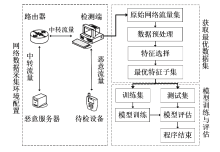
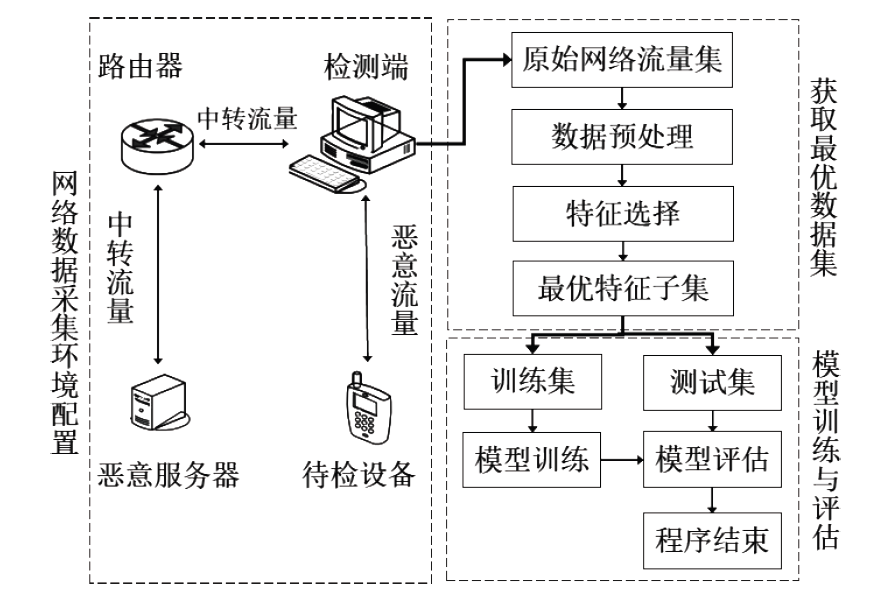
信息网络安全 ›› 2021, Vol. 21 ›› Issue (12): 9-18.doi: 10.3969/j.issn.1671-1122.2021.12.002
基于改进哈里斯鹰算法同步优化特征选择的恶意软件检测方法
- 中国刑事警察学院公安信息技术与情报学院,沈阳 110854
-
收稿日期:2021-09-26出版日期:2021-12-10发布日期:2022-01-11 -
通讯作者:徐国天 E-mail:xu_guo_tian888@163.com -
作者简介:徐国天(1978—),男,辽宁,教授,硕士,主要研究方向为网络安全及电子数据取证|刘猛猛(1997—),男,安徽,硕士研究生,主要研究方向为网络安全 -
基金资助:公安部软科学计划项目(2020LLYJXJXY031);辽宁省自然科学基金(2019-ZD-0167);辽宁省自然科学基金(20180550841);辽宁省自然科学基金(2015020091);中央高校基本科研业务费(D2021006);中央高校基本科研业务费(3242017013);公安部技术研究计划课题(2016JSYJB06);辽宁网络安全执法协同创新中心资助项目(WXZX-201807010);辽宁省教育厅科学研究经费项目(LJKZ0072);研究生创新能力提升项目(2021YCYB44)
Malware Detection Method Based on Improved Harris Hawks Optimization Synchronization Optimization Feature Selection
- College of Public Security Information Technology and Intelligence, Criminal Investigation Police University of China, Shenyang 110854, China
-
Received:2021-09-26Online:2021-12-10Published:2022-01-11 -
Contact:XU Guotian E-mail:xu_guo_tian888@163.com
摘要:
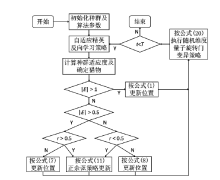
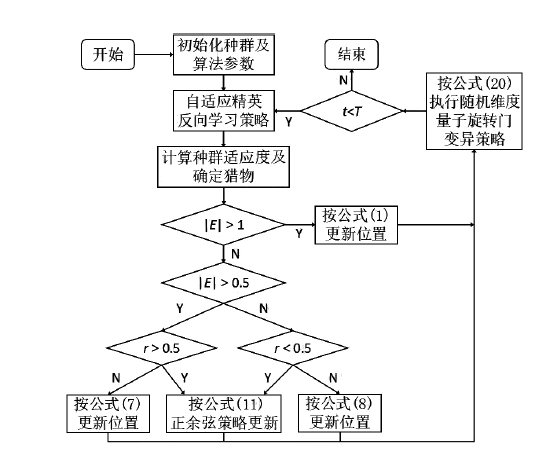
针对恶意软件检测领域存在特征选择与模型参数调优难度大的问题,文章提出一种基于改进哈里斯鹰(Improved Harris Hawks Optimization,IHHO)算法同步优化特征选择的恶意软件检测方法。首先,将自适应精英反向学习策略、正余弦位置更新方式、circle混沌能量因子以及随机维度量子旋转门变异策略引入HHO算法,增强其全局探索和局部开发能力,提升算法收敛精度和稳定性。然后,采用IHHO同步优化极端梯度提升树分类算法参数及特征选择,构建基于网络流量特征的恶意软件检测模型。最后,使用改进算法对CICInvesAndMal2019数据集进行特征子集提取与模型参数寻优仿真实验。实验结果表明,IHHO算法能选取更高质量特征子集并提升恶意软件检测模型分类能力。
中图分类号:
引用本文
徐国天, 刘猛猛. 基于改进哈里斯鹰算法同步优化特征选择的恶意软件检测方法[J]. 信息网络安全, 2021, 21(12): 9-18.
XU Guotian, LIU Mengmeng. Malware Detection Method Based on Improved Harris Hawks Optimization Synchronization Optimization Feature Selection[J]. Netinfo Security, 2021, 21(12): 9-18.
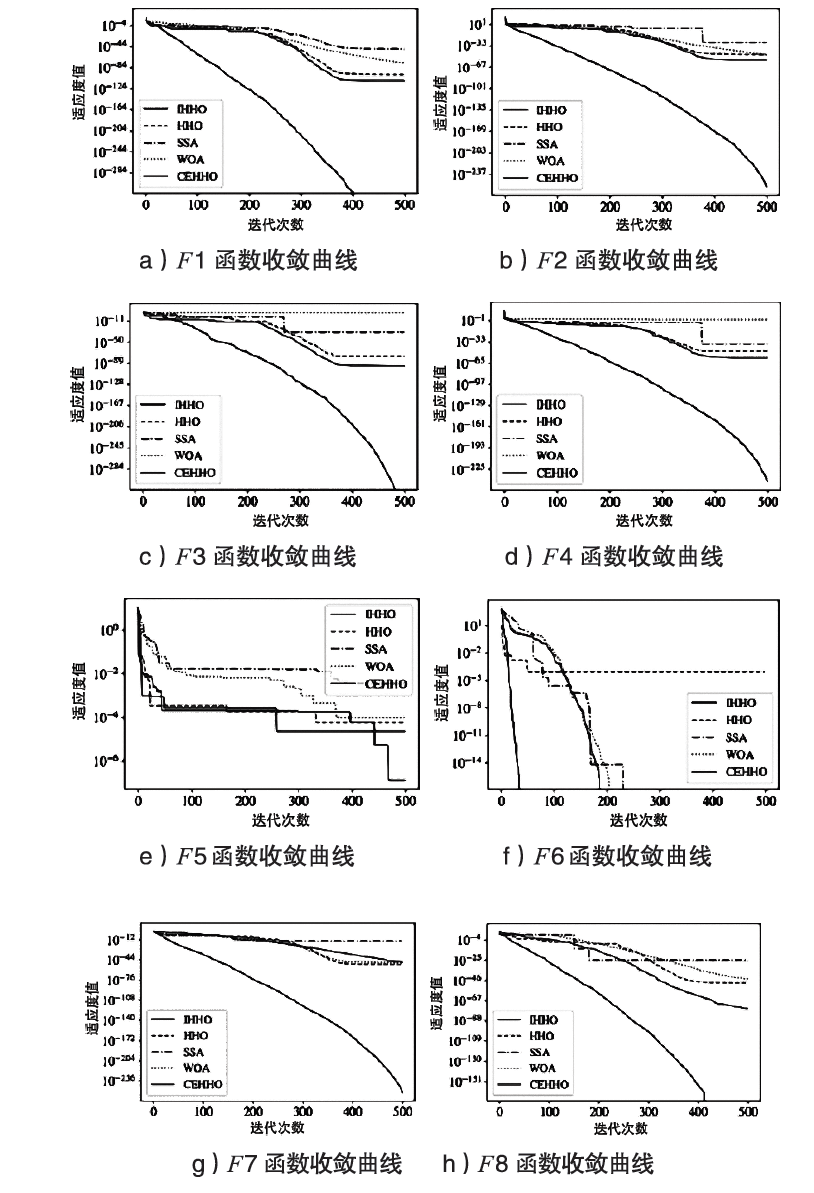
表1
基准测试函数
| 公式 | 维度 | 范围 | 最优值 |
|---|---|---|---|
| $F1\left( x \right)=\underset{i=1}{\overset{n}{\mathop \sum }}\,{{x}_{i}}^{2}$ | 30 | [-100,100] | 0 |
| $F2\left( x \right)=\underset{i=1}{\overset{n}{\mathop \sum }}\,\left| {{x}_{i}} \right|+\underset{i=1}{\overset{n}{\mathop \prod }}\,\left| {{x}_{i}} \right|$ | 30 | [-10,10] | 0 |
| $F3\left( x \right)=\underset{i=1}{\overset{n}{\mathop \sum }}\,{{\left( \underset{j=i}{\overset{i}{\mathop \sum }}\,{{x}_{j}} \right)}^{2}}$ | 30 | [-100,100] | 0 |
| $F4\left( x \right)=\text{ma}{{\text{x}}_{i}}\left\{ \left| {{x}_{i}} \right|,1\le i\le n \right\}$ | 30 | [-100,100] | 0 |
| $F5\left( x \right)=\underset{i=1}{\overset{n-1}{\mathop \sum }}\,\left[ 100{{\left( {{x}_{i+1}}-{{x}_{i}}^{2} \right)}^{2}}+{{\left( {{x}_{i}}-1 \right)}^{2}} \right]$ | 30 | [-1.28,1.28] | 0 |
| $F6\left( x \right)=\frac{1}{4000}\underset{i=1}{\overset{n}{\mathop \sum }}\,{{x}_{i}}^{2}-\underset{i=1}{\overset{n}{\mathop \prod }}\,\cos \left( \frac{{{x}_{i}}}{\sqrt{i}} \right)+1$ | 30 | [-600,600] | 0 |
| $F7\left( x \right)=\underset{i=1}{\overset{d}{\mathop \sum }}\,\left| {{x}_{i}}\text{sin}\left( {{x}_{i}} \right)+0.1{{x}_{i}} \right|$ | 30 | [-10,10] | 0 |
| $F8\left( x \right)=1-\text{cos}\left( 2\text{ }\!\!\pi\!\!\text{ }\sqrt{\underset{i=1}{\overset{d}{\mathop \sum }}\,{{x}_{i}}^{2}} \right)+0.1\sqrt{\underset{i=1}{\overset{d}{\mathop \sum }}\,{{x}_{i}}^{2}}$ | 30 | [-100,100] | 0 |
表2
算法测试结果比较
| 测试 函数 | 算法 | IHHO | HHO | SSA | WOA | CEHHO |
|---|---|---|---|---|---|---|
| F1 | Average | 0.00E+00 | 3.02E-98 | 5.11E-46 | 1.51E-71 | 9.64E-111 |
| St.d | 0.00E+00 | 1.58E-98 | 2.67E-46 | 6.92E-71 | 4.58E-111 | |
