信息网络安全 ›› 2022, Vol. 22 ›› Issue (11): 47-54.doi: 10.3969/j.issn.1671-1122.2022.11.006
基于OpenSSL密码软件的SM2算法加解密漏洞分析
- 1. 中国科学技术大学,合肥 230027
2. 电磁空间信息重点实验室,合肥 230027
3. 北京中科研究院,北京 100193
Analysis of SM2 Encryption and Decryption Vulnerability in OpenSSL
LIU Zhenya1,2, LIN Jingqiang1,2,3( )
)
- 1. University of Science and Technology, Hefei 230027, China
2. Key Laboratory of Electromagnetic Space Information, Hefei 230027, China
3. Beijing Research Institute of USTC, Beijing 100193, China
摘要:
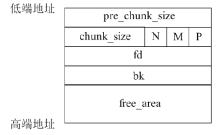
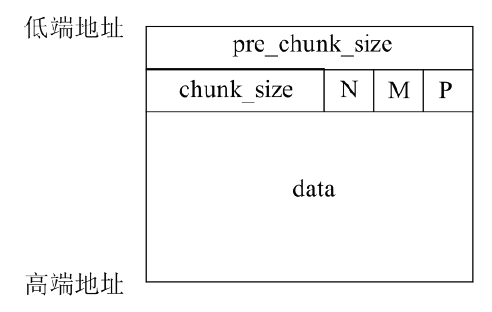
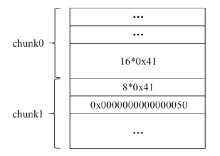
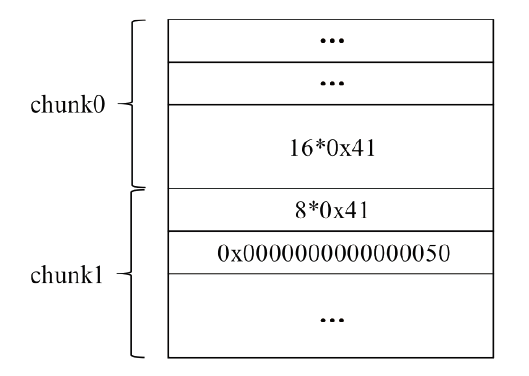
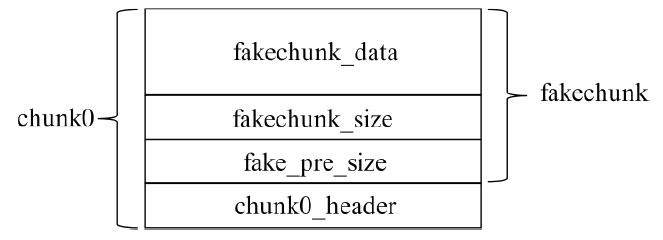
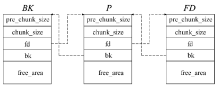
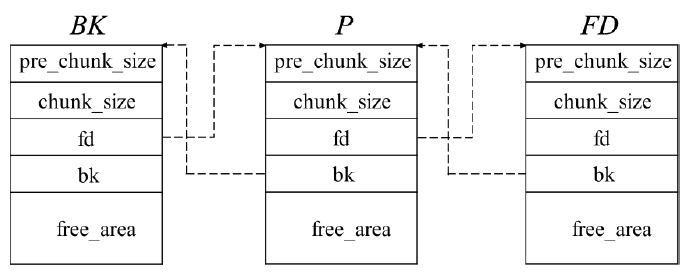
OpenSSL是一个广泛应用的开源库。2021年8月26日OpenSSL修补了一个缓冲区溢出漏洞,造成该漏洞的原因是SM2算法解密函数计算出的缓冲区可能小于实际的明文大小。文章首先结合OpenSSL源码,对缓冲区溢出的原理进行深入分析;然后根据溢出原理,对溢出攻击的可行性进行分析;最后设计实验对溢出攻击进行验证。由于SM2解密函数计算用于容纳明文的缓冲区大小时,没有考虑椭圆曲线上点的编码问题,当编码长度小于计算函数中的预设值时,就会导致缓冲区小于实际明文大小。攻击者根据这一特性可以快速穷举计算获取合适的椭圆曲线点,进而构造合适的密文进行缓冲区溢出攻击;并且能够使用同一个椭圆曲线点对持有不同公私钥对的SM2解密方进行缓冲区溢出攻击。
中图分类号: