信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 30-41.doi: 10.3969/j.issn.1671-1122.2020.07.004
基于异常加密流量标注的Android恶意进程识别方法研究
- 中国刑事警察学院网络犯罪侦查系,沈阳 110854
-
收稿日期:2019-12-15出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:徐国天 E-mail:459536384@qq.com -
作者简介:徐国天(1978—),男,辽宁,副教授,硕士,主要研究方向为网络安全、电子物证 -
基金资助:辽宁省自然科学基金(2019-ZD-0167);辽宁省自然科学基金(2015020091);辽宁省自然科学基金(20180550841);中央高校基本科研业务费(3242017013);公安部技术研究计划(2016JSYJB06)
Android Malicious Process Identification Method Based on Abnormal Encrypted Traffic Annotation
- Cyber Crime Investigation Department, Criminal Investigation Police University of China, Shenyang 110854, China
-
Received:2019-12-15Online:2020-07-10Published:2020-08-13 -
Contact:Guotian XU E-mail:459536384@qq.com
摘要:
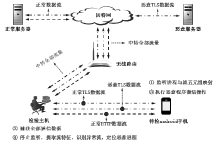
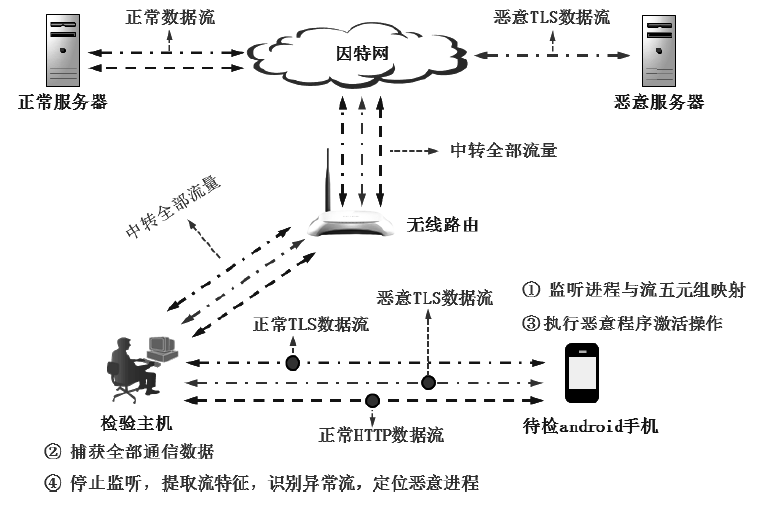
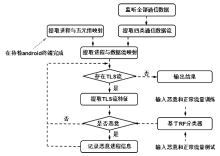
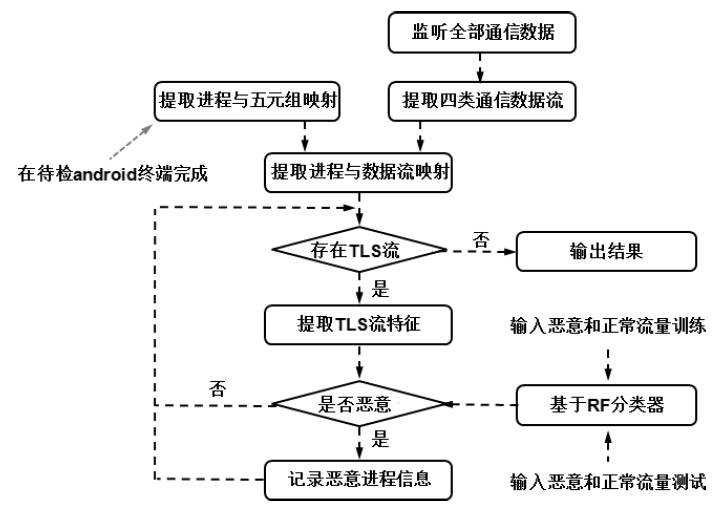
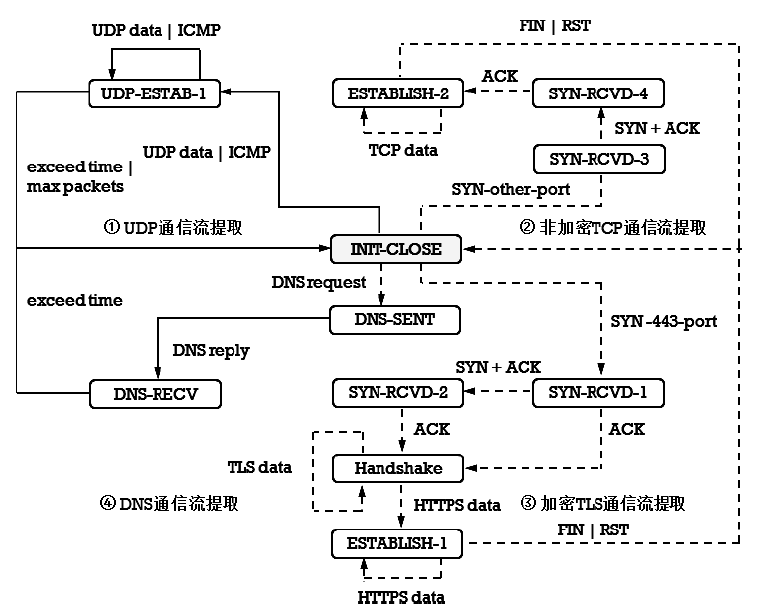
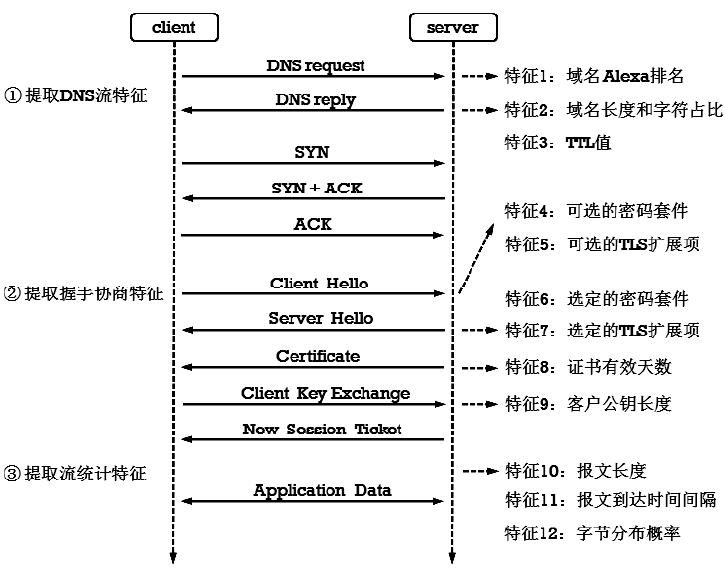
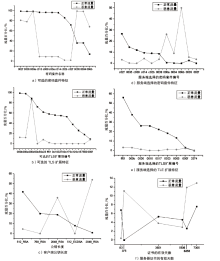
现有Android恶意样本分析方法需要提前获得待检的样本程序,当待检对象是Android智能终端而非一个样本程序时,因无法确定智能终端内哪个进程为待检恶意进程,导致样本分析法无法有效应用。现有针对恶意加密流量的检测方法可以达到较高的识别精度,但无法确定恶意流量与Android终端内恶意进程的映射关系,即无法确定恶意加密流量是由哪个进程产生的,也就不能锁定恶意进程具体位置信息。针对上述问题,文章提出一种基于异常加密流量标注的Android恶意进程识别方法,通过监听待检Android终端产生的网络通信数据,提取TLS加密通信流DNS特征、TLS握手协商特征和流统计特征,采用基于随机森林算法的二元分类器,识别恶意加密通信流;再通过提取流五元组特征值,在恶意加密通信流与Android终端进程之间建立一一映射关系,确定终端内恶意进程的具体位置。实验结果表明,该方法对复杂网络环境下未知恶意加密流量的检测精确度为97.46%,可根据检测出的恶意加密数据流定位Android终端内的恶意进程。
中图分类号:
引用本文
徐国天. 基于异常加密流量标注的Android恶意进程识别方法研究[J]. 信息网络安全, 2020, 20(7): 30-41.
