成图像的分辨率;最后,在生成器网络中加入域适应损失指导载密图像的生成,模型整体采用生成对抗的方式进行训练,减小载体图像和载密图像之间的跨域差异。实验结果表明,与其他以图藏图隐写算法相比,文章所提算法在保证图像质量的同时,提高了信息隐藏的安全性和嵌入容量。
中图分类号:
引用本文
李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1): 93-102.
LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation[J]. Netinfo Security, 2023, 23(1): 93-102.
表1
Alaska2数据集上不同方法的视觉质量对比(PSNR分值/SSIM百分比)
| BALUJA | HiDDeN | UDH | INN | 本文方法 | |
|---|---|---|---|---|---|
| 载体/ 载密 QF=75 QF=85 QF=95 | 33.27/84.3% 35.40/95.9% 36.41/96.6% | 31.21/77.59% 35.183/94.28% 35.87/98.7% | 35.791/91.13% 35.935/96.26% 38.33/98.5% | 36.82/91.45% 39.01/96.6% 39.13/97% | 37.42/94% 37.69/94.32% 37.95/94.7% |
| 秘密/ 提取 QF=75 QF=85 QF=95 | 30.33/81% 33.465/91.14% 35.89/95.85% | 31.53/82.7% 33.98/94% 34.72/94.8% | 35.22/90.53% 34.97/92.3% 37.18/96.7% | 35.8/92% 38.115/95.8% 39.355/96% | 35.958/92.67% 36.115/91.4% 36.45/93.9% |
| [1] |
YU Kunliang, CHEN Liquan, WANG Yu, et al. A Channel Coding Information Hiding Algorithm for Images Based on Uniform Cyclic Shift[J]. Multimedia Tools and Applications, 2022, 81(8): 11279-11300.
doi: 10.1007/s11042-022-12034-8 URL |
| [2] | LIN C C, CHANG C C, KAO W J, et al. Efficient Electronic Patient Information Hiding Scheme with Tamper Detection Function for Medical Images[J]. IEEE Access, 2022(10): 18470-18485. |
| [3] | PAN Feng, LI Jun, YANG Xiaoyuan. Image Steganography Method Based on PVD and Modulus Function[C]// IEEE. 2011 International Conference on Electronics, Communications and Control (ICECC). New York: IEEE, 2011: 282-284. |
| [4] |
MIELIKAINEN J. LSB Matching Revisited[J]. IEEE Signal Processing Letters, 2006, 13(5): 285-287.
doi: 10.1109/LSP.2006.870357 URL |
| [5] | COX I J, MILLER M L, BLOOM J A, et al. Digital Watermarking and Steganography[J]. Morgan Kaufmann, 2008, 11: 61-103. |
| [6] |
FILLER T, JUDAS J, FRIDRICH J. Minimizing Additive Distortion in Steganography Using Syndrome-Trellis Codes[J]. IEEE Transactions on Information Forensics and Security, 2011, 6(3): 920-935.
doi: 10.1109/TIFS.2011.2134094 URL |
| [7] | VOLKHONSKIY D, BORISENKO B, BURNAEV E. Generative Adversarial Networks for Image Steganography[EB/OL]. (2016-11-05)[2022-09-10]. https://openreview.net/pdf?id=H1hoFU9xe.htm. |
| [8] |
TANG Weixuan, LI Bin, TAN Shuquan, et al. CNN-based adversarial embedding for image steganography[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(8): 2074-2087.
