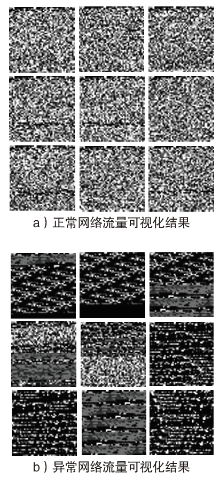
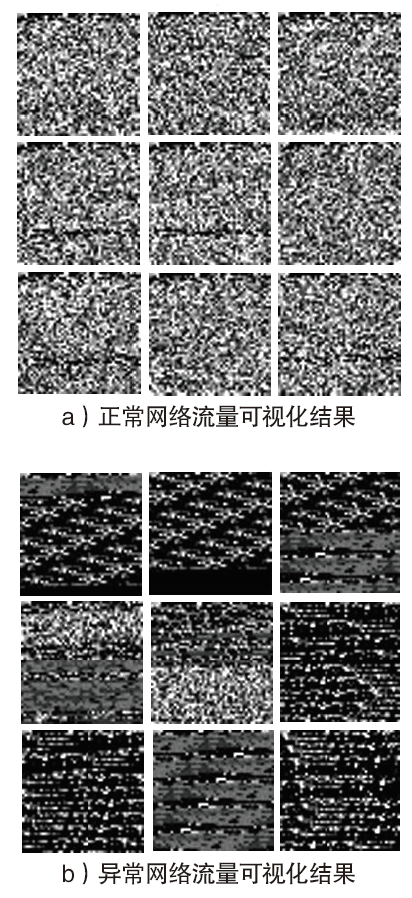
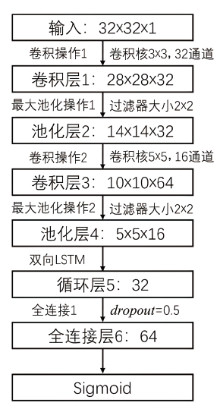
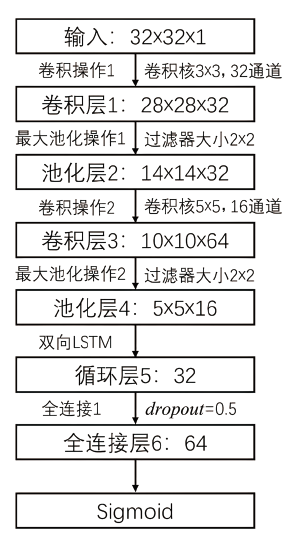
信息网络安全 ›› 2021, Vol. 21 ›› Issue (7): 54-62.doi: 10.3969/j.issn.1671-1122.2021.07.007
基于卷积循环神经网络的网络流量异常检测技术
- 中国运载火箭技术研究院,北京 100076
-
收稿日期:2021-01-12出版日期:2021-07-10发布日期:2021-07-23 -
通讯作者:马泽文 E-mail:desperate_ma@163.com -
作者简介:徐洪平(1969—),男,河南,研究员,硕士,主要研究方向为网络空间安全|马泽文(1996—),男,辽宁,硕士研究生,主要研究方向为网络空间安全|易航(1982—),男,辽宁,研究员,硕士,主要研究方向为网络空间安全|张龙飞(1988—),男,陕西,工程师,本科,主要研究方向为飞行器设计 -
基金资助:国家自然科学基金(62072025)
Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network
XU Hongping, MA Zewen( ), YI Hang, ZHANG Longfei
), YI Hang, ZHANG Longfei
- China Academy of Launch Vehicle Technology, Beijing 100076, China
-
Received:2021-01-12Online:2021-07-10Published:2021-07-23 -
Contact:MA Zewen E-mail:desperate_ma@163.com
摘要:
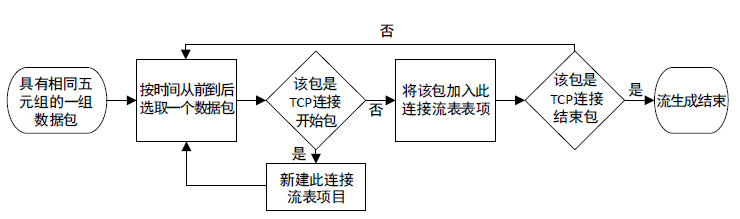
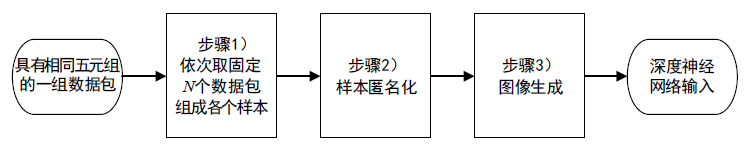
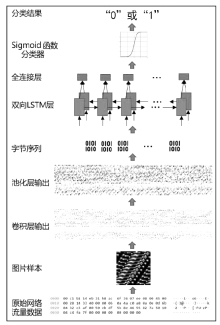
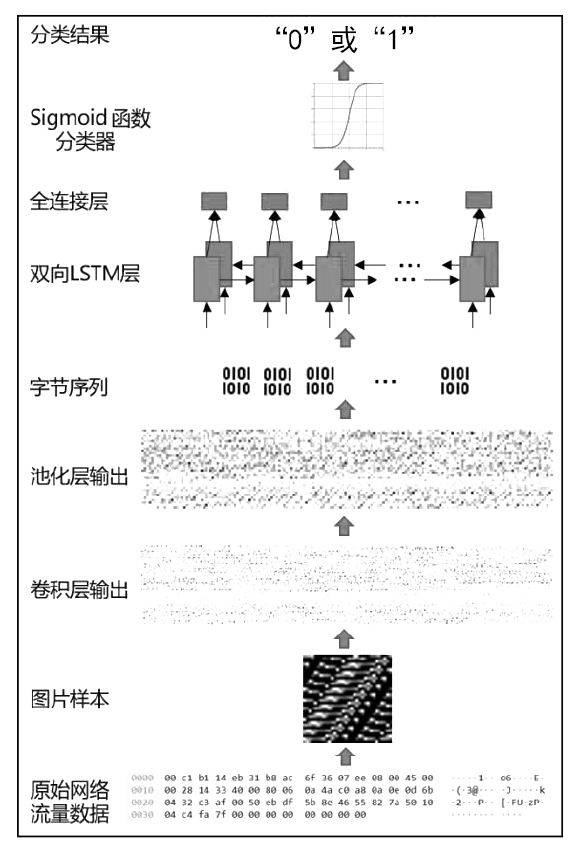
