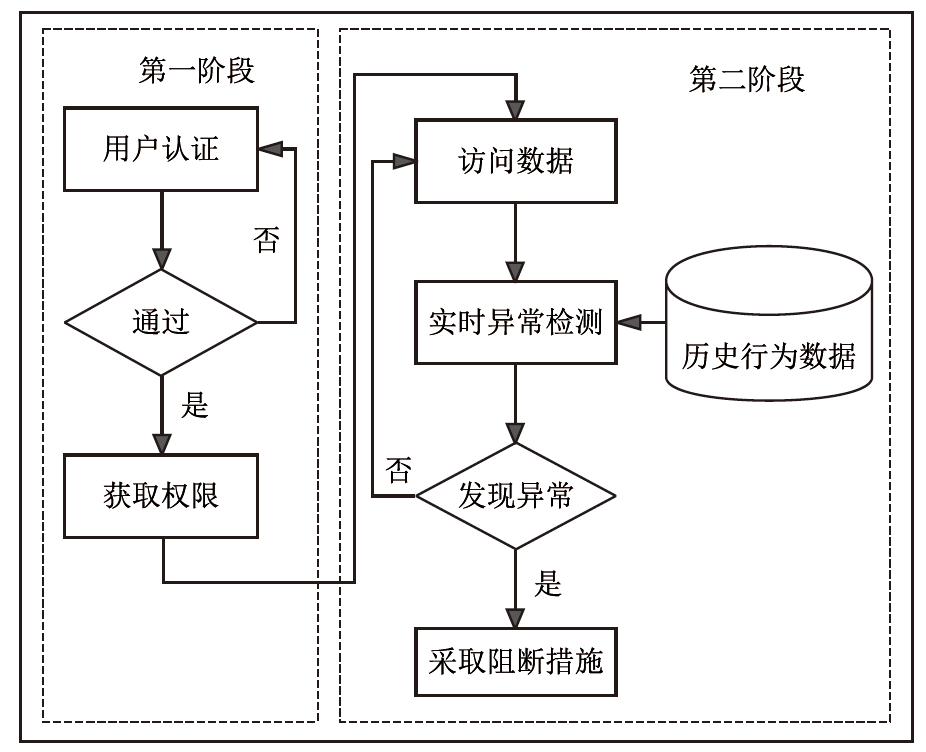
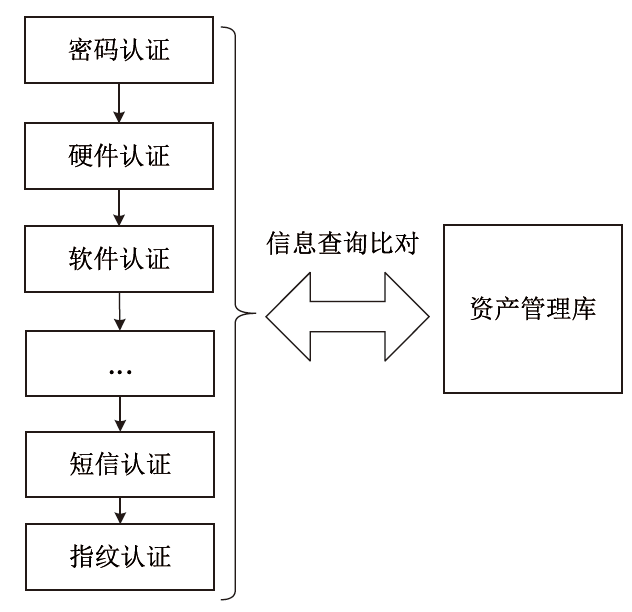
Netinfo Security ›› 2024, Vol. 24 ›› Issue (11): 1632-1642.doi: 10.3969/j.issn.1671-1122.2024.11.003
Previous Articles Next Articles
Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems
CHEN Baogang1, ZHANG Yi1, YAN Song2( )
)
- 1. Department of Automation, Tsinghua University, Beijing 100084, China
2. School of Traffic Management, People’s Public Security University of China, Beijing 100038, China
-
Received:2024-08-10Online:2024-11-10Published:2024-11-21
CLC Number:
Cite this article
CHEN Baogang, ZHANG Yi, YAN Song. Research on Multi-Factor Continuous Trustworthy Identity Authentication for Users in Civil Aviation Air Traffic Control Operational Information Systems[J]. Netinfo Security, 2024, 24(11): 1632-1642.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.11.003
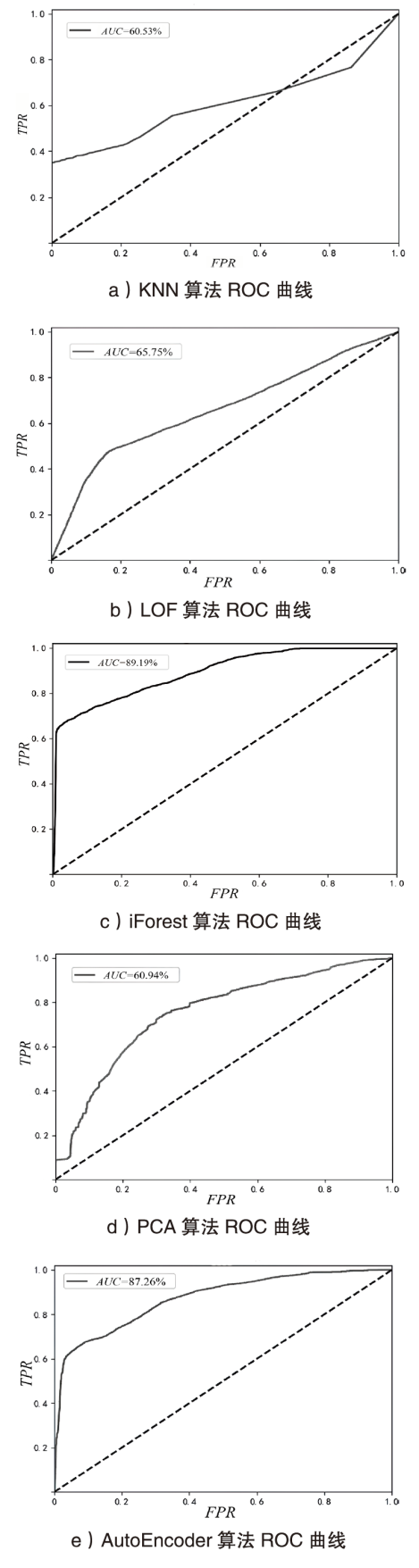
| 方法 | 流量分组 | 超参数 | 异常识别率 | 异常误报率 | AUC | |
|---|---|---|---|---|---|---|
| KNN | 全流量 | 邻近点 | 10 | 35.57% | 8.67% | 60.21% |
| 30 | 31.27% | 9.20% | 59.46% | |||
| 50 | 29.82% | 9.12% | 58.61% | |||
| 70 | 29.59% | 8.96% | 58.11% | |||
| 90 | 29.81% | 9.14% | 58.40% | |||
| 分组流量 | 10 | 39.57% | 5.21% | 60.53% | ||
| 30 | 39.12% | 5.44% | 60.23% | |||
| 50 | 40.51% | 6.83% | 58.90% | |||
| 70 | 40.11% | 6.61% | 57.98% | |||
| 90 | 39.97% | 7.14% | 57.97% | |||
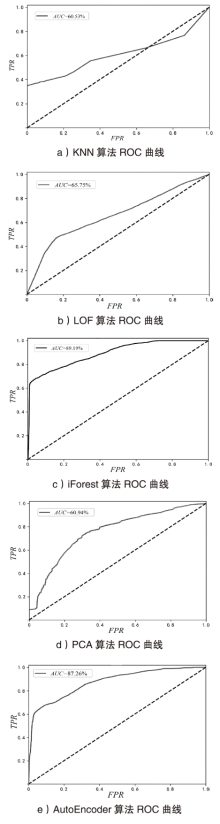
| LOF | 全流量 | 250 | 26.70% | 9.39% | 61.50% | |
