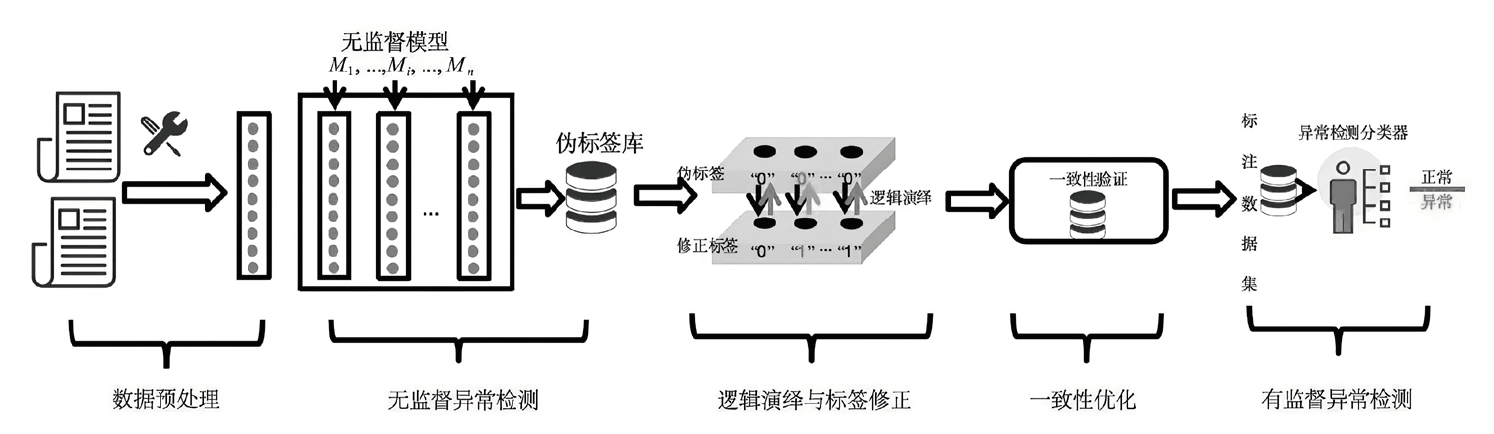
| [1] |
HE Ke, KIM D D, ASGHAR M R. Adversarial Machine Learning for Network Intrusion Detection Systems: A Comprehensive Survey[J]. IEEE Communications Surveys & Tutorials, 2023, 25(1): 538-566.
|
| [2] |
QIN Zhongyuan, MA Nan, YU Yacong, et al. Network Anomaly Detection Based on Dual Graph Convolutional Network and Autoencoders[J]. Netinfo Security, 2023, 23(9): 1-11.
|
|
秦中元, 马楠, 余亚聪, 等. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9):1-11.
|
| [3] |
CHANG Zhihao, YU Linzhu, XU Yanchao, et al. Neural Embeddings for KNN Search in Biological Sequence[C]//AAAI. Proceedings of the AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2024: 38-45.
|
| [4] |
DAI Wangzhou, XU Qiuling, YU Yang, et al. Bridging Machine Learning and Logical Reasoning by Abductive Learning[C]//ACM. Proceedings of the 33rd International Conference on Neural Information Processing Systems. New York: ACM, 2019: 32-44.
|
| [5] |
LIU F T, TINGKaiming, ZHOU Zhihua. Isolation Forest[C]//IEEE. 2008 Eighth IEEE International Conference on Data Mining. New York: IEEE, 2008: 413-422.
|
| [6] |
BREUNIG M M, KRIEGEL H P, NG R T, et al. LOF: Identifying Density-Based Local Outliers[C]//ACM. Proceedings of the 2000 ACM SIGMOD International Conference on Management of Data. New York: ACM, 2000: 93-104.
|
| [7] |
ZHANG Minling, ZHOU Zhihua. ML-KNN: A Lazy Learning Approach to Multi-Label Learning[J]. Pattern Recognition, 2007, 40(7): 2038-2048.
|
| [8] |
HU Wentao, JIANG Dawei, WU Sai, et al. Distributional Constraint Discovery for Intelligent Auditing[J]. Knowledge and Information Systems, 2023, 65(12): 5195-5229.
|
| [9] |
HU Wentao, JIANG Dawei, WU Sai, et al. IceBerg: Deep Generative Modeling for Constraint Discovery and Anomaly Detection[C]//IEEE. 2022 IEEE International Conference on Parallel & Distributed Processing with Applications. New York: IEEE, 2022: 74-81.
|
| [10] |
LIU Yuxiao, CHEN Wei, ZHANG Tianyue, et al. Explainable Anomaly Traffic Detection Based on Sparse Autoencoders[J]. Netinfo Security, 2023, 23(7): 74-85.
|
|
刘宇啸, 陈伟, 张天月, 等. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7):74-85.
|
| [11] |
HAN Qi, QIAN Xin, XU Hongxiang, et al. DM-CNN: Dynamic Multi-Scale Convolutional Neural Network with Uncertainty Quantification for Medical Image Classification[J]. Computers in Biology and Medicine, 2024, 168: 107758.
|
| [12] |
ACHARYA T, ANNAMALAI A, CHOUIKHA M F. Optimizing the Performance of Network Anomaly Detection Using Bidirectional Long Short-Term Memory (Bi-LSTM) and over-Sampling for Imbalance Network Traffic Data[J]. Advances in Science Technology and Engineering Systems Journal, 2023, 8(6): 144-154.
|
| [13] |
YUAN Lining, LI Xin, WANG Xiaodong, et al. Graph Embedding Models: A Survey[J]. Journal of Frontiers of Computer Science and Technology, 2022, 16(1): 59-87.
|
|
袁立宁, 李欣, 王晓冬, 等. 图嵌入模型综述[J]. 计算机科学与探索, 2022, 16(1):59-87.
doi: 10.3778/j.issn.1673-9418.2104020
|
| [14] |
FAN Wenfei, HAN Ziyan, WANG Yaoshu, et al. Discovering Top-K Rules Using Subjective and Objective Criteria[J]. Proceedings of the ACM on Management of Data, 2023, 1(1): 1-29.
|
| [15] |
HUANG Qiang, LUO Pingyi, TUNG A K H. A New Sparse Data Clustering Method Based on Frequent Items[J]. Proceedings of the ACM on Management of Data, 2023, 1(1): 29-58.
|
| [16] |
ZONG Bo, SONG Qi, MIN M R, et al. Deep Autoencoding Gaussian Mixture Model for Unsupervised Anomaly Detection[C]//ICLR. InInternational Conference on Learning Representations (ICLR). San Diego: ICLR, 2020: 1-19.
|
| [17] |
DONG Shuqin, ZHANG Bin. Network Traffic Anomaly Detection Method Based on Deep Features Learning[J]. Journal of Electronics & Information Technology, 2020, 42(3): 1-9.
|
|
董书琴, 张斌. 基于深度特征学习的网络流量异常检测方法[J]. 电子与信息学报, 2020, 42(3):1-9.
|
| [18] |
YE Huanrong, LI Muyuan, JIANG Bo. Research on DGA Malicious Domain Name Detection Method Based on Transfer Learning and Threat Intelligence[J]. Netinfo Security, 2023, 23(10): 8-15.
|
|
叶桓荣, 李牧远, 姜波. 基于迁移学习和威胁情报的DGA恶意域名检测方法研究[J]. 信息网络安全, 2023, 23(10):8-15.
|
| [19] |
FU Yu, WANG Kun, DUAN Xueyuan, et al. Survey of Research on Abnormal Traffic Detection for Software Defined Networks[J]. Journal on Communications, 2024, 45(3): 208-226.
doi: 10.11959/j.issn.1000-436x.2024016
|
|
付钰, 王坤, 段雪源, 等. 面向软件定义网络的异常流量检测研究综述[J]. 通信学报, 2024, 45(3):208-226.
doi: 10.11959/j.issn.1000-436x.2024016
|
| [20] |
ZHANG Yuchen, LI Lianghui, MA Chenyang, et al. A Log Anomaly Detection Method with Variables[J]. Netinfo Security, 2023, 23(10): 16-20.
|
|
张玉臣, 李亮辉, 马辰阳, 等. 一种融合变量的日志异常检测方法[J]. 信息网络安全, 2023, 23(10):16-20.
|
| [21] |
HU Wentao, JIANG Dawei, WU Sai, et al. Complex Integrity Constraint Discovery: Measuring Trust in Modern Intelligent Railroad Systems[J]. Journal of Zhejiang University-Science A, 2022, 23(10): 832-837.
|
| [22] |
BREVE B, CARUCCIO L, CIRILLO S, et al. IndiBits: Incremental Discovery of Relaxed Functional Dependencies Using Bitwise Similarity[C]//IEEE. 2023 IEEE 39th International Conference on Data Engineering (ICDE). New York: IEEE, 2024: 1393-1405.
|
| [23] |
CAO Lei, YAN Yizhou, WANG Yu, et al. AutoOD: Automatic Outlier Detection[J]. Proceedings of the ACM on Management of Data, 2023, 1(1): 1-27.
|
| [24] |
IMAN S, ARASH H, ALI A. Ghorba-Ni, Intrusion Detection Evaluation Dataset(CICIDS2017)[EB/OL]. (2022-11-29)[2024-05-30]. https://www.unb.ca/cic/datasets/ids-2017.html.
|
| [25] |
ZHONG Ying, WANG Zhiliang, SHI Xingang, et al. RFG-HELAD: A Robust Fine-Grained Network Traffic Anomaly Detection Model Based on Heterogeneous Ensemble Learning[J]. IEEE Transactions on Information Forensics and Security, 2024, 19(1): 5895-5910.
|
 )
)