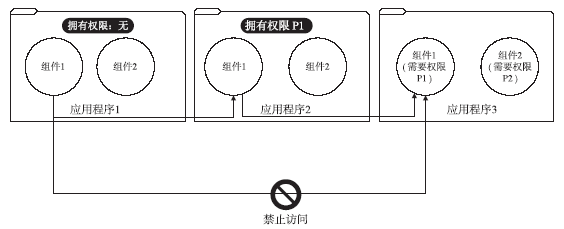
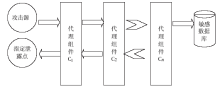
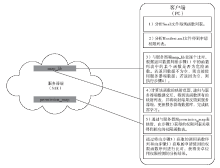
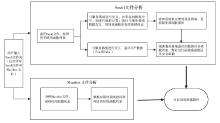
| [1] |
360互联网安全中心.2015年第三季度中国手机安全状况报告[EB/OL]. , 2015-10-22.
|
| [2] |
ONGTANG M, MCLAUGHLIN S, ENCK W, et al.Semantically Rich Application-centric Security in Android[J]. Security and Communication Networks,2012,5(6) : 658-673.
|
| [3] |
廖明华,郑力明.Android 安全机制分析与解决方案初探[J].科学技术与工程,2009,26(11):6351-6354.
|
| [4] |
ENCK W, ONGTANG M, MCDANIEL P.Understanding Android Security[J].IEEE Security & Privacy, 2009 , 7(1) : 53-54.
|
| [5] |
SHABTAI A,KANONOV U,ELOVICI Y.Intrusion Detection on Mobile Devices Using the Knowledge Based Temporal-abstraction Method[J]. Systems and Software, 2010, 83(8) :1527-1536.
|
| [6] |
张帆,钟章队. 基于权限分析的手机恶意软件检测与防范[J]. 信息网络安全,2015(10):66-73.
|
| [7] |
SHABTAI A, FLEDEL Y, ELOVICI Y, et al.Using the KBTA Method for Inferring Computer and Network Security Alerts from Timestamped, Rawsystem Metrics[J]. Computer Virology, 2009, 8(3): 267-298.
|
| [8] |
闫梅, 彭新光. 基于Android安全机制的权限检测系统[J] . 计算机工程与设计,2013,34(3):854-858.
|
| [9] |
DAVI L,DMITRIENKO A,SADEGHI A R, et al.Privilege Escalation Attacks on Android[M]. Berlin : Springer, 2011.
|
| [10] |
FELT A P, GREENWOOD K, WAGNER D. The Effectiveness of Install-time Permission Systems for Third-party Applications[EB/OL]., 2010-12-3.
|
| [11] |
刘智伟,孙其博. 基于权限管理的Android应用行为检测[J]. 信息网络安全,2014(6):72-77.
|
| [12] |
DIETZ M, SHASHI S, et al. Quire: Lightweight Provenance for Smart Phone Operating Systems[J]. Computing Research Repository, 2011, abs/1102(2) : 2334.
|
| [13] |
于达. 一种针对Android系统提权攻击的检测方法研究与实现[D].北京:北京大学,2013.
|
| [14] |
张金鑫,杨晓辉. 基于权限分析的Android应用程序检测系统[J]. 信息网络安全,2014(7):30-34.
|
 ), Weiping WEN3, Zhong CHEN1
), Weiping WEN3, Zhong CHEN1