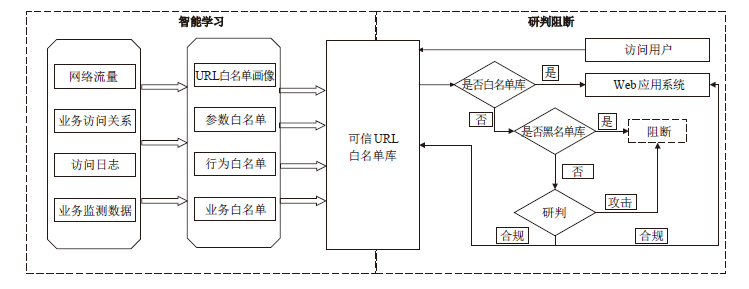
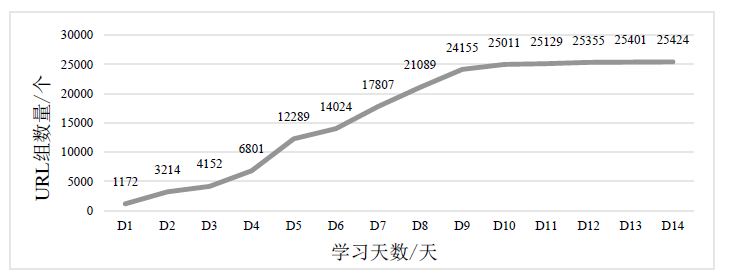
Netinfo Security ›› 2021, Vol. 21 ›› Issue (3): 1-6.doi: 10.3969/j.issn.1671-1122.2021.03.001
Previous Articles Next Articles
Research on Unknown Threat Blocking Technology of Web Application Based on URL Intelligent Whitelist
HUANG Changhui( ), HU Guangjun, LI Haiwei
), HU Guangjun, LI Haiwei
- First Research Institute of the Ministry of Public Security of PRC, Beijing 100048, China
-
Received:2020-12-20Online:2021-03-10Published:2021-03-16 -
Contact:HUANG Changhui E-mail:huangch@gov110.cn
CLC Number:
Cite this article
HUANG Changhui, HU Guangjun, LI Haiwei. Research on Unknown Threat Blocking Technology of Web Application Based on URL Intelligent Whitelist[J]. Netinfo Security, 2021, 21(3): 1-6.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.03.001
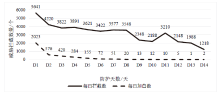
| 总体拦截威胁情况 | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
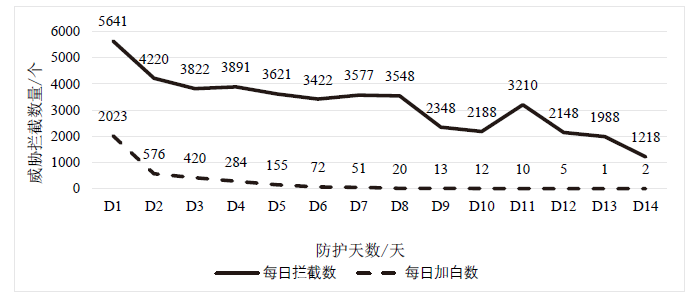
| 天数/天 | D1 | D2 | D3 | D4 | D5 | D6 | D7 | D8 | D9 | D10 | D11 | D12 | D13 | D14 |
| 拦截总数/个 | 5641 | 4220 | 3822 | 3891 | 3621 | 3422 | 3577 | 3548 | 2348 | 2188 | 3210 | 2148 | 1988 | 1218 |
| 有效威胁数/个 | 3618 | 3644 | 3402 | 3607 | 3466 | 3350 | 3526 | 3528 | 2335 | 2176 | 3200 | 2143 | 1987 | 1216 |
| 拦截准确率/% | 64 | 86 | 89 | 92 | 95 | 97 | 98 | 99 | 99 | 99 | 99 | 99 | 99 | 99 |
| 每日拦截威胁明细 | ||||||||||||||
| 目录扫描/条 | 3099 | 3015 | 2822 | 3124 | 2926 | 2772 | 2817 | 3141 | 2119 | 1802 | 2797 | 1722 | 1500 | 827 |
| Webshell写入/个 | 156 | 162 | 214 | 124 | 304 | 211 | 199 | 88 | 21 | 238 | 96 | 107 | 257 | 68 |
| 命令执行/个 | 120 | 71 | 30 | 89 | 120 | 193 | 274 | 69 | 72 | 23 | 147 | 93 | 118 | 89 |
| Struct3利用/个 | 65 | 105 | 114 | 201 | 67 | 11 | 137 | 176 | 18 | 10 | 28 | 8 | 54 | 218 |
| SQL注入/个 | 114 | 235 | 184 | 58 | 25 | 128 | 54 | 36 | 102 | 31 | 76 | 133 | 18 | 6 |
| 其他漏洞利用/个 | 3 | 1 | 0 | 1 | 2 | 0 | 5 | 0 | 0 | 2 | 1 | 0 | 0 | 3 |
| 其他/个 | 61 | 55 | 38 | 10 | 22 | 35 | 40 | 18 | 3 | 70 | 55 | 80 | 40 | 5 |
| [1] | GUO Qiquan. Comprehensive Construction of National Cyberspace Security Prevention and Control System[J]. China National Conditions and Strength, 2020,29(4):1. |
| 郭启全. 全面构建国家网络空间安全综合防控体系[J]. 中国国情国力, 2020,29(4):1. | |
| [2] | GUO Qiquan. Developing Cyberspace Visualization Technology to Support the Construction of Network Security Comprehensive Prevention and Control System[J]. Bulletin of Chinese Academy of Sciences, 2020,35(7):917-924. |
| 郭启全. 发展网络空间可视化技术支撑网络安全综合防控体系建设[J]. 中国科学院院刊, 2020,35(7):917-924. | |
| [3] | GUO Qiquan. The Situation and Task of National Critical Information Infrastructure Security Protection[J]. Secrecy Science and Technology. 2016,6(7):4-6, 1. |
