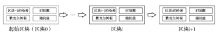
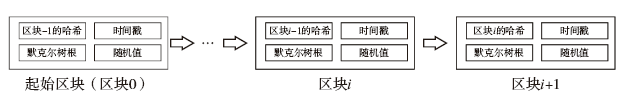
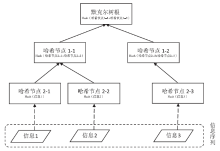
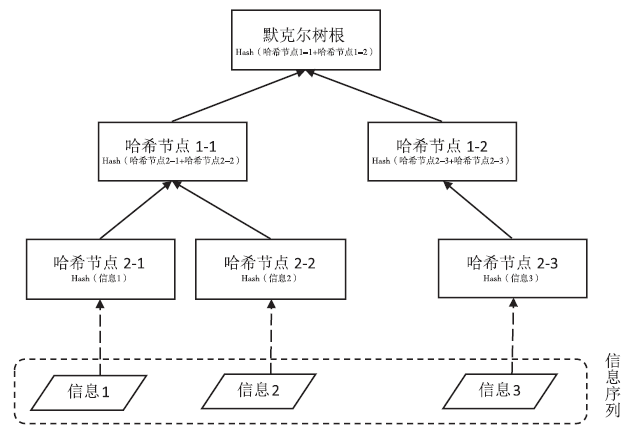
| [1] |
DIFFIE W, HELLMAN M E.New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6):644-654.
|
| [2] |
SHAMIR A.Identity-based Cryptosystems and Signature Schemes[J].Lecture Notes in Computer Science, 1984, 21(2):47-53.
|
| [3] |
ALRIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[EB/OL].,2017-10-15.
|
| [4] |
NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System [EB/OL]. Available: ,2008-2-15.
|
| [5] |
LAMPORT L, SHOSTAK R, PEASE M.The Byzantine Generals Problem[J]. ACM Transactions on Programming Languages and Systems, 1982, 4(3): 382–401.
|
| [6] |
DON T,ALEX T.Realizing the Potential of Blockchain [EB/OL]. ,2017-6-10.
|
| [7] |
JESSE M W. The Future of Financial Infrastructure[EB/OL]., 2016-8-10.
|
| [8] |
LARIMER D.Transactions as Proof-of-stake [EB/OL]., 2013-8-10.
|
| [9] |
LARIMER D.Delegated Proof-of-stake White Paper [EB/OL]., 2014-8-10.
|
| [10] |
WILLIAM S.Ethereum ‘Blockchain Bloat’ Could Reach 1TB In 2017 [EB/OL]., 2017-10-15.
|
| [11] |
WANG X, FENG D, LAI X, et al.Collisions for Hash Functions MD4, MD5, HAVAL-128 and RIPEMD[J]. IACR Cryptology ePrint Archive, 2004 (8): 199-203.
|
| [12] |
STEVENS M, BURSZTEIN E, KARPMAN P, et al. The First Collision for Full SHA-1[EB/OL]. .2017-10-15.
|
| [13] |
Cryptology Group at Centrum Wiskunde & Informatica (CWI).Google Research Security SHAttered [EB/OL]. .
|
| [14] |
WANG Xiaoyun, YIN Yiqun Lisa, YU Hongbo.Finding Collisions in the Full SHA-1[C] // Victor Shoup. Advances in Cryptology-CRYPTO 2005, August 14-18, 2005, University of California, Santa Barbara. Berlin, Heidelberg: Springer, 2005: 17-36.
|
| [15] |
HEILMAN E, KENDLER A, ZOHAR A, et al.Eclipse attacks on Bitcoin's peer-to-peer network[C] // USENIX. 24th USENIX Security Symposium, August 12-14, 2015, Washington ,USA. Washington : USENIX , 2015:129-144.
|
| [16] |
APOSTOLAKI M, ZOHAR A, Vanbever L.Hijacking Bitcoin: Routing Attacks on Cryptocurrencies[C]// IEEE.38th IEEE Symposium on Security and Privacy, May 22-25, 2017, San Jose, CA, USA.New York: IEEE, 2017: 375-392
|
| [17] |
WANG Maoning, DUAN Meijiao.The Second-preimage Attack to Blockchain Based on the Structure of Merkle Hash Tree[J]. Netinfo Security, 2018, 18(1): 38-44.
|
|
王卯宁, 段美姣. 基于Merkle哈希树结构的区块链第二原像攻击[J]. 信息网络安全, 2018, 18(1): 38-44.
|
| [18] |
ROSENFELD M. Analysis of Hashrate-based Double Spending[EB/OL]., 2014-7-15.
|
| [19] |
ZHAO Kuo, XING Yongheng.Security Survey of Internet of Things Driven by Block Chain Technology[J]. Netinfo Security, 2017, 17(5): 1-6.
|
|
赵阔, 邢永恒. 区块链技术驱动下的物联网安全研究综述[J]. 信息网络安全, 2017, 17(5): 1-6.
|
| [20] |
MEI Haitao, LIU Jie. Industry Present Situation, Existing Problems and Strategy Suggestion of Blockchain[J]. Telecommunications Science, 2016, 32(11):134-138.
|
|
梅海涛, 刘洁. 区块链的产业现状、存在问题和政策建议[J]. 电信科学, 2016, 32(11):134-138.
|
| [21] |
TANG Chunming, GAO Long.Multi-parties Key Agreement Protocol in Block Chain[J]. Netinfo Security, 2017, 17(12): 17-21.
|
|
唐春明, 高隆. 区块链系统下的多方密钥协商协议[J]. 信息网络安全, 2017, 17(12): 17-21.
|
 ), Xiaomei FU2
), Xiaomei FU2