doi: 10.1109/TIFS.2019.2891237 URL |
| [9] | SHI Haichao, DONG Jing, WANG Wei, et al. Ssgan: Secure Steganography Based on Generative Adversarial Networks[C]// Springer. In Pacific Rim Conference on Multimedia. Berlin: Springer, 2017: 534-544. |
| [10] | NGUYEN B C, YOON S M, LEE H-K. Multi Bit Plane Image Steganography[C]// Springer. International Workshop on Digital Watermarking. Berlin:Springer, 2006: 61-70. |
| [11] | HETAL S, MUTZEL P. A Graph-Theoretic Approach to Steganography[C]// Springer. IFIP International Conference on Communications and Multimedia Security. Berlin:Springer, 2005: 119-128. |
| [12] | PEVNY T, FILLER T, BAS P. Using High-Dimensional Image Models to Perform Highly Undetectable Steganography[C]// Springer. In International Workshop on Information Hiding. Berlin:Springer, 2010: 161-177. |
| [13] | HOLUB V, FRIDRICH J. Designing Steganographic Distortion Using Directional Filters[C]// IEEE. 2012 IEEE International Workshop on Information Forensics and Security (WIFS). New York:IEEE, 2012: 234-239. |
| [14] | HOLUB V, FRIDRICH J, DENEMARK T. Universal Distortion Function for Steganography in an Arbitrary Domain[J]. EURASIP Journal on Information Security, 2014(1): 1-13. |
| [15] | LI Bin, WANG Ming, HUANG Jiwu, et al. A New Cost Function for Spatial Image Steganography[C]// IEEE. 2014 IEEE International Conference on Image Processing (ICIP). New York:IEEE, 2014: 4206-4210. |
| [16] |
PEVNY T, BAS P, FRIDRICH J. Steganalysis by Subtractive Pixel Adjacency Matrix[J]. IEEE Transactions on Information Forensics and Security, 2010, 5(2): 215-224.
doi: 10.1109/TIFS.2010.2045842 URL |
| [17] | GOODFELLOW L J, POUGET-A J, MIRZA M, et al. Generative Adversarial Nets. Advances in Neural Information Processing Systems[C]// ACM. Proceedings of the 27th International Conference on Neural Information Processing Systems. New York: ACM, 2014: 2672-2680. |
| [18] | RADFORD A, METZ L, CHINTALA S. Unsupervised Representation Learning with Deep Convolutional Generative Adversarial Networks[EB/OL]. (2016-01-07)[2022-09-10]. https://arxiv.org/abs/1511.06434.htm. |
| [19] | LIU Mingming, ZHANG Minqing, LIU Jia, et al. Coverless Information Hiding Based on Generative Adversarial Networks[J]. Journal of Applied Sciences, 2018, 36(2): 371-382. |
| 刘明明, 张敏情, 刘佳, 等. 基于生成对抗网络的无载体信息隐藏[J]. 应用科学学报, 2018, 36(2): 371-382. | |
| [20] | BI Xinliang, YANG Haibin, YANG Xiaoyuan, et al. Generative Strganography Scheme Based on StarGAN[J]. Netinfo Security, 2020, 20(12): 64-71. |
| 毕新亮, 杨海滨, 杨晓元, 等. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71. | |
| [21] | LIN Zhouhan, FENG Minwei, SANTOS C N, et al. A Structured Self-Attentive Sentence Embedding[J]. arXiv preprint arXiv, 2017, 3(9): 1-15. |
| [22] | ZHANG X, KONG X, WANG P, et al. Cover-Source Mismatch in Deep Spatial Steganalysis[C]//Springer. International Workshop on Digital Watermarking. Berlin:Springer, 2019: 71-83. |
| [23] | DASTGHEIB M B, JAHROMI M F, NEJAD J T. A Low Cost Image Steganalysis by Using Domain Adaptation[J]. International Journal of Information Science and Management (IJISM), 2018, 16(1): 191-201. |
| [24] |
YANG Yong, KONG Xiangwei, WANG Bo, et al. Steganalysis on Internet Images Via Domain Adaptive Classifier[J]. Neurocomputing, 2019, 351: 205-216.
doi: 10.1016/j.neucom.2019.04.025 |
| [25] | WANG Yaojie, YANG Xiaoyuan, LIU jia. Cross-Domain Image Steganography Based on GANs[C]// Springer. International Conference on Security with Intelligent Computing and Big-data Services. Berlin:Springer, 2018: 743-755. |
| [26] | GABRIEL G. NinaSR: Efficient Small and Large ConvNets for Super-Resolution. GitHub repository[EB/OL]. (2021-08-21)[2022-09-10]. https://github.com/Coloquinte/torchSR. |
| [27] |
DUAN Xintao, LIU Nao, GOU Mengxiao, et al. SteganoCNN: Image Steganography with Generalization Ability Based on Convolutional Neural Network[J]. Entropy, 2020, 22(10): 1155.
