信息网络安全 ›› 2025, Vol. 25 ›› Issue (1): 124-132.doi: 10.3969/j.issn.1671-1122.2025.01.011
基于子树序列规则挖掘的Dockerfile误配置检测和修复方法
- 陆军工程大学指挥控制工程学院,南京 210007
-
收稿日期:2024-05-14出版日期:2025-01-10发布日期:2025-02-14 -
通讯作者:赵宁 E-mail:zhaonig@yeah.net -
作者简介:王金双(1978—),男,江苏,副教授,博士,主要研究方向为系统安全|赵宁(1993—),女,辽宁,硕士研究生,CCF会员,主要研究方向为系统安全|崔帅(1998—),女,山东,硕士研究生,主要研究方向为系统安全
A Method for Subtree Sequence Rule Mining-Based Dockerfile Misconfiguration Detection and Repair
WANG Jinshuang, ZHAO Ning( ), CUI Shuai
), CUI Shuai
- College of Command and Control Engineering, Army Engineering University, Nanjing 210007, China
-
Received:2024-05-14Online:2025-01-10Published:2025-02-14 -
Contact:ZHAO Ning E-mail:zhaonig@yeah.net
摘要:
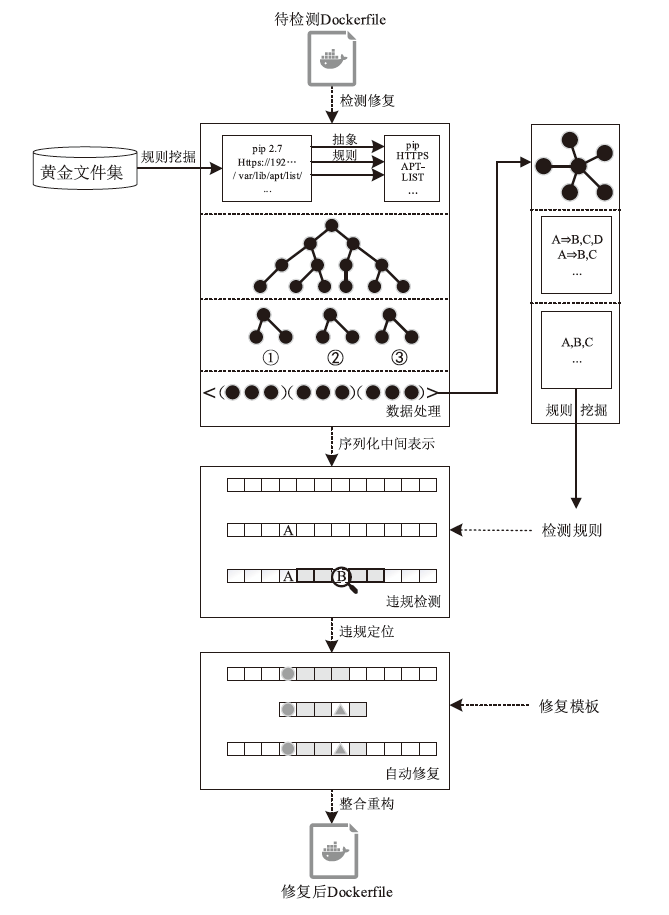
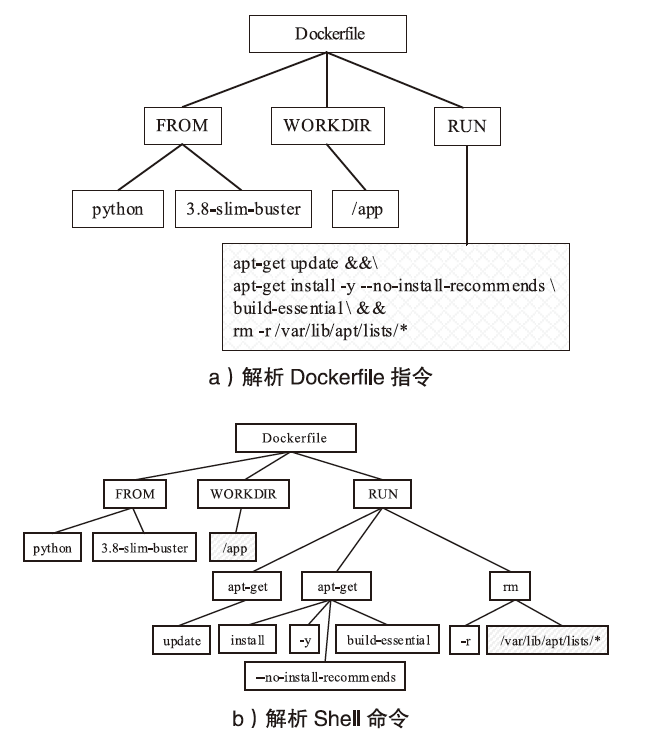
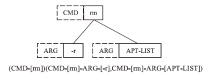
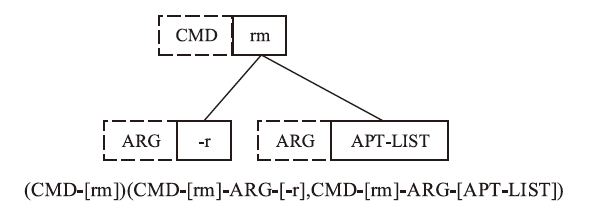
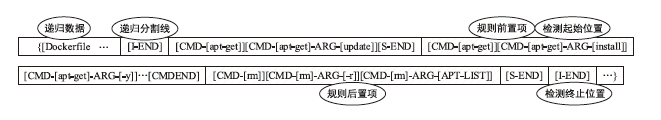
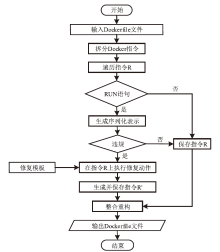
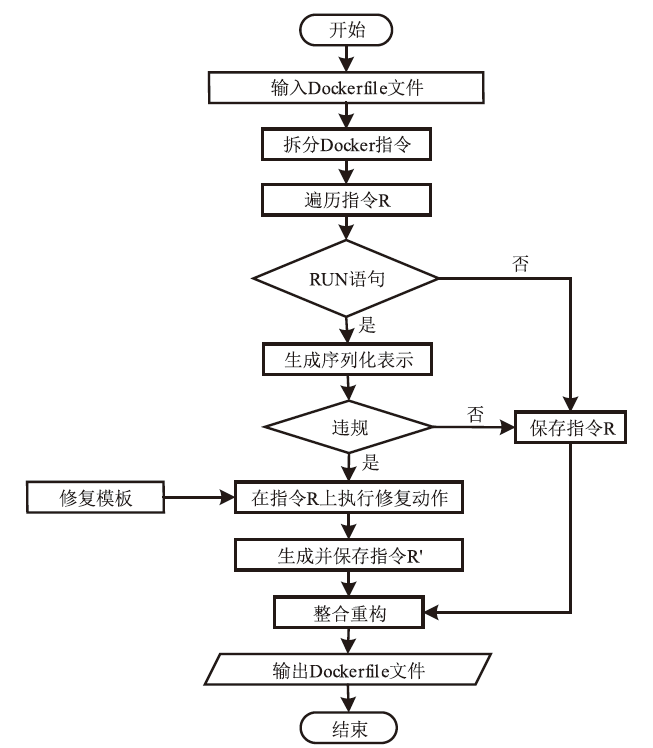
Dockerfile是用于构建Docker容器镜像的文本文件,它包含一系列指令和配置,用于描述如何组装一个Docker容器的运行环境。然而,配置不当的Dockerfile可能引发很多性能与安全方面的问题。现有基于规则挖掘的检测与修复方法主要关注常见命令内部的关联性,忽略了命令之间的依赖联系。这些方法通常侧重于高频命令,容易遗漏低频命令中的隐藏规律。针对上述问题,文章提出一种基于子树序列规则挖掘的Dockerfile误配置检测和修复方法。首先,将Dockerfile转化为抽象语法树,进一步分解为有序子树,并对子树进行序列化处理,以构建中间表示。随后,通过对子树进行聚类分组,并采用序列规则挖掘算法对各分组执行规则挖掘。在规则挖掘过程中,将规则前项限定为子树根节点,从而有效聚焦目标指令并抑制规则生成的爆发式增长。最后,进一步筛选最大序列规则,提取常用命令搭配模式,并总结归纳语义规则作为基准,用于Dockerfile的违规检测和自动修复。实验结果表明,该方法成功挖掘出31条语义规则,其中包括12条未公开规则。在违规检测精确率方面,相较于基准方法提升了10%;在修复成功率方面,相较于基准方法提升了5.6%。
中图分类号:
引用本文
王金双, 赵宁, 崔帅. 基于子树序列规则挖掘的Dockerfile误配置检测和修复方法[J]. 信息网络安全, 2025, 25(1): 124-132.
WANG Jinshuang, ZHAO Ning, CUI Shuai. A Method for Subtree Sequence Rule Mining-Based Dockerfile Misconfiguration Detection and Repair[J]. Netinfo Security, 2025, 25(1): 124-132.
表2
提取的语义规则
| 规则描述 | 等级 | 支持度 | 置信度 | 命令频次/次 | 违反规则的危害 |
|---|---|---|---|---|---|
| chgrp使用参数-r | 建议 | 16 | 76% | 25 | 子目录或文件未 正确改组,产生运行时的权限问题 |
| mkdir使用参数-p | 建议 | 913 | 75% | 1838 | — |
| sed使用参数-i | 建议 | 285 | 87% | 1015 | 未原地编辑文件,导致配置不生效 |
| chown使用参数-r | 建议 | 227 | 73% | 489 | — |
| bundle使用参数--clean | 建议 | 27 | 73% | 57 | 增加镜像体积 |
| ln使用参数-s | 必须 | 352 | 74% | 914 | — |
| rm使用参数-rf | 建议 | 1875 | 78% | 3865 | — |
| sha512sum/sha256sum使用参数-c校验文件 完整性 | 建议 | 220 | 72% | 409 | 使用损坏或被篡改的文件,增加安全风险 |
| pip install使用参数 --no-cache-dir | 必须 | 862 | 62% | 2280 | — |
| apk add参数--no-cache | 必须 | 716 | 79% | 1928 | — |
| apt-get install使用 参数-y | 必须 | 2693 | 83% | 9727 | — |
| apt-get install使用 参数--no-install-recommends | 必须 | 1777 | 55% | 9727 | — |
| zypper install使用参数 --no-recommends | 必须 | 42 | 59% | 192 | 安装大量不必要的推荐包,增加镜像体积 |
| gpg使用参数--batch 进入批处理模式 | 建议 | 157 | 69% | 607 | — |
| gpg使用参数 --keyserver指定公钥 服务器 | 建议 | 144 | 63% | 607 | — |
| gpg使用参数--recv-keys接收公钥 | 建议 | 136 | 60% | 607 | 无法正确接收密钥,导致无法验证下载的包的真实性 |
| conda install使用 参数-y | 必须 | 81 | 62% | 338 | 构建中断等待用户输入 |
| yum install使用 参数-y | 必须 | 341 | 90% | 1177 | — |
| dnf install使用参数-y | 必须 | 69 | 90% | 175 | — |
| poetry install使用 参数-y | 必须 | 20 | 67% | 52 | 构建中断等待用户输入 |
| 使用yum安装依赖后应清除缓存 | 必须 | 241 | 64% | 1177 | — |
| 使用conda安装依赖后应清除缓存 | 必须 | 95 | 73% | 338 | — |
| 使用dnf安装依赖后应清除缓存 | 必须 | 56 | 73% | 175 | — |
| 使用microdnf安装 依赖后应清除缓存 | 必须 | 22 | 96% | 63 | 增加镜像体积 |
| apt-get安装依赖应先更新 | 必须 | 2717 | 84% | 9727 | — |
| microdnf安装依赖应先更新 | 必须 | 18 | 78% | 63 | 安装过时的软件包 |
| helm使用https 超链接 | 必须 | 27 | 96% | 96 | 数据传输过程中易受中间人攻击,增大泄密风险 |
| curl使用https 超链接 | 必须 | 705 | 69% | 1651 | — |
| git clone使用https 超链接 | 建议 | 426 | 61% | 1774 | — |
| wget使用https 超链接 | 必须 | 378 | 68% | 864 | 数据传输过程中易受中间人攻击,增大泄密风险 |
| 使用gosu nobody降低权限 | 建议 | 15 | 59% | 97 | — |
表5
自动修复性能比较
| 规则描述 | 修复前违规数量/条 | 修复后违规数量/条 | |||
|---|---|---|---|---|---|
| 修复后SRMDR | 成功率 | 修复后Parfum | 成功率 | ||
| apk add 缺少 --no-cache参数 | 12 | 12 | 100% | 8 | 66.7% |
| pip install 缺少 --no-cache-dir参数 | 46 | 37 | 80.4% | 43 | 93.5% |
| apt- get install 缺少 -y参数 | 1 | 1 | 100% | 1 | 100% |
