信息网络安全 ›› 2015, Vol. 15 ›› Issue (2): 71-76.doi: 10.3969/j.issn.1671-1122.2015.02.012
多水印技术及其在数字作品交易中的应用
- 解放军北京军区总医院信息科,北京 100700
-
收稿日期:2015-01-13出版日期:2015-02-10发布日期:2015-07-05 -
作者简介:作者简介: 苏娇娆(1976-),女,北京,工程师,硕士,主要研究方向:数字水印。
Research on Multiple Watermarking and Application in Digital Works Transaction System
- Information Department of PLA Beijing Military General Hospital, Beijing 100700, China
-
Received:2015-01-13Online:2015-02-10Published:2015-07-05
摘要:
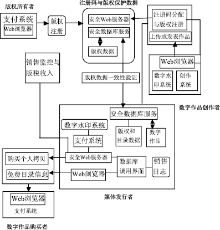
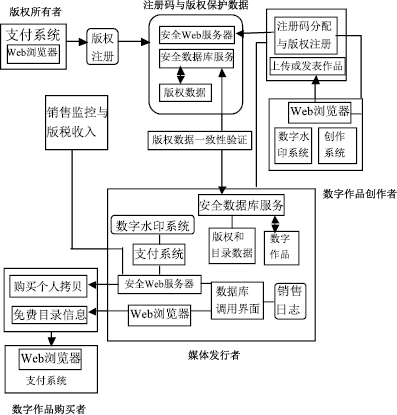
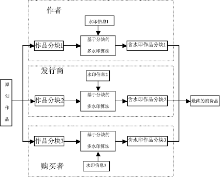
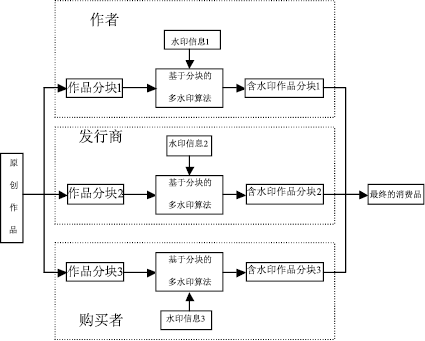
随着数字时代的到来,数字水印技术在版权保护、广播监视、内容认证等领域所起的作用越来越重要。经过多年的发展,数字水印技术在理论、算法和应用等各个方面都取得了很大的进展。然而,已有的水印研究大都针对单水印技术,多水印技术的研究相对较少。多水印技术有其特殊的应用场合和应用价值,针对多水印技术及其应用展开研究具有重要的意义。文章首先研究了多次嵌入、分块嵌入、融合嵌入和基于扩展变换的嵌入等典型多水印算法的优缺点;然后分析了数字作品交易过程中的版权和盗版等问题,以选定的分块多水印算法为基础,设计并实现了基于多水印技术的数字作品交易系统。该系统在原创作品中首先加入包含作者身份和创作时间等信息的水印;然后将作品转交给发行商,在其中嵌入发行商的相关信息;当用户购买作品时,再将包含用户信息的水印嵌入作品中卖给用户。文章通过实验验证了所设计方案的有效性和鲁棒性。文章最后展望了多水印技术的前景。
中图分类号:
引用本文
苏娇娆. 多水印技术及其在数字作品交易中的应用[J]. 信息网络安全, 2015, 15(2): 71-76.
SU Jiao-rao. Research on Multiple Watermarking and Application in Digital Works Transaction System[J]. Netinfo Security, 2015, 15(2): 71-76.