doi: 10.3390/e22101155 URL |
| [28] |
BOROUMAND M, CHEN Mo, FRIDRICH J. Deep Residual Network for Steganalysis of Digital Images[J]. IEEE Transactions on Information Forensics and Security, 2019, 14(5): 1181-1193.
doi: 10.1109/TIFS.2018.2871749 URL |
| [29] |
BALUJA S. Hiding Images within Images[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2020, 42(7): 1685-1697.
doi: 10.1109/TPAMI.2019.2901877 pmid: 30835212 |
| [30] | ZHU Jiren, KAPLAN R, JOHNSON J, et al. Hidden: Hiding Data with Deep Networks[C]// Springer. European Conference on Computer Vision (ECCV). Berlin: Springer, 2018: 682-697. |
| [31] | ZHANG Chaoning, BENZ P, KARJAUV A, et al. UDH: Universal Deep Hiding for Steganography, Watermarking, and Light Field Messaging[J]. Advances in Neural Information Processing Systems, 2020, 33: 10223-10234. |
| [32] | LU Shaoping, WANG Rong, ZHANG Tao, et al. Large-Capacity Image Steganography Based on Invertible Neural Networks[C]// IEEE. IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2021: 10816-10825. |
| [33] | HOLUB V, FRIDRICH J. Low-Complexity Features for JPEG Steganalysis Using Undecimated DCT[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(2): 219-228. |
| [1] | 杨婉霞, 陈帅, 管磊, 杨忠良. 宋词自动生成的信息隐藏算法[J]. 信息网络安全, 2022, 22(7): 46-54. |
| [2] | 夏强, 何沛松, 罗杰, 刘嘉勇. 基于普遍对抗噪声的高效载体图像增强算法[J]. 信息网络安全, 2022, 22(2): 64-75. |
| [3] | 郭森森, 王同力, 慕德俊. 基于生成对抗网络与自编码器的网络流量异常检测模型[J]. 信息网络安全, 2022, 22(12): 7-15. |
| [4] | 林文兵, 张敏情, 周能, 孔咏骏. 基于同态加密的密文域可逆信息隐藏技术研究[J]. 信息网络安全, 2021, 21(4): 73-80. |
| [5] | 王耀杰, 杨晓元, 刘文超. 基于数字化卡登格的生成图像隐写方案[J]. 信息网络安全, 2021, 21(2): 70-77. |
| [6] | 雷雨, 刘佳, 李军, 柯彦. 一种基于条件生成对抗网络的图像隐写方法研究与实现[J]. 信息网络安全, 2021, 21(11): 48-57. |
| [7] | 张敏情, 周能, 刘蒙蒙, 柯彦. 同态加密域可逆信息隐藏技术研究[J]. 信息网络安全, 2020, 20(8): 25-36. |
| [8] | 彭中联, 万巍, 荆涛, 魏金侠. 基于改进CGANs的入侵检测方法研究[J]. 信息网络安全, 2020, 20(5): 47-56. |
| [9] | 毕新亮, 杨海滨, 杨晓元, 黄思远. 基于StarGAN的生成式图像隐写方案[J]. 信息网络安全, 2020, 20(12): 64-71. |
| [10] | 唐洪琼, 钮可, 张英男, 杨晓元. 自适应二维直方图迁移的视频可逆隐写算法[J]. 信息网络安全, 2019, 19(9): 106-110. |
| [11] | 王耀杰, 钮可, 杨晓元. 基于生成对抗网络的图像隐藏方案[J]. 信息网络安全, 2019, 19(5): 54-60. |
| [12] | 欧博, 石向莲. 基于深度无合成误差模型的三维图像可逆信息隐藏方法研究[J]. 信息网络安全, 2018, 18(5): 24-31. |
| [13] | 熊金波, 马蓉, 张媛媛, 戴睿煜. 面向社交网络的图片信息隐藏方法与实现[J]. 信息网络安全, 2017, 17(3): 6-8. |
| [14] | 陆海宁. 可隐藏搜索模式的对称可搜索加密方案[J]. 信息网络安全, 2017, 17(1): 38-42. |
| [15] | 肖迪, 王莹, 常燕廷, 周佳奇. 基于加法同态与多层差值直方图平移的密文图像可逆信息隐藏算法[J]. 信息网络安全, 2016, 16(4): 9-16. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||