信息网络安全 ›› 2016, Vol. 16 ›› Issue (4): 17-22.doi: 10.3969/j.issn.1671-1122.2016.04.003
基于可信根服务器的虚拟TCM密钥管理功能研究
- 1.北京工业大学计算机学院,北京 100124
2.可信计算北京市重点实验室,北京 100124
Research of Virtual Trusted Cryptography Module’s Secret Key Management Based on the Trusted Root Server
Guan WANG1,2, Huahao YUAN1,2( )
)
- 1. College of Computer, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
摘要:
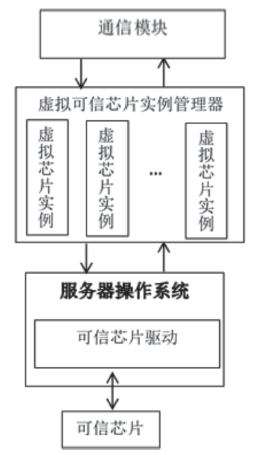
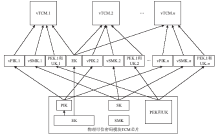
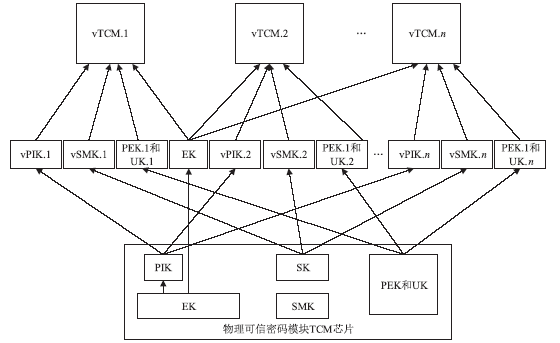
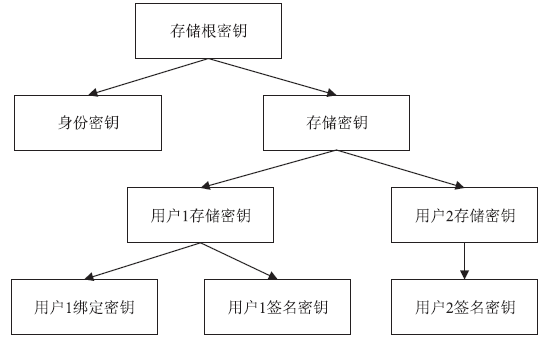
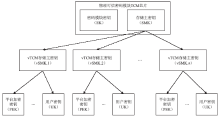
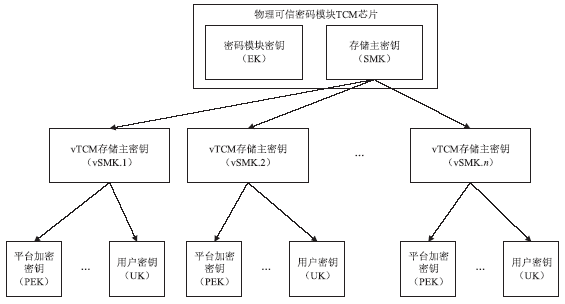
可信计算技术是保障云环境安全的一个重要手段。可信根服务器是利用可信计算技术保护虚拟机安全的一个很好的解决方案,这种方案的特征在于以可信芯片为基础,通过虚拟化技术产生多个虚拟可信芯片为云环境中的虚拟机提供可信服务。虚拟的可信芯片实例都集中在可信根服务器上由管理器进行统一管理。文章将国产的可信密码模块TCM芯片作为可信根服务器中的物理可信根,以可信计算密码支撑平台为基础来进行研究。文章分析了可信密码模块芯片TCM中各种密钥的特点,对可信根服务器中的密钥管理功能进行了研究,针对密钥的产生、存储和加载提出了方案。在该方案中,所有的虚拟可信密码模块vTCM密钥均通过vTCM管理器调用物理可信密码模块TCM芯片来产生,保证了密钥产生的规范性。
中图分类号: