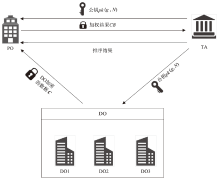
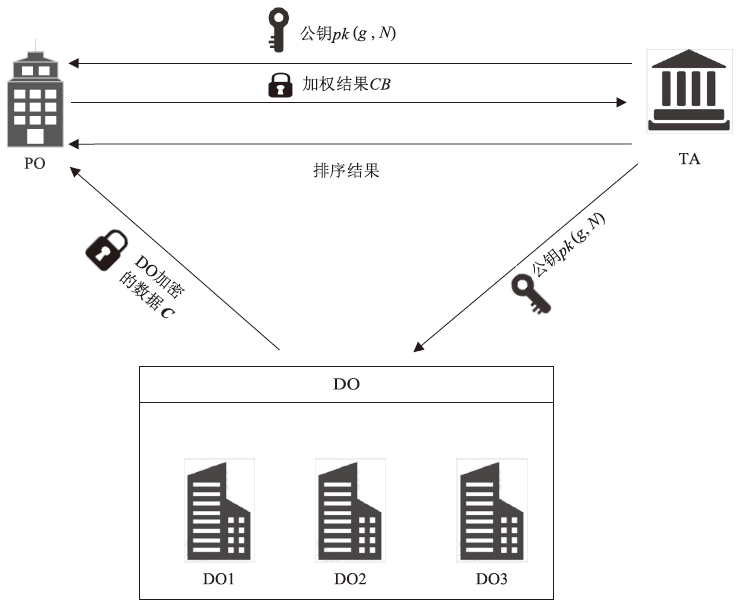
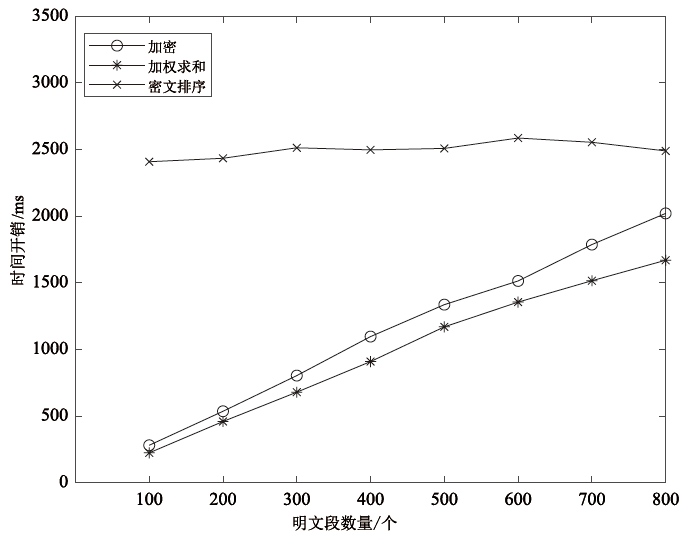
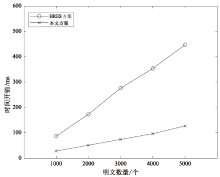
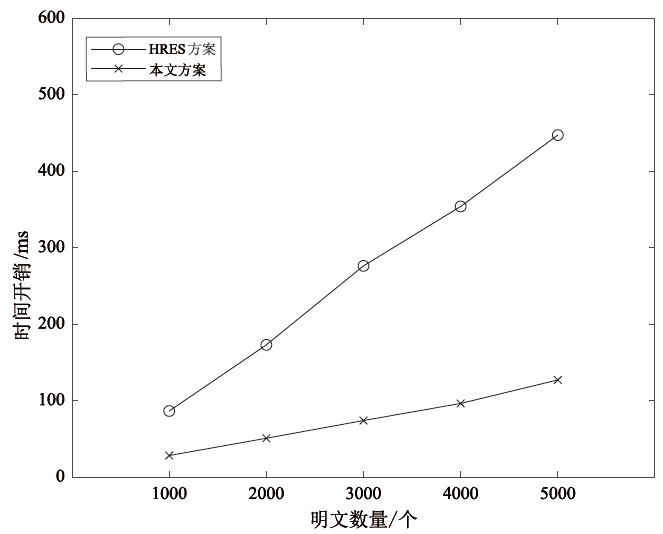
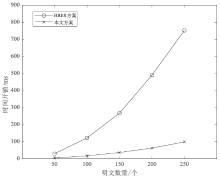
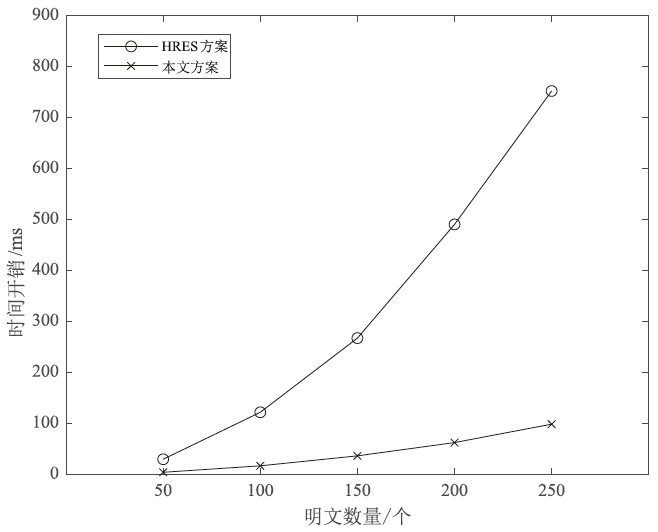
Netinfo Security ›› 2025, Vol. 25 ›› Issue (12): 1975-1989.doi: 10.3969/j.issn.1671-1122.2025.12.012
Previous Articles Next Articles
Privacy-Preserving Sorting Scheme Based on Paillier Homomorphic Encryption
WANG Houzhen1,2( ), JIANG Haolang1, LIU Jichen1, TU Hang1
), JIANG Haolang1, LIU Jichen1, TU Hang1
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Advanced Cryptography and System Security Key Laboratory of Sichuan Province, Chengdu 610054, China
-
Received:2025-01-24Online:2025-12-10Published:2026-01-06 -
Contact:WANG Houzhen E-mail:whz@whu.edu.cn
CLC Number:
Cite this article
WANG Houzhen, JIANG Haolang, LIU Jichen, TU Hang. Privacy-Preserving Sorting Scheme Based on Paillier Homomorphic Encryption[J]. Netinfo Security, 2025, 25(12): 1975-1989.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.12.012
| 方案 | 计算开销 | 加密算法 | 困难性假设 |
|---|---|---|---|
| 文献[11]方案 | Paillier | 复合剩余类 | |
| 文献[12]方案 | Paillier | 复合剩余类 | |
| 文献[13]方案 | Paillier | 复合剩余类 | |
| 文献[15]方案 | BCP | 离散对数困难 | |
| 本文方案 | & 3.5{{\log }_{2}}N+2{{\log }_{2}}(N+1)+ \\ & 2{{\log }_{2}}\alpha +1 \\ \end{align}$ | Paillier | 复合剩余类 |
| 方案对比 | HRES方案 | 本文方案 | |
|---|---|---|---|
| 同态特性 | 满足加法同态特性 | 满足加法同态特性 | |
| 角色 | 用户、数据服务提供方、安全控制服务器 | DO、PO、TA | |
| 明文 加密 | 密钥生成 | 所有角色均生成一对用户公私钥;数据服务提供方和安全控制服务器通过密钥交换协议生成公钥PK | 由TA生成算法的公钥和私钥,不需要额外生成新的 密钥 |
| 加密方式 | 使用PK和用户公钥加密 | 明文仅能由DO使用公钥 加密 | |