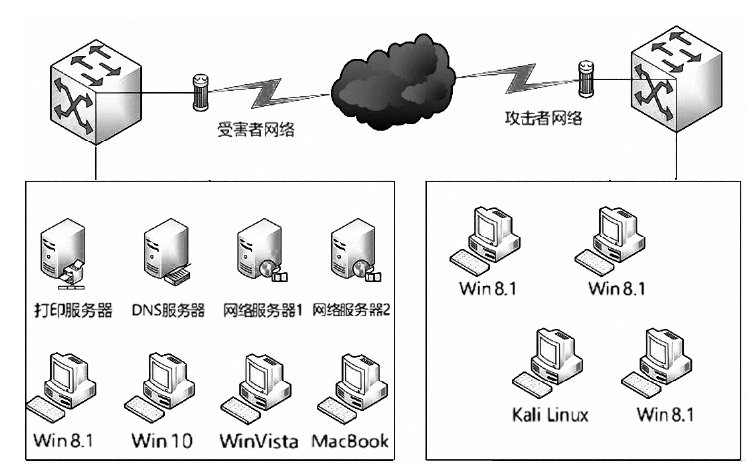
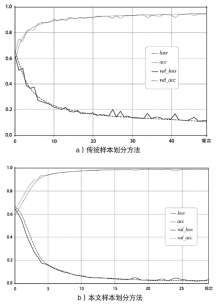
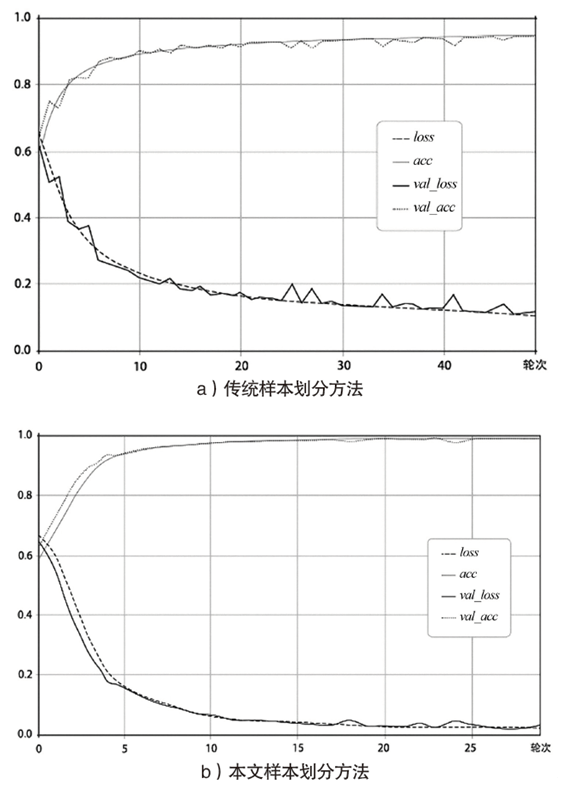
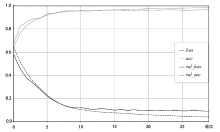
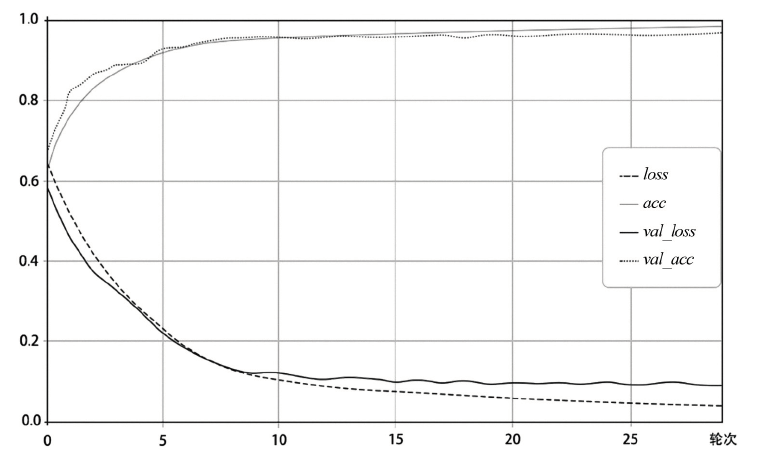
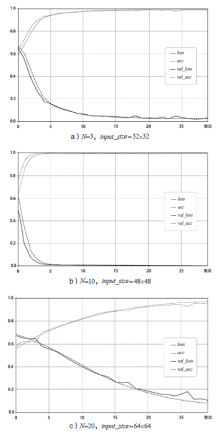
随着互联网技术的广泛普及,网络安全问题也随之增加。作为网络系统的主要防御手段之一,对网络流量进行异常检测从过去基于流量负载特征和基于异常特征库匹配的检测方式,逐渐向基于机器学习、深度学习的分类方法转变。文章首先提出一种基于数据包数目的网络流量数据样本划分方法,然后组合使用深度学习中的卷积神经网络和循环神经网络提出一种基于卷积循环神经网络的网络流量异常检测算法,该算法能更充分地提取网络流量数据在空间域和时间域上的特征;最后使用公开网络流量数据集进行流量异常检测实验。实验得到了很高的精度、召回率和准确率,验证了文章方法的有效性。
中图分类号:
引用本文
徐洪平, 马泽文, 易航, 张龙飞. 基于卷积循环神经网络的网络流量异常检测技术[J]. 信息网络安全, 2021, 21(7): 54-62.
XU Hongping, MA Zewen, YI Hang, ZHANG Longfei. Network Traffic Anomaly Detection Technology Based on Convolutional Recurrent Neural Network[J]. Netinfo Security, 2021, 21(7): 54-62.
表1
两个实验的具体实验结果
| 卷积循环神经网络 + 传统样本划分方法 | 卷积神经网络 + 本文样本划分方法 | 卷积循环神经网络 + 本文样本划分方法 | ||
|---|---|---|---|---|
| 训练集 | 精度 | 0.9386 | 0.9818 | 0.9920 |
| 召回率 | 0.9599 | 0.9916 | 0.9958 | |
| 准确率 | 0.9485 | 0.9866 | 0.9938 | |
| 验证集 | 精度 | 0.9320 | 0.9588 | 0.9927 |
| 召回率 | 0.9616 | 0.9779 | 0.9860 | |
