信息网络安全 ›› 2020, Vol. 20 ›› Issue (6): 26-35.doi: 10.3969/j.issn.1671-1122.2020.06.004
大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议
- 1.江南大学物联网工程学院,无锡 214122
2.江南大学物联网技术应用教育部工程研究中心,无锡 214122
-
收稿日期:2020-02-21出版日期:2020-06-10发布日期:2020-10-21 -
通讯作者:孙子文 E-mail:sunziwen@jiangnan.edu.cn -
作者简介:孙子文(1968—),女,江苏,教授,博士,主要研究方向为无线传感网络理论与技术、信息安全等|张向阳(1995—),女,安徽,硕士研究生,主要研究方向为信息安全 -
基金资助:国家自然科学基金(61373126);江苏省自然科学基金(BK20131107);中央高校基本科研业务费专项资金(JUSRP51310A)
Large-scale Mobile RFID System Shamir’s Key Sharing PUF Security Authentication Protocol
SUN Ziwen1,2( ), ZHANG Xiangyang1
), ZHANG Xiangyang1
- 1. School of Internet of Things Engineering, Jiangnan University, Wuxi 214122, China
2. Engineering Research Center of Internet of Things Technology Applications of Ministry of Education, Jiangnan University, Wuxi 214122, China
-
Received:2020-02-21Online:2020-06-10Published:2020-10-21 -
