信息网络安全 ›› 2020, Vol. 20 ›› Issue (7): 42-52.doi: 10.3969/j.issn.1671-1122.2020.07.005
一种基于软件定义网络的主机指纹抗探测模型
- 1.信息工程大学网络空间安全学院,郑州 450001
2.数学工程与先进计算国家重点实验室,郑州 450001
-
收稿日期:2019-12-15出版日期:2020-07-10发布日期:2020-08-13 -
通讯作者:张涛 E-mail:1019032076@qq.com -
作者简介:张涛(1995—),男,山东,硕士研究生,主要研究方向为信息安全、移动目标防御|芦斌(1981—),男,山西,副教授,博士,主要研究方向为人工智能、网络空间安全|李玎(1992—),男,河南,博士研究生,主要研究方向为网络与信息安全、流量分析|何康(1992—),男,山东,博士研究生,主要研究方向为深度学习、网络空间安全 -
基金资助:国家自然科学基金(61601517)
A Host Fingerprint Anti-detection Model Based on SDN
ZHANG Tao1,2( ), LU Bing1,2, LI Ding1,2, HE Kang1,2
), LU Bing1,2, LI Ding1,2, HE Kang1,2
- 1. Cyberspace Security Institute, Information Engineering University, Zhengzhou 450001, China
2. State Key Laboratory of Mathematical Engineering and Advanced Computing, Zhengzhou 450001, China
-
Received:2019-12-15Online:2020-07-10Published:2020-08-13 -
Contact:Tao ZHANG E-mail:1019032076@qq.com
摘要:
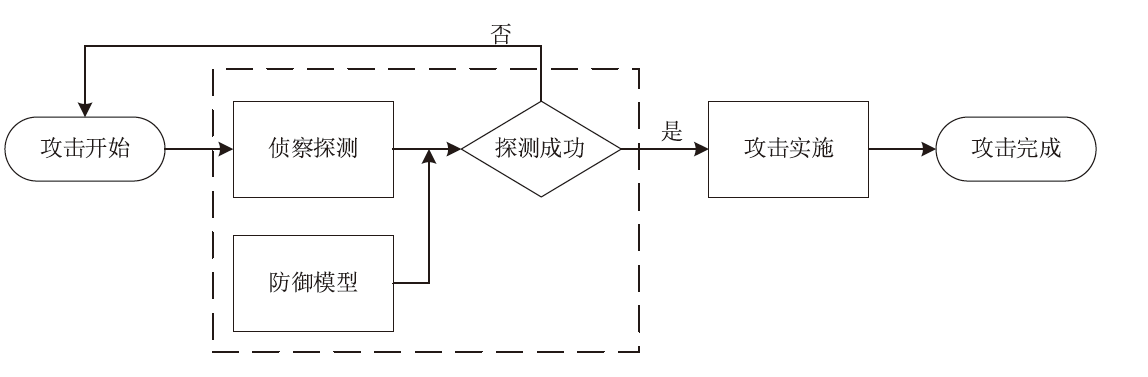