| 密文 排序 | 密文要求 | 仅能比较使用公钥PK加密的密文 | 可以比较DO加密的密文,也可以比较PO加权求和 |
| 实现方式 | 对密文进行同态减法操作,再由数据服务提供方和安全控制服务器共同判断新密文的正负性,最终由发起密文排序请求的用户判断密文排序结果 | 由TA使用私钥对两条密文的比值进行解密,根据解密结果判断密文之间的大小 关系 | |
| [1] | BOLDYREVA A, CHENETTE N, LEE Y, et al. Order-Preserving Symmetric Encryption[C]// Springer. The 28th Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2009). Heidelberg: Springer, 2009: 224-241. |
| [2] | BOLDYREVA A, CHENETTE N, O’NEILL A. Order-Preserving Encryption Revisited: Improved Security Analysis and Alternative Solutions[C]// Springer. The 31st Annual Cryptology Conference (CRYPTO 2011). Heidelberg: Springer, 2011: 578-595. |
| [3] | YUM D H, KIM D S, KIM J S, et al. Order-Preserving Encryption for Non-Uniformly Distributed Plaintexts[C]// Springer. Information Security Applications (WISA 2011). Heidelberg: Springer, 2011: 84-97. |
| [4] | BONEH D, LEWI K, RAYKOVA M, et al. Semantically Secure Order-Revealing Encryption: Multi-Input Functional Encryption without Obfuscation[C]// Springer. The 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2015). Heidelberg: Springer, 2015: 563-594. |
| [5] | CHENETTE N, LEWI K, WEIS S A, et al. Practical Order-Revealing Encryption with Limited Leakage[C]// Springer. Fast Software Encryption:The 23rd International Conference. Heidelberg: Springer, 2016: 474-493. |
| [6] | CASH D, LIU Fenghao, O’NEILL A, et al. Reducing the Leakage in Practical Order-Revealing Encryption[EB/OL]. (2016-06-28)[2024-10-25]. https://eprint.iacr.org/2016/661. |
| [7] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computation, 1978, 4(11): 169-180. |
