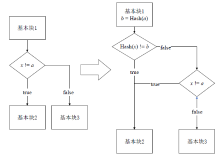
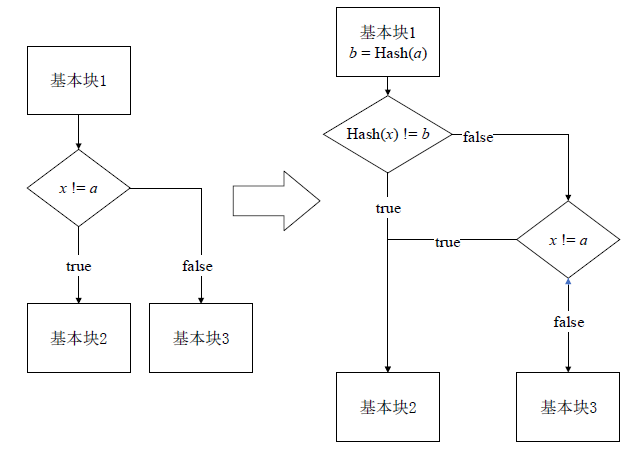
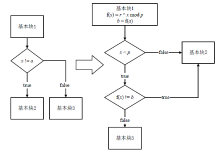
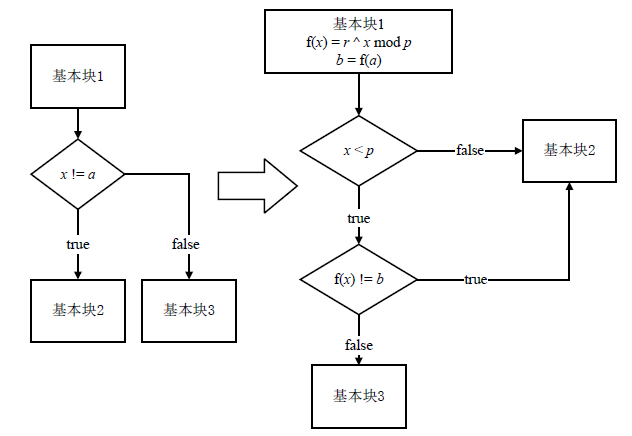
信息网络安全 ›› 2021, Vol. 21 ›› Issue (7): 17-26.doi: 10.3969/j.issn.1671-1122.2021.07.003
一种对抗符号执行的代码混淆系统
- 北京大学软件与微电子学院,北京 100080
-
收稿日期:2021-04-05出版日期:2021-07-10发布日期:2021-07-23 -
通讯作者:文伟平 E-mail:weipingwen@ss.pku.edu.cn -
作者简介:文伟平(1976—),男,湖南,教授,博士,主要研究方向为网络攻击与防范、软件安全漏洞分析、恶意代码研究、信息系统逆向工程和可信计算技术|方莹(1995—),女,浙江,硕士研究生,主要研究方向为网络与系统安全、智能合约安全|叶何(1998—),男,安徽,硕士研究生,主要研究方向为网络与系统安全、云计算|陈夏润(1997—),男,江西,硕士研究生,主要研究方向为网络与系统安全、漏洞挖掘 -
基金资助:国家自然科学基金(61872011)
A Code Obfuscation System against Symbolic Execution Attacks
WEN Weiping( ), FANG Ying, YE He, CHEN Xiarun
), FANG Ying, YE He, CHEN Xiarun
- School of Software and Microelectronics, Peking University, Beijing 100080, China
