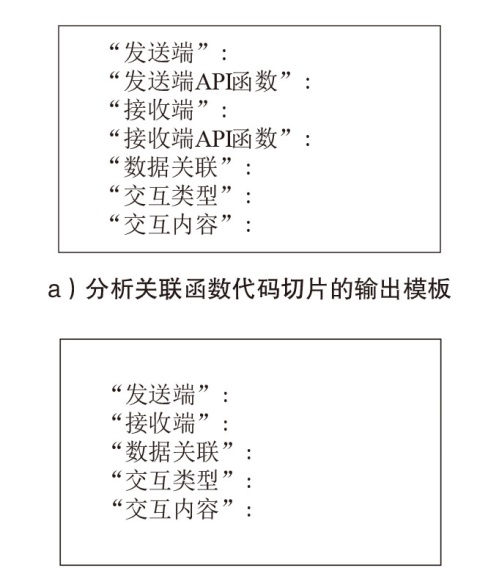
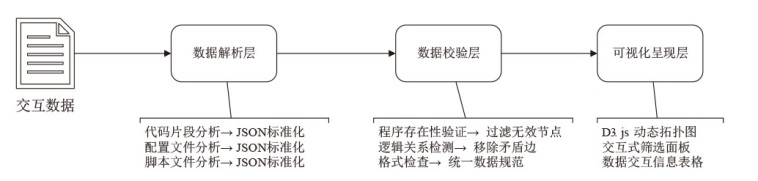
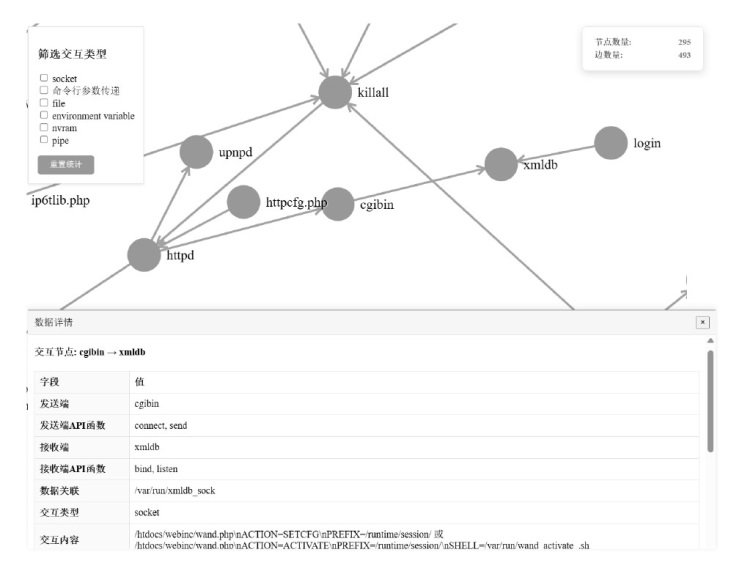
| [1] |
IOT Business News. 5 Game-Changing IoT Trends to Watch in 2025[EB/OL]. (2025-03-12)[2025-05-06]. https://iotbusinessnews.com/2025/03/12/16089-5-game-changing-iot-trends-to-watch-in-2025/.
|
| [2] |
360 Digital Security Group·Vulnerability Intelligence Service. (2025). 2024 Annual Cybersecurity Vulnerability Analysis Report[EB/OL]. (2025-02-10)[2025-05-06]. https://cdn.isc.360.com/isc-cxo/2024_Vulnerability_Report.pdf.
|
|
360数字安全集团·漏洞情报服务. (2025). 2024年度网络安全漏洞分报告[EB/OL]. (2025-02-10)[2025-05-06]. https://cdn.isc.360.com/isc-cxo/2024_Vulnerability_Report.pdf.
|
| [3] |
JIAO Yongsheng, SHU Hui. Reversing of Interprocess Communication Based on TEMU[J]. Application Research of Computers, 2013, 30(7): 5-10.
|
|
焦永生, 舒辉. 基于TEMU的进程间通信过程逆向[J]. 计算机应用研究, 2013, 30(7): 5-10.
|
| [4] |
HENDERSON A, YAN L K, HU X, et al. DECAF: A Platform-Neutral Whole-System Dynamic Binary Analysis Platform[J]. IEEE Transactions on Software Engineering, 2017, 43(2): 164-184.
|
| [5] |
LIWY7Z. Taint Aalysis Technology[EB/OL]. (2022-03-03)[2025-05-06]. https://blog.csdn.net/weixin_44442186/article/details/123263226.
|
|
LIWY7Z. 污点分析技术[EB/OL]. (2022-03-03)[2025-05-06]. https://blog.csdn.net/weixin_44442186/article/details/123263226.
|
| [6] |
REDINI N, MACHIRY A, WANG R, et al. Karonte: Detecting Insecure Multi-Binary Interactions in Embedded Firmware[C]// IEEE. 2020 IEEE Symposium on Security and Privacy. New York: IEEE, 2020: 1544-1561.
|
| [7] |
WU Yuhao, WANG Jinwen, WANG Yujie, et al. Your Firmware Has Arrived: A Study of Firmware Update Vulnerabilities[C]// USENIX. 33rd USENIX Security Symposium. Berkeley: USENIX, 2024: 5627-5644.
|
| [8] |
LI Wen, JIANG Ming, LUO Xiapu, et al. POLYCRUISE: A Cross-Language Dynamic Information Flow Analysis[C]// USENIX. 31st USENIX Security Symposium. Berkeley: USENIX, 2022: 2513-2530.
|
| [9] |
CHEN Libo, WANG Yanhao, LINGHU Jiaqi, et al. SaTC: Shared-Keyword Aware Taint Checking for Detecting Bugs in Embedded Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(4): 2421-2433.
|
| [10] |
CHEN Libo, WANG Yanhao, CAI Quanpu, et al. Sharing More and Checking Less: Leveraging Common Input Keywords to Detect Bugs in Embedded Systems[C]// USENIX. 30th USENIX Security Symposium. Berkeley: USENIX, 2021: 303-319.
|
| [11] |
ALHANAHNAH M, STEVENS C, CHEN B, et al. IoTCom: Dissecting Interaction Threats in IoT Systems[J]. IEEE Transactions on Software Engineering, 2023, 49(4): 1523-1539.
|
| [12] |
WANG Rui, WANG Xiaofeng, ZHANG Kehuan, et al. Towards Automatic Reverse Engineering of Software Security Configurations[C]// ACM. The 15th ACM Conference on Computer and Communications Security. New York: ACM, 2008: 245-256.
|
| [13] |
XIAO Yuting, CHEN Jiongyi, HU Yupeng, et al. FIRMRES: Exposing Broken Device-Cloud Access Control in IoT through Static Firmware Analysis[C]// IEEE. The 2024 54th Annual IEEE/IFIP International Conference on Dependable Systems and Networks. New York: IEEE, 2024: 495-506.
|
| [14] |
LI Xixing, WEI Qiang, WU Zehui, et al. Finding Taint-Style Vulnerabilities in Lua Application of IoT Firmware with Progressive Static Analysis[EB/OL]. (2023-08-28) [2025-05-06]. https://www.mdpi.com/2076-3417/13/17/9710.
|
| [15] |
LIU Puzhuo, SUN Chengnian, ZHENG Yaowen, et al. LLM-Powered Static Binary Taint Analysis[J]. ACM Transactions on Software Engineering and Methodology, 2025, 34(3): 1-36.
|
| [16] |
LIU Hangtian, ZHENG Lei, GAN Shuitao, et al. EAGLEYE: Exposing Hidden Web Interfaces in IoT Devices via Routing Analysis[EB/OL]. (2025-02-24)[2025-05-06]. https://dx.doi.org/10.14722/ndss.2025.240399.
|
| [17] |
CHEN Yi, YAO Yepeng, WANG Xiaofeng, et al. Bookworm Game: Automatic Discovery of LTE Vulnerabilities through Documentation Analysis[C]// IEEE. The 2021 IEEE Symposium on Security and Privacy. New York: IEEE, 2021: 1770-1787.
|
| [18] |
TIAN Junfeng, XING Wenjing, LI Zhen. BVDetector: A Program Slice-Based Binary Code Vulnerability Intelligent Detection System[EB/OL]. (2020-02-20)[2025-05-06]. https://www.sciencedirect.com/science/article/pii/S0950584920300392.
|
| [19] |
LEMOS R, HEINRICH T, MAZIERO C A, et al. Is It Safe? Identifying Malicious Apps through the Use of Metadata and Inter-Process Communication[C]// IEEE. The 2022 IEEE International Systems Conference SysCon. New York: IEEE, 2022: 1-8.
|
| [20] |
LI Meijian, WANG Yongjun, XIE Peidai, et al. Reverse Analysis of Secure Communication Protocol Based on Taint Analysis[EB/OL]. (2014-05-22)[2025-05-06]. https://ieeexplore.ieee.org/document/6992222.
|
| [21] |
JI Yang, LEE S, DOWING E, et al. RAIN: Refinable Attack Investigation with On-demand Inter-Process Information Flow Tracking[C]// ACM. The 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 311-326.
|
| [22] |
COLE E. Static Taint Analysis of Binary Executables Using Architecture-Neutral Intermediate Representation[R]. St. Louis: Washington University in St. Louis, WUCSE-2019-1177, 2019.
|
| [23] |
LIU N F, LIN K, HEWITT J, et al. Lost in the Middle: How Language Models Use Long Contexts[J]. Transactions of the Association for Computational Linguistics, 2024, 12: 157-173.
|
 ), FENG Yuan
), FENG Yuan