| [8] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer. The 18th International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 1999). Heidelberg: Springer, 1999: 223-238. |
| [9] | GENTRY C, HALEVI S. Implementing Gentry’s Fully-Homomorphic Encryption Scheme[C]// Springer. The 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques (EUROCRYPT 2011). Heidelberg: Springer, 2011: 129-148. |
| [10] | CHATTERJEE A, KAUSHAL M, SENGUPTA I. Accelerating Sorting of Fully Homomorphic Encrypted Data[C]// Springer. The 14th International Conference on Cryptology (INDOCRYPT 2013). Heidelberg: Springer, 2013: 262-273. |
| [11] |
LI Shundong, WANG Daoshun. Efficient Secure Multiparty Computation Based on Homomorphic Encryption[J]. Acta Electronica Sinica, 2013, 41(4): 798-803.
doi: 10.3969/j.issn.0372-2112.2013.04.029 |
|
李顺东, 王道顺. 基于同态加密的高效多方保密计算[J]. 电子学报, 2013, 41(4): 798-803.
doi: 10.3969/j.issn.0372-2112.2013.04.029 |
|
| [12] | ZUO Xiangjian, LI Shundong, YANG Xiaoli. An Efficient Homomorphic Encryption Based Solution to Millionaires’ Problem[J]. Journal of Chinese Computer Systems. 2017, 38(3): 455-459. |
| 左祥建, 李顺东, 杨晓莉. 同态加密的百万富翁问题高效解决方案[J]. 小型微型计算机系统, 2017, 38(3): 455-459. | |
| [13] |
LI Shundong, ZUO Xiangjian, YANG Xiaoli, et al. Secure Vector Dominance Protocol and Its Applications[J]. Acta Electronica Sinica, 2017, 45(5): 1117-1123.
doi: 10.3969/j.issn.0372-2112.2017.05.014 |
|
李顺东, 左祥建, 杨晓莉, 等. 安全向量优势协议及其应用[J]. 电子学报, 2017, 45(5): 1117-1123.
doi: 10.3969/j.issn.0372-2112.2017.05.014 |
|
| [14] |
LIU Ximeng, CHOO K R, DENG R H, et al. Efficient and Privacy-Preserving Outsourced Calculation of Rational Numbers[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 15(1): 27-39.
