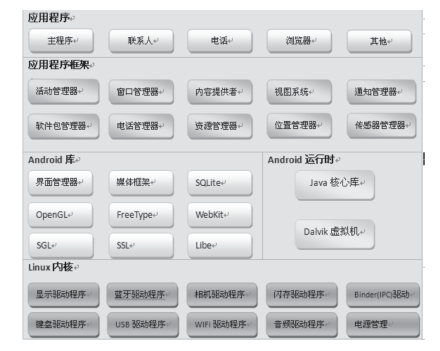
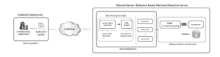
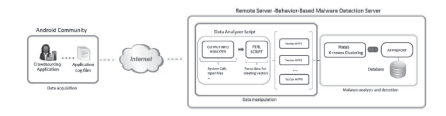
| [1] |
赵洋,胡龙,熊虎,等. 基于沙盒的Android恶意软件动态分析方案[J]. 信息网络安全,2014,(12):21-26.
|
| [2] |
Wu D, Mao C, Wei T, et al.DroidMat: Android Malware Detection through Manifest and API Calls Tracing[C] //Conference on Information Security. IEEE, 2012:62-69.
|
| [3] |
Sahs J, Khan L.A Machine Learning Approach to Android Malware Detection[C] //European Intelligence and Security Informatics Conference. IEEE, 2012:141-147.
|
| [4] |
Grampurohit V, Kumar V, Rawat S, et al.Category Based Malware Detection for Android[J]. Communications in Computer & Information Science, 2014,(2):35-42.
|
| [5] |
徐剑,武爽,孙琦,等. 面向Android应用程序的代码保护方法研究[J]. 信息网络安全,2014,(10):11-17.
|
| [6] |
Talha K A, Alper D I, Aydin C.APK Auditor: Permission-based Android malware detection system[J]. Digital Investigation, 2015,3(1):1-14.
|
| [7] |
Sheen S, Anitha R, Natarajan V.Android based malware detection using a Multifeature Collaborative Decision Fusion approach[J]. Neurocomputing, 2015,6(1): 151.
|
| [8] |
Aafer Y, Du W, Yin H.DroidAPIMiner: Mining API-Level Features for Robust Malware Detection in Android[J]. Lecture Notes of the Institute for Computer Sciences Social Informatics & Telecommunications Engineering, 2013,(2):86-103.
|
| [9] |
Grace M, Zhou Y, Zhang Q, et al.Riskranker: scalable and accurate zero-day android malware detection[C]//Proceedings of the 10th international conference on Mobile systems, applications, and services. ACM, 2012: 281-294.
|
| [10] |
高岳,胡爱群. 基于权限分析的Android隐私数据泄露动态检测方法[J]. 信息网络安全,2014,(2):27-31.
|
| [11] |
Egele M, Scholte T, Kirda E, et al.A Survey on Automated Dynamic Malware Analysis Techniques and Tools[J]. Acm Computing Surveys, 2012, 44(2):169-192.
|
| [12] |
Rieck K, Trinius P, Willems C, et al.Automatic analysis of malware behavior using machine learning[J]. Journal of Computer Security, 2011, 19(4):30-39.
|
| [13] |
Jin R, Wang B.Malware Detection for Mobile Devices Using Software-Defined Networking[R].Research & Educational Experiment Workshop. IEEE, 2013:81-88.
|
| [14] |
Asaf Shabtai, Uri Kanonov, Yuval Elovici, et al.“Andromaly”: a behavioral malware detection framework for android devices[J]. Journal of Intelligent Information Systems, 2011, 38(1):161-190.
|
| [15] |
Peng G, Shao Y, Wang T, et al.Research on Android Malware Detection and Interception Based on Behavior Monitoring[J]. Wuhan University Journal of Natural Sciences, 2012, 17(5):421-427.
|
| [16] |
刘智伟,孙其博. 基于权限管理的Android应用行为检测[J]. 信息网络安全,2014,(6):72-77.
|
| [17] |
Min L X, Cao Q H.Runtime-based Behavior Dynamic Analysis System for Android Malware Detection[J]. Information Technology Applications in Industry Computer Engineering & Materials Science, 2013,(6):25-41.
|
| [18] |
Yuan Z, Lu Y, Wang Z, et al.Droid-Sec: deep learning in android malware detection[C]//Proceedings of the 2014 ACM conference on SIGCOMM. ACM, 2014: 371-372.
|
| [19] |
包佳敏,胡爱群. Android系统文件监听技术的研究[J]. 信息网络安全,2014,(3):46-51.
|
| [20] |
Arp D, Spreitzenbarth M, Hübner M, et al.Drebin: Effective and explainable detection of android malware in your pocket[C]//Proc. of NDSS. 2014.
|
| [21] |
Gascon H, Yamaguchi F, Arp D, et al.Structural detection of android malware using embedded call graphs[C]//Proceedings of the 2013 ACM workshop on Artificial intelligence and security. ACM, 2013: 45-54.
|
| [22] |
Burguera I, Zurutuza U, Nadjm-tehrani S. Crowdroid: Behavior-Based Malware Detection System for Android[C]//Proceedings of the Acm Conference on Computer & Communications Security, 2011:15-26.
|
| [23] |
Enck W, Cox L P, Jung J, et al.TaintDroid: An Information-Flow Tracking System for Realtime Privacy Monitoring on Smartphones[C]// Proceedings of Usenix Conference on Operating Systems Design & Implementation Osdi, 2010, 57(3):99-106.
|