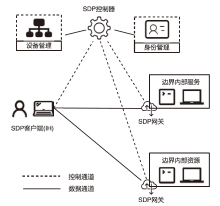
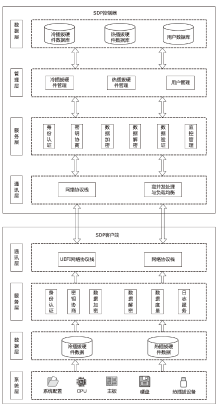
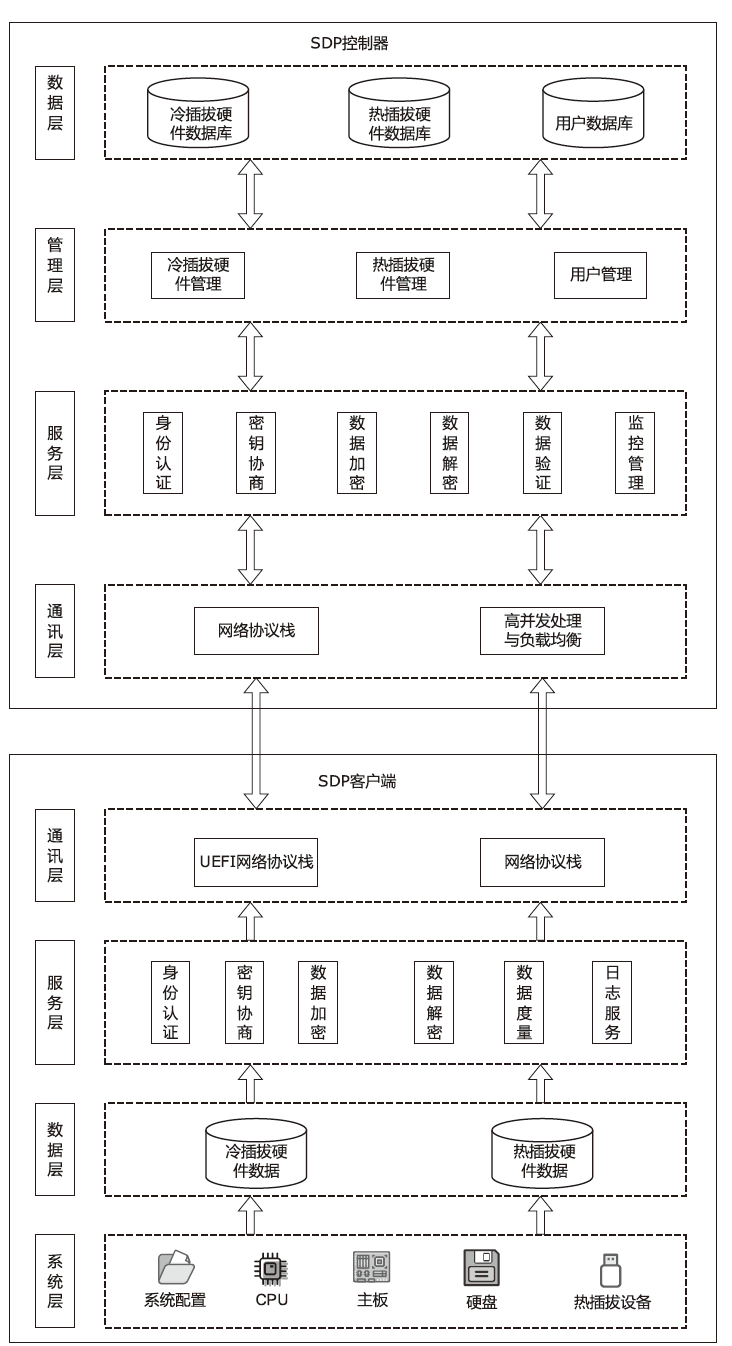
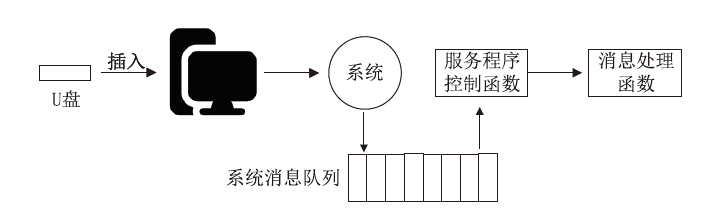
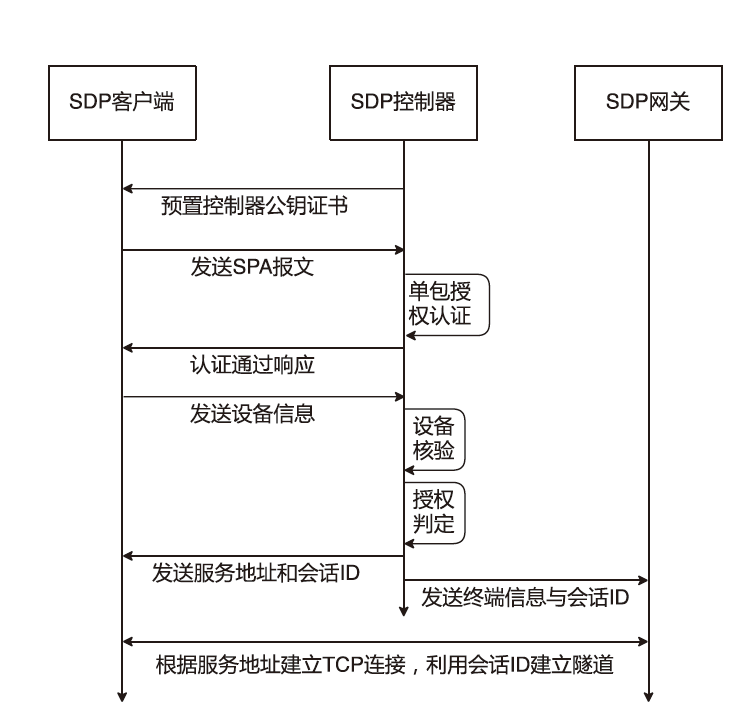
| [1] |
SAMANIEGO M, DETERS R. Zero-Trust Hierarchical Management in IoT[C]// IEEE. 2018 IEEE International Congress on Internet of Things (ICIOT). IEEE, 2018: 88-95.
|
| [2] |
ROSE S, BORCHERT O, MITCHELL S, et al. Zero Trust Architecture[EB/OL]. (2020-08-16)[2023-01-30]. https://csrc.nist.gov/publications/detail/sp/800-207/final?ref=hackernoon.com.
|
| [3] |
BARTH D, GILMAN E. Zero Trust Networks: Building Trusted Systems in Untrusted Networks[M]. Sebastopol: O’Reilly Media, 2017.
|
| [4] |
MOUBAYED A, REFAEY A, SHAMI A. Software-Defined Perimeter (Sdp): State of the Art Secure Solution for Modern Networks[J]. IEEE Network, 2019, 33(5): 226-233.
doi: 10.1109/MNET.65
URL
|
| [5] |
INDU I, ANAND P, BHASKAR V. Identity and Access Management in Cloud Environment: Mechanisms and Challenges[J]. Engineering Science and Technology, 2018, 21(4): 574-588.
|
| [6] |
SHARMA D H, DHOTE C A, POTEY M M. Identity and Access Management As Security-as-a-Service From Clouds[J]. Procedia Computer Science, 2016, 79: 170-174.
doi: 10.1016/j.procs.2016.03.117
URL
|
| [7] |
SHEIKH N, PAWAR M, LAWRENCE V. Zero Trust Using Network Micro Segmentation[C]// IEEE. IEEE INFOCOM 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE 2021: 1-6.
|
| [8] |
SALLAM A, REFAEY A, SHAMI A. On the Security of SDN: A Completed Secure and Scalable Framework Using the Software-Defined Perimeter[J]. IEEE access, 2019, 7: 146577-146587.
doi: 10.1109/Access.6287639
URL
|
| [9] |
ZAHEER Z, CHANG H, MUKHERJEE S, et al. Eztrust: Network-Independent Zero-Trust Perimeterization for Microservices[C]// ACM. Proceedings of the 2019 ACM Symposium on SDN Research. New York: ACM, 2019: 49-61.
|
| [10] |
WARD R, BEYER B. Beyondcorp: A New Approach to Enterprise Security[EB/OL]. (2014-04-08)[2023-01-30]. https://research.google/pubs/pub43231/.
|
| [11] |
DECUSATIS C, LIENGTIRAPHAN P, SAGER A, et al. Implementing Zero Trust Cloud Networks with Transport Access Control and First Packet Authentication[C]// IEEE. 2016 IEEE International Conference on Smart Cloud. New York: IEEE, 2016: 5-10.
|
| [12] |
Cloud Security Alliance (CSA). Software-Defined Perimeter (SDP) Specification v2.0[EB/OL]. (2022-10-03)[2023-01-30]. https://cloudsecurityalliance.org/artifacts/software-defined-perimeter-zero-trust-specification-v2/.
|
| [13] |
BRICKER G. Unified Extensible Firmware interface (UEFI) and Secure Boot: Promise and Pitfalls[J]. Journal of Computing Sciences in Colleges, 2013, 29(1): 60-63.
|
| [14] |
YAO Q, WANG Q, ZHANG X, et al. Dynamic Access Control and Authorization System Based on Zero-Trust Architecture[C]// RIS. Proceedings of the 2020 1st International Conference on Control, Robotics and Intelligent System. New York: RIS, 2020: 123-127.
|
| [15] |
SAATY R W. The Analytic Hierarchy Process—What it is and How it is Used[J]. Mathematical Modelling, 1987, 9(3): 161-176.
doi: 10.1016/0270-0255(87)90473-8
URL
|
| [16] |
WU Kehe, CHENG Rui, JIANG Xiaochen, et al. Security Protection Scheme of Power IoT Based on SDP[J]. Netinfo Security, 2022, 22(2): 32-38.
|
|
吴克河, 程瑞, 姜啸晨, 等. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38.
|