| 准确率 | 0.9459 | 0.9679 | 0.9927 | |
| 测试集 | 精度 | 0.9346 | 0.9620 | 0.9923 |
| 召回率 | 0.9552 | 0.9747 | 0.9862 | |
| 准确率 | 0.9442 | 0.9681 | 0.9893 | |
| [1] | LIU Xingbin, YANG Jianhua, XIE Gaogang, et al. Automated-mining of Packet Signatures for Traffic Identification at Application Layer with Apriori Algorithm[J]. Journal on Communications, 2009, 29(12):51-59. |
| [2] | ZHAO Shuang, CHEN Shuhui. Review: Traffic Identification Based on Machine Learning[J]. Computer Engineering and Science, 2018, 40(10):1746-1756. |
| 赵双, 陈曙晖. 基于机器学习的流量识别技术综述与展望[J]. 计算机工程与科学, 2018, 40(10):1746-1756. | |
| [3] | LIU Xingbin, YANG Jianhua, XIE Gaogang, et al. Automated Mining of Packet Signatures for Traffic Identification at Application Layer with Apriori Algorithm[J]. Journal on Communications, 2008, 29(12):51-59. |
| 刘兴彬, 杨建华, 谢高岗, 等. 基于Apriori算法的流量识别特征自动提取方法[J]. 通信学报, 2008, 29(12):51-59. | |
| [4] |
AHMED M, MAHMOOD A N, HU Jiankun. A Survey of Network Anomaly Detection Techniques[J]. Journal of Network and Computer Applications, 2016, 60(C):19-31.
doi: 10.1016/j.jnca.2015.11.016 URL |
| [5] | MOORE A W, ZUEV D. Internet Traffic Classification Using Bayesian Analysis Techniques[C]// ACM. The 2005 ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, June 6-10, 2005, Banff, Alberta, Canada. New York: ACM, 2005: 50-60. |
| [6] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[C]// INSTICC. 4th International Conference on Information Systems Security and Privacy (ICISSP), October 22-24, 2018, Funchal, Portugal. Berlin: Springer, 2018: 172-188. |
| [7] |
NASEER S, SALEEM Y, KHALID S, et al. Enhanced Network Anomaly Detection Based on Deep Neural Networks[J]. IEEE Access, 2018, 6(8):48231-48246.
doi: 10.1109/ACCESS.2018.2863036 URL |
| [8] | WANG Wei, ZHU Ming, ZENG Xuewen, et al. Malware Traffic Classification Using Convolutional Neural Network for Representation Learning[C]// IEEE. 2017 International Conference on Information Networking, January 11-13, Da Nang, Vietnam. NJ: IEEE, 2017: 712-717. |
| [9] | LECUN Y, JACKEL L, BOTTOU L, et al. Learning Algorithms for Classification: A Comparison on Handwritten Digit Recognition[C]// CTP-PBSRI. The CTP-PBSRI Joint Workshop on Theoretical Physics, February 2-4, 1995, Pohang, Korea. Singapore: World Science, 1995: 261-276. |
| [10] | LIANG Jie, CHEN Jiahao, ZHANG Xueqin, et al. One-hot Encoding and Convolutional Neural Network-based Anomaly Detection[J]. Journal of Tsinghua University (Science and Technology), 2019, 59(7):523-529. |
| 梁杰, 陈嘉豪, 张雪芹, 等. 基于独热编码和卷积神经网络的异常检测[J]. 清华大学学报(自然科学版), 2019, 59(7):523-529. | |
| [11] | ZHANG Yansheng, LI Xiwang, LI Dan, et al. Abnormal Flow Monitoring of Industrial Control Network Based on Convolutional Neural Network[J]. Journal of Computer Applications, 2019, 39(5):1512-1517. |
| 张艳升, 李喜旺, 李丹, 等. 基于卷积神经网络的工控网络异常流量检测[J]. 计算机应用, 2019, 39(5):1512-1517. | |
| [12] | RADFORD B J, APOLONIO L M, TRIAS A J, et al. Network Traffic Anomaly Detection Using Recurrent Neural Networks[EB/OL]. https://arxiv.org/pdf/1803.10769v1.pdf, 2020-11-25. |
| [13] | KRIZHEVSKY A, SUTSKEVER I, HINTON G. ImageNet Classification with Deep Convolutional Neural Networks[EB/OL]. https://web.cs.ucdavis.edu/~yjlee/teaching/ecs289g-winter2018/alexnet.pdf, 2020-11-25. |
| [14] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR), June 27-30, 2016, Las Vegas, NV, USA. NJ: IEEE, 2016: 770-778. |
| [15] |
SHI Baoguang, BAI Xiang, YAO Cong. An End-to-end Trainable Neural Network for Image-based Sequence Recognition and Its Application to Scene Text Recognition[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2016, 39(11):2298-2304.
doi: 10.1109/TPAMI.2016.2646371 URL |
| [16] | WANG Yequan, HUANG Minlie, ZHU Xiayan, et al. Attention-based LSTM for Aspect-level Sentiment Classification[C]// EMNLP. The 2016 Conference on Empirical Methods in Natural Language Processing, November 1-4, 2016, Austin, Texas, USA. Cambridge: The Association for Computational Linguistics, 2016: 606-615. |
| [17] | HINTON G, SRIVASTAVA N, KRIZHEVSKY A, et al. Improving Neural Networks by Preventing Co-adaptation of Feature Detectors[EB/OL]. https://www.researchgate.net/publication/228102719_Improving_neural_networks_by_preventing_co-adaptation_of_feature_detectors, 2020-11-28. |
| [18] | SRIVASTAVA N, HINTON G, KRIZHEVSKY A, et al. Dropout: A Simple Way to Prevent Neural Networks from Overfitting[J]. Journal of Machine Learning Research, 2014, 15(1):1929-1958. |
| [1] | 于克辰, 郭莉, 姚萌萌. 基于空间及能量维度的黑盒对抗样本生成方法[J]. 信息网络安全, 2021, 21(3): 72-78. |
| [2] | 方勇, 朱光夏天, 刘露平, 贾鹏. 基于深度学习的浏览器Fuzz样本生成技术研究[J]. 信息网络安全, 2019, 19(3): 26-33. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||