| F2 | Average | 1.71E-258 | 7.56E-50 | 6.73E-28 | 8.94E-45 | 1.24E-57 |
| St.d | 0.00E+00 | 2.10E-49 | 5.51E-28 | 2.34E-45 | 8.37E-57 | |
| F3 | Average | 0.00E+00 | 1.28E-77 | 4.35E-34 | 4.45E+04 | 3.54E-95 |
| St.d | 0.00E+00 | 7.02E-77 | 1.54E-34 | 1.53E+04 | 5.81E-95 | |
| F4 | Average | 2.96E-258 | 1.86E-47 | 8.19E-31 | 4.91E+01 | 4.96E-61 |
| St.d | 0.00E+00 | 9.19E-47 | 3.36E-31 | 3.08E+01 | 8.34E-61 | |
| F5 | Average | 5.56E-06 | 8.94E-05 | 1.70E-03 | 2.99E-03 | 8.64E-05 |
| St.d | 8.92E-07 | 9.91E-05 | 1.01E-03 | 3.20E-03 | 2.29E-05 | |
| F6 | Average | 0.00E+00 | 9.02E-05 | 0.00E+00 | 0.00E+00 | 0.00E+00 |
| St.d | 0.00E+00 | 1.85E-05 | 0.00E+00 | 0.00E+00 | 0.00E+00 | |
| F7 | Average | 2.78E-256 | 1.53E-56 | 7.35E-20 | 1.83E-46 | 3.28E-42 |
| St.d | 0.00E+00 | 5.65E-56 | 2.52E-21 | 8.89E-46 | 7.15E-42 | |
| F8 | Average | 0.00E+00 | 3.36E-49 | 5.92E-35 | 1.34E-42 | 6.06E-77 |
| St.d | 0.00E+00 | 1.38E-48 | 3.11E-35 | 6.87E-41 | 2.59E-77 |
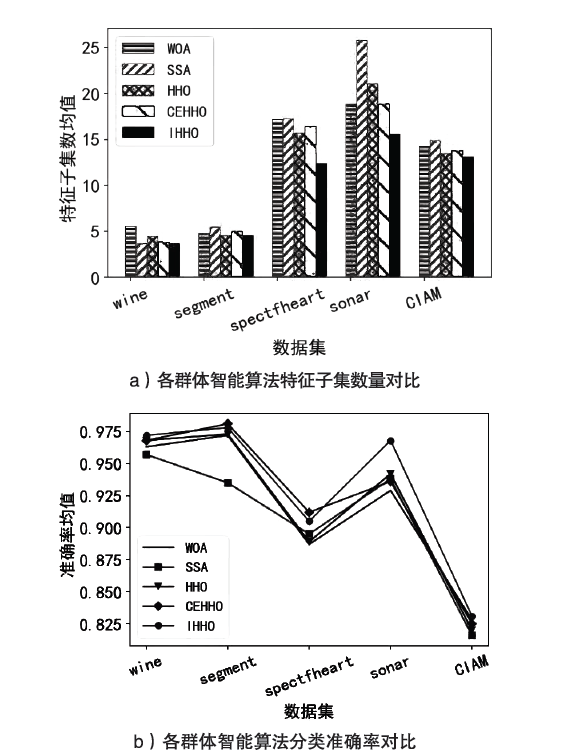
表4
不同特征选择算法对比实验
| 算法 | wine | segment | spectfheart | sonar | CICInvesAndMal | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| 特征数 | Acc | 特征数 | Acc | 特征数 | Acc | 特征数 | Acc | 特征数 | Acc | |
| 卡方 检验 | 4 | 0.907 | 5 | 0.910 | 14 | 0.814 | 15 | 0.777 | 15 | 0.725 |
| 互信 息法 | 4 | 0.907 | 5 | 0.916 | 14 | 0.839 | 15 | 0.841 | 15 | 0.786 |
| RFRFE | 4 | 0.907 | 5 | 0.919 | 14 | 0.814 | 15 | 0.809 | 15 | 0.795 |
| XGBoostF | 4 | 0.907 | 5 | 0.975 | 14 | 0.862 | 15 | 0.841 | 15 | 0.801 |
| WOA | 5.6 | 0.963 | 4.8 | 0.972 | 17.2 | 0.887 | 18.9 | 0.929 | 14.3 | 0.828 |
| SSA | 3.7 | 0.957 | 5.5 | 0.935 | 17.3 | 0.895 | 25.8 | 0.938 | 14.9 | 0.816 |
| HHO | 4.5 | 0.968 | 4.6 | 0.973 | 15.7 | 0.889 | 21.1 | 0.942 | 13.5 | 0.820 |
| CEHHO | 3.8 | 0.968 | 5.1 | 0.981 | 16.5 | 0.912 | 18.9 | 0.936 | 13.8 | 0.825 |
| IHHO | 3.7 | 0.972 | 4.6 | 0.978 | 12.4 | 0.905 | 15.6 | 0.968 | 13.2 | 0.831 |
| [1] | China Internet Network Information Center. The 48th Statistical Report on China’s Internet Development[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/202109/t20210915_71543.htm, 2021-09-15. |
| 中国互联网络信息中心. 第48次中国互联网络发展状况统计报告[EB/OL]. http://www.cnnic.net.cn/hlwfzyj/hlwxzbg/hlwtjbg/202109/t20210915_71543.htm, 2021-09-15. | |
| [2] | LI Wenjia, GE Jigang, DAI Guqian. Detecting Malware for Android Platform: an SVM-based Approach[C]// IEEE. 2015 2nd International Conference on Cyber Security and Cloud Computing, November 3-6, 2015, New Jersey, USA. New York: IEEE, 2016: 464-469. |
| [3] | ARP D, SPREITZENBARTH M, HUBNER M, et al. DREBIN: Effective and Explainable Detection of Android Malware in Your Pocket[C]// NDSS. 21st Network and Distributed System Security Symposium, February 23-26, 2014, California, USA. California: NDSS, 2014: 23-26. |
| [4] | CHAN P P K, SONG Wenkai. Static Detection of Android Malware by Using Permissions and API calls[C]// IEEE. 2014 International Conference on Machine Learning and Cybernetics, July 13-16, 2014, Lanzhou, China. New York: IEEE, 2014: 82-87. |
| [5] | YU Yuaner, ZHANG Linlin, ZHAO Kai, et al. Android Malware Family Classification Method Based on Sensitive Permissions and API[J]. Journal of Zhengzhou University(Natural Science Edition), 2020, 52(3):75-79, 91. |
| 于媛尔, 张琳琳, 赵楷, 等. 基于敏感权限和API的Android恶意软件家族分类方法[J]. 郑州大学学报(理学版), 2020, 52(3):75-79,91. | |