-
Received:2021-04-05Online:2021-07-10Published:2021-07-23 -
Contact:WEN Weiping E-mail:weipingwen@ss.pku.edu.cn
摘要:
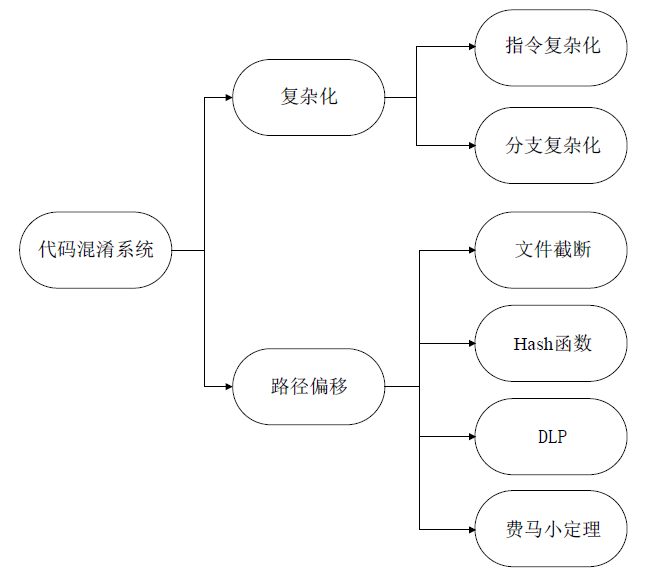
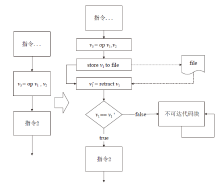
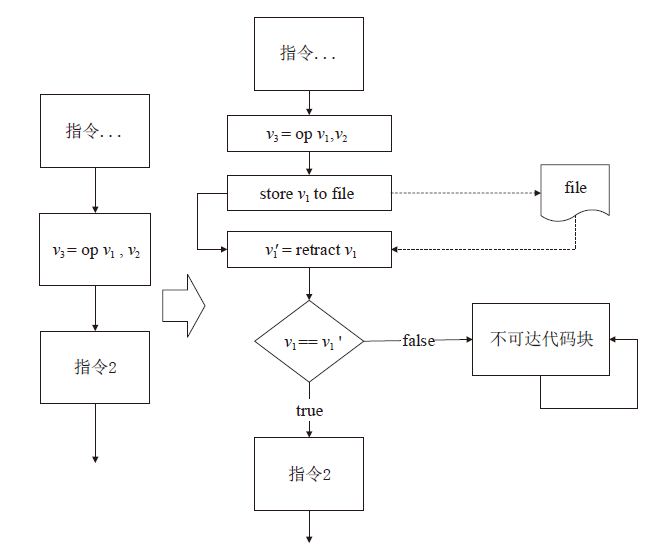
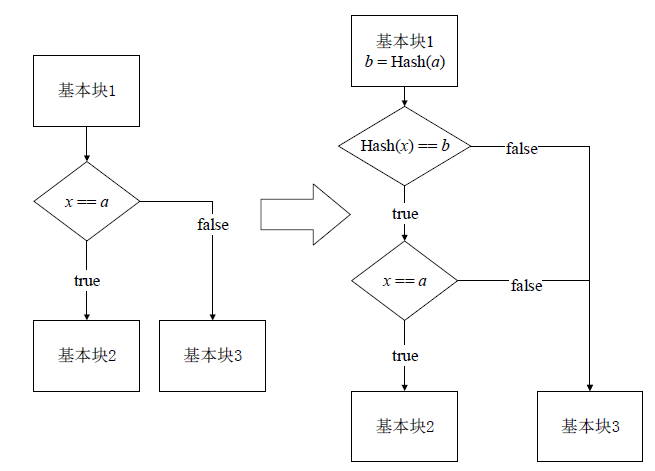
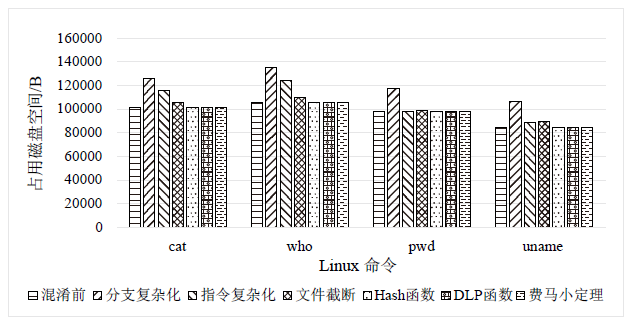
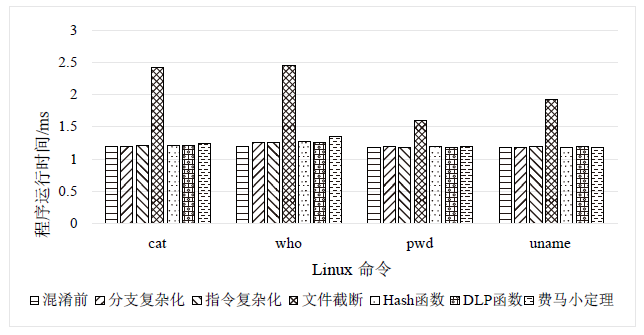
符号执行在辅助挖掘软件漏洞和软件去混淆等领域取得了很大的进展,作为保护软件安全最有效手段之一的代码混淆系统如今几乎无法对抗符号执行的攻击。为解决上述问题,文章从混淆系统的功能扩展和符号执行工具的弱点利用出发,通过丰富OLLVM的同义指令替换集合和恒真谓词集合,设计不透明谓词对软件控制流进行混淆以及对分支条件进行加固,提出一种可以兼容多种编程语言、可扩展并且可以对抗符号执行攻击的代码混淆系统。实验表明,文章提出的混淆系统可以在不改变软件原有功能的前提下诱导符号执行工具分析不可达的路径或者保护软件的部分路径不被探索到,从而可以有效对抗符号执行攻击。相较传统混淆系统,文章提出的混淆系统在对抗符号执行攻击方面具有明显优势。
中图分类号:
引用本文
文伟平, 方莹, 叶何, 陈夏润. 一种对抗符号执行的代码混淆系统[J]. 信息网络安全, 2021, 21(7): 17-26.