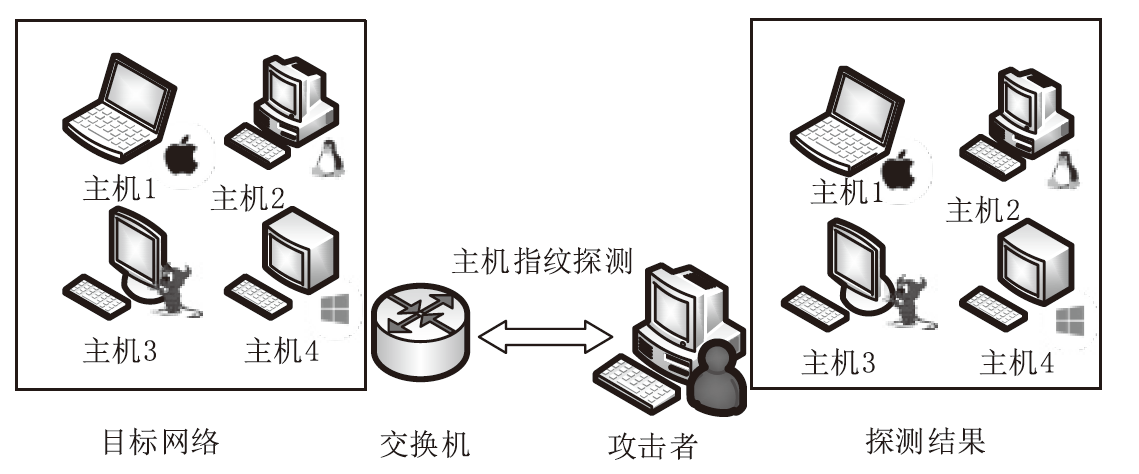
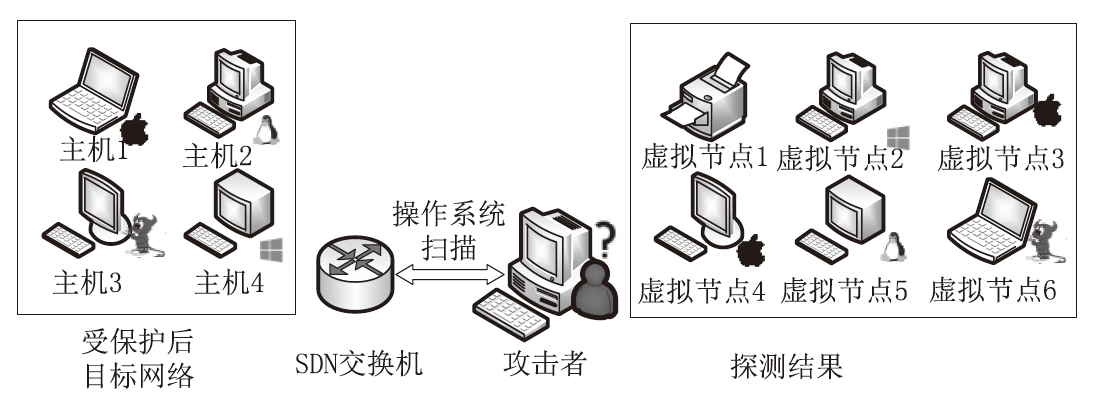
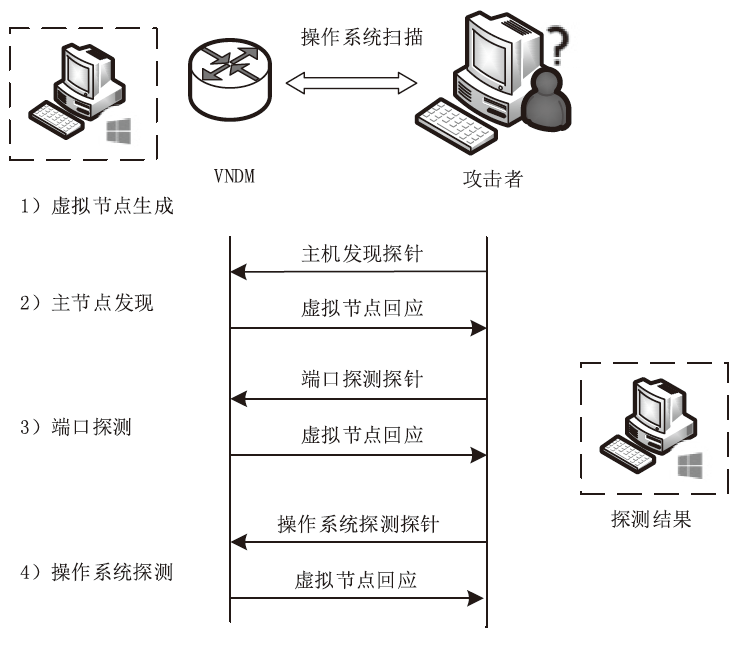
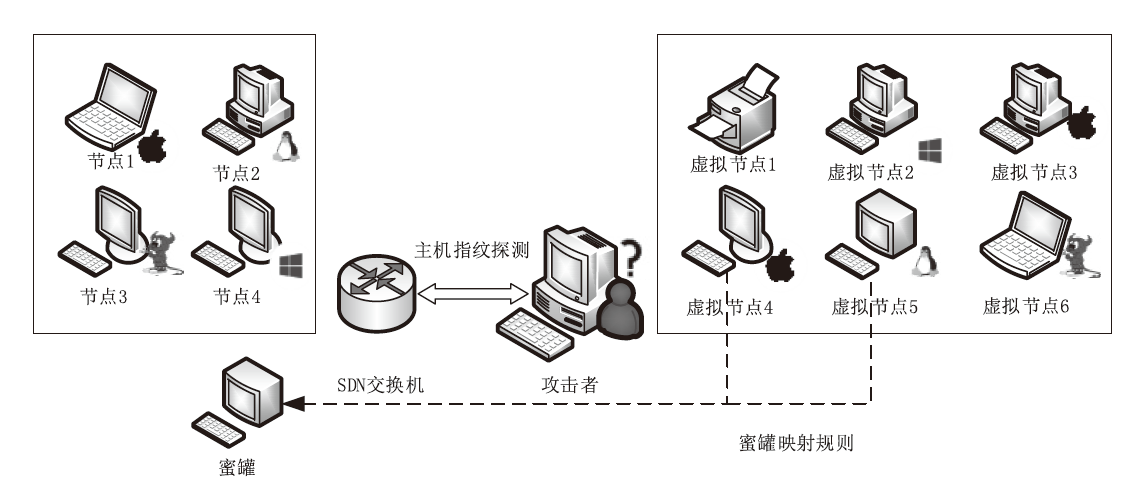
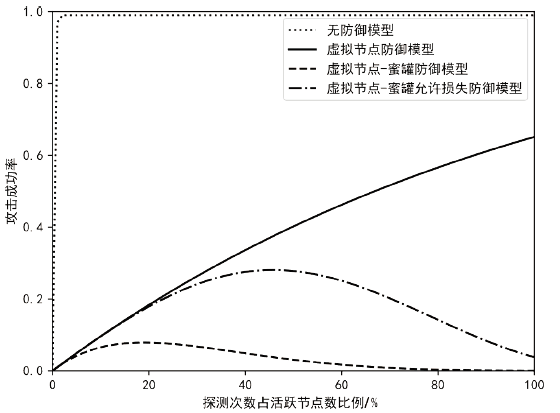
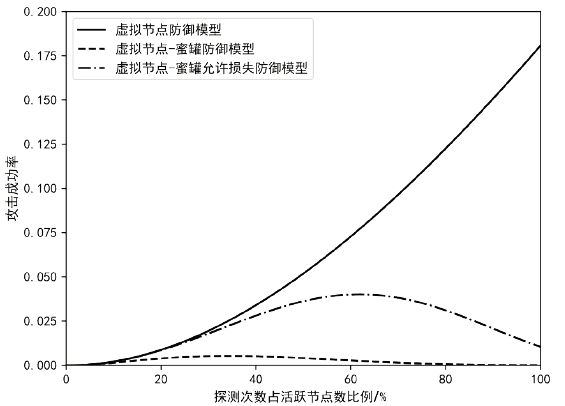
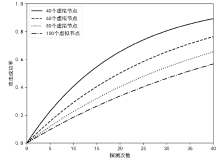
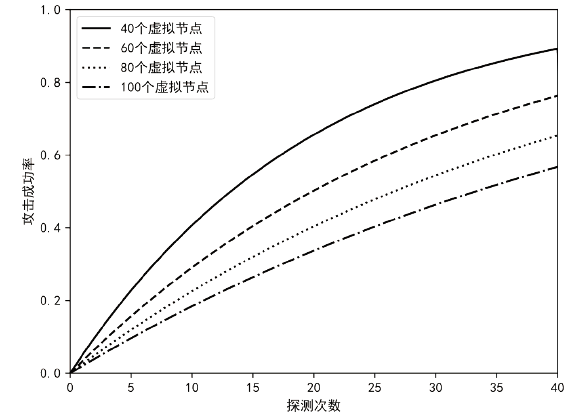
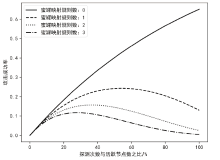
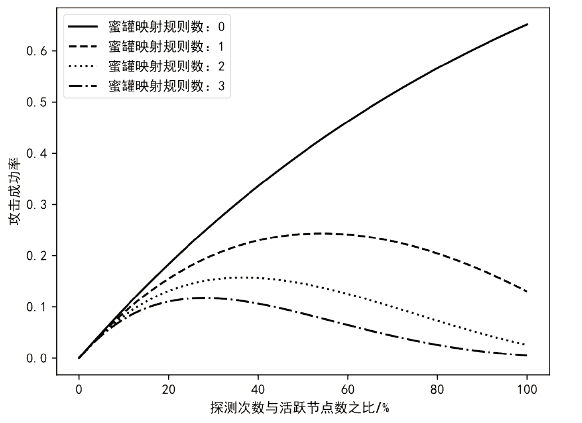
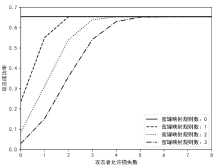
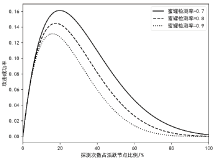
