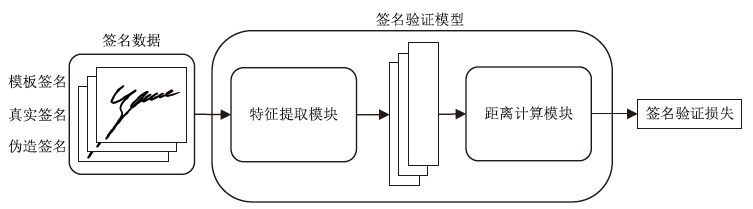
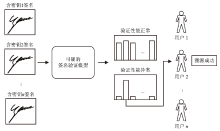
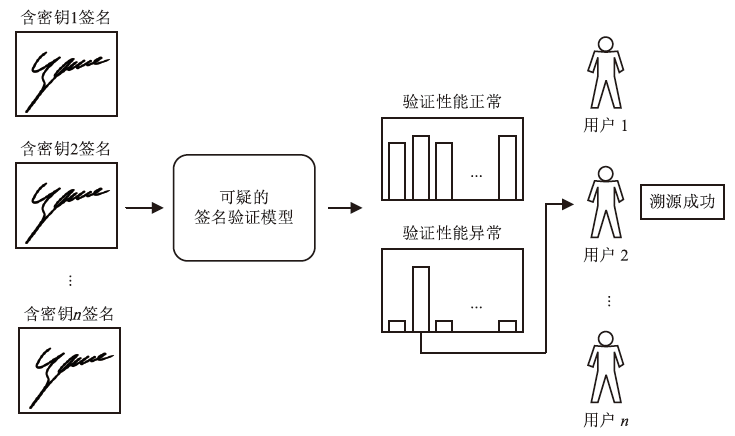
信息网络安全 ›› 2025, Vol. 25 ›› Issue (12): 1927-1935.doi: 10.3969/j.issn.1671-1122.2025.12.008
基于对比学习的动态手写签名验证模型保护方法
- 1.南京信息工程大学数字取证教育部工程研究中心,南京 210044
2.南京信息工程大学计算机学院,南京 210044
3.南京信息工程大学网络空间安全学院,南京 210044
-
收稿日期:2025-10-10出版日期:2025-12-10发布日期:2026-01-06 -
通讯作者:付章杰 E-mail:fzj@nuist.edu.cn -
作者简介:付章杰(1983—),男,河南,教授,博士,CCF会员,主要研究方向为人工智能安全、深度伪造取证和区块链安全|陈天宇 (2001—),男,江苏,硕士研究生,主要研究方向为信息隐藏|崔琦(1994—),男,辽宁,副教授,博士,主要研究方向为信息隐藏、深度学习模型安全 -
基金资助:国家自然科学基金(U22B2062);国家自然科学基金(62172232);国家自然科学基金(62402230);江苏省自然科学基金(BK20240693)
Dynamic Handwritten Signature Verification Models Protection Method Based on Contrastive Learning
FU Zhangjie1,2,3( ), CHEN Tianyu1,2,3, CUI Qi1,2,3
), CHEN Tianyu1,2,3, CUI Qi1,2,3
- 1. Engineering Research Center of Digital Forensics Ministry of Education, Nanjing University of Information Science and Technology, Nanjing 210044, China
2. School of Computer Science, Nanjing University of Information Science and Technology, Nanjing 210044, China
3. School of Cyberspace Security, Nanjing University of Information Science and Technology, Nanjing 210044, China
-
Received:2025-10-10Online:2025-12-10Published:2026-01-06 -
Contact:FU Zhangjie E-mail:fzj@nuist.edu.cn
摘要:
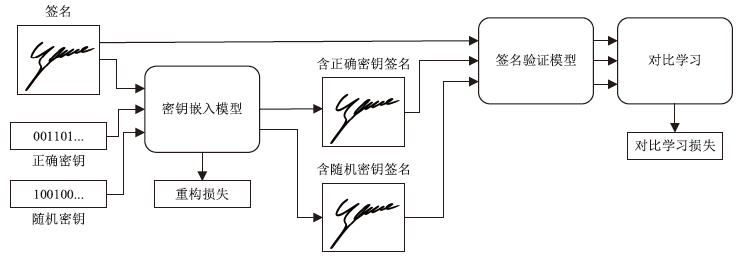
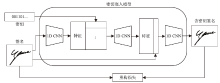
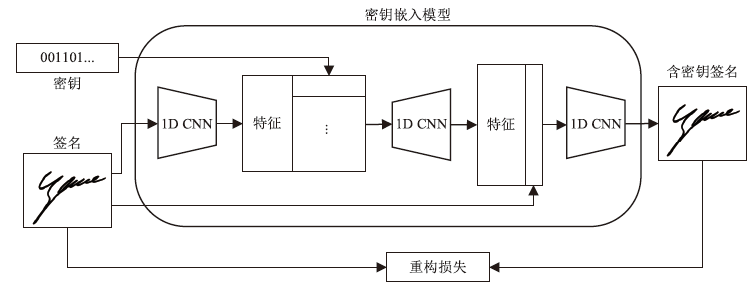
动态手写签名作为一种重要的身份验证手段,通常通过比对签名模板与待验证签名,并依据阈值判断真伪。然而,随着深度学习在手写签名验证中的广泛应用,模型规模与训练成本显著增加,且模型作为服务提供时,面临被非法调用或滥用的风险。为确保签名验证模型仅被授权用户使用,文章提出一种基于对比学习的动态手写签名模型保护方法。该方法通过构建含正确密钥的签名与原始签名,以及含正确密钥与含随机密钥签名之间的对比损失,联合优化密钥嵌入和签名验证模型,利用对比学习让模型与含正确密钥签名关联的同时,区分出原始签名和含随机密钥签名,使模型仅对包含正确密钥的签名保持验证能力,从而有效防止未经授权的访问;同时,该机制可实现模型所有权确认与知识产权追踪。基于大型动态签名数据集DeepSignDB的实验结果表明,在拥有4张签名模板并包含熟练伪造样本的条件下,含正确密钥签名等错误率从原模型的2.65%上升为4.40%,原始签名和含随机密钥签名分别上升至16.98%与16.51%,实现了在显著增强模型安全性和可追溯性的同时,仍能保持原有的签名验证性能。
中图分类号:
引用本文
付章杰, 陈天宇, 崔琦. 基于对比学习的动态手写签名验证模型保护方法[J]. 信息网络安全, 2025, 25(12): 1927-1935.