Contact:SUN Ziwen E-mail:sunziwen@jiangnan.edu.cn
摘要:
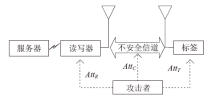
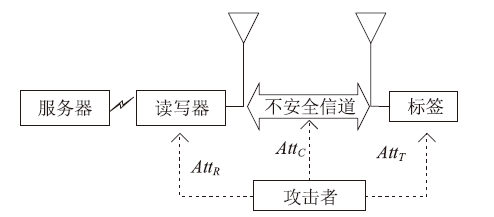
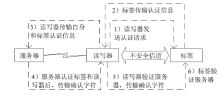
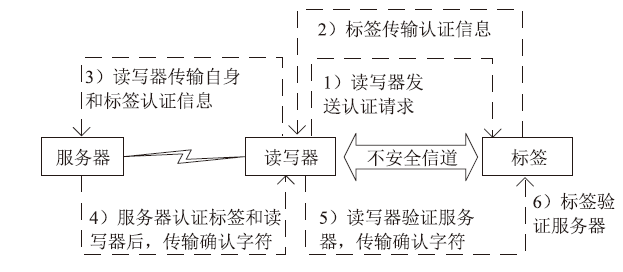
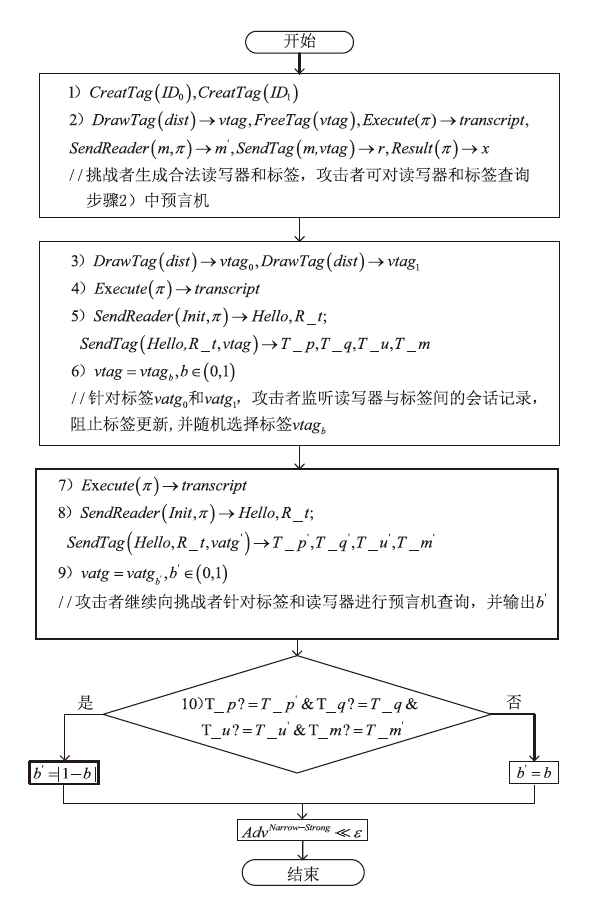
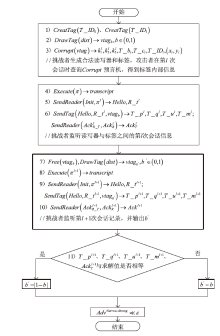
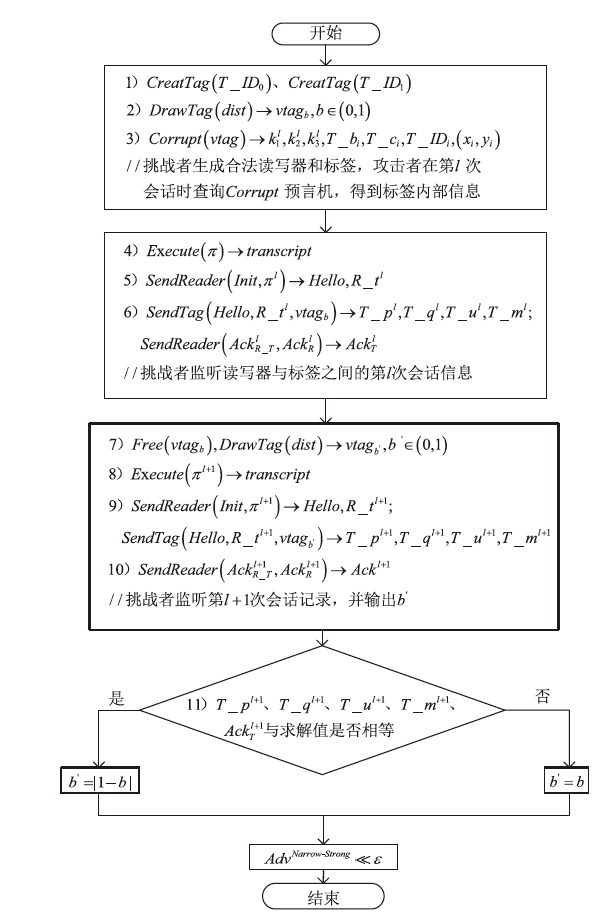
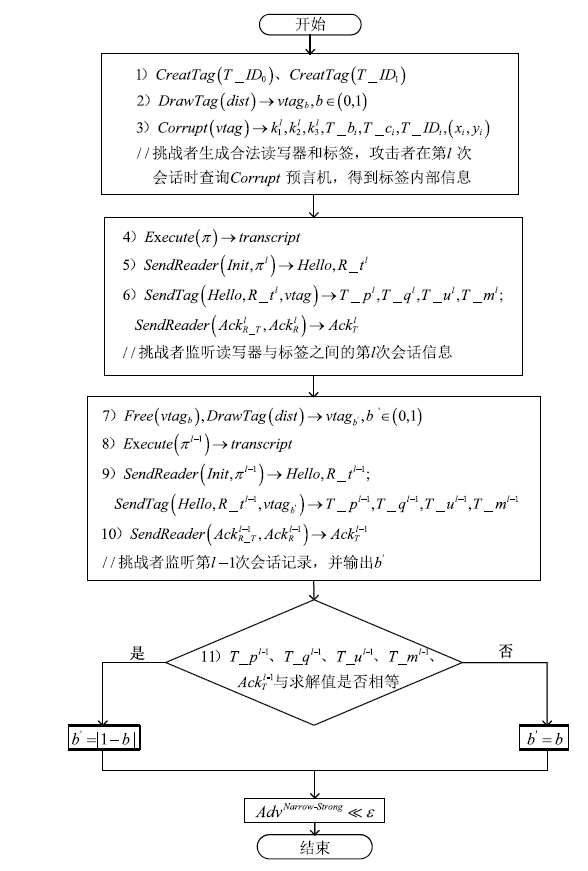
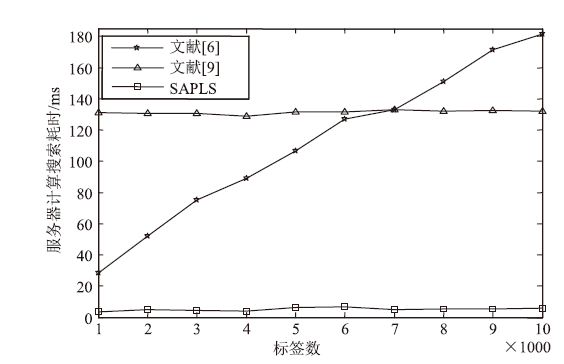
针对大规模移动无线射频识别(RFID)系统多样且存在严重的安全隐患问题,文章研究了一种Shamir’s密钥共享安全认证协议。该协议采用物理不可克隆函数(PUF)两步生成会话密钥机制,可避免标签和读写器遭受物理入侵带来的假冒攻击;服务器端对读写器合法性进行认证,以适用于移动RFID系统的应用场景;采用时间戳阈值与更新机制抵御重放攻击;采用Shamir’s密钥共享方案,降低服务器搜索计算开销,适用于大规模RFID系统。文章改进Vaudenay模型预假设,对认证协议进行安全和隐私性分析证明,结果表明,该协议可抵抗多种攻击。使用C#语言对服务器认证耗时进行对比实验,结果表明,该协议服务器认证耗时较其他协议具有明显优势,能够满足大规模移动RFID系统的应用要求。
中图分类号:
引用本文
孙子文, 张向阳. 大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议[J]. 信息网络安全, 2020, 20(6): 26-35.
SUN Ziwen, ZHANG Xiangyang. Large-scale Mobile RFID System Shamir’s Key Sharing PUF Security Authentication Protocol[J]. Netinfo Security, 2020, 20(6): 26-35.
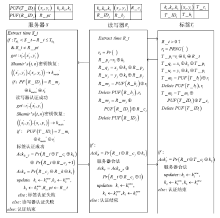
表1
符号注释表
| 符号 | 注释 |
|---|---|
| ${{R}_{j}}/{{T}_{i}}/S$ | 第$j$个读写器/第$i$个标签/服务器 |
| $T\_I{{D}_{i}}/R\_I{{D}_{j}}$ | 第$i$个标签/第$j$个读写器标识符 |
| $({{x}_{j}},{{y}_{j}})/({{x}_{i}},{{y}_{i}})/({{x}_{s}},{{y}_{s}})/{{k}_{main}}$ | 第$j$个读写器/第$i$个标签/服务器中影子密钥对/主密钥 |
| $PUF()$ | PUF运算 |
| $R\_t/S\_t$ | 读写器发起认证时刻的时间戳/服务器接收认证信息时刻的时间戳 |
| $PRNG()$ | 伪随机数生成器 |
| ${{r}_{1}},{{r}_{2}}$ | 随机数 |
| ${{k}_{1}},{{k}_{2}},{{k}_{3}}$ | 共享密钥 |
表2
Vaudenay模型预言机介绍
| 预言机 | 功能介绍 |
|---|---|
| $CreatTag\left( IDS \right)$ | 生成唯一标识符为$IDS$的标签 |
| $DrawTag\left( dist \right)\to vtag$ | 按照分配概率函数$dist$随机选择标签,为标签分配临时标识$vtag$ |
| $FreeTag\left( vtag \right)$ | 释放$vtag$标签 |
| $E\text{x}ecute\left( \pi \right)\to transcript$ | 执行协议实例$\pi $,返回会话记录$transcript$ |
| $Launch\left( {} \right)\to \pi $ | 读写器重新启动认证协议实例$\pi $ |
| $SendReader\left( m,\pi \right)\to m'$ | 读写器接收消息$m$,输出消息$m'$ |
| $SendTag\left( m,\pi \right)\to m'$ | 标签$T$接收到消息$m$,输出消息$m'$ |
| $Result\left( \pi \right)\to x$ | 协议实例$\pi $成功,返回1,否则返回0 |
| $Corrupt\left( vtag \right)$ | 攻击者入侵窃取标签$vtag$内部消息 |
| [1] | BONO S, GREEN M, STUBBLEFIELD A, et al. Security Analysis of a Cryptographically-enabled RFID Device[EB/OL]. https://www.researchgate.net/publication/228651694_Security_analysis_of_a_cryptographically-enabled_RFID_device, 2019 -8-9. |
| [2] | DOSS R, SUNDARESAN S, ZHOU W. Apractical Quadratic Residues Based Scheme for Authentication and Privacy in Mobile RFID Systems[J]. Ad Hoc Networks, 2013,11(1):383-396. |
| [3] | YANG Yulong, PENG Changgen, ZHOU Zhou. Mobile RFID Security Authentication Protocol Based on Edwards Curve[J]. Journal of Communications, 2014,35(11):132-137. |
| 杨玉龙, 彭长根, 周洲, 等. 基于Edwards曲线的移动RFID安全认证协议[J]. 通信学报, 2014,35(11):132-137. | |
| [4] | SANDHYA M, RANGASWAMY T R. A Secure and Effecient Authentication Protocol for Mobile RFID Systems[J]. Journal of Digital Information Management, 2011,9(3):99-105. |
| [5] | LIU Peng, ZHANG Changhong, OU Qingyu. Hash Function-based Mobile Radio Frequency Identification Mutual Authentication Security Protocol Involves[J]. Computer Application, 2013,33(5):1350-1352. |
| 刘鹏, 张昌宏, 欧庆于. 基于Hash函数的移动射频识别互认证安全协议涉及[J]. 计算机应用, 2013,33(5):1350-1352. | |
| [6] | WANG Guowei, JIA Zongpu, PENG Weiping. Mobile RFID Two-way Authentication Protocol Based on Dynamic Shared Key[J]. Journal of Electronics, 2017,45(3):612-618. |
| 王国伟, 贾宗璞, 彭维平. 基于动态共享密钥的移动RFID双向认证协议[J]. 电子学报, 2017,45(3):612-618. | |
| [7] | SUN Ziwen, LI Song. Lightweight RFID Mobile Authentication Protocol Using PUF to Protect Location Privacy[J]. Computer Science and Exploration, 2019,13(3):418-428. |
| 孙子文, 李松. 采用PUF保护位置隐私的轻量级RFID移动认证协议[J]. 计算机科学与探索, 2019,13(3):418-428. | |
| [8] | PAPPU R. Physical One-way Function[EB/OL]. https://www.docin.com/p-1684681622.html, 2019 -8-11. |
| [9] | CHIOU S Y, CHANG S Y. An Enhanced Authentication Scheme in Mobile RFID System[EB/OL]. https://www.researchgate.net/publication/321861476_An_Enhanced_Authentication_Scheme_in_Mobile_RFID_System, 2019 -8-12. |
| [10] | RONG Huigui, MO Jinxia, CHANG Bingguo, et al. Key Distribution and Recovery Algorithm Based on Shamir Secret Sharing[J]. Journal of Communications, 2015,36(3):60-69. |
| 荣辉桂, 莫进侠, 常炳国, 等. 基于Shamir秘密共享的密钥分发与恢复算法[J]. 通信学报, 2015,36(3):60-69. | |
| [11] | VAUDENAY S. On privacy models for RFID[M]. Advances in Cryptology-ASIACRYPT 2007. Heidelberg: Springer, 2007: 68-87. |
| [12] | SHAMIR A. How to Share A Secret[J]. Communications of the ACM, 1979,22(11):612-613. |
| [13] | LIU Y, EZERMAN M F, WANG H. Double Verification Protocol via Secret Sharing for Low-cost RFID Tags[EB/OL]. https://www.onacademic.com/detail/journal_1000040419206110_45fd.html, 2019 -8-11. |
| [14] | ARMKNECHT F, MAES R, SADEGHI A, et al. A Formalization of the Security Features of Physical Functions [C]// 2011 IEEE Symposium. Security and Privacy, May 22-25, 2011, Berkeley, CA, USA. New Jersey: IEEE, 2011: 397-412. |
| [15] | LI Changting, ZHANG Qinglong, LIU Zongbin. FROPUF: Extract More Entropy from FPGA-based Oscillator Ring PUF[J]. Journal of Information Security, 2018,3(1):16-30. |
| [16] | ALAGHEBAND M R, AREF M R. Simulation-based Traceability Analysis of RFID Authentication Protocols[M]. California: Kluwer Academic Publishers, 2014. |
| [1] | 沈金伟, 赵一, 梁春林, 张萍. 基于循环分组的RFID群组标签所有权转移协议[J]. 信息网络安全, 2020, 20(9): 102-106. |
| [2] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [3] | 韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 19(12): 64-71. |
| [4] | 张小红, 郭焰辉. 基于椭圆曲线密码的RFID系统安全认证协议研究[J]. 信息网络安全, 2018, 18(10): 51-61. |
| [5] | 李智聪, 周治平. 物联网中增强安全的RFID认证协议[J]. 信息网络安全, 2018, 18(1): 80-87. |
| [6] | 王萍, 周治平. 一种基于云的RFID所有权转移协议的改进[J]. 信息网络安全, 2017, 17(8): 60-68. |
| [7] | 杨玉龙, 彭长根, 郑少波, 朱义杰. 基于移动智能终端的超轻量级移动RFID安全认证协议[J]. 信息网络安全, 2017, 17(5): 22-27. |
| [8] | 马庆, 郭亚军, 曾庆江, 徐铎. 一种新的超轻量级RFID双向认证协议[J]. 信息网络安全, 2016, 16(5): 44-50. |
| [9] | 张玉婷, 严承华. 一种基于双向认证协议的RFID标签认证技术研究[J]. 信息网络安全, 2016, 16(1): 64-69. |
| [10] | 杨元原, 陆臻, 顾健. RFID安全协议追踪攻击的形式化分析[J]. 信息网络安全, 2015, 15(9): 25-28. |
| [11] | 李飞, 刘宗斌, 章庆隆, 林璟锵. DSP平台上基于PUF的两种真随机数产生方法研究[J]. 信息网络安全, 2015, 15(9): 186-190. |
| [12] | 吴潇, 常成, 覃文杰, 程久军. 基于RFID和数字水印技术的标签防伪验证方法[J]. 信息网络安全, 2015, 15(8): 26-34. |
| [13] | 吴海兵;孙玉绘;刘迅;张旭东. 基于RFID的校车人员安全管理系统[J]. , 2013, 13(2): 0-0. |
| [14] | 胡国胜;方龙雄. RFID系统安全分析[J]. , 2013, 13(2): 0-0. |
| [15] | 王秋晨;王雷;夏鲁宁. 基于RFID的移动存储设备安全管控方案[J]. , 2013, 13(10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||