信息网络安全 ›› 2025, Vol. 25 ›› Issue (1): 134-148.doi: 10.3969/j.issn.1671-1122.2025.01.012
一个用于Java应用程序运行时保护的混合系统
- 北京大学软件与微电子学院,北京 100091
-
收稿日期:2024-11-04出版日期:2025-01-10发布日期:2025-02-14 -
通讯作者:文伟平 E-mail:weipingwen@pku.edu.cn -
作者简介:江昊(2000—),男,湖北,硕士研究生,主要研究方向为软件与系统安全、漏洞挖掘|刘成杰(1998—),男,湖南,博士研究生,主要研究方向为软件安全、漏洞挖掘和入侵检测|文伟平(1976—),男,湖南,教授,博士,主要研究方向为系统与网络安全、大数据与云安全、智能计算安全 -
基金资助:国家自然科学基金(61872011)
A Hybrid System for Runtime Protection inside Java Application
JIANG Hao, LIU Chengjie, WEN Weiping( )
)
- School of Software & Microelectronics, Peking University, Beijing 100091, China
-
Received:2024-11-04Online:2025-01-10Published:2025-02-14 -
Contact:WEN Weiping E-mail:weipingwen@pku.edu.cn
摘要:
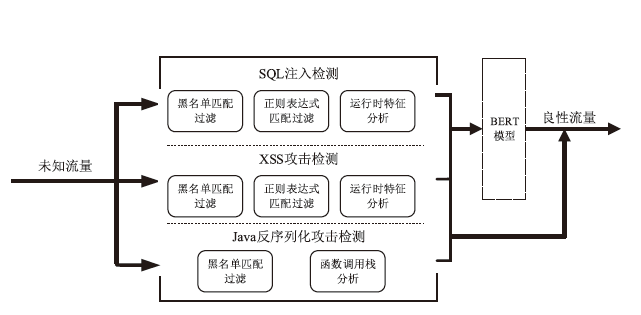
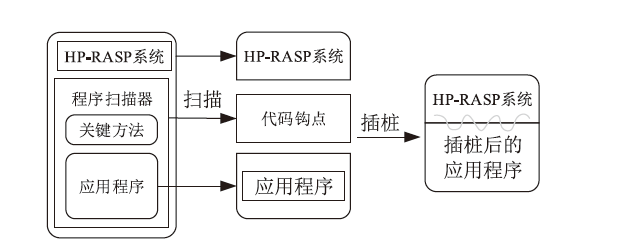