| 郭启全. 国家关键信息基础设施安全保护面临的形势和任务[J]. 保密科学技术, 2016,6(7):4-6,1. | |
| [4] | HU Guangjun, LI Haiwei, WANG Rui. Research on Security Protection Technology of Critical Information Infrastructure Based on Multi-level Behavior Security[J]. Police Technology, 2021,37(1):8-11. |
| 胡光俊, 李海威, 王锐. 基于多层次行为安全的关键信息基础设施安全防护技术研究[J]. 警察技术, 2021,37(1):8-11. | |
| [5] | WANG Yijun, HUANG Changhui, ZHANG Zihan, et al. Research on Comprehensive Protection Scheme of Government Website Group Based on Microisolation Technology[J]. Police Technology, 2017,33(2):8-11. |
| 王奕钧, 黄长慧, 张子瀚, 等. 基于微隔离技术的政府网站群综合防护方案研究[J]. 警察技术, 2017,33(2):8-11. | |
| [6] | LI Jiancong. Web Application Attack Detection Based on Deep Learning[D]. Chengdu: School of Information and Communication Engineering, 2020. |
| 李建聪. 基于深度学习的Web应用攻击检测[D]. 成都:电子科技大学, 2020. | |
| [7] | SHEN Changxian. Constructing Information Security System of Active Defense and Comprehensive Prevention[J]. Financial Computerizing, 2010,17(12):12-18, 7. |
| 沈昌祥. 构建积极防御综合防范的信息安全保障体系[J]. 金融电子化, 2010,17(12):12-18,7. | |
| [8] | YU Hang, WANG Shuai, JIN Huamin. RASP Based Web Security Detection Method[J]. Telecommunications Science, 2020,36(11) 113-120. |
| 余航, 王帅, 金华敏. 基于RASP的Web安全检测方法[J]. 电信科学, 2020,36(11) 113-120. | |
| [9] | ZHANG Xiangling, WANG Huan. Construction of Active Defense System Based on Whitelist Technology[C]//Computer Security Professional Committee of China Computer Society, The 28th National Computer Security Academic Exchange Conference, October 10, 2013, Guiyang, CHINA. Shanghai: Netinfo Security, 2013: 188-190. |
| 章翔凌, 王欢. 基于白名单技术构建主动防御体系[C]//中国计算机学会计算机安全专业委员会.第28次全国计算机安全学术交流会, 2013-10-10,贵阳.上海:信息网络安全, 2013: 188-190. | |
| [10] | WANG Huan, ZHANG Xiangling. Construction of Application Security Container Based on Whitelist Technology[J]. Secrecy Science and Technology, 2012,3(10):18-22. |
| 王欢, 章翔凌. 基于“白名单”技术思路构建应用安全容器[J]. 保密科学技术. 2012,3(10):18-22. | |
| [11] | ZHANG Meng. Research on Technology of URLSecurity Detection Based on Machine Learning[D]. Harbin: Harbin Institute of Technology, 2019. |
| 张萌. 基于机器学习的URL安全检测技术的研究[D]. 哈尔滨:哈尔滨工业大学, 2019. | |
| [12] | YAN Xiaodan. Research on Network Traffic Anomaly Detection and Privacy Security Protection Based on Deep Learning[D]. BeiJing: Beijing University of Posts and Telecommunications, 2020. |
| 闫晓丹. 基于深度学习的网络流量异常检测及隐私安全防护研究[D]. 北京:北京邮电大学, 2020. | |
| [13] | SHI Bo, WANG Hongyan, GUO Xudong. Research on Abnormal Violations Monitoring Based on Business Whitelist[J]. Netinfo Security, 2015,15(9):144-148. |
| 石波, 王红艳, 郭旭东. 基于业务白名单的异常违规行为监测研究[J]. 信息网络安全, 2015,15(9):144-148. | |
| [14] | SHEN Zhuanghao. Web Application Security Protection Based on Whitelist[J]. Journal of Guangzhou University(Natural Science Edition), 2012,11(6):27-31. |
