信息网络安全 ›› 2020, Vol. 20 ›› Issue (8): 62-70.doi: 10.3969/j.issn.1671-1122.2020.08.008
云环境下支持属性撤销的无密钥托管属性基加密方案
- 北京工业大学信息学部,北京 100124
-
收稿日期:2020-05-13出版日期:2020-08-10发布日期:2020-10-20 -
通讯作者:宋硕 E-mail:18813157122@163.com -
作者简介:宋硕(1996—),女,山东,硕士研究生,主要研究方向为密码学和属性加密|张兴兰(1970—),女,山西,教授,博士,主要研究方向为密码学和安全协议等。 -
基金资助:国家自然科学基金(61801008)
Attribute-based Encryption Scheme without Key Escrow Supporting Attribute Revocation in Cloud Environment
- Department of Information, Beijing University of Technology, Beijing 100124, China
-
Received:2020-05-13Online:2020-08-10Published:2020-10-20 -
Contact:SONG Shuo E-mail:18813157122@163.com
摘要:
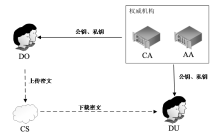
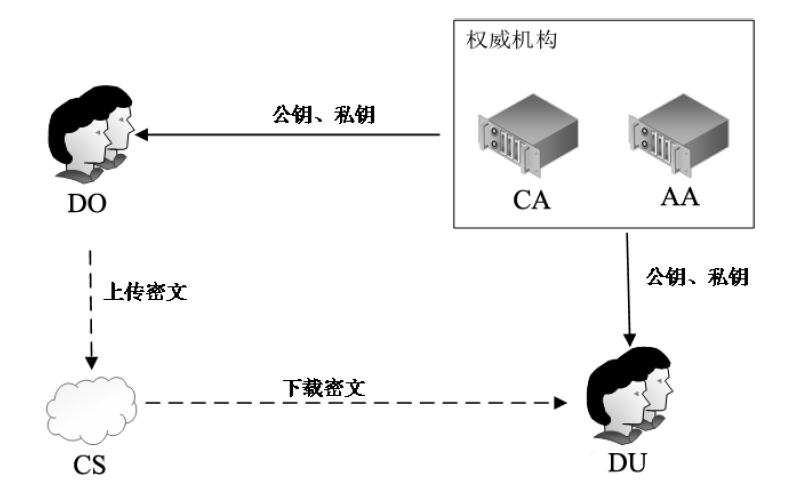
为解决ABE方案中存在的密钥托管问题和属性撤销的效率问题,文章提出支持解密外包和无密钥托管的属性基加密撤销方案。方案中,若用户的某个属性被撤销,属性权威首先根据最新的属性更新密钥生成同类复杂函数并广播给未撤销该属性的用户;然后用户利用同类复杂函数更新自己的密钥;最后属性权威根据属性更新密钥更新云服务器中的密文,实现属性撤销。该方案在属性撤销过程中减少了属性权威的计算量和通信量,同时利用半诚实的云服务器执行部分解密来减少用户的计算量,并引入中央权威和属性权威联合生成用户的密钥解决密钥托管问题。安全性证明和性能分析表明,该方案基于q-Parallel BDHE假设达到了标准模型下的选择明文安全,较同类方案具有更高的计算效率。
中图分类号:
引用本文
宋硕, 张兴兰. 云环境下支持属性撤销的无密钥托管属性基加密方案[J]. 信息网络安全, 2020, 20(8): 62-70.
SONG Shuo, ZHANG Xinglan. Attribute-based Encryption Scheme without Key Escrow Supporting Attribute Revocation in Cloud Environment[J]. Netinfo Security, 2020, 20(8): 62-70.