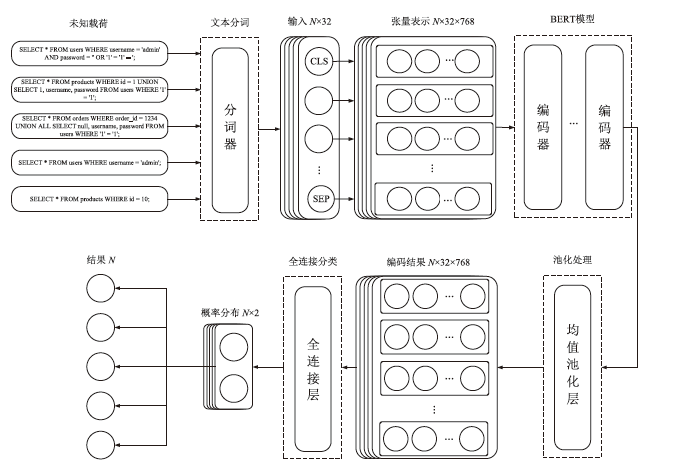
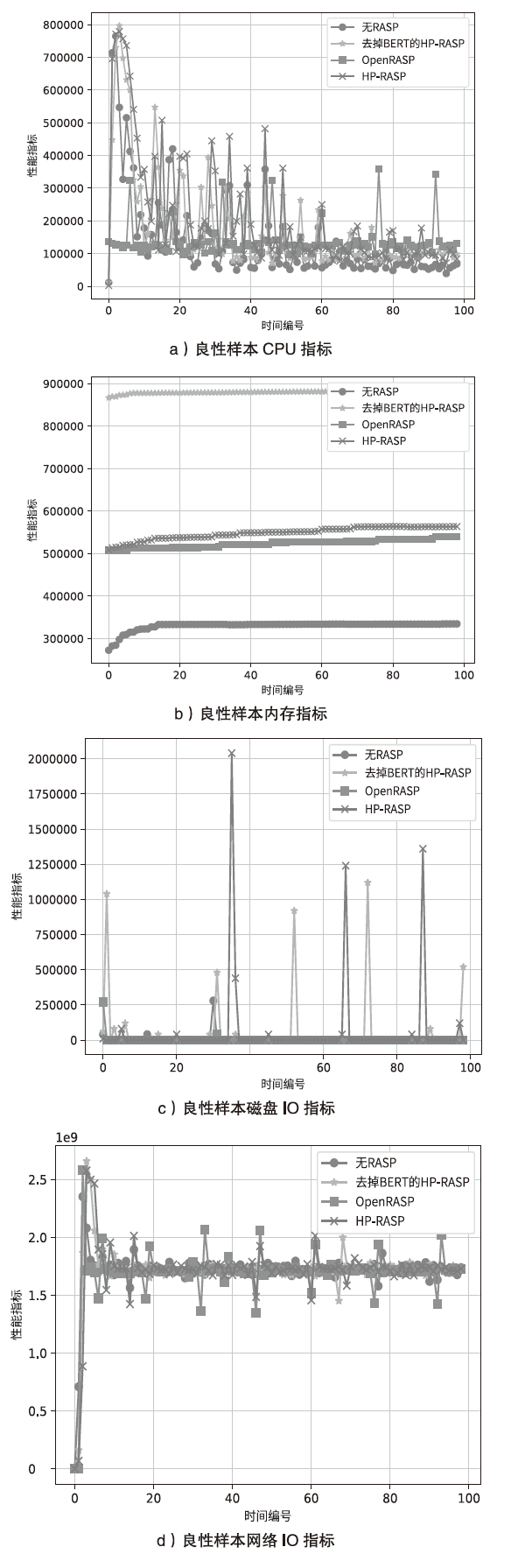
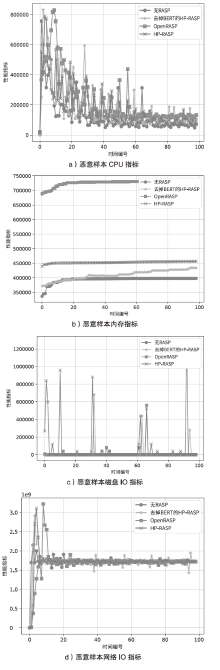
近年来,应用程序运行时自我保护RASP技术作为一种嵌入式防护机制,广泛应用于检测和防御Web应用程序中的常见攻击,如SQL注入、跨站脚本XSS攻击以及Java反序列化攻击。然而,现有RASP系统多采用基于黑名单的检测方法,容易被绕过且难以应对新型攻击。为此,文章提出一种混合系统HP-RASP,该系统结合启发式规则和深度学习模型,在应用程序运行时提供自适应的安全保护。文章将BERT模型引入RASP系统,用于分析和检测SQL注入攻击,同时通过对常见方法调用栈进行监控和黑名单匹配,防御XSS和反序列化攻击。HP-RASP利用Java插桩技术,动态插入关键类和方法的监控逻辑,实现对Web请求的实时分析。文章在多个开源数据集上评估了该系统的检测性能,并将其与当前主流RASP系统OpenRASP进行了对比。实验结果表明,在检测准确率、性能开销和系统鲁棒性方面,HP-RASP相较现有方案均有显著提升;在SQL注入方面,准确率达到81.9%,比OpenRASP提升了1.84倍,召回率和F1分数也显著高于OpenRASP;在XSS防护方面,HP-RASP对反射型XSS和存储型XSS的召回率均达到99.9%,对反序列化攻击的召回率达到84.6%;在响应时间和资源消耗方面,HP-RASP表现良好,并未显著增加响应时间和资源消耗。
中图分类号:
引用本文
江昊, 刘成杰, 文伟平. 一个用于Java应用程序运行时保护的混合系统[J]. 信息网络安全, 2025, 25(1): 134-148.
JIANG Hao, LIU Chengjie, WEN Weiping. A Hybrid System for Runtime Protection inside Java Application[J]. Netinfo Security, 2025, 25(1): 134-148.
表1
部分SQL危险类
| 类 | 钩点 |
|---|---|
| com/mysql/jdbc/NonRegisteringDriver | ConnectionHook |
| com/mysql/jdbc/NonRegisteringDriver | DriverManagerHook |
| org/sqlite/JDBC | DriverManagerHook |
| org/postgresql/Driver | DriverManagerHook |
| com/mysql/jdbc/PreparedStatement | StatementHook |
| com/mysql/jdbc/StatementImpl | StatementHook |
| org/sqlite/jdbc3/JDBC3Statement | StatementHook |
| ... | ... |
| rg/postgresql/jdbc/PgStatement | StatementHook |
| org/hsqldb/jdbc/JDBCStatement | StatementHook |
| com/mysql/jdbc/ResultSetImpl | SQLResultSetHook |
| org/sqlite/jdbc3/JDBC3ResultSet | SQLResultSetHook |
| oracle/jdbc/.../OracleResultSetImpl | SQLResultSetHook |
| org/sqlite/Conn | ConnectionPreparedHook |
| oracle/jdbc/.../PhysicalConnection | ConnectionPreparedHook |
| com/ibm/db2/jcc/am/Connectio | ConnectionPreparedHook |
| org/apache/../fileupload/FileUploadBase | MultipleHook |
表2
部分XSS风险类
| 类 | 钩点 |
|---|---|
| com/bes/.../OutputBuffer | BESResponseBodyHook |
| io/undertow/.../ServletRequestContext | ServerRequestHook |
| io/undertow/.../AttachmentKey | ServerRequestHook |
| org/apache/coyote/Response | ServerResponseBodyHook |
| ... | ... |
| org/apache/catalina/connector/Request | ServerParamHook |
| apache/catalina/.../FilterChain | ServerPreRequestHook |
| apache/catalina/.../CoyoteAdapter | ServerPreRequestHook |
| org/springframework/.../RequestWrapper | SpringHook |
表5
不同解决方案的耗时比较
| 解决方案 | 50% Line /ms | 90% Line /ms | 95% Line /ms | 吞吐率 /QPS | 接受速率 /KB·s-1 | 发送速率/KB·s-1 |
|---|---|---|---|---|---|---|
| 原始应用程序 (良性) | 4 | 6 | 6 | 200.1 | 1016.11 | 29.90 |
| 原始应用程序 (恶意) | 5 | 5 | 5 | 200.0 | 1025.18 | 33.10 |
| OpenRASP (良性) | 5 | 6 | 7 | 199.8 | 1029.22 | 29.86 |
| OpenRASP (恶意) | 5 | 9 | 30 | 199.8 | 1062.84 | 36.20 |
| 去掉BERT的HP-RASP (良性) | 5 | 7 | 10 | 199.9 | 1028.87 | 29.87 |
| 去掉BERT的HP-RASP (恶意) | 5 | 7 | 9 | 199.9 | 1059.99 | 34.77 |
| HP-RASP (良性) | 5 | 7 | 10 | 200.0 | 1028.93 | 29.87 |
| HP-RASP (恶意) | 5 | 7 | 9 | 200.1 | 1069.78 | 34.79 |
| [1] | JOHN P, TERRY A H. SANS 2022 Top New Attacks and Threat Report[EB/OL]. (2022-09-12)[2024-10-22]. https://www.sans.org/white-papers/sans-2022-top-new-attacks-threat-report/. |
| [2] | ALWAN Z S, YOUNIS M F. Detection and Prevention of SQL Injection Attack: A Survey[J]. International Journal of Computer Science and Mobile Computing, 2017, 6(8): 5-17. |
| [3] | GUNAWAN T S, KASIM L M, KARTIWI M, et al. Penetration Testing Using Kali Linux: SQL Injection, XSS, Wordpres, and WPA2 Attacks[J]. Indonesian Journal of Electrical Engineering and Computer Science, 2018, 12(2): 729-737. |