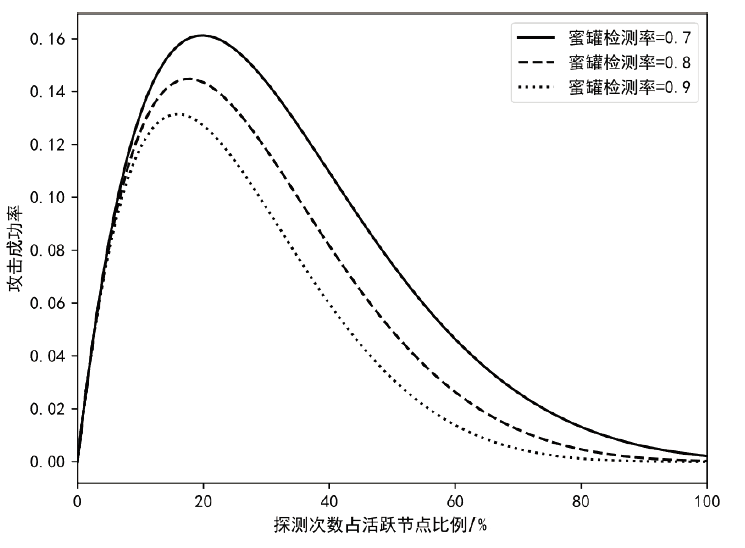
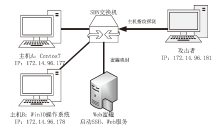
针对主机指纹探测防御困难的问题,文章提出基于软件定义网络的主机指纹抗探测模型。模型构造包含虚假指纹信息的虚拟节点,通过识别指纹探针,按照指纹模板构造响应报文,实现对指纹探测攻击的欺骗。随后提出蜜罐映射与流量牵引技术,结合蜜罐技术将指向虚拟节点的攻击流量重定向到蜜罐,实现对攻击行为的捕获分析。为了分析模型对网络安全带来的收益,建立该模型防御效能的概率模型,量化了探测次数、虚拟节点数量、蜜罐映射规则数、允许损失数、虚拟节点欺骗率和蜜罐检测率等参数对攻击成功概率的影响。最后结合DPDK技术基于X86平台搭建原型系统,实验结果表明该模型与典型的抗识别工具IPMorph相比具备更高的欺骗成功率,且带来的额外性能开销低于5%。
中图分类号:
引用本文
张涛, 芦斌, 李玎, 何康. 一种基于软件定义网络的主机指纹抗探测模型[J]. 信息网络安全, 2020, 20(7): 42-52.