表1
本文方案与其他方案的性能比较
| 方案 | 密钥长度/bit | 密文长度/bit | 加密计算量 | 解密计算量 | 访问 策略 | 属性即时撤销 | 无密钥托管 | |
|---|---|---|---|---|---|---|---|---|
| 云服 务器 | 用户 | |||||||
| 文献[ | (|S|+ 5)|G| | (2|T|+ 3)|G| | (3|T|+ 2)E | (2|D|+ 1)P | E | LSSS | √ | √ |
| 文献[ | (|S|+ 2)|G| | (2|T|+ 2)|G| | (2|T|+ 2)E | × | (2|D|+ 1)P | 访问树 | √ | √ |
| 文献[ | (|S|+ 4)|G| | (2|T|+ 2)|G| | (3|T|+ 2)E | (6|D|+ 4)P | (2|D|+ 1)P | LSSS | √ | × |
| 文献[ | (2|S|+ 3)|G| | (|T|+ 2)|G| | (2|T|+ 2)E | (3|D|+ 1)P | E | LSSS | √ | × |
| 文献[ | (3|S|+ 1)|G| | (2|T|+ 2)|G| | (3|T|+ 2)E | 3|D|P | P | 访问树 | √ | × |
| 文献[ | (2|S|+ 1)|G| | (4|T|+ 1)|G| | (6|T|+ 1)E | 3|D|P+ 2|D|E | E | LSSS | × | √ |
| 文献[ | (2|S|+ 3)|G| | (3|T|+ 3)|G| | (7|T|+ 5)E | (3|D|+ 2)P | P | LSSS | √ | × |
| 文献[ | (2|S|+ 2)|G| | (5|T|+ 2)|G| | (5|T|+ 6)E | × | (3|D|+ 8)P | LSSS | × | × |
| 本文方案 | (|S|+ 2)|G| | (2|T|+ 2)|G| | (4|T|+ 2)E | 2|D|P | P | LSSS | √ | √ |
表1
| [1] | YU Shucheng, WANG Cong, REN Kui, et al. Attribute-based Data Sharing with Attribute Revocation[EB/OL]. http://www.researchgate.net/publication/221609318_Attribute_based_data_sharing_with_attribute_revocation, 2020-4-19. |
| [2] | HUR J, NOH D K. Attribute-based Access Control with Efficient Revocation in Data Outsourcing Systems[J]. IEEE Transactions on Parallel and Distributed Systems, 2011,22(7):1214-1221. |
| [3] | LI Xuejun, ZHANG Dan, LI Hui. Efficient Revocable Attribute-based Encryption Scheme[J]. Journal on Communications, 2019,40(6):32-39. |
| [4] | IBRAIMI L, PETKOVIC M, NIKOVA S, et al. Mediated Ciphertext- policy Attribute-based Encryption and Its Applications[C]// Springer. The 10th International Workshop on Information Security Applications, WISA 2009, August 25-27, 2009, Busan, Korea. Heidelberg: Springer, 2009: 309-323. |
| [5] | ZHANG Wenfang, CHEN Zhen, LIU Xudong, et al. CP-ABE Scheme Supporting Fine-grained Attribute Direct Revocation[J]. Journal of Software, 2019,30(9):2760-2771. |
| 张文芳, 陈桢, 刘旭东, 等. 支持细粒度属性直接撤销的CP-ABE方案[J]. 软件学报, 2019,30(9):2760-2771. | |
| [6] | GAO Jiaxin, SUN Jiameng, QIN Jing. Traceable Outsourcing Attribute-based Encryption with Attribute Revocation[J]. Journal of Computer Research and Development, 2019,56(10):2160-2169. |
| 高嘉昕, 孙加萌, 秦静. 支持属性撤销的可追踪外包属性加密方案[J]. 计算机研究与发展, 2019,56(10):2160-2169. | |
| [7] | LIANG Xiaohui, CAO Zhenfu, LIN Huang, et al. Provably Secure and Efficient Bounded Ciphertext Policy Attribute Based Encryption[C]// ACM. The 4th International Symposium on ACM Symposium on Information, Computer and Communications Security Computer(4th ASIACCS 2009), March 10-12, 2009, Sydney, Australia. New York: ACM, 2009: 343-352. |
| [8] | WANG Guangbo, LIU Haitao, WANG Chenlu, et al. Revocable Attribute-based Encryption in Cloud Storage[J]. Journal of Computer Research and Development, 2018,55(6):1190-1200. |
| 王光波, 刘海涛, 王晨露, 等. 云存储环境下可撤销属性加密[J]. 计算机研究与发展, 2018,55(6):1190-1200. | |
| [9] | SUN Lei, ZHAO Zhiyuan, WANG Jianhua, et al. Attribute-based Encryption Scheme Supporting Attribute Revocation in Cloud Storage Environment[J]. Journal on Communications, 2019,40(5):47-56. |
| 孙磊, 赵志远, 王建华, 等. 云存储环境下支持属性撤销的属性基加密方案[J]. 通信学报, 2019,40(5):47-56. | |
| [10] | LI Jiguo, YAO Wei, HAN Jinguang, et al. User Collusion Avoidance CP-ABE With Efficient Attribute Revocation for Cloud Storage[J]. IEEE Systems Journal, 2018,12(2):1767-1777. |
| [11] | QI Fang, LI Yanmei, TANG Zhe. Revocable and Traceable Key-policy Attribute-based Encryption Scheme[J]. Journal on Communications, 2018,39(11):63-69. |
| [12] | CHASE M, CHOW S S M. Improving Privacy and Security in Multi-Authority Attribute-Based Encryption[C]// ACM. ACM Conference on Computer and Communications Security(CCS 2009), November 9-13, 2009, Chicago, Illinois, USA. New York: ACM, 2009: 121-130. |
| [13] | ZHANG Xing, WEN Zilong, SHEN Qingni, et al. Accountable Attribute-based Encryption Scheme Without Key Escrow[J]. Journal of Computer Research and Development, 2015,52(10):2293-2303. |
| 张星, 文子龙, 沈晴霓, 等. 可追责并解决密钥托管问题的属性基加密方案[J]. 计算机研究与发展, 2015,52(10):2293-2303. | |
| [14] | ZHAO Zhiyuan. Research on Ciphertext-policy Attribute-based Encryption Schemes for Cloud Storage[D]. Zhengzhou: Information Engineering University, 2018. |
| 赵志远. 面向云存储的密文策略属性基加密方案研究[D]. 郑州:信息工程大学, 2018. | |
| [15] | DEHASPE L, RAEDT L. D. Mining Association Rules in Multiple Relations[C]// Springer. International Workshop on Inductive Logic Programming, September 17-20, 1997, Prague, Czech Republic. Heidelberg: Springer, 1997: 125-132. |
| [16] | JUNBEOM H. Improving Security and Efficiency in Attribute-based Data Sharing[J]. IEEE Transactions on Knowledge and Data Engineering, 2013,25(10):2271-2282. |
| [17] | CHOW S S M. Removing Escrow from Identity-based Encryption[J]. Lecture Notes in Computer Science Proc, 2009,5443:256-276. |
| [18] | BELENKIY M, CAMENISCH J, CHASE M, et al. Randomizable Proofs and Delegatable Anonymous Credentials[C]// Springer. Advances in Cryptology - CRYPTO 2009, 29th Annual International Cryptology Conference, August 16-20, 2009, Santa Barbara, CA, USA. Heidelberg: Springer, 2009: 108-125. |
| [19] | ZHANG Kai, MA Jianfeng, LI Hui, et al. Multi-authority Attribute-based Encryption with Efficient Revocation[J]. Journal on Communications, 2017,38(3):83-91. |
| 张凯, 马建峰, 李辉, 等. 支持高效撤销的多机构属性加密方案[J]. 通信学报, 2017,38(3):83-91. | |
| [20] | LIAN Huijie, WANG Qingxian, WANG Guangbo. Large Universe Ciphertext-policy Attribute-based Encryption with Attribute Level User Revocation in Cloud Storage[J]. The International Arab Journal of Information Technology, 2020,17(1):107-117. |
| [21] | MA Haiying, WANG Zhanjun, GUAN Zhijin. Efficient Ciphertext-policy Attribute-based Online/Offline Encryption with User Revocation[J]. Security and Communication Networks, 2019,19:1-11. |
| [1] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [2] | 李晓冉, 郝蓉, 于佳. 具有数据上传管控的无证书可证明数据持有方案[J]. 信息网络安全, 2020, 20(1): 83-88. |
| [3] | 闫玺玺, 叶青, 刘宇. 云环境下支持隐私保护和用户撤销的属性基加密方案[J]. 信息网络安全, 2017, 17(6): 14-21. |
| [4] | 荣星, 江荣. 一种基于混合属性的多授权中心云访问方案[J]. 信息网络安全, 2016, 16(11): 6-6. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||