| [4] | APPLEBAUM S, GABER T, AHMED A. Signature-Based and Machine-Learning-Based Web Application Firewalls: A Short Survey[J]. Procedia Computer Science, 2021, 189: 359-367. |
| [5] | JUNIOR M D, EBECKEN N F. A New WAF Architecture with Machine Learning for Resource-Efficient Use[J]. Computers & Security, 2021, 106: 102290. |
| [6] | RAZZAQ A, HUR A, SHAHBAZ S, et al. Critical Analysis on Web Application Firewall Solutions[C]// IEEE. 2013 IEEE Eleventh International Symposium on Autonomous Decentralized Systems (ISADS). New York: IEEE, 2013: 1-6. |
| [7] | NGUYEN H T, TORRANO-GIMENEZ C, ALVAREZ G, et al. Application of the Generic Feature Selection Measure in Detection of Web Attacks[C]// Springer. Computational Intelligence in Security for Information Systems. Heidelberg: Springer, 2011: 25-32. |
| [8] | WEISSBACHER M, ROBERTSON W, KIRDA E, et al. ZigZag: Automatically Hardening Web Applications against Client-Side Validation Vulnerabilities[C]// USENIX. The 24th USENIX Security Symposium (USENIX Security 15). Berkeley: USENIX, 2015: 737-752. |
| [9] | PRABHUDESAI P, BHALERAO A A, PRABHUDESAI R. Web Application Firewall: Artificial Intelligence Arc[J]. International Research Journal of Engineering and Technology, 2019, 6(8): 3706-3708. |
| [10] | TEKEREK A, BAY O F. Design and Implementation of an Artificial Intelligence-Based Web Application Firewall Model[J]. Neural Network World, 2019, 29(4): 189-206. |
| [11] | DEMETRIO L, VALENZA A, COSTA G, et al. WAF-A-MoLE: Evading Web Application Firewalls through Adversarial Machine Learning[C]// ACM. Proceedings of the 35th Annual ACM Symposium on Applied Computing. New York: ACM, 2020: 1745-1752. |
| [12] | YUAN E, MALEK S. A Taxonomy and Survey of Self-Protecting Software Systems[C]// IEEE. 2012 7th International Symposium on Software Engineering for Adaptive and Self-Managing Systems (SEAMS). New York: IEEE, 2012: 109-118. |
| [13] | CLINCY V, SHAHRIAR H. Web Application Firewall: Network Security Models and Configuration[C]// IEEE. 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC). New York: IEEE, 2018: 835-836. |
| [14] | SALEMI M. Automated Rules Generation into Web Application Firewall Using Runtime Application Self-Protection[D]. Louvain-La-Neuve: Ecole Polytechnique De Louvain, 2020. |
| [15] | SETH A. Comparing Effectiveness and Efficiency of Interactive Application Security Testing (IAST) and Runtime Application Self-Protection (RASP) Tools[M]. Raleigh: North Carolina State University, 2022. |