XU Guotian. Android Malicious Process Identification Method Based on Abnormal Encrypted Traffic Annotation[J]. Netinfo Security, 2020, 20(7): 30-41.
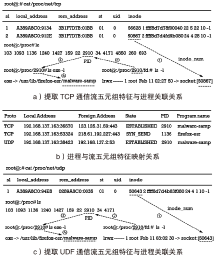
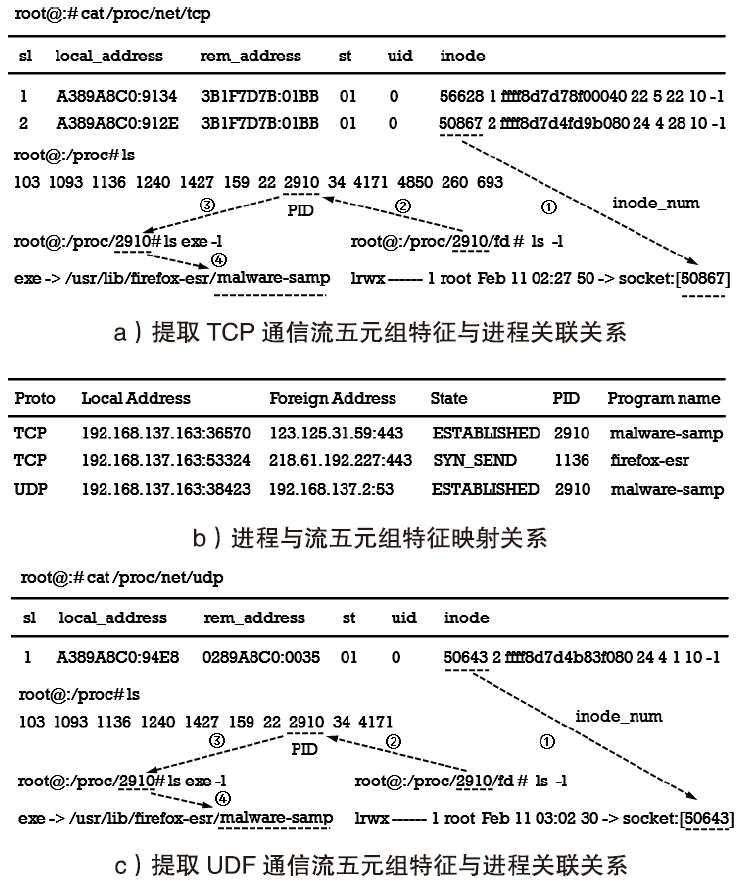
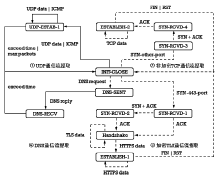
表3
进程与数据流映射表
| Proto | Local Address | Foreign Address | State | PID | Program name | Packet Num |
|---|---|---|---|---|---|---|
| TCP | 192.168.137.163:36570 | 123.125.31.59:443 | ESTABLISHED | 2910 | malware-samp | 102.103... |
| TCP | 192.168.337.163:53324 | 218.61.192.227:443 | SYN_SEND | 1136 | firefox-esr | 204 |
| UDP | 192.168.137.163:38423 | 192.168.137.2:53 | ESTABLISHED | 2910 | malware-samp | 162.164 … |
| [1] | CISCO . Cisco Encrypted Traffic Analytics White Paper[EB/OL]. https://www.cisco.com/c/en/us/solutions/enterprise-networks/enterprise-network-security/eta.html, 2019-7-1. |
| [2] | VINOD P, ZEMMARI A, CONTI M. A Machine Learning Based Approach to Detect Malicious Android Apps Using Discriminant System Calls[J]. Future Generation Computer Systems, 2019,94(6):333-350. |
| [3] |
HAN Weijie, XUE Jingfeng, WANGYong . MalDAE: Detecting and Explaining Malware Based on Correlation and Fusion of Static and Dynamic Characteristics[J]. Computers and Security, 2019,83(3):208-233.
doi: 10.1016/j.cose.2019.02.007 URL |
| [4] | ZHANG M, DUAN Y, YIN H. Semantics-aware Android Malware Classification Using Weighted Contextual API Dependency Graphs[C]// ACM. Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 1105-1116. |
| [5] | ARORA A, GARG S. Malware Detection Using Network Traffic Analysis in Android Based Mobile Devices[C]// IEEE. 2014 Eighth International Conference on Next Generation Mobile Apps, September 1-4, 2014, Oxford, United Kingdom. New York: IEEE, 2014: 66-71. |
| [6] | HU Bin, ZHOU Zhihong, YAO Lihong, et al. TLS Malicious Traffic Detection Based on Combined Features of Packet Payload and Stream Fingerprints[J]. Computer Engineering, 2019,20(10):32-41. |
| 胡斌, 周志洪, 姚立红, 等. 基于报文负载和流指纹联合特征的TLS恶意流量检测[J]. 计算机工程, 2019,20(10):32-41. | |
| [7] | BLAKE A, SUBHARTHI P, DAVID M. Deciphering Malware’s Use of TLS[J]. Journal of Computer Virology & Hacking Techniques, 2017,3(2):30-45. |
| [8] |
XIE N N, WANG X, WANG W. Fingerprinting Android Malware Families[J]. Frontiers of Computer Science, 2019,13(3):637-646.
doi: 10.1007/s11704-017-6493-y URL |
| [9] | LAYA T H, ANDI F A, ARASH H L. Extensible Android Malware Detection and Family Classification Using Network-Flows and API-Calls[J]. The IEEE(53rd) International Carnahan Conference on Security Technology, 2019,4(1):26-30. |
| [10] | ARASH H L, ANDI F A. Toward Developing A Systematic Approach to Generate Benchmark Android Malware Datasets and Classification[J]. 52nd IEEE International Carnahan Conference on Security Technology(ICCST), 2018,2(1):40-49. |
| [11] |
CAI H, MENG N, RYDER B. Droidcat: Effective Android Malware Detection and Categorization Via App-level Profiling[J]. IEEE Transactions on Information Forensics and Security, 2019,14(6):1455-1470.
doi: 10.1109/TIFS.2018.2879302 URL |
| [12] | NGUYEN , ARMITAGE . A Survey of Techniques for Internet TrafficClassification Using Machine Learning[J]. Communications Surveys & Tutorials, 2008,10(4):56-76. |
| [13] | ZANDER , NGUYEN , ARMITAGE . Automated Traffic Classificationand Application Identification Using Machine Learning[J]. The 30thIEEE Conference on Local Computer Networks, 2005,12(1):250-257. |
| [14] | LI Hao, MA Kun, CHEN Zhenxiang, et al. Unknown Malware Detection Based on Network Traffic Analysis[J]. Journal of Jinan University, 2019,33(6):500-505. |
| 李浩, 马坤, 陈贞翔, 等. 基于网络流量分析的未知恶意软件检测[J]. 济南大学学报, 2019,33(6):500-505. | |
| [15] | LI Hongling, ZHAN Yi. Statistics Analysis and Research on Common Permissions of Android Malwares[J]. Computer Technology and Development, 2017,27(11):132-136. |
| 李红灵, 詹翊. Android恶意程序常用权限分析及统计研究[J]. 计算机技术与发展, 2017,27(11):132-136. | |
| [16] | MALHOTRA A. Android Malware: Study and Analysis of Malware for Privacy Leak in Ad-hoc Network[J]. International Journal of Computer Science & Network Security, 2013,12(3):39-43. |