ZHANG Tao, LU Bing, LI Ding, HE Kang. A Host Fingerprint Anti-detection Model Based on SDN[J]. Netinfo Security, 2020, 20(7): 42-52.
表1
指纹探测结果
| 命令 | IP | MAC | 操作 系统 | 端口 | 网络距离 |
|---|---|---|---|---|---|
| 2019/12/13 9:20 nmap -O 172.14.96.0/24 | 172.14. 96.177 | 00:21:85:FD: C1:D2 | Linux 2.7.3 | 80/443/1025/ 8080 | 1 |
| 172.14. 96.178 | 8C:89:A5:0F: 17:D4 | Windows 10 | 23/443/3389 | 1 | |
| 172.14. 96.179 | 00:21:CC:CD: 24:37 | Linux 3.10 | 22/80/8080 | 1 | |
| 172.14. 96.181 | 2C:53:4A:03: CF:BC | Windows 7 | 22/23/3389 | 0 | |
| 2019/12/13 9:37 nmap -O 172.14.96.0/24 | 172.14. 96.177 | 08:00:CD:68: 31:38 | Windows Server 2012 R2 Update1 | 22/110/3389/ 1433 | 1 |
| 172.14. 96.178 | 8C:89:A5:0F: 17:D4 | Windows 10 | 23/443/3389 | 1 | |
| 172.14. 96.179 | 00:21:CC:CD: 24:37 | Linux 3.10 | 22/80/8080 | 1 | |
| 172.14. 96.181 | 2C:53:4A:03: CF:BC | Windows 7 | 22/23/3389 | 0 |
| [1] | ZHUANG R, DELOACH S A, OU X. Towards A Theory of Moving Target Defense[C]// ACM. Proceedings of the First ACM Workshop on Moving Target Defense, November 3, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 31-40. |
| [2] | DAVID J, THOMAS C. Efficient DDoS Flood Attack Detection Using Dynamic Thresholding on Flow-based Network Traffic[J]. Computers & Security, 2019,82(7):284-295. |
| [3] | SHAMSI Z, NANDWANI A, LEONARD D, et al. Hershel: Single-Packet OS Fingerprinting[J]. ACM SIGMETRICS Performance Evaluation Review, 2014,42(1):195-206. |
| [4] | PRIGENT G, VICHOT F, HARROUET F. IpMorph: Fingerprinting Spoofing Unification[J]. Journal in Computer Virology, 2010,6(4):329-342. |
| [5] | MA Junliang, WANG Xili, HE Juhou, et al. Research and Design of Enhanced Anti-Xprobe2[J]. Computer Engineering and Applications, 2012,48(32):1-4. |
| 马君亮, 汪西莉, 何聚厚, 等. 增强型Anti-Xprobe2的研究与设计[J]. 计算机工程与应用, 2012,48(32):1-4. | |
| [6] | KAMPANAKIS P, PERROS H, BEYENE T. SDN-based Solutions for Moving Target Defense Network Protection[C]// IEEE. The Fifteenth International Symposium on a World of Wireless, Mobile and Multimedia Networks, Jun 16-19, 2014, Sydney, Australia. New York: IEEE, 2014: 1-6. |
| [7] | JIA Zhaopeng. Research on Defense Oriented Network Spoofing Technology[D]. Beijing: Beijing University of Posts and Telecommunications, 2018. |
| 贾召鹏. 面向防御的网络欺骗技术研究[D]. 北京:北京邮电大学, 2018. | |
| [8] | HAN W, ZHAO Z, DOUPÉ A, et al. Honeymix: Toward Sdn-based Intelligent Honeynet[C]// ACM. Proceedings of the 2016 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization, March 9-11, 2016, New Orleans Louisiana USA. New York: ACM, 2016: 1-6. |