FU Zhangjie, CHEN Tianyu, CUI Qi. Dynamic Handwritten Signature Verification Models Protection Method Based on Contrastive Learning[J]. Netinfo Security, 2025, 25(12): 1927-1935.
表1
模板数量为1时的签名验证性能
| 数据集 | 模型 | 熟练伪造 | 随机伪造 | ||||
|---|---|---|---|---|---|---|---|
| 原始 | 正确 密钥 | 随机 密钥 | 原始 | 正确 密钥 | 随机 密钥 | ||
| MCYT | 未保护 | 4.06% | 4.22% | 3.99% | 0.55% | 0.51% | 0.49% |
| 保护 | 30.07% | 8.40% | 19.55% | 26.10% | 2.87% | 15.17% | |
| BiosecurID | 未保护 | 2.51% | 2.76% | 2.46% | 0.65% | 0.73% | 0.91% |
| 保护 | 30.02% | 6.51% | 36.52% | 28.46% | 3.29% | 31.45% | |
| Biosecure DS2 | 未保护 | 4.96% | 5.06% | 5.04% | 1.14% | 1.28% | 1.39% |
| 保护 | 32.55% | 11.56% | 27.76% | 30.79% | 5.69% | 21.97% | |
| e-BioSign DS2 | 未保护 | 4.35% | 4.76% | 4.58% | 2.14% | 2.31% | 2.05% |
| 保护 | 24.63% | 7.62% | 11.77% | 23.87% | 4.53% | 12.05% | |
| e-BioSign DS1 | 未保护 | 6.50% | 6.60% | 7.10% | 1.99% | 2.11% | 2.01% |
| 保护 | 27.62% | 10.86% | 12.42% | 23.84% | 4.41% | 7.24% | |
| DeepSignDB | 未保护 | 4.42% | 4.59% | 4.49% | 0.94% | 0.96% | 1.20% |
| 保护 | 31.18% | 9.52% | 24.34% | 28.04% | 4.11% | 20.45% | |
表2
模板数量为4时的签名验证性能
| 数据集 | 模型 | 熟练伪造 | 随机伪造 | ||||
|---|---|---|---|---|---|---|---|
| 原始 | 正确 密钥 | 随机 密钥 | 原始 | 正确 密钥 | 随机 密钥 | ||
| MCYT | 未保护 | 2.21% | 2.54% | 2.26% | 0.21% | 0.17% | 0.19% |
| 保护 | 16.97% | 3.26% | 10.36% | 12.52% | 0.68% | 6.17% | |
| BiosecurID | 未保护 | 1.26% | 1.19% | 1.19% | 0.41% | 0.31% | 0.50% |
| 保护 | 15.48% | 2.30% | 28.79% | 13.06% | 0.75% | 22.39% | |
| Biosecure DS2 | 未保护 | 3.51% | 4.05% | 3.45% | 1.35% | 1.57% | 1.66% |
| 保护 | 18.58% | 6.07% | 19.02% | 14.53% | 2.44% | 11.54% | |
| e-BioSign DS2 | 未保护 | 1.33% | 1.42% | 1.42% | 0.71% | 0.71% | 0.71% |
| 保护 | 13.19% | 3.57% | 8.09% | 11.48% | 2.14% | 5.71% | |
| e-BioSign DS1 | 未保护 | 3.21% | 3.77% | 3.49% | 1.55% | 1.49% | 1.58% |
| 保护 | 13.97% | 5.71% | 6.90% | 10.24% | 2.21% | 3.38% | |
| DeepSignDB | 未保护 | 2.65% | 2.99% | 2.69% | 0.74% | 0.77% | 0.86% |