| [17] | LIU Xiaojian, LEI Qian, DU Xi, et al. Static Detection Approach for Android Malware Based on Multi-level Features[J]. Journal of Huazhong University of Science and Technology, 2020,48(2):1-7. |
| 刘晓建, 雷倩, 杜茜, 等. 多层次特征的Android恶意程序静态检测方法[J]. 华中科技大学学报, 2020,48(2):1-7. | |
| [18] | ENCK W, GILBERT P, HAN S. TaintDroid:An Information-flow Tracking System for Realtime Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2014,32(2):99-106. |
| [19] | ZHANG Xuetao, SUN Meng, WANG Jinshuang. Multi-Granularity Android Malware Fast Detection Based on Opcode[J]. Journal of Network and Information Security, 2019,5(6):85-94. |
| 张雪涛, 孙蒙, 王金双. 基于操作码的安卓恶意代码多粒度快速检测方法[J]. 网络与信息安全学报, 2019,5(6):85-94. | |
| [20] | WANG Run, TANG Benxiao, WANG Lina. Deeprd: Android Repackaging Application Detection Method Based on Siamese LSTM Network[J]. Journal on Communications, 2018,39(8):69-82. |
| 汪润, 唐奔宵, 王丽娜. 基于Siamese LSTM网络的Android重打包应用检测方法[J]. 通信学报, 2018,39(8):69-82. | |
| [21] |
SHABTAI A, MOSKOVITCH R, FEHER C. Detecting Unknown Malicious Code by Applying Classification Techniques on Opcode Patterns[J]. Security Informatics, 2012,1(1):1-22.
doi: 10.1186/2190-8532-1-1 URL |
| [22] | YERIMA S Y, SEZER S, MUTTIK I. High Accuracy Android Malware Detection Using Ensemble Learning[J]. Information Security, 2016,9(6):313-320. |
| [23] | XU Yichao, YUAN Qianting, XU Jian. Fine-Grained Android Malware Classification with Behavior Features[J]. Application Research of Computers, 2019,37(10):21-27. |
| 许逸超, 袁倩婷, 徐建. 基于静态行为特征的细粒度Android恶意软件分类[J]. 计算机应用研究, 2019,37(10):21-27. | |
| [24] | WEI F, LI Y, ROY S. Deep Ground TruthAnalysis of Current Android Malware[J]. International Conference on Detection of Intrusions and Malware, 2017,10(2):252-276. |
| [25] | ALLIX , BISSYANDE , KLEIN . Androzoo: Collecting Millions of Android Apps for the Research Community[J]. Mining Software Repositories, 2016,20(2):46-53. |
| [1] | 宋鑫, 赵楷, 张琳琳, 方文波. 基于随机森林的Android恶意软件检测方法研究[J]. 信息网络安全, 2019, 19(9): 1-5. |
| [2] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [3] | 段詠程, 王雨晴, 李欣, 杨乐. 基于RSAR的随机森林网络安全态势要素提取[J]. 信息网络安全, 2019, 19(7): 75-81. |
| [4] | 张蕾华, 牛红太, 王仲妮, 刘雪红. 基于大数据的前科人员犯罪预警模型构建研究[J]. 信息网络安全, 2019, 19(4): 82-89. |
| [5] | 翟继强, 肖亚军, 杨海陆, 王健. 改进的人工蜂群结合优化的随机森林的U2R攻击检测研究[J]. 信息网络安全, 2018, 18(12): 38-45. |
| [6] | 项川, 潘无穷, 黎火荣, 林璟锵. 支持商密算法TLS浏览器的设计与实现[J]. 信息网络安全, 2017, 17(4): 26-33. |
| [7] | 林伟宁, 陈明志, 詹云清, 刘川葆. 一种基于PCA和随机森林分类的入侵检测算法研究[J]. 信息网络安全, 2017, 17(11): 50-54. |
| [8] | 马跃鹏, 刘吉强, 王健. 基于缓存命中的DPI系统预处理方法[J]. 信息网络安全, 2016, 16(10): 69-75. |
| [9] | . 基于随机森林算法的网络舆情文本信息分类方法研究[J]. , 2014, 14(11): 36-. |
| [10] | 吴坚, 沙晶. 基于随机森林算法的网络舆情文本信息分类方法研究[J]. 信息网络安全, 2014, 15(11): 36-40. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||