| [16] | ČISAR P, ČISAR S M. The Framework of Runtime Application Self-Protection Technology[C]// IEEE. 2016 IEEE 17th International Symposium on Computational Intelligence and Informatics (CINTI). New York: IEEE, 2016: 81-86. |
| [17] | DEVLIN J, CHANG Mingwei, LEE K, et al. BERT: Pre-Training of Deep Bidirectional Transformers for Language Understanding[EB/OL]. [2024-10-20]. https://arxiv.org/abs/1810.04805v2. |
| [18] | ROGERS A, KOVALEVA O, RUMSHISKY A. A Primer in BERTology: What We Know about How BERT Works[J]. Transactions of the Association for Computational Linguistics, 2020, 8: 842-866. |
| [19] | WHANG T, LEE D, LEE C, et al. An Effective Domain Adaptive Post-Training Method for BERT in Response Selection[EB/OL]. [2024-10-20]. https://arxiv.org/abs/1908.04812v2. |
| [20] | LI Junlong, ZHANG Zhuosheng, ZHAO Hai, et al. Task-Specific Objectives of Pre-Trained Language Models for Dialogue Adaptation[EB/OL]. (2020-09-10)[2024-10-20]. https://www.semanticscholar.org/paper/Task-specific-Objectives-of-Pre-trained-Language-Li-Zhang/1cad933afc55f1a562e27ebd4f65c5d0f5a6c26a. |
| [21] | SUN Yi, ZHENG Yu, HAO Chao, et al. NSP-BERT: A Prompt-Based Few-Shot Learner through an Original Pre-Training Task: Next Sentence Prediction[EB/OL]. [2024-10-20]. https://arxiv.org/abs/2109.03564v2. |
| [22] | Baidu. OpenRASP[EB/OL]. (2017-8-10)[2024-10-20]. https://github.com/baidu/openrasp. |
| [23] | Gartner. IT Glossary[EB/OL]. (2012-06-07)[2024-10-20]. https://www.gartner.com/en/information-technology/glossary/runtime-application-self-protection-rasp. |
| [24] | LANE A. Understanding and Selecting RASP: Technology Overview[EB/OL]. (2016-05-17)[2024-10-20]. https://securosis.com/blog/understanding-and-selecting-rasp-technology-overview. |
| [25] | YIN Zhongxu, LI Zhufeng, CAO Yan. A Web Application Runtime Application Self-Protection Scheme against Script Injection Attacks[C]// Springer. Cloud Computing and Security. Heidelberg: Springer, 2018: 566-577. |
| [26] | QIU Ruonan, HU Anqi, PENG Guojun, et al. A General Detection and Location Scheme for Java Web Framework Vulnerability Based on RASP Technology[J]. Journal of Wuhan University (Natural Science Edition), 2020, 66(3): 285-296. |
| 邱若男, 胡岸琪, 彭国军, 等. 基于RASP技术的Java Web框架漏洞通用检测与定位方案[J]. 武汉大学学报(理学版), 2020, 66(3):285-296. | |
| [27] | LI Yulin, CHEN Libo, LIU Yujiang, et al. Java Deserialization Vulnerability Defense Technology Based on Run-Time Detection[J]. Chinese Journal of Network and Information Security, 2024, 10(2): 154-164. |
| [28] |
YU Hang, WANG Shuai, JIN Huamin. RASP Based Web Security Detection Method[J]. Telecommunications Science, 2020, 36(11): 113-120.
doi: 10.11959/j.issn.1000-0801.2020294 |
|
余航, 王帅, 金华敏. 基于RASP的Web安全检测方法[J]. 电信科学, 2020, 36(11):113-120.