| 500 | 32.63% | 9.17% | 65.75% | |||
| 1000 | 32.28% | 9.19% | 65.09% | |||
| 1500 | 32.28% | 9.19% | 64.70% | |||
| 2000 | 32.47% | 9.18% | 64.48% | |||
| 分组流量 | 250 | 32.13% | 9.19% | 64.50% | ||
| 500 | 31.50% | 9.22% | 63.67% | |||
| 1000 | 28.04% | 9.34% | 61.20% | |||
| 1500 | 23.62% | 9.50% | 56.90% | |||
| 2000 | 22.77% | 9.53% | 58.73% | |||
| iForest | 全流量 | 决策树数量 | 50 | 52.01% | 8.43% | 84.83% |
| 100 | 48.95% | 8.50% | 83.16% | |||
| 150 | 56.19% | 8.30% | 84.53% | |||
| 200 | 58.20% | 8.22% | 85.32% | |||
| 250 | 57.21% | 8.27% | 84.37% | |||
| 分组流量 | 50 | 64.67% | 7.52% | 88.13% | ||
| 100 | 64.70% | 7.84% | 88.66% | |||
| 150 | 64.19% | 7.77% | 88.34% | |||
| 200 | 64.49% | 7.71% | 89.19% | |||
| 250 | 64.68% | 7.74% | 88.92% | |||
| PCA | 全流量 | — | 31.97% | 9.20% | 75.26% | |
| 分组流量 | — | 47.23% | 8.62% | 60.94% | ||
| AutoEncoder | 全流量 | — | 29.03% | 9.31% | 76.20% | |
| 分组流量 | — | 43.22% | 8.63% | 87.26% | ||
| 算法 | 特征工程 | 异常识别率 | 异常误报率 |
|---|---|---|---|
| KNN | 聚合数据 | 56.03% | 11.22% |
| 聚合数据+时段分组 | 82.17% | 4.04% | |
| 随机森林 | 聚合数据 | 91.60% | 2.64% |
| 聚合数据+时段分组 | 91.80% | 2.76% | |
| GBDT | 聚合数据 | 90.53% | 2.26% |
| 聚合数据+时段分组 | 88.87% | 1.00% | |
| ExtraTrees | 聚合数据 | 88.60% | 0.84% |
| 聚合数据+时段分组 | 88.60% | 0.84% | |
| Adaboost | 聚合数据 | 19.80% | 4.18% |
| 聚合数据+时段分组 | 91.37% | 2.50% | |
| GaussianNB | 聚合数据 | 9.99% | 5.59% |
| 聚合数据+时段分组 | 91.83% | 8.04% | |
| CategoricalNB | 聚合数据 | 16.33% | 6.00% |
| 聚合数据+时段分组 | 86.80% | 0.60% |
| [1] | International Civil Aviation Organization. CYBERSECURITY ACTION PLAN-Second Edition[EB/OL]. [2024-05-11]. https://www.icao.int/aviationcybersecurity/Documents/CYBERSECURITY ACTION PLAN-Second edition.EN.pdf. |
| [2] | XU Dandan, LI Peiyu, ZHANG Shiqian, et al. Research on Multi-Factor Authentication Method in Unified Identity Authentication System[J]. Journal of Fuzhou University(Natural Science Edition), 2023, 51(5): 616-620. |
| 许丹丹, 李沛谕, 张世倩, 等. 统一身份认证系统中的多因子身份认证方法[J]. 福州大学学报(自然科学版), 2023, 51(5):616-620. | |
| [3] | OMETOV A, BEZZATEEV S, MÄKITALO N, et al. Multi-Factor Authentication: A Survey[J]. Cryptography, 2018, 2(1): 1-31. |
| [4] | ZHANG Meng, YIN Qiqi. Research Progress of Static Password Authentication Technology[J]. Cyberspace Security, 2018, 9(7): 11-14. |
| 张猛, 尹其其. 静态口令认证技术研究进展[J]. 网络空间安全, 2018, 9(7):11-14. | |
| [5] | ZHAO Zhihui, LI Xinshe. Research on Password-Based Identity Authentication System[J]. Network Security Technology & Application, 2009(4): 18-19. |
| 赵志辉, 李新社. 基于口令的身份认证系统研究[J]. 网络安全技术与应用, 2009(4):18-19. | |
| [6] | YOU Lin. A Survey on Biometric Cryptographic Technology[J]. Journal of Hangzhou Dianzi University(Natural Sciences), 2015, 35(3): 1-17. |
| 游林. 生物特征密码技术综述[J]. 杭州电子科技大学学报(自然科学版), 2015, 35(3):1-17. | |
| [7] |
LI Fujuan, MA Zhuo, WANG Qun. Survey on Identity Management in Blockchain Systems[J]. Computer Engineering and Applications, 2024, 60(1): 57-73.
doi: 10.3778/j.issn.1002-8331.2302-0189 |
|
李馥娟, 马卓, 王群. 区块链系统身份管理机制研究综述[J]. 计算机工程与应用, 2024, 60(1):57-73.
doi: 10.3778/j.issn.1002-8331.2302-0189 |
|
| [8] | ZHAO Liang, MAO Bing, XIE Li. Survey of Acess Control[J]. Computer Engineering, 2004, 30(2): 1-2. |
| 赵亮, 茅兵, 谢立. 访问控制研究综述[J]. 计算机工程, 2004, 30(2):1-2. | |
| [9] | LIU Long, CHEN Jianbin, XUE Ruisi. Research and Design of Data Permission Management[J]. Value Engineering, 2013, 32(31): 215-216. |
| 刘龙, 陈建斌, 薛锐思. 数据权限管理的研究和设计[J]. 价值工程, 2013, 32(31):215-216. | |
| [10] | POTTIER F, SKALKA C, SMITH S. A Systematic Approach to Static Access Control[J]. ACM Transactions on Programming Languages and Systems, 2005, 27(2): 344-382. |
| [11] | CHEN T S, CHUNG J Y, TIAN Changsi, et al. A Novel Key Management Scheme for Dynamic Access Control in a User Hierarchy[J]. Applied Mathematics and Computation, 2005, 162(1): 339-351. |
| [12] | YU Jiang, SU Jinhai, ZHANG Yongfu. Design and Analysis of USB-Key Based Strong Password Authentication Scheme[J]. Journal of Computer Applications, 2011, 31(2): 511-513. |
| 于江, 苏锦海, 张永福. 基于USB-Key的强口令认证方案设计与分析[J]. 计算机应用, 2011, 31(2):511-513. | |
| [13] | KRIEGEL H P, KRÖGER P, ZIMEK A. Outlier Detection Techniques[J]. Tutorial at KDD, 2010, 10: 1-76. |
| [14] | LAI K H, ZHA Daochen, WANG Guanchu, et al. TODS: An Automated Time Series Outlier Detection System[EB/OL]. [2024-05-22]. https://www.xueshufan.com/publication/3175611124. |
| [15] | SIEGMUND D. Error Probabilities and Average Sample Number of the Sequential Probability Ratio Test[J]. Journal of the Royal Statistical Society Series B: Statistical Methodology, 1975, 37(3): 394-401. |
| [16] | GOLDSTEIN M, DENGEL A. Histogram-Based Outlier Score(hbos): A Fast Unsupervised Anomaly Detection Algorithm[J]. KI-2012: Poster and Demo Track, 2012, 1: 59-63. |
| [17] | BOUKERCHE A, ZHENG Lining, ALFANDI O. Outlier Detection: Methods, Models, and Classification[J]. ACM Computing Surveys, 2020, 53(3): 1-37. |
| [18] | WALFISH S. A Review of Statistical Outlier Methods[J]. Pharmaceutical Technology, 2006, 30(11): 82-86. |
| [19] | GU Xiaoyi, AKOGLU L, RINALDO A. Statistical Analysis of Nearest Neighbor Methods for Anomaly Detection[EB/OL]. (2019-07-08)[2024-05-22]. https://arxiv.org/abs/1907.03813v1. |
| [20] | BREUNIG M M, KRIEGEL H P, NG R T, et al. LOF: Identifying Density-Based Local Outliers[C]//ACM. The 2000 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2000: 93-104. |
| [21] | LIU F T, TINGKaiming, ZHOU Zhihua. Isolation Forest[C]//IEEE. 2008 8th IEEE International Conference on Data Mining. New York: IEEE, 2008: 413-422. |
| [22] | SHYU M L, CHEN S C, SARINNAPAKORN K, et al. A Novel Anomaly Detection Scheme Based on Principal Component Classifier[C]//IEEE. The IEEE Foundations and New Directions of Data Mining Workshop. New York: IEEE, 2003: 172-179. |
| [23] | RUMELHART D E, HINTON G E, WILLIAMS R J. Learning Representations by Back-Propagating Errors[J]. Nature, 1986, 323: 533-536. |
| [24] |
HINTON G E, OSINDERO S, TEH Y W. A Fast Learning Algorithm for Deep Belief Nets[J]. Neural Computation, 2006, 18(7): 1527-1554.
doi: 10.1162/neco.2006.18.7.1527 pmid: 16764513 |
| [25] | BREIMAN L. Random Forests[J]. Machine Learning, 2001, 45: 5-32. |
| [26] | FRIEDMAN J H. Greedy Function Approximation: A Gradient Boosting Machine[J]. The Annals of Statistics, 2001, 29(5): 1189-1232. |
| [27] | GEURTS P, ERNST D, WEHENKEL L. Extremely Randomized Trees[J]. Machine Learning, 2006, 63(1): 3-42. |
| [28] | FREUND Y, SCHAPIRE R E. Experiments with a New Boosting Algorithm[C]//ACM. 13th International Conference on International Conference on Machine Learning. New York: ACM, 1996: 148-156. |
| [29] | ZHANG H. The Optimality of Naive Bayes[EB/OL]. [2024-05-22]. https://aaai.org/papers/flairs-2004-097/. |
| [30] | RENNIE J D M, SHIH L, TEEVAN J, et al. Tackling the Poor Assumptions of Naive Bayes Text Classifiers[EB/OL]. [2024-05-22]. https://www.semanticscholar.org/paper/Tackling-the-Poor-Assumptions-of-Naive-Bayes-Text-Rennie-Shih/b7fab2f72ebbf4e98def1daf8c29ffcfe91183bf. |
| [31] | MANNING C D, RAGHAVAN P, SCHÜTZE H. Introduction to Information Retrieval[M]. Cambridge: Cambridge University Press, 2008. |
| [32] | METSIS V, ANDROUTSOPOULOS I, PALIOURAS G. Spam Filtering with Naive Bayes-which Naive Bayes?[EB/OL]. [2024-05-22]. http://pdfs.semanticscholar.org/39a8/0339844a27e63a2b82ae4f8eb964da787172.pdf. |
| [1] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [2] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| [3] | QI Han, WANG Jingtong, ABDULLAH Gani, GONG Changqing. Robustness of Variational Quantum Convolutional Neural Networks Based on Random Quantum Layers [J]. Netinfo Security, 2024, 24(3): 363-373. |
| [4] | JIANG Rong, LIU Haitian, LIU Cong. Unsupervised Network Intrusion Detection Method Based on Ensemble Learning [J]. Netinfo Security, 2024, 24(3): 411-426. |
| [5] | FENG Guangsheng, JIANG Shunpeng, HU Xianlang, MA Mingyu. New Research Progress on Intrusion Detection Techniques for the Internet of Things [J]. Netinfo Security, 2024, 24(2): 167-178. |
| [6] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [7] | LAN Haoliang, WANG Qun, XU Jie, XUE Yishi, ZHANG Bo. Review of Research on Blockchain-Based Federated Learning [J]. Netinfo Security, 2024, 24(11): 1643-1654. |
| [8] | HU Wentao, XU Jingkai, DING Weijie. Unsupervised Network Traffic Anomaly Detection Based on Abductive Learning [J]. Netinfo Security, 2024, 24(11): 1675-1684. |
| [9] | WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain [J]. Netinfo Security, 2024, 24(10): 1515-1527. |
| [10] | ZHANG Zihan, LAI Qingnan, ZHOU Changling. Survey on Fuzzing Test in Deep Learning Frameworks [J]. Netinfo Security, 2024, 24(10): 1528-1536. |
| [11] | SA Qirui, YOU Weijing, ZHANG Yifei, QIU Weiyang, MA Cunqing. A Survey of Ownership Protection Schemes for Federated Learning Models [J]. Netinfo Security, 2024, 24(10): 1553-1561. |
| [12] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [13] | QIN Zhongyuan, MA Nan, YU Yacong, CHEN Liquan. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders [J]. Netinfo Security, 2023, 23(9): 1-11. |
| [14] | XUE Yu, ZHANG Yixuan. Survey on Deep Neural Architecture Search [J]. Netinfo Security, 2023, 23(9): 58-74. |
| [15] | WANG Juan, ZHANG Chong, GONG Jiaxin, LI Jun’e. Review of Fuzzing Based on Machine Learning [J]. Netinfo Security, 2023, 23(8): 1-16. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||