| [6] | XIAO Yunchang, SU Haifeng, QIAN Yucun, et al. A Behavior-based Family Clustering Method for Android Malware[J]. Journal of Wuhan University(Natural Science Edition), 2016, 62(5):429-436. |
| 肖云倡, 苏海峰, 钱雨村, 等. 一种基于行为的Android恶意软件家族聚类方法[J]. 武汉大学学报(理学版), 2016, 62(5):429-436. | |
| [7] |
SARACINO A, SCANDURRA D, DINI G, et al. MADAM: Effective and Efficient Behavior-based Android Malware Detection and Prevention[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(1):83-97.
doi: 10.1109/TDSC.2016.2536605 URL |
| [8] | HAO Jingwei, PAN Limin, LI Rui. Low Redundancy Feature Selection Method for Android Malware Detection[N]. Journal of Beijing University of Aeronautics and Astronautics, 2021-03-02(3) |
| 郝靖伟, 潘丽敏, 李蕊. Android恶意软件检测低冗余特征选择方法[N]. 北京航空航天大学学报, 2021-03-02(3). | |
| [9] | FATIMA A, MAURYA R, DUTTA M K, et al. Android Malware Detection Using Genetic Algorithm Based Optimized Feature Selection and Machine Learning[C]// IEEE. 2019 42nd International Conference on Telecommunications and Signal Processing (TSP), July 1-3, 2019, Budapest, Hungary. New York: IEEE, 2019: 220-223. |
| [10] | MOODI M, GHAZVINI M, MOODI H. A Hybrid Intelligent Approach to Detect Android Botnet Using Smart Self-adaptive Learning-based PSO-SVM[J]. Knowledge-Based Systems, 2021, 22(2):831-860. |
| [11] | JIA Heming, LI Yao, SUN Kangjian. Simultaneous Feature Selection Optimization Based on Hybrid Sooty Tern Optimization Algorithm and Genetic Algorithm[N]. Acta Automatica Sinica, 2021-09-08(9). |
| 贾鹤鸣, 李瑶, 孙康健. 基于遗传乌燕鸥算法的同步优化特征选择[N]. 自动化学报, 2021-09-08(9). | |
| [12] |
ALJARAH I, ALA’M A Z, FARIS H, et al. Simultaneous Feature Selection and Support Vector Machine Optimization Using the Grasshopper Optimization Algorithm[J]. Cognitive Computation, 2018, 10(2):478-495.