| apt-get缺少--no-install-recommends参数 | 73 | 73 | 100% | 68 | 93.2% |
| apt-get安装依赖后 未清缓存 | 66 | 65 | 98.4% | 57 | 86.4% |
| dnf安装依赖后 未清缓存 | 1 | 1 | 100% | 1 | 100% |
| 总计 | 199 | 189 | 95% | 178 | 89.4% |
| [1] | POTDAR A M, NARAYAN D G, KENGOND S, et al. Performance Evaluation of Docker Container and Virtual Machine[J]. Procedia Computer Science, 2020, 171: 1419-1428. |
| [2] | Dockerdocs. Building Best Practices[EB/OL]. [2024-04-30]. https://docs.docker.com/build/building/best-practices. |
| [3] | HENKEL J, SILVA D, TEIXEIRA L, et al. Shipwright: A Human-in-the-Loop System for Dockerfile Repair[C]// IEEE. 2021 IEEE/ACM 43rd International Conference on Software Engineering:Companion Proceedings (ICSE-Companion). New York: IEEE, 2021: 198-199. |
| [4] | CITO J, SCHERMANN G, WITTERN J E, et al. An Empirical Analysis of the Docker Container Ecosystem on GitHub[C]// IEEE. 2017 IEEE/ACM 14th International Conference on Mining Software Repositories (MSR). New York: IEEE, 2017: 323-333. |
| [5] | WU Yiwen, ZHANG Yang, WANG Tao, et al. Dockerfile Changes in Practice: A Large-Scale Empirical Study of 4, 110 Projects on GitHub[C]// IEEE. 2020 27th Asia-Pacific Software Engineering Conference (APSEC). New York: IEEE, 2020: 247-256. |
| [6] | HENKEL J, BIRD C, LAHIRI S K, et al. Learning From, Understanding, and Supporting DevOps Artifacts for Docker[C]// IEEE. 2020 IEEE/ACM 42nd International Conference on Software Engineering (ICSE). New York: IEEE, 2020: 38-49. |
| [7] | ZHOU Yu, ZHAN Weilin, LI Zi, et al. DRIVE: Dockerfile Rule Mining and Violation Detection[J]. ACM Transactions on Software Engineering and Methodology, 2023, 33(2): 1-23. |
| [8] | DURIEUX T. Parfum: Detection and Automatic Repair of Dockerfile Smells[EB/OL]. (2023-02-09)[2024-04-20]. https://arxiv.org/abs/2302.01707v2. |
| [9] | ABDELWAHAB A, YOUSSEF N. Performance Evaluation of Sequential Rule Mining Algorithms[J]. Applied Sciences, 2022, 12(10): 5230-5238. |
| [10] | SOLANKI S K, PATEL J T. A Survey on Association Rule Mining[C]// IEEE. 2015 Fifth International Conference on Advanced Computing & Communication Technologies. New York: IEEE, 2015: 212-216. |
| [11] |
LI Zi, ZHOU Yu. Method for Mining Program Semantic Rules and Detecting Violations Based on Sequence[J]. Computer Science, 2024, 51(6): 78-84.