WEN Weiping, FANG Ying, YE He, CHEN Xiarun. A Code Obfuscation System against Symbolic Execution Attacks[J]. Netinfo Security, 2021, 21(7): 17-26.
表1
指令替换表
| 原指令 | 替换后 |
|---|---|
| a = b c | a = (b d) (c-d) |
| a = (b-r r) (c r-r) | |
| a = (bh ch) (bl cl) | |
| a = b c zero | |
| a = b-c | a = b d; a = a-c; a = a-d |
| a = b-d; a = a-c; a = a d | |
| a = (bh-ch) (bl-cl) | |
| a = (b r-r)- (c-r r) | |
| a = b-c-zero | |
| a = b * c | a = (b-r r)*c |
| a = (b-r r)* (c-r r) | |
| a = b * c | a = (b zero)* (c-zero) |
| a = b << c | a = (b r-r) << c |
| a = (bh << c)% 1 << 16 ( bl << c)% 1 << 16 | |
| a = b >> c | a = ( b r-r) << c |
| a = b & c | a = (b r-r)& (c r-r) |
| a = (b zero)& (c-zero) | |
| a = bl & cl bh & ch | |
| a = b | c | a = (b r-r) | (c r-r) |
| a = (b zero) | (c-zero) | |
| a = bl | cl bh | ch | |
| a = b ^ c | a = (b r-r) ^ (c r-r) |
| a = (b zero) ^ (c-zero) | |
| a = bl ^ cl bh ^ ch |
| [1] | COLLBERG C, THOMBORSON C, LOW D. Breaking Abstractions and Unstructuring Data Structures[C]// IEEE. The 1998 International Conference on Computer Languages, May 14-16, 1998, Chicago, IL, USA. Los Alamitos: IEEE Comp Soc, 1998: 28-38. |
| [2] | BANESCU S, COLLBERG C, GANESH V, et al. Code Obfuscation Against Symbolic Execution Attacks[C]// ACSA. 32nd Annual Computer Security Applications Conference, December 5-9, 2016, Los Angeles, CA, USA. New York: Association for Computing Machinery, 2016: 189-200. |
| [3] |
BOYER R S, ELSPAS B, LEVITT K N. SELECT—A Formal System for Testing and Debugging Programs by Symbolic Execution[J]. ACM SigPlan Notices, 1975, 10(6):234-245.
doi: 10.1145/390016.808445 URL |
| [4] | CLARKE L A. A Program Testing System[C]// ACM. 1976 ACM Annual Conference, October 20-22, 1976, Houston, TX, USA. New York: Association for Computing Machinery, 1976: 488-491. |
| [5] |
KING J C. Symbolic Execution and Program Testing[J]. Communications of the ACM, 1976, 19(7):385-394.
doi: 10.1145/360248.360252 URL |
| [6] | SALWAN J, BARDIN S, POTET M L. Symbolic Deobfuscation: From Virtualized Code Back to the Original[C]// SIDAR. 15th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, DIMVA 2018, June 28-29, 2018, Saclay, France. New York: Springer Verlag, 2018: 372-392. |
| [7] | YADEGARI B, DEBRAY S. Symbolic Execution of Obfuscated Code[C]// ACM SIGSAC. 22nd ACM SIGSAC Conference on Computer and Communications Security, CCS 2015, October 12-16, 2015, Denver, CO, USA. New York: Association for Computing Machinery, 2015: 732-744. |
| [8] | YADEGARI B, JOHANNESMEYER B, WHITELY B, et al. A Generic Approach to Automatic Deobfuscation of Executable Code[C]// IEEE Computer Society's Technical Committee (TC). 36th IEEE Symposium on Security and Privacy, May 18-20, 2015, San Jose, CA, USA. Piscataway: Institute of Electrical and Electronics Engineers Inc., 2015: 674-691. |
| [9] | BRUMLEY D, HARTWIG C, LIANG Zhenkai, et al. Automatically Identifying Trigger-based Behavior in Malware[M]. New York: Springer, 2008. |
| [10] | MING Jiang, XU Dongpeng, WANG Li, et al. Loop: Logic-oriented Opaque Predicate Detection in Obfuscated Binary Code[C]// ACM SIGSAC. 22nd ACM SIGSAC Conference on Computer and Communications Security, CCS 2015, October 12-16, 2015, Denver, CO, USA. New York: Association for Computing Machinery, 2015: 757-768. |
