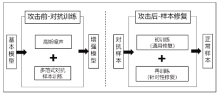
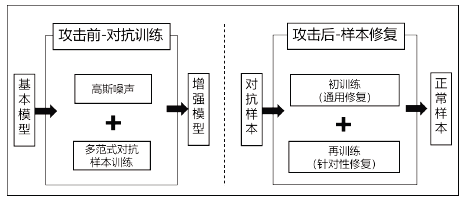
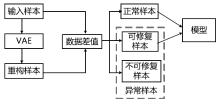
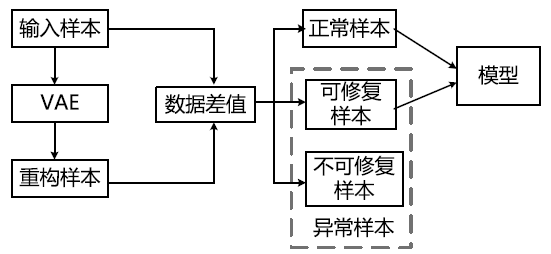
| [1] |
DONG Yinpeng, LIAO Fangzhou, PANG Tianyu, et al. Boosting Adversarial Attacks with Momentum[EB/OL]. , 2018-5-22.
|
| [2] |
GOODFELLOW Ian J, SHLENS J, SZEGEDY C. Explaining and Harnessing Adversarial Examples[EB/OL]..6572, 2015-3-20.
|
| [3] |
ZHANG Sisi, ZUO Xin, LIU Jianwei.The Problem of the Adversarial Examples in Deep Learning[J]. Chinese Journal of Computers, 2018, 41(102): 1-20.
|
|
张思思,左信,刘建伟.深度学习中的对抗样本问题[J].计算机学报,2018,41(102):1-20.
|
| [4] |
YI Ping, WANG Kedi, HUANG Cheng, et al.Adversarial Attacks in Artificial Intelligence: A Survey[J]. Journal of Shanghai Jiaotong University, 2018, 52(10): 1298-1306.
|
|
易平,王科迪,黄程,等.人工智能对抗攻击研究综述[J].上海交通大学学报,2018,52(10):1298-1306.
|
| [5] |
ELSAYED G F, SHANKAR S, CHEUNG B, et al. Adversarial Examples that Fool both Human and Computer Vision[EB/OL]. , 2018-5-22.
|
| [6] |
QIU Yue, LI Siqi.Security Threat Analysis and Solutions for the Development and Application of Artificial Intelligence[J]. Netinfo Security, 2018, 18(9): 35-41.
|
|
裘玥,李思其.人工智能发展应用过程的安全威胁分析及解决策略研究[J].信息网络安全,2018,18(9):35-41.
|
| [7] |
“The 9th Network Security Innovation Development High-end Forum-Artificial Intelligence Security Theme Forum” was held in Shanghai[J]. Netinfo Security, 2019, 19(4): 97.
|
|
“第九期网络安全创新发展高端论坛——人工智能安全主题论坛”在沪举办[J].信息网络安全,2019,19(4):97.
|
| [8] |
ROSS A S, DOSHI-VELEZ F. Improving the Adversarial Robustness and Interpretability of Deep Neural Networks by Regularizing Their Input Gradients[EB/OL]. , 2017-11-26.
|
| [9] |
YU Yingchao, DING Lin, CHEN Zuoning.Research on Attacks and Defenses towards Machine Learning Systems[J]. Netinfo Security, 2018, 18(9): 10-18.
|
|
于颖超,丁琳,陈左宁.机器学习系统面临的安全攻击及其防御技术研究[J].信息网络安全,2018,18(9):10-18.
|
| [10] |
SONG Lei, MA Chunguang, DUAN Guanghan.Machine Learning Security and Privacy: A Survey[J]. Chinese Journal of Network and Information Security, 2018, 4(8): 1-11.
|
|
宋蕾,马春光,段广晗.机器学习安全及隐私保护研究进展[J].网络与信息安全学报,2018,4(8):1-11.
|