| 保护 | 16.98% | 4.40% | 16.51% | 13.01% | 1.45% | 13.11% | |
表3
在DeepSignDB数据集上不同损失函数对签名验证性能的影响
| 模板 数量/张 | 模型 | 熟练伪造 | 随机伪造 | ||||
|---|---|---|---|---|---|---|---|
| 原始 | 正确 密钥 | 随机 密钥 | 原始 | 正确 密钥 | 随机 密钥 | ||
| 1 | 未保护 | 4.42% | 4.59% | 4.49% | 0.94% | 0.96% | 1.20% |
| 保护一 | 37.88% | 11.05% | 25.46% | 35.77% | 5.01% | 22.73% | |
| 保护二 | 31.18% | 9.52% | 24.34% | 28.04% | 4.11% | 20.45% | |
| 4 | 未保护 | 2.65% | 2.99% | 2.69% | 0.74% | 0.77% | 0.86% |
| 保护一 | 22.78% | 4.79% | 16.86% | 18.15% | 1.61% | 13.34% | |
| 保护二 | 16.98% | 4.40% | 16.51% | 13.01% | 1.45% | 13.11% | |
表5
在DeepSignDB数据集上不同模型保护方法对签名验证性能的影响
| 模板数量 /张 | 模型 | 熟练伪造 | 随机伪造 | ||||
|---|---|---|---|---|---|---|---|
| 原始 | 正确 密钥 | 随机 密钥 | 原始 | 正确 密钥 | 随机 密钥 | ||
| 1 | DeepIPR | 33.11% | 20.16% | 36.43% | 28.59% | 14.61% | 34.54% |
| SSAT | 41.20% | 17.35% | 35.71% | 36.85% | 10.05% | 33.53% | |
| 本文方法 | 31.18% | 9.52% | 24.34% | 28.04% | 4.11% | 20.45% | |
| 4 | DeepIPR | 18.78% | 9.55% | 29.66% | 14.21% | 6.07% | 24.77% |
| SSAT | 25.82% | 7.59% | 27.30% | 18.98% | 3.72% | 22.63% | |
| 本文方法 | 16.98% | 4.40% | 16.51% | 13.01% | 1.45% | 13.11% | |
| [1] | LAI Songxuan. Signature Verification and Writer Identification Based on Deep Learning and Domain Knowledge[D]. Guangzhou: South China University of Technology, 2021. |
| 赖松轩. 基于深度学习与领域知识的签名认证与笔迹识别[D]. 广州: 华南理工大学, 2021. | |
| [2] | QUAN Zhonghua. A Study of the Authentication Based on Online Signatures[D]. Hefei: University of Science and Technology of China, 2007. |
| 全中华. 基于动态手写签名的身份认证研究[D]. 合肥: 中国科学技术大学, 2007. | |
| [3] | DIAZ M, FISCHER A, PLAMONDON R, et al. Towards an Automatic On-Line Signature Verifier Using Only One Reference Per Signer[C]// IEEE. 2015 13th International Conference on Document Analysis and Recognition (ICDAR). New York: IEEE, 2015: 631-635. |
| [4] |
SAKOE H, CHIBA S. Dynamic Programming Algorithm Optimization for Spoken Word Recognition[J]. IEEE Transactions on Acoustics, Speech, and Signal Processing, 1978, 26(1): 43-49.