doi: 10.11896/jsjkx.230300224 |
|
李孜, 周宇. 基于序列的程序语义规则挖掘与违规检测方法[J]. 计算机科学, 2024, 51(6): 78-84.
doi: 10.11896/jsjkx.230300224 |
|
| [12] | JULIET T D, KHANNA N H, SREEJITH S, et al. Intelligent Mining of Association Rules Based on Nanopatterns for Code Smells Detection[J]. Scientific Programming, 2023(6): 1058-1072. |
| [13] | RUBIN J, HENNICHE A N, MOHA N, et al. Sniffing Android Code Smells: An Association Rules Mining-Based Approach[C]// IEEE. 2019 IEEE/ACM 6th International Conference on Mobile Software Engineering and Systems (MOBILESoft). New York: IEEE, 2019: 123-127. |
| [14] | BIAN Pan, LIANG Bin, SHI Wenchang, et al. NAR-Miner: Discovering Negative Association Rules from Code for Bug Detection[C]// ACM. Proceedings of the 2018 26th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering. New York: ACM, 2018: 411-422. |
| [15] | DU Jiaoling, ZHANG Xiangli, ZHANG Hongmei, et al. Research and Improvement of Apriori Algorithm[C]// IEEE. 2016 Sixth International Conference on Information Science and Technology (ICIST). New York: IEEE, 2016: 117-121. |
| [16] | FOURNIER-VIGER P, FAGHIHI U, NKAMBOU R, et al. CMRules: Mining Sequential Rules Common to Several Sequences[J]. Knowledge-Based Systems, 2012, 25(1): 63-76. |
| [17] | FOURNIER-VIGER P, TSENG V S. TNS: Mining Top-K Non-Redundant Sequential Rules[C]// ACM. Proceedings of the 28th Annual ACM Symposium on Applied Computing. New York: ACM, 2013: 164-166. |
| [18] | SENTHILKUMAR A. An Efficient FP-Growth Based Association Rule Mining Algorithm Using Hadoop MapReduce[J]. Indian Journal of Science and Technology, 2020, 13(34): 3561-3571. |
| [19] | WANG Chenshu, CHANG J Y. MISFP-Growth: Hadoop-Based Frequent Pattern Mining with Multiple Item Support[J]. Applied Sciences, 2019, 9(10): 2075-2086. |
| [20] | FOURNIER-VIGER P, NKAMBOU R, TSENG V S. RuleGrowth: Mining Sequential Rules Common to Several Sequences by Pattern-Growth[C]// ACM. Proceedings of the 2011 ACM Symposium on Applied Computing. New York: ACM, 2011: 956-961. |
| [21] | PEI Jian, HAN Jiawei, MORTAZAVI-ASL B, et al. Mining Sequential Patterns by Pattern-Growth: The PrefixSpan Approach[J]. IEEE Transactions on Knowledge and Data Engineering, 2004, 16(11): 1424-1440. |
| [1] | 张伟, 徐智刚, 陈云芳, 黄海平. 一种基于动态Docker的SDN蜜网设计与实现[J]. 信息网络安全, 2022, 22(4): 40-48. |
| [2] | 郑军, 聂榕, 王守信, 谭毓安. 基于Docker容器故障恢复的属性权重快照选择策略[J]. 信息网络安全, 2021, 21(5): 12-18. |
| [3] | 王鹃, 杨泓远, 樊成阳. 一种基于多阶段攻击响应的SDN动态蜜罐[J]. 信息网络安全, 2021, 21(1): 27-40. |
| [4] | 边曼琳, 王利明. 云环境下Docker容器隔离脆弱性分析与研究[J]. 信息网络安全, 2020, 20(7): 85-95. |
| [5] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [6] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||