使用本文
| [1] | Tirkel A Z,Rankin G A,Van Schyndel R M,et al. Electronic Watermark[C]//Digital Image ComputingTechnology and Applications DICTA 93. Sidney: Maquarie University, 1993: 666-673. |
| [2] | 孙圣和,陆哲明,牛夏牧.数字水印技术及应用[M].北京:科学出版社,2004. |
| [3] | 王颖,肖俊,王蕴红.数字水印原理与技术[M].北京:科学出版社,2007. |
| [4] | Chen B, Wornell G W.Provably Robust Digital Watermarking[C]//Proc. of the SPIE: Multimedia Systems and ApplicationsⅡ.Bellingham:Society of Photo-Optical Instrumentation Engineers, 1999, (3845): 43-54. |
| [5] | Schyndel R G, Tirkel A Z, Osborne C F.A Digital Watermark[C]// First IEEE International Image Processing Conference. Austin: University of Texas, 1994, (2): 86-90. |
| [6] | Cox I J, Miller M L.数字水印[M].王颖,黄志蓓,译.北京:电子工业出版社,2003. |
| [7] | Cravers, Menmonn, Yeobl. Resolving Rightful Ownerships with Invisible Watermarking Techniques[J]. IEEE Journal on Seclected Areas in Communications. 1998, 16(4): 573-586. |
| [8] | Eggers J J, Su J K, Girod B.A Blind Watermarking Scheme Based on Structured Codebooks[J]. IEE Colloquium (Digest), 2000, (39): 27-47. |
| [9] | Watson A B.DCT Quantization Matrices Visually Optimized for Individual Images[J].Human Vision,Visual Processing and Digital Display.1993,(1):202-216. |
| [10] | Ahumada A J, Peterson H A.Luminance-Model-Based DCT Quantization for Color Image Compression[C]// Proceeding of the SPIE. 1992, (1666): 365-374. |
| [11] | Cox I J, Kilian J, Leighton T, et al.Secure Spread Spectrum Watermarking for Images, Audio and Video[C]// Proceedings of the 1996 IEEE International Conference in Image Processing. CA: IEEE, Los Alamitos, 1996,(3): 243-246. |
| [12] | 杨德刚,陈永红.在数字图像中嵌入多水印的算法研究[J]. 计算机工程与应用,2005 ,41(21):41-44. |
| [13] | 杨洋,陈小平. 一种数字音频多水印算法[J]. 苏州大学学报:工学版,2004, 24(1):18-22. |
| [14] | 马苗,田红鹏.一种多类多水印方案[J],西南交通大学学报, 2003,38(2): 235-239. |
| [15] | 李京兵,黄席樾 .一种鲁棒的多水印嵌入和检测算法与仿真[J]. 计算机仿真,2005,22(9):254-258. |
| [16] | 张伟,高珍,张志浩.基于正交向量组的多水印算法研究[J].计算机工程. 2006,32(4) :174-176. |
| [17] | 李秋珍, 邹复好.基于CDMA技术的多水印算法[J].计算机应用,2005 ,25(11) :2538-2540. |
| [18] | Xiao Jun, Wang Ying. Multiple Watermarking based on Spread Transform[C]// 8th International Conference on Signal Processing(ICSP2006),2006,(4):2640-2643. |
| [19] | Cox I J, Kilian J, Leighton T,et al.Secure spread spectrum watermarking for multimedia[J]. IEEE Trans. on Image Processing, 1997,6(12):1673-1687. |
| [20] | 张良,张军,宗杰.数字图像频率域多水印共存技术研究[J].电视技术,2003 ,(4): 66-67. |
| [21] | Mintzer F, Braudaway G W.If one watermark is good,are more better?[C]// IEEE International Conference on Acoustics,Speech and Signal Processing,1999:2067-2069. |
| [22] | Wu M, Tang E, Liu B.Data Hiding in Digital Binary Image[C]// IEEE International Conference on Multi-Media and Expo. New York: Los Alamitos, 2000, (1): 393-396. |
| [23] | Ahumada A J, Peterson H A.Luminance-Model-Based DCT Quantization for Color Image Compression[C]// Proceeding of the SPIE,1992,(1666):365-374. |
| [24] | 王丽娜,张焕国.信息隐藏技术与应用[M].武汉:武汉大学出版社,2003. |
| [25] | Lu H, Kot A C, Cheng J.Secure Data Hiding in Binary Document Images for Authentication[C]// Proceedings of the 2003 IEEE International Symposium on Circuits and Systems. Bangkok: Institute of Electrical and Electronics Engineers Inc, 2003,(3): 806-809. |
| [1] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [2] | 仝鑫, 金波, 王斌君, 翟晗名. 融合对抗增强和多任务优化的恶意短信检测方法[J]. 信息网络安全, 2023, 23(10): 21-30. |
| [3] | 李宏军, 郎为民, 邓刚. 一种高效的大数据中心完整性检查方案研究[J]. 信息网络安全, 2016, 16(5): 1-8. |
| [4] | 何冰;苏变玲. 基于Krawtchouk不变矩的零水印算法研究[J]. , 2013, 13(7): 0-0. |
| [5] | 袁静;任卫红;朱建平. 等级测评中关键安全保护功能有效性测评技术研究[J]. , 2013, 13(1): 0-0. |
| [6] | 唐刚;朱信铭;程晓妮. 数据加密有效性测试的探究[J]. , 2012, 12(Z): 0-0. |
| [7] | 李馥娟. 从频发的信息泄露事件分析Web服务安全[J]. , 2012, 12(7): 0-0. |
| [8] | 卓见;郑世慧;徐国胜. FastICA图像水印改进算法[J]. , 2012, 12(6): 0-0. |
| [9] | 杨晓涛;张笈;温英新;王莎莎. 基于分块小波变换的数字视频水印算法[J]. , 2012, 12(12): 0-0. |
| [10] | 何冰;朱志平. 基于奇异值分解的抗几何攻击鲁棒性盲水印算法[J]. , 2012, 12(11): 0-0. |
| [11] | 孙国梓;俞超;陈丹伟;金仙力. 基于瀑布模型的可信取证方法[J]. , 2009, 9(7): 0-0. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||
|
全文 14
|
|
|||||||||||||||||||||||||||||||||||||||||||||
|
摘要 200
|
|
|||||||||||||||||||||||||||||||||||||||||||||