| [9] | LA Q D, QUEK T Q S, LEE J, et al. Deceptive Attack and Defense Game in Honeypot-enabled Networks for the Internet of Things[J]. IEEE Internet of Things Journal, 2016,3(6):1025-1035. |
| [10] | FAN W, DU Z, CREASEY M, et al. HoneyDOC: An Efficient Honeypot Architecture Enabling all-round Design[J]. IEEE Journal on Selected Areas in Communications, 2019,37(3):683-697. |
| [11] | SHI L, LI Y, LIU T, et al. Dynamic Distributed Honeypot Based on Blockchain[EB/OL]. https://ieeexplore.ieee.org/document/8727529, 2019-11-15. |
| [12] | JAFARIAN J H, NIAKANLAHIJI A, AL-SHAER E, et al. Multi-dimensional Host Identity Anonymization for Defeating Skilled Attackers[C]// ACM. Proceedings of the 2016 ACM Workshop on Moving Target Defense, October 24, 2018, Vienna, Austria. New York: ACM, 2016: 47-58. |
| [13] | ZHUGE Jianwei, TANG Yong, HAN Xinhui, et al. Honeypot Technology Research and Application[J]. Journal of Software, 2013,24(4):825-842. |
| 诸葛建伟, 唐勇, 韩心慧, 等. 蜜罐技术研究与应用进展[J]. 软件学报, 2013,24(4):825-842. | |
| [14] | LI Yan. Design and Implementation of Honeynet Active Defense System Based on SDN[D]. Beijing: Beijing University of Posts and Telecommunications, 2019 |
| 李俨. 基于SDN的蜜网主动防御系统设计与实现[D]. 北京:北京邮电大学, 2019. | |
| [15] | BONFIM M S, DIAS K L, FERNANDES S F L. Integrated NFV/SDN Architectures: A Systematic Literature Review[J]. ACM Computing Surveys (CSUR), 2019,51(6):1-39. |
| [16] | HERWIG S, HARVEY K, HUGHEY G, et al. Measurement and Analysis of Hajime, A Peer-to-peer IoT Botnet[EB/OL]. http://www.cs.umd.edu/~smherwig/pub/18-imc/hajime-poster.pdf, 2019-10-15. |
| [17] | CERON J M, STEDING J K, HOEPERS C, et al. Improving Iot Botnet Investigation Using An Adaptive Network Layer[J]. Sensors, 2019,19(3):727. |
| [18] | PONGRÁCZ G, MOLNÁR L, KIS Z L. Removing Roadblocks from SDN: OpenFlow Software Switch Performance on Intel DPDK[C]// IEEE. 2013 Second European Workshop on Software Defined Networks, October 10-11, 2013, Berlin, Germany. New York: IEEE, 2013: 62-67. |
| [1] | 郭亚军, 蒲东齐. 基于蜜罐加密算法的个人隐私数据保护[J]. 信息网络安全, 2019, 19(12): 38-46. |
| [2] | 张京京;闫晓蔚;唐薇;蔡建顺. 基于蜜罐技术的垃圾邮件搜集系统设计与实现[J]. , 2013, 13(5): 0-0. |
| [3] | 徐娜;周勇林. 大规模分布式蜜网技术研究与应用[J]. , 2013, 13(3): 0-0. |
| [4] | 李秋锐. 基于蜜罐网络的邮件捕获系统分析与部署[J]. , 2012, 12(1): 0-0. |
| [5] | 贾保先;谢圣献. 基于本体和上下文感知的主动式计算机犯罪取证模型设计研究[J]. , 2012, 12(1): 0-0. |
| [6] | 孙国梓;薛磊;李云. 一种基于蜜罐技术的主机取证系统研究[J]. , 2010, (12): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||