doi: 10.11959/j.issn.1000-0801.2020294 |
|
| [29] | LIEM C, ABDALLAH E, OKOYE C, et al. Runtime Self-Protection in a Trusted Blockchain-Inspired Ledger[EB/OL]. [2024-10-20]. https://www.academia.edu/38279827/Runtime_Self_Protection_in_a_Trusted_Blockchain_inspired_Ledger. |
| [30] | YANG Wenchuan, PENG Jing. Research on EVM-Based Smart Contract Runtime Self-Protection Technology Framework[C]// Springer. Web, Artificial Intelligence and Network Applications:Proceedings of the Workshops of the 34th International Conference on Advanced Information Networking and Applications (WAINA-2020). Heidelberg: Springer, 2020: 617-627. |
| [31] | HALFOND W G J, ORSO A. AMNESIA: Analysis and Monitoring for NEutralizing SQL-Injection Attacks[C]// ACM. Proceedings of the 20th IEEE/ACM International Conference on Automated Software Engineering. New York: ACM, 2005: 174-183. |
| [32] | KOMIYA R, PAIK I, HISADA M. Classification of Malicious Web Code by Machine Learning[C]// IEEE. 2011 3rd International Conference on Awareness Science and Technology (iCAST). New York: IEEE, 2011: 406-411. |
| [33] | PUTTHACHAROEN R, BUNYATNOPARAT P. Protecting Cookies from Cross Site Script Attacks Using Dynamic Cookies Rewriting Technique[C]// IEEE. The 13th International Conference on Advanced Communication Technology (ICACT2011). New York: IEEE, 2011: 1090-1094. |
| [34] | ZHANG Qianjie, CHEN Hao, SUN Jianhua. An Execution-Flow Based Method for Detecting Cross-Site Scripting Attacks[C]// IEEE. The 2nd International Conference on Software Engineering and Data Mining. New York: IEEE, 2010: 160-165. |
| [35] | GUO Chun, CAI Wenyan, SHEN Guowei, et al. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload[J]. Netinfo Security, 2021, 21(7): 43-53. |
| 郭春, 蔡文艳, 申国伟, 等. 基于关键载荷截取的SQL注入攻击检测方法[J]. 信息网络安全, 2021, 21(7):43-53. | |
| [36] | HUANG Kaijie, WANG Jian, CHEN Jiongyi. A Large Language Model Based SQL Injection Attack Detection Method[J]. Netinfo Security, 2023, 23(11): 84-93. |
| 黄恺杰, 王剑, 陈炯峄. 一种基于大语言模型的SQL注入攻击检测方法[J]. 信息网络安全, 2023, 23(11):84-93. | |
| [37] | MITROPOULOS D, STROGGYLOS K, SPINELLIS D, et al. How to Train Your Browser[J]. ACM Transactions on Privacy and Security, 2016, 19(1): 1-31. |
| [38] | TAN Yuchen, CAI Jingjing, NI Chen. Research on Web Attack Detection Technology Based on Deep Learning[J]. Netinfo Security, 2020, 20(S2): 122-126. |
| 谭宇辰, 蔡晶晶, 倪辰. 基于深度学习的Web攻击检测技术研究[J]. 信息网络安全, 2020, 20(S2): 122-126. | |
| [39] | MA Zheng, CHEN Xuebin, ZHANG Guopeng, et al. XSS Attack Detection Method Based on Genetic Algorithm and Support Vector Machine[J]. Journal of Jiangsu University (Natural Science Edition), 2024, 45(6): 686-693. |
| 马征, 陈学斌, 张国鹏, 等. 基于遗传算法和支持向量机的XSS攻击检测方法[J]. 江苏大学学报(自然科学版), 2024, 45(6):686-693. | |
| [40] | KOUTROUMPOUCHOS N, LAVDANIS G, VERONI E, et al. ObjectMap: Detecting Insecure Object Deserialization[C]// ACM. Proceedings of the 23rd Pan-Hellenic Conference on Informatics. New York: ACM, 2019: 67-72. |
| [41] | CRISTALLI S, VIGNATI E, BRUSCHI D, et al. Trusted Execution Path for Protecting Java Applications against Deserialization of Untrusted Data[C]// Springer. International Symposium on Recent Advances in Intrusion Detection. Heidelberg: Springer, 2018: 445-464. |
| [42] | LI Yulin, CHEN Libo, LIU Yujiang, et al. Java Deserialization Vulnerability Defense Technology Based on Run-Time Detection[J]. Chinese Journal of Network and Information Security, 2024, 10(2): 154-164. |
| [43] |
ZHENG Peng, SHA Letian. Java Deserialization Vulnerability Detection Method Based on Hybrid Analysis[J]. Computer Engineering, 2023, 49(12): 136-145.