doi: 10.1109/TDSC.2016.2536601 URL |
| [15] | DING Wenxiu, YAN Zheng, DENG R H. Encrypted Data Processing with Homomorphic Re-Encryption[J]. Information Sciences, 2017(409): 35-55. |
| [16] | ZHENG Yandong, LU Rongxing, YANG Xue, et al. Achieving Efficient and Privacy-Preserving Top-K Query over Vertically Distributed Data Sources[C]// IEEE. 2019 IEEE International Conference on Communications (ICC 2019). New York: IEEE, 2019: 1-6. |
| [17] | LI Yuxi, ZHOU Fucai, XU Jian, et al. Multiple-Keyword Encrypted Search with Relevance Ranking on Dual-Server Model[J]. Journal of Computer Research and Development, 2018, 55(10): 2149-2163. |
| 李宇溪, 周福才, 徐剑, 等. 双服务器模型下支持相关度排序的多关键字密文搜索方案[J]. 计算机研究与发展, 2018, 55(10): 2149-2163. | |
| [18] | HUANG Daxin, GAN Qingqing, WANG Xiaoming, et al. Toward Comparable Homomorphic Encryption for Crowd-Sensing Network[EB/OL]. (2020-06-30)[2024-10-25]. https://ia.cr/2020/806. |
| [19] | JOST C, LAM H, MAXIMOV A, et al. Encryption Performance Improvements of the Paillier Cryptosystem[EB/OL]. (2015-09-08)[2024-10-25]. https://ia.cr/2015/864. |
| [20] | BARKER E, CHEN Lidong, ROGINSKY A, et al. Recommendation for Pair-Wise Key-Establishment Using Integer Factorization Cryptography[R]. Gaithersburg: National Institute of Standards and Technology, SP 800-56B Rev. 2, 2018. |
| [21] | LIN H Y, TZENG W G. An Efficient Solution to the Millionaires’ Problem Based on Homomorphic Encryption[C]// Springer. Applied Cryptography and Network Security (ACNS 2005). Heidelberg: Springer, 2005: 456-466. |
| [22] | DESCHAMPS J P. Hardware Implementation of Finite-Field Arithmetic[M]. New York: McGraw-Hill Education, 2009. |
| [23] | LYU Kewei, CHEN Chi. Research on Proactive Generation Protocol of Beaver Triples[J]. Netinfo Security, 2022, 22(12): 16-24. |
| 吕克伟, 陈驰. Beaver三元组主动性生成协议研究[J]. 信息网络安全, 2022, 22(12): 16-24. | |
| [24] |
DAMGARD I, JURIK M, NIELSEN J B. A Generalization of Paillier’s Public-Key System with Applications to Electronic Voting[J]. International Journal of Information Security, 2010, 9(6): 371-385.
doi: 10.1007/s10207-010-0119-9 URL |
| [25] | LI Liang, ZHANG Yinghui, DENG Kaixin, et al. Privacy-Aware Power Injection in 5G Smart Grid[J]. Netinfo Security, 2018, 18(12): 87-92. |
| 李梁, 张应辉, 邓恺鑫, 等. 5G智能电网中具有隐私保护的电力注入系统[J]. 信息网络安全, 2018, 18(12): 87-92. |
| [1] | SHI Yijuan, ZHOU Danping, FAN Lei, LIU Yin. Secure Multi-Party Computation Protocol Based on Trusted Execution Environment [J]. Netinfo Security, 2025, 25(9): 1439-1446. |
| [2] | TIAN Haibo, LI Yitong, DU Yusong. General Construction and Instantiation for Query Request Bandwidth Optimization in Homomorphic Encryption-Based PIR [J]. Netinfo Security, 2025, 25(7): 1092-1102. |
| [3] | QIN Jinlei, KANG Yimin, LI Zheng. Lightweight Fine-Grained Multi-Dimensional Multi-Subset Privacy-Preserving Data Aggregation for Smart Grid [J]. Netinfo Security, 2025, 25(5): 747-757. |
| [4] | QIN Siying, SUN Bing, FU Shaojing, TANG Xiaomei. Key Switching for Somewhat Homomorphic Encryption Based on RLWR [J]. Netinfo Security, 2025, 25(12): 1961-1974. |
| [5] | CHEN Chunling, LU Xianhui, WANG Ruida, BAI Jikang, XIE Shubing. Research on Gate Bootstrapping in Fully Homomorphic Encryption [J]. Netinfo Security, 2025, 25(11): 1691-1706. |
| [6] | ZHANG Yang, WEI Rong, YOU Qidi, JIANG Xiaotong. An E-Voting Protocol Based on Multi-Key Homomorphic Encryption [J]. Netinfo Security, 2025, 25(1): 88-97. |
| [7] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [8] | LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(9): 1375-1385. |
| [9] | GUO Qian, ZHAO Jin, GUO Yi. Hierarchical Clustering Federated Learning Framework for Personalized Privacy-Preserving [J]. Netinfo Security, 2024, 24(8): 1196-1209. |
| [10] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| [11] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [12] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [13] | LAI Chengzhe, ZHAO Yining, ZHENG Dong. A Privacy Preserving and Verifiable Federated Learning Scheme Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(1): 93-105. |
| [14] | LI Zengpeng, WANG Mei, CHEN Mengjia. Research of New Forms of Pseudorandom Random Function [J]. Netinfo Security, 2023, 23(5): 11-21. |
| [15] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||