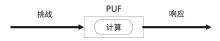
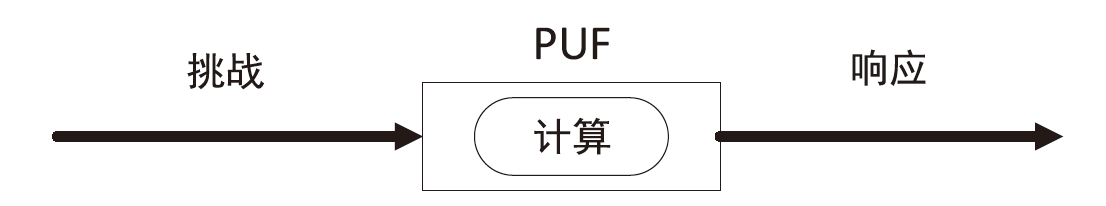
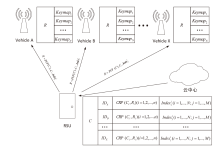
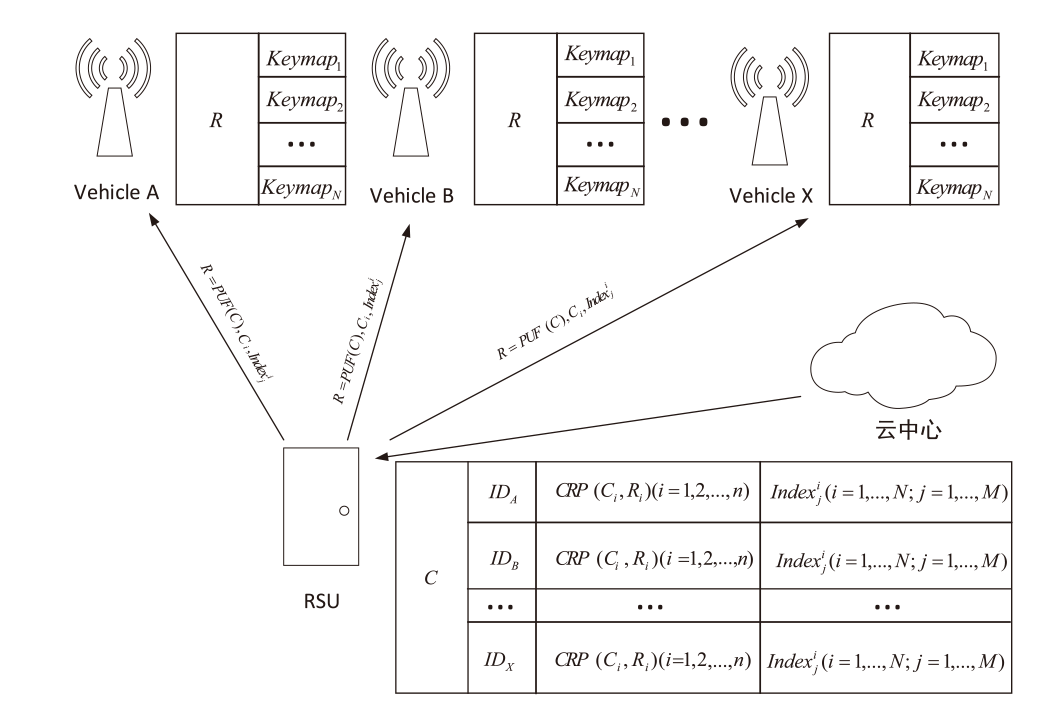
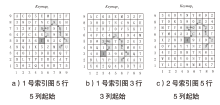
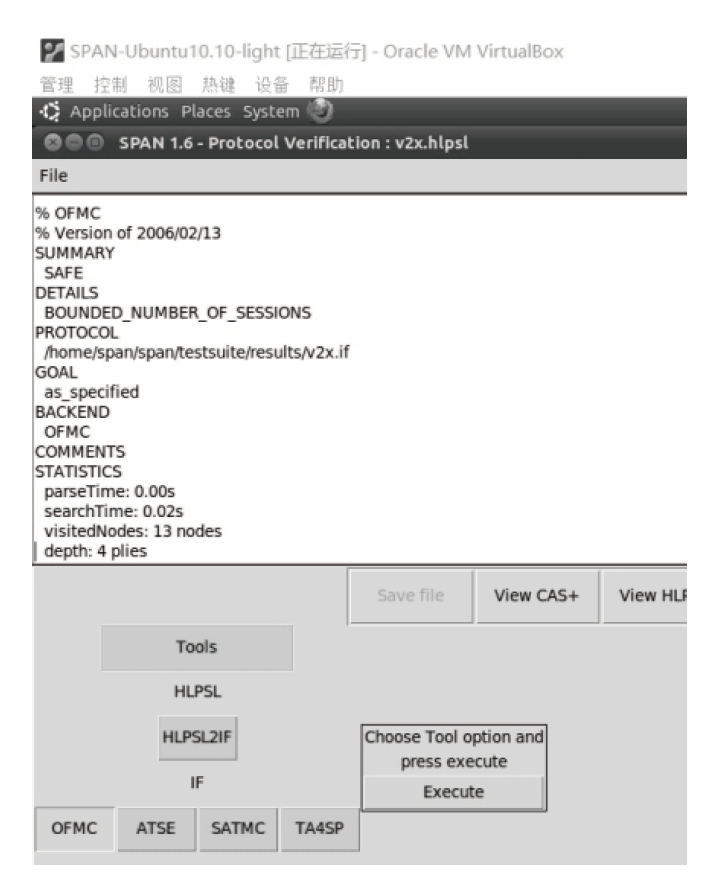
Netinfo Security ›› 2023, Vol. 23 ›› Issue (12): 38-48.doi: 10.3969/j.issn.1671-1122.2023.12.005
Previous Articles Next Articles
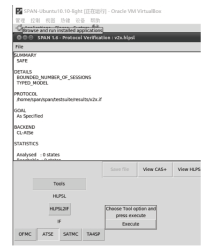
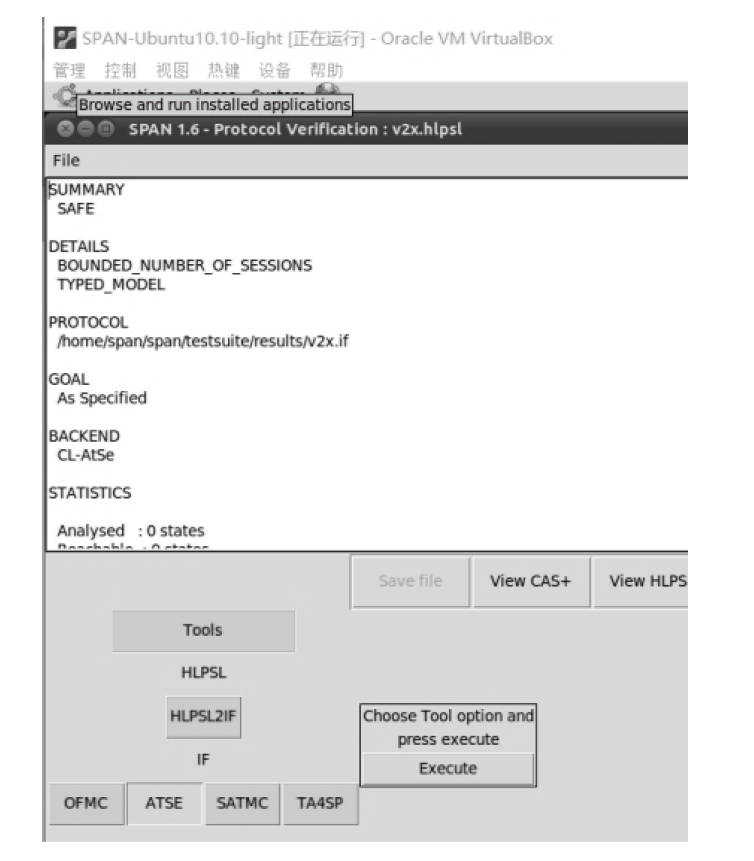
MI-PUF-Based Secure Authentication Protocol for V2X Communication
TAN Weijie1,2,3,4, YANG Yuting1,2( ), NIU Kun1,2, PENG Changgen1,2,4
), NIU Kun1,2, PENG Changgen1,2,4
- 1. State Key Laboratory of Public Big Data, Guizhou University, Guiyang 550025, China
2. College of Computer Science and Technology, Guizhou University, Guiyang 550025, China
3. Key Laboratory of Advance Manufacturing Technology of the Ministry of Education, Guizhou University, Guiyang 550025, China
4. Guizhou Big Data Academy, Guiyang 550025, China
-
Received:2023-08-18Online:2023-12-10Published:2023-12-13
CLC Number:
Cite this article
TAN Weijie, YANG Yuting, NIU Kun, PENG Changgen. MI-PUF-Based Secure Authentication Protocol for V2X Communication[J]. Netinfo Security, 2023, 23(12): 38-48.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.12.005
| [1] | YE Ping, HAO Tieliang, ZHAO Dehua, et al. Research on the Information Security Technology of Car Networking from the Perspective of Automobile Enterprise[J]. Automobile Applied Technology, 2019, 284(5): 59-63. |
| 叶平, 郝铁亮, 赵德华, 等. 从车企的角度对车联网信息安全技术研究[J]. 汽车实用技术, 2019, 284(5): 59-63. | |
| [2] |
SONG Tao, LI Xiuhua, LI Hui, et al. Overview of Research on Security Encryption Authentication Technology of IoV in Big Data Era[J]. Computer Science, 2022, 49(4): 340-353.
doi: 10.11896/jsjkx.210400112 |
|
宋涛, 李秀华, 李辉, 等. 大数据时代下车联网安全加密认证技术研究综述[J]. 计算机科学, 2022, 49(4): 340-353.
doi: 10.11896/jsjkx.210400112 |
|
| [3] | BAO Jun, ZHANG Xinyou, FENG Li, et al. Security Authentication Protocol for Internet of Vehicles Based on Blockchain[J]. Application Research of Computers, 2023, 40(10): 34-41, 47. |
| 包俊, 张新有, 冯力, 等. 一种基于区块链的车联网安全认证协议[J]. 计算机应用研究, 2023, 40(10): 34-41, 47. | |
| [4] | ZANG Meimei, ZHU Ying, LAN Rushi, et al. BAVC: Efficient Blockchain-Based Authentication Scheme for Vehicular Secure Communication[C]// IEEE. 2021 13th International Conference on Advanced Computational Intelligence (ICACI). New York: IEEE, 2021: 346-350. |
| [5] |
LU Xiaozhen, XIAO Liang, XU Tangwei, et al. Reinforcement Learning Based PHY Authentication for VANETs[J]. IEEE Transactions on Vehicular Technology, 2020, 69(3): 3068-3079.
doi: 10.1109/TVT.25 URL |
| [6] |
XIAO Liang, LU Xiaozhen, XU Tangwei, et al. Reinforcement Learning-Based Physical-Layer Authentication for Controller Area Networks[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 2535-2547.
doi: 10.1109/TIFS.10206 URL |
| [7] | HE Yefeng, LI Guoqing, LIU Jixiang. Conditional Privacy-Preserving Authentication Scheme Based on Fog Computing and Multi TA in VANET[J]. Application Research of Computers, 2023, 40(6): 1845-1849. |
| 何业锋, 李国庆, 刘继祥. 车联网中基于雾计算和多TA的条件隐私保护认证方案[J]. 计算机应用研究, 2023, 40(6): 1845-1849. | |
| [8] |
ZHONG Hong, CHEN Lei, CUI Jie, et al. Secure and Lightweight Conditional Privacy-Preserving Authentication for Fog-Based Vehicular Ad Hoc Networks[J]. IEEE Internet of Things Journal, 2022, 9(11): 8485-8497.