doi: 10.1109/TASSP.1978.1163055 URL |
| [5] | YAN Chendan, YANG Yang, CHENG Jiujun, et al. A DTW Signature Verification System Based on Statistical Modeling[J]. Netinfo Security, 2015, 15(7): 64-70. |
| 鄢晨丹, 杨阳, 程久军, 等. 基于统计模型的DTW签名认证系统[J]. 信息网络安全, 2015, 15(7):64-70. | |
| [6] |
SANTOSH K C, WENDLING L. Character Recognition Based on Non-Linear Multi-Projection Profiles Measure[J]. Frontiers of Computer Science, 2015, 9(5): 678-690.
doi: 10.1007/s11704-015-3400-2 |
| [7] |
LIU Yishu, YANG Zhihua, YANG Lihua. Online Signature Verification Based on DCT and Sparse Representation[J]. IEEE Transactions on Cybernetics, 2014, 45(11): 2498-2511.
doi: 10.1109/TCYB.2014.2375959 URL |
| [8] |
GALBALLY J, DIAZ-CABRERA M, FERRER M A, et al. On-Line Signature Recognition through the Combination of Real Dynamic Data and Synthetically Generated Static Data[J]. Pattern Recognition, 2015, 48(9): 2921-2934.
doi: 10.1016/j.patcog.2015.03.019 URL |
| [9] |
SHARMA A, SUNDARAM S. A Novel Online Signature Verification System Based on GMM Features in a DTW Framework[J]. IEEE Transactions on Information Forensics and Security, 2016, 12(3): 705-718.
doi: 10.1109/TIFS.2016.2632063 URL |
| [10] | DIAZ M, FERRER M A, IMPEDOVO D, et al. A Perspective Analysis of Handwritten Signature Technology[J]. ACM Computing Surveys (CSUR), 2019, 51(6): 1-39. |
| [11] |
LAI Songxuan, JIN Lianwen, ZHU Yecheng, et al. SynSig2Vec: Forgery-Free Learning of Dynamic Signature Representations by Sigma Lognormal-Based Synthesis and 1D CNN[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2021, 44(10): 6472-6485.
doi: 10.1109/TPAMI.2021.3087619 URL |
| [12] |
JIANG Jiajia, LAI Songxuan, JIN Lianmen, et al. DsDTW: Local Representation Learning with Deep Soft-Dtw for Dynamic Signature Verification[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2198-2212.