| 沈壮毫. 基于白名单的Web应用程序安全防护[J]. 广州大学学报(自然科学版), 2012,11(6):27-31. | |
| [15] | LIU Aijiang, HUANG Changhui, HU Guangjun. Detection Method of Trojan’s Control Domain Based on Improved Neural Network Algorithm[J]. Telecommunications Science, 2014,30(7):39-42. |
| 刘爱江, 黄长慧, 胡光俊. 基于改进神经网络算法的木马控制域名检测方法[J]. 电信科学, 2014,30(7):39-42. |
| [1] | SHI Leyi, XU Xinghua, LIU Yihao, LIU Jia. An Improved Probabilistic Neural Network Method of Security Situation Assessment for Industrial Control System [J]. Netinfo Security, 2021, 21(3): 15-25. |
| [2] | LIU Yanhua, LIU Zhihuang. An Anonymous Data Authentication Method Based on User Behavior Pattern [J]. Netinfo Security, 2021, 21(3): 44-52. |
| [3] | LI Jiawei, WU Kehe, ZHANG Bo. Research on Anomaly Detection of Power Industrial Control System Based on Gaussian Mixture Clustering [J]. Netinfo Security, 2021, 21(3): 53-63. |
| [4] | LU Honglin, WANG Liming. User-oriented Data Privacy Preserving Method for Federated Learning that Supports User Disconnection [J]. Netinfo Security, 2021, 21(3): 64-71. |
| [5] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [6] | YU Kechen, GUO Li, YAO Mengmeng. The Generation of Black Box Adversarial Sample Based on Spatial and Energy Dimension [J]. Netinfo Security, 2021, 21(3): 72-78. |
| [7] | SHANG Wen, WANG Hongxia. Speaker Identity Tracing Scheme in 5G Communication Based on Fingerprint [J]. Netinfo Security, 2021, 21(3): 79-86. |
| [8] | GUO Xuanzhen, PAN Zulie, SHEN Yi, CHEN Yuanchao. DNS Rebinding Detection Technology Based on Passive DNS Data Analysis [J]. Netinfo Security, 2021, 21(3): 87-95. |
| [9] | ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data [J]. Netinfo Security, 2021, 21(3): 26-36. |
| [10] | ZHOU Yihua, DONG Songshou, YANG Yuguang. A Lattice-based Identity-based Proxy Partially Blind Signature Scheme in the Standard Model [J]. Netinfo Security, 2021, 21(3): 37-43. |
| [11] | CHEN Jie, TONG Peng, YAO Si. A White-box Implementation Scheme of Lightweight Block Cipher GIFT [J]. Netinfo Security, 2021, 21(2): 16-23. |
| [12] | TU Guoqing, YANG Yanhao, LIU Shubo. Vulnerability Analysis of Geohash Code Against k-nearest Neighbor Attack [J]. Netinfo Security, 2021, 21(2): 10-15. |
| [13] | DU Ye, WANG Zimeng, LI Meihong. Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine [J]. Netinfo Security, 2021, 21(2): 1-9. |
| [14] | LI Zhaoyang, TAN Jinglei, HU Ruiqin, ZHANG Hongqi. Moving Target Defense Method Based on Double Address Hopping [J]. Netinfo Security, 2021, 21(2): 24-33. |
| [15] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-keyword Fine-grained Searchable Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2021, 21(2): 34-44. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||