doi: 10.1007/s12559-017-9542-9 URL |
| [13] | ALABERT A, BERTI A, CABALLERO R, et al. No-free-lunch Theorems in the Continuum[J]. Theoretical Computer Science, 2015, 60(2):98-106. |
| [14] | JIAO Shan, CHONG Guoshuang, HUANG Changcheng, et al. Orthogonally Adapted Harris Hawks Optimization for Parameter Estimation of Photovoltaic Models[J]. Energy, 2020, 20(3):732-763. |
| [15] | QAIS M H, HASANIEN H M, ALGHUWAINEM S. Parameters Extraction of Three-diode Photovoltaic Model Using Computation and Harris Hawks Optimization[J]. Energy, 2020, 19(5):649-670. |
| [16] | HEIDARI A A, MIRJALILI S, FARIS H, et al. Harris Hawks Optimization: Algorithm and Applications[J]. Future Generation Computer Systems, 2019, 32(3):849-872. |
| [17] | TIZHOOSH H R. Opposition-based Learning: A New Scheme for Machine Intelligence[C]// IEEE. Proceedings of Computational Intelligence for Modelling, November 28-30, 2005, Vienna, Austria. New York: IEEE, 2005: 695-701. |
| [18] | TANG Andi, HAN Tong, XU Dengwu, et al. Chaotic elite Harris Hawks Optimization Algorithm[J]. Journal of Computer Applications, 2021, 41(8):2265-2272. |
| 汤安迪, 韩统, 徐登武, 等. 混沌精英哈里斯鹰优化算法[J]. 计算机应用, 2021, 41(8):2265-2272. | |
| [19] | TAHERI L, FITRIAH A, LASHKARI A. H. et al. Extensible Android Malware Detection and Family Classification Using Network-flows and API-Calls[C]// IEEE. 53rd International Carnahan Conference on Security Technology, October 1-3, 2019, Chennai, India. New York: IEEE, 2019: 1-8. |
| [1] | 陈庆港, 杜彦辉, 韩奕, 刘翔宇. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. |
| [2] | 徐国天, 沈耀童. 基于XGBoost和LightGBM双层模型的恶意软件检测方法[J]. 信息网络安全, 2020, 20(12): 54-63. |
| [3] | 宋鑫, 赵楷, 张琳琳, 方文波. 基于随机森林的Android恶意软件检测方法研究[J]. 信息网络安全, 2019, 19(9): 1-5. |
| [4] | 张健, 陈博翰, 宫良一, 顾兆军. 基于图像分析的恶意软件检测技术研究[J]. 信息网络安全, 2019, 19(10): 24-31. |
| [5] | 黄世锋, 郭亚军, 崔建群, 曾庆江. 基于优化模糊C均值的手机恶意软件检测[J]. 信息网络安全, 2016, 16(1): 45-50. |
| [6] | 树雅倩, 付安民, 黄振涛. 基于云平台的移动支付类恶意软件检测系统的设计与实现[J]. 信息网络安全, 2016, 16(1): 59-63. |
| [7] | 李建熠, 李晖, 黄梦媛. 基于内核日志的移动终端恶意软件检测[J]. 信息网络安全, 2015, 15(7): 58-63. |
| [8] | . 基于信息熵的网络流量信息结构特征研究[J]. , 2014, 14(3): 28-. |
| [9] | 严承华;程晋;樊攀星. 基于信息熵的网络流量信息结构特征研究[J]. , 2014, 14(3): 0-0. |
| [10] | 巫锡洪;刘宝旭;杨沛安. 基于域名的僵尸网络行为分析[J]. , 2013, 13(9): 0-0. |
| [11] | 康文丹;展鹇;白静;蔡旺. 基于行为的移动智能终端恶意软件自动化分析与检测系统[J]. , 2013, 13(12): 0-0. |
| [12] | 彭国军;王泰格;邵玉如;刘梦冷. 基于网络流量特征的未知木马检测技术及其实现[J]. , 2012, 12(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||