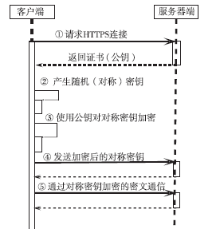
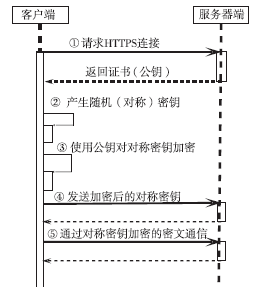
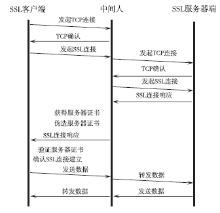
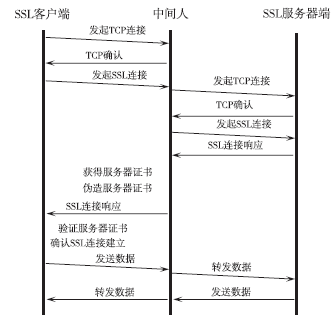
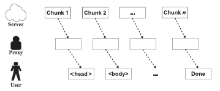
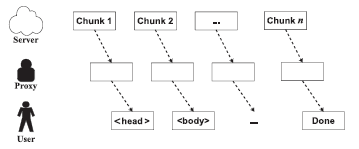
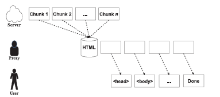
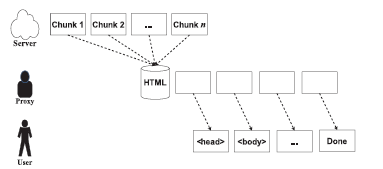
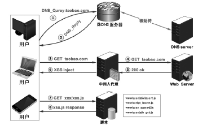
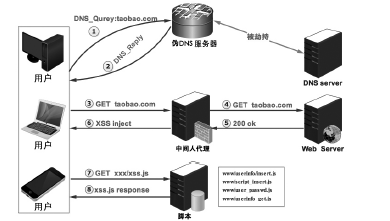
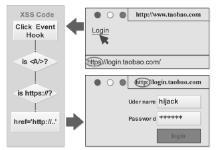
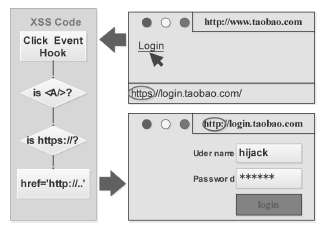
信息网络安全 ›› 2016, Vol. 16 ›› Issue (3): 15-20.doi: 10.3969/j.issn.1671-1122.2016.03.003
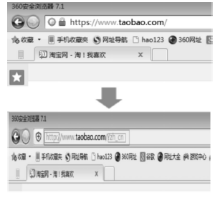
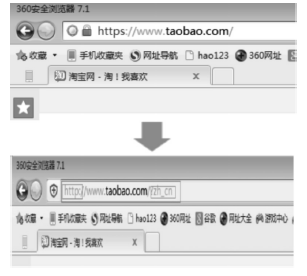
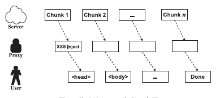
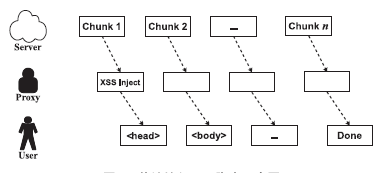
针对HTTPS的Web前端劫持及防御研究
- 重庆邮电大学通信学院,重庆 400065
Research on the Web Front-end Hijacking and Defense against HTTPS
Guofeng ZHAO( ), Yong CHEN, Xinheng WANG
), Yong CHEN, Xinheng WANG
- College of Communication, Chongqing University of Posts and Telecommunications, Chongqing 400065, China