doi: 10.1109/JIOT.2021.3116039 URL |
| [9] | HOU Wanyu, SUN Yu, LI Dawei, et al. Anonymous Authentication and Key Agreement Protocol for 5G-V2V Based on PUF[J]. Journal of Computer Research and Development, 2021, 58(10): 197-209. |
| 侯琬钰, 孙钰, 李大伟, 等. 基于 PUF 的 5G 车联网 V2V 匿名认证与密钥协商协议[J]. 计算机研究与发展, 2021, 58(10): 197-209. | |
| [10] | GAO Yan, DENG Lunzhi, SHI Hongyu, et al. Certificateless Strong Anonymous Aggregate Signature Scheme for the Internet of Vehicles[J]. Journal of Guizhou Normal University (Natural Sciences), 2022, 40(2): 96-104. |
| 高岩, 邓伦治, 施虹宇, 等. 适用于车联网的无证书强匿名聚合签名方案[J]. 贵州师范大学学报(自然科学版), 2022, 40(2): 96-104. | |
| [11] |
ZHOU Jun, CAO Zhenfu, QIN Zhan, et al. LPPA: Lightweight Privacy-Preserving Authentication from Efficient Multi-Key Secure Outsourced Computation for Location-Based Services in VANETs[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 420-434.
doi: 10.1109/TIFS.10206 URL |
| [12] |
HE Debiao, ZEADALLY S, XU Baowen, et al. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(12): 2681-2691.
doi: 10.1109/TIFS.2015.2473820 URL |
| [13] | CHOI Y, LEE J, SHIN H, et al. Mutual Authentication Method between PUFs[C]// IEEE. 2022 International Conference on Electrical, Computer and Energy Technologies (ICECET). New York: IEEE, 2022: 1-5. |
| [14] |
CHEN An. Utilizing the Variability of Resistive Random Access Memory to Implement Reconfigurable Physical Unclonable Functions[J]. IEEE Electron Device Letters, 2015, 36(2): 138-140.
doi: 10.1109/LED.2014.2385870 URL |
| [15] |
XIONG Jun, MA Dongtang, WONG K, et al. Robust Masked Beamforming for MISO Cognitive Radio Networks with Unknown Eavesdroppers[J]. IEEE Transactions on Vehicular Technology, 2016, 65(2): 744-755.
doi: 10.1109/TVT.2015.2400452 URL |
| [16] | AYSU A, GULCAN E, MORIYAMA D, et al. End-to-End Design of a PUF-Based Privacy Preserving Authentication Protocol[C]// Springer. International Workshop Cryptographic Hardware and Embedded Systems. Berlin:Springer, 2015: 556-576. |
| [17] |
AMAN M, CHUA K, SIKDAR B. Mutual Authentication in IoT Systems Using Physical Unclonable Functions[J]. IEEE Internet of Things Journal, 2017, 4(5): 1327-1340.
doi: 10.1109/JIoT.6488907 URL |
| [18] | PATIL A, HAMZA R, HASSAN A, et al. Efficient Privacy-Preserving Authentication Protocol Using PUFs with Blockchain Smart Contracts[EB/OL]. [2023-08-10]. https://doi.org/10.1016/j.cose.2020.101958. |
| [19] |
WANG Zhenyu, GUO Yang, LI Shaoqing, et al. Design of Efficient Anonymous Authentication Protocol for Lightweight IoT Devices[J]. Journal on Communications, 2022, 43(7): 49-61.
doi: 10.11959/j.issn.1000-436x.2022125 |
|
王振宇, 郭阳, 李少青, 等. 面向轻量级物联网设备的高效匿名身份认证协议设计[J]. 通信学报, 2022, 43(7): 49-61.
doi: 10.11959/j.issn.1000-436x.2022125 |
|
| [20] | BAI Haodong, JIA Xiaoying. A Physical Unclonable Function Based Device Authentication Protocol for Smart Grid[J]. Journal of South-Central Minzu University(Natural Science Edition), 2023, 42(3): 382-386. |
| 白昊东, 贾小