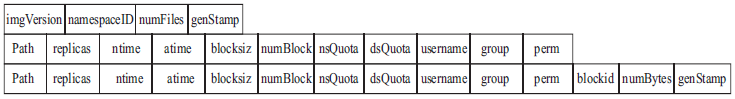
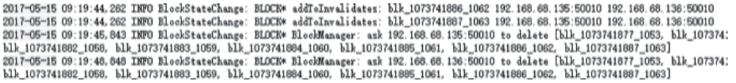
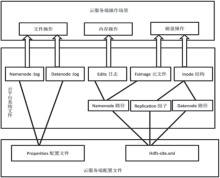
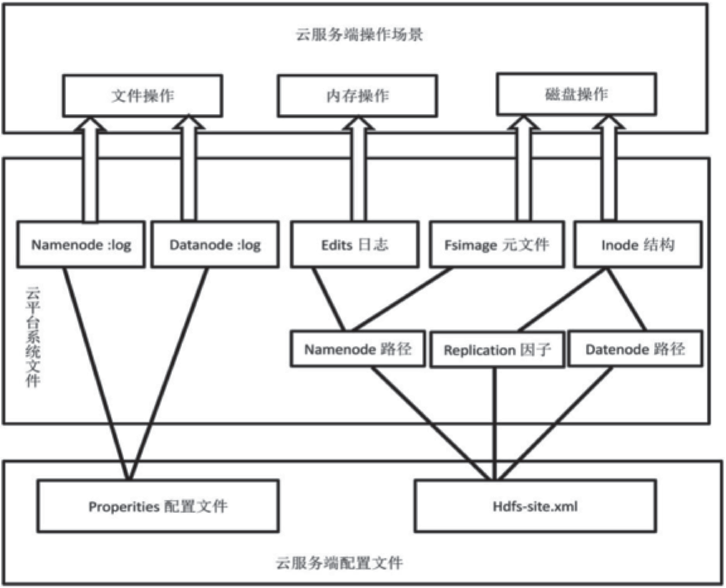
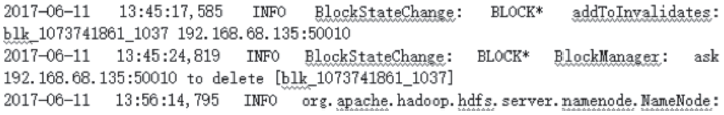
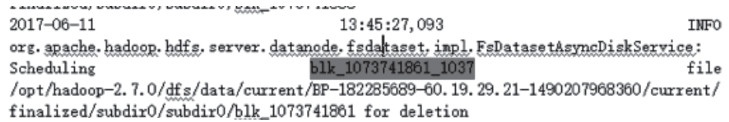
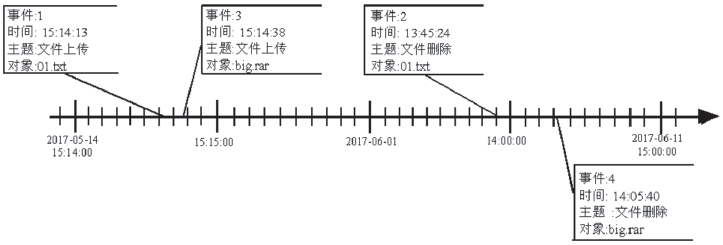
| [1] |
罗文华,龙立名.基于证据源特征的计算机犯罪场景重现本体模型构建[J].计算机科学,2016,43(12):38-42.
|
| [2] |
赵波,戴中华,向騻,等.一种云平台可信性分析模型建立方法[J].软件学报,2016,27(6):1349-1365.
|
| [3] |
董振兴,张青,陈龙,等.云存储服务数字取证调查[J].计算机科学,2015,42(11A):348-351.
|
| [4] |
CHOO K K R, HERMAN M,IORGA M, et al.Cloud Forensics: State-of-the-art and Future Directions[J]. Digital Investigation,2016(18):77-78.
|
| [5] |
SANG T.A Log Based Approach to Make Digital Forensics Easier on Cloud Computing[C]//IEEE.2013 Third International Conference on Intelligent System Design and Engineering Applications, January16-18,2013,Zhangjiajie, Hunan, China. New York:IEEE, 2013:91-94.
|
| [6] |
YAVUZ A A, PENG N.Ning. BAF: An efficient publicly verifiablesecure audit logging scheme for distributed systems[C]//IEEE.ACSAC '09 Proceedings of the 2009 Annual Computer Security Applications Conference,December 7-11,2009,Hawaii,USA. New York:IEEE,2009:219-228.
|
| [7] |
PICHAN M,LAZARESCU M,SOH S T.Cloud Forensics: Technical Challenges,Solutions and Comparative Analysis[J].Digital Investigation,2015(13):38-57.
|
| [8] |
ZAWOAD S,DUTTA A K,HASAN R.SecLaaS: Secure Logging-as-a-service for Cloud Forensics[C]//ACM. ASIA CCS '13 Proceedings of the 8th ACM SIGSAC symposium on Information, computer and communications security, May 8-10, 2013,Hangzhou, China. New York:ACM, 2013:219-230.
|
| [9] |
树雅倩,付安民,黄振涛.基于云平台的移动支付类恶意软件检测系统的设计与实现[J].信息网络安全,2016(1):59-63.
|
| [10] |
邹锦沛,陈航,徐菲.计算机网络取证和调查的科学研究[J].中兴通讯技术,2016(1):31-33.
|
| [11] |
计海萍,徐磊,蔚晓玲,等.云计算环境下基于身份的分层加密管理系统研究[J].信息网络安全,2016(5):30-36.
|
| [12] |
孟永伟,黄建强,曹腾飞,等. Hadoop集群部署实验的设计与实现[J].实验技术与管理,2015(1):145-149.
|
| [13] |
李建熠,李晖,黄梦媛.基于内核日志的移动终端恶意软件检测[J].信息网络安全,2015(7):58-63.
|
| [14] |
武鲁,王连海,顾卫东.基于云的计算机取证系统研究[J].计算机科学,2012(5):83-85.
|
| [15] |
GAO Y,LI B L.A Forensic Method for Efficient File Extraction in HDFS Based on Three-Level Mapping[J]. 武汉大学学报(自然科学英文版),2017,22(2):114-126.
|
 ), Jun WANG1, Yuanyuan SUN2
), Jun WANG1, Yuanyuan SUN2