| [11] | TOFIGHI S R, CHRISTOFI M, ELBAZ-VINCENT P, et al. Dose: Deobfuscation Based on Semantic Equivalence[C]// ACM. 8th Software Security, Protection, and Reverse Engineering Workshop, SSPREW 2018, December 3-4, 2018, San Juan, PR, USA. New York: Association for Computing Machinery, 2018: 1-12. |
| [12] | EYROLLES N, GOUBIN L, VIDEAU M. Defeating Mba-based Obfuscation[C]// ACM SIGSAC. 2nd International Workshop on Software PROtection, SPRO 2016,October 28, 2016, Vienna, Austria. New York: Association for Computing Machinery, 2016-27-37. |
| [13] | GABRIEL F. Deobfuscation: Recovering An OLLVM-protected Program[EB/OL]. https://blog.quarkslab.com/deobfuscation-recovering-an-ollvm-protected-program.html, 2014-12-04. |
| [14] | SCHRITTWIESER S, KATZENBEISSER S, KINDER J, et al. Protecting Software through Obfuscation: Can It Keep Pace with Progress in Code Analysis?[J]. ACM Computing Surveys (CSUR), 2016, 49(1):1-37. |
| [15] | R1KK3R. Obfuscator-LLVM[EB/OL]. https://github.com/obfuscator-LLVM/obfuscator, 2017-06-29. |
| [16] | WJQ. Armariris[EB/OL]. https://github.com/GoSSIP-SJTU/Armariris, 2019-06-03. |
| [17] | NAVILLE. HikariObfuscator[EB/OL]. https://github.com/HikariObfuscator/Hikari, 2020-01-30. |
| [18] | ZHOU Yongxin, MAIN Alec, GU Yuanxiang, et al. Information Hiding in Software with Mixed Boolean-arithmetic Transforms[EB/OL]. https://link.springer.com/chapter/10.1007/978-3-540-77535-5_5, 2007-08-27. |
| [19] | XU Hui, ZHOU Yangfan, KANG Yu, et al. Manufacturing Resilient Bi-opaque Predicates against Symbolic Execution[C]// IEEE. 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, DSN 2018, June 25-28, 2018, Luxembourg City, Luxembourg. Piscataway: Institute of Electrical and Electronics Engineers Inc., 2018: 666-677. |
| [20] | SHARIF M I, LANZI A, GIFFIN J T, et al. Impeding Malware Analysis Using Conditional Code Obfuscation[C]// NDSS. 15th Annual Network and Distributed System Security Symposium, February 10-13, 2008, San Diego, CA, USA. Reston: Internet Society, 2008: 321-333. |
| [21] | WANG Zhi, MING Jiang, JIA Chunfu, et al. Linear Obfuscation to Combat Symbolic Execution[C]// ESORICS. 16th European Symposium on Research in Computer Security, September 12-14, 2011, Leuven, Belgium. Berlin: Springer Verlag, 2011: 210-226. |
| [22] | STEPHENS J, YADEGARI B, COLLBERG C, et al. Probabilistic Obfuscation through Covert Channels[C]// IEEE. 3rd IEEE European Symposium on Security and Privacy, EURO S and P 2018, April 24-26, 2018, London, UK. Piscataway: Institute of Electrical and Electronics Engineers Inc., 2018: 243-257. |
| [23] | JIEWEIWEI. MD5[EB/OL]. https://github.com/JieweiWei/md5, 2014-10-24. |
| [24] | RSWINDELL. SHA1[EB/OL]. https://github.com/clibs/sha1, 2021-03-24. |
| [1] | 李明磊, 黄晖, 陆余良. 面向漏洞挖掘的基于符号分治区的测试用例生成技术[J]. 信息网络安全, 2020, 20(5): 39-46. |
| [2] | 陈虎, 周瑶, 赵军锁. 针对特定文件结构和关键指令的符号执行优化方法[J]. 信息网络安全, 2018, 18(9): 86-94. |
| [3] | 顾微微, 黄桂芳, 廖茂东. 代码混淆在密码协议中的应用[J]. 信息网络安全, 2017, 17(9): 81-84. |
| [4] | 王夏菁, 胡昌振, 马锐, 高欣竺. 二进制程序漏洞挖掘关键技术研究综述[J]. 信息网络安全, 2017, 17(8): 1-13. |
| [5] | 彭建山, 奚琪, 王清贤. 二进制程序整型溢出漏洞的自动验证方法[J]. 信息网络安全, 2017, 17(5): 14-21. |
| [6] | 文伟平, 张汉, 曹向磊. 基于Android可执行文件重组的混淆方案的设计与实现[J]. 信息网络安全, 2016, 16(5): 71-77. |
| [7] | 时志伟;李小军. 基于信息流分析的源代码漏洞挖掘技术研究[J]. , 2011, 11(11): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||