doi: 10.1109/TIFS.2022.3180219 URL |
| [13] | HASHIM Z, AHMED H M, ALKHAYYAT A H. A Comparative Study among Handwritten Signature Verification Methods Using Machine Learning Techniques[EB/OL]. (2022-10-15)[2025-09-30]. https://onlinelibrary.wiley.com/doi/full/10.1155/2022/8170424. |
| [14] | ZHOU Weilin, LIAO Zhimin, LI Ke, et al. The Construction of the “Internet + Cloud Signature” Public Service Cloud Platform[J]. Network Security Technology and Application, 2023(4): 58-61. |
| 周蔚林, 廖智敏, 李科, 等. “互联网+云签”公共服务云平台的建设[J]. 网络安全技术与应用, 2023(4):58-61. | |
| [15] | JIN Biao, LIN Xiang, XIONG Jinbo, et al. Intellectual Property Protection of Deep Neural Network Models Based on Watermarking Technology[J]. Journal of Computer Research and Development, 2024, 61(10): 2587-2606. |
| 金彪, 林翔, 熊金波, 等. 基于水印技术的深度神经网络模型知识产权保护[J]. 计算机研究与发展, 2024, 61(10):2587-2606. | |
| [16] | NAMBA R, SAKUMA J. Robust Watermarking of Neural Network with Exponential Weighting[C]// ACM. The 2019 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2019: 228-240. |
| [17] |
ZHENG Yue, WANG Si, CHANG C H. A DNN Fingerprint for Non-Repudiable Model Ownership Identification and Piracy Detection[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 2977-2989.
doi: 10.1109/TIFS.2022.3198267 URL |
| [18] |
DIAZ M, FERRER M A, ESKANDER G S, et al. Generation of Duplicated Off-Line Signature Images for Verification Systems[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2016, 39(5): 951-964.
doi: 10.1109/TPAMI.2016.2560810 URL |
| [19] |
TOLOSANA R, VERA-RODRIGUEZ R, FIERREZ J, et al. DeepSign: Deep On-Line Signature Verification[J]. IEEE Transactions on Biometrics, Behavior, and Identity Science, 2021, 3(2): 229-239.
doi: 10.1109/TBIOM.2021.3054533 URL |
| [20] | TOLOSANA R, VERA-RODRIGUEZ R, GONZALEZ-GARCIA C, et al. SVC-onGoing: Signature Verification Competition[EB/OL]. (2022-02-24)[2025-09-30]. https://www.sciencedirect.com/science/article/pii/S0031320322000905. |
| [21] |
SHEN Qi, LUAN Fangjun, YUAN Shuai. Multi-Scale Residual Based Siamese Neural Network for Writer-Independent Online Signature Verification[J]. Applied Intelligence, 2022, 52(12): 14571-14589.
doi: 10.1007/s10489-022-03318-5 |
| [22] | WU Xiaomeng, KIMURA A, KASHINO K, et al. Total Whitening for Online Signature Verification Based on Deep Representation[C]// IEEE. 2020 25th International Conference on Pattern Recognition (ICPR). New York: IEEE, 2021: 655-661. |
| [23] |
VORUGUNTI C S, PULABAIGARI V, GORTHI R K S S, et al. Osvfusenet: Online Signature Verification by Feature Fusion and Depth-Wise Separable Convolution Based Deep Learning[J]. Neurocomputing, 2020, 409: 157-172.
doi: 10.1016/j.neucom.2020.05.072 URL |
| [24] | FAN Xuefeng, ZHOU Xiaoyi, ZHU Bingbing, et al. Survey of Copyright Protection Schemes Based on DNN Model[J]. Journal of Computer Research and Development, 2022, 59(5): 953-977. |
| 樊雪峰, 周晓谊, 朱冰冰, 等. 深度神经网络模型版权保护方案综述[J]. 计算机研究与发展, 2022, 59(5)953-977. | |
| [25] | JIN Song, WANG Yuhang. On Protecting Neural Network Model in Memristor Platforms[J]. Chinese Journal of Computers, 2022, 45(11): 2377-2392. |
| 靳松, 汪宇航. 一种面向忆阻器平台的神经网络模型保护方法[J]. 计算机学报, 2022, 45(11):2377-2392. | |
| [26] | GUO Jingjing, LIU Jiuzun, MA Yong, et al. Backdoor Attack Defense Method for Federated Learning Based on Model Watermarking[J]. Chinese Journal of Computers, 2024, 47(3): 662-676. |
| 郭晶晶, 刘玖樽, 马勇, 等. 基于模型水印的联邦学习后门攻击防御方法[J]. 计算机学报, 2024, 47(3):662-676. | |
| [27] | PYONE A, MAUNG M, KIYA H. Training DNN Model with Secret Key for Model Protection[C]// IEEE. 2020 IEEE 9th Global Conference on Consumer Electronics (GCCE). New York: IEEE, 2020: 818-821. |
| [28] | XU Chaohui, CUI Qi, DONG Jinxin, et al. IDEA: An Inverse Domain Expert Adaptation Based Active DNN IP Protection Method[EB/OL]. (2024-09-29)[2025-09-30]. https://arxiv.org/html/2410.00059v1. |
| [29] | LI Peihao, HUANG Jie, WU Huaqing, et al. SecureNet: Proactive Intellectual Property Protection and Model Security Defense for DNNs Based on Backdoor Learning[EB/OL]. (2024-03-07)[2025-09-30]. https://doi.org/10.1016/j.neunet.2024.106199. |
| [30] | LIU Ziyu, ZHOU Tong, LUO Yukui, et al. TBNet: A Neural Architectural Defense Framework Facilitating DNN Model Protection in Trusted Execution Environments[C]// ACM. The 61st ACM/IEEE Design Automation Conference. New York: ACM, 2024: 1-6. |
| [31] |
NIE Hewang, LU Songfeng, WU Junjun, et al. Deep Model Intellectual Property Protection with Compression-Resistant Model Watermarking[J]. IEEE Transactions on Artificial Intelligence, 2024, 5(7): 3362-3373.
doi: 10.1109/TAI.2024.3351116 URL |
| [32] |
FAN Lixin, NG K W, CHAN C S, et al. DeepIPR: Deep Neural Network Ownership Verification with Passports[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2021, 44(10): 6122-6139.
doi: 10.1109/TPAMI.2021.3088846 URL |
| [33] | XUE Mingfu, WU Yinghao, ZHANG L Y, et al. SSAT: Active Authorization Control and User’s Fingerprint Tracking Framework for DNN IP Protection[J]. ACM Transactions on Multimedia Computing, Communications and Applications, 2024, 20(10): 1-24. |
| [34] | XIE Yingsha, MIN Rui, QIN Zeyu, et al. RoMa: A Robust Model Watermarking Scheme for Protecting IP in Diffusion Models[EB/OL]. (2025-07-01)[2025-09-30]. https://openreview.net/forum?id=TN1XsCahN7. |
| [35] | KONG Cong, XU Rui, CHEN Jiawei, et al. Protecting Copyright of Medical Pre-Trained Language Models: Training-Free Backdoor Model Watermarking[C]// ACM. The 33rd ACM International Conference on Multimedia. New York: ACM, 2025: 11590-11599. |
| [36] |
ORTEGA-GARCIA J, FIERREZ-AGUILAR J, SIMON D, et al. MCYT Baseline Corpus: A Bimodal Biometric Database[J]. IEE Proceedings-Vision, Image and Signal Processing, 2003, 150(6): 395-401.
doi: 10.1049/ip-vis:20031078 URL |
| [37] |
FIERREZ J, GALBALLY J, ORTEGA-GARCIA J, et al. BiosecurID: A Multimodal Biometric Database[J]. Pattern Analysis and Applications, 2010, 13(2): 235-246.
doi: 10.1007/s10044-009-0151-4 URL |
| [38] |
ORTEGA-GARCIA J, FIERREZ-AGUILAR J, ALONSO-FERNANDEZ F, et al. The Multiscenario Multienvironment BioSecure Multimodal Database (BMDB)[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2009, 32(6): 1097-1111.
doi: 10.1109/TPAMI.2009.76 URL |
| [39] | TOLOSANA R, VERA-RODRIGUEZ R, FIERREZ-AGUILAR J, et al. Benchmarking Desktop and Mobile Handwriting across COTS Devices: The E-BioSign Biometric Database[EB/OL]. (2017-05-05)[2025-09-30]. https://pmc.ncbi.nlm.nih.gov/articles/PMC5419513/. |
| [1] | 王亚欣, 张健. 基于少样本命名实体识别技术的电子病历指纹特征提取[J]. 信息网络安全, 2024, 24(10): 1537-1543. |
| [2] | 刘高扬, 吴伟玲, 张锦升, 王琛. 多模态对比学习中的靶向投毒攻击[J]. 信息网络安全, 2023, 23(11): 69-83. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||