doi: 10.19678/j.issn.1000-3428.0066151 |
|
郑鹏, 沙乐天. 基于混合分析的Java反序列化漏洞检测方法[J]. 计算机工程, 2023, 49(12):136-145.
doi: 10.19678/j.issn.1000-3428.0066151 |
|
| [44] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning[J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| 项慧, 薛鋆豪, 郝玲昕. 基于语言特征集成学习的大语言模型生成文本检测[J]. 信息网络安全, 2024, 24(7):1098-1109. | |
| [45] | Oracle. Interface Instrumentation[EB/OL]. [2024-10-20]. https://docs.oracle.com/javase/7/docs/api/java/lang/instrument/Instrumentation.html. |
| [46] | HEUSER S, NADKARNI A, ENCK W, et al. ASM: A Programmable Interface for Extending Android Security[C]// USENIX. The 23rd USENIX Security Symposium (USENIX Security 14). Berkeley: USENIX. 2014: 1005-1019. |
| [47] | İsmail T. Payloadbox[EB/OL]. (2024-06-18)[2024-10-20]. https://github.com/payloadbox/. |
| [48] | Syed S. Sql Injection Dataset[EB/OL]. (2021-09-09)[2024-10-20]. https://www.kaggle.com/datasets/syedsaqlainhussain/sql-injection-dataset. |
| [49] | Chris F. Ysoseria[EB/OL]. (2024-05-31)[2024-10-20]. https://github.com/frohoff/ysoserial. |
| [1] | 李元诚, 罗昊, 王庆乐, 李建彬. 一种基于ATT&CK的新型电力系统APT攻击建模[J]. 信息网络安全, 2023, 23(2): 26-34. |
| [2] | 王鹃, 王蕴茹, 翁斌, 龚家新. 机器学习在x86二进制反汇编中的应用研究综述[J]. 信息网络安全, 2022, 22(6): 9-25. |
| [3] | 周枝凝, 王斌君, 翟一鸣, 仝鑫. 基于ALBERT动态词向量的垃圾邮件过滤模型[J]. 信息网络安全, 2020, 20(9): 107-111. |
| [4] | 尤玮婧, 刘丽敏, 马悦, 韩东. 基于安全硬件的云端数据机密性验证方案[J]. 信息网络安全, 2020, 20(12): 1-8. |
| [5] | 刘玉岭, 唐云善, 张琦, 李枫. 电力调度自动化软件安全态势评估方法[J]. 信息网络安全, 2019, 19(8): 15-21. |
| [6] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [7] | 王锐强, 金大海. 软件安全中基于判断逻辑的空指针引用故障检测[J]. 信息网络安全, 2015, 15(6): 47-54. |
| [8] | . Fuzzing 测试技术综述[J]. , 2014, 14(3): 87-. |
| [9] | 史记;曾昭龙;杨从保;李培岳. Fuzzing 测试技术综述[J]. , 2014, 14(3): 0-0. |
| [10] | 关通, 任馥荔, 文伟平, 张浩. 基于Windows的软件安全典型漏洞利用策略探索与实践[J]. 信息网络安全, 2014, 14(11): 59-65. |
| [11] | 张志海;郑春一;张红军. 一种面向等级保护的软件安全需求分析方法研究[J]. , 2013, 13(8): 0-0. |
| [12] | 梅瑞;武学礼;文伟平. 基于Android平台的代码保护技术研究[J]. , 2013, 13(7): 0-0. |
| [13] | 范渊;凌霄. Android程序安全检测模型[J]. , 2013, 13(10): 0-0. |
| [14] | 王一岚;郭嵩. 基于静态分析的Java源代码后门检测技术研究[J]. , 2012, 12(7): 0-0. |
| [15] | 江雷;朱建平. 面向等级保护的软件安全需求分析方法研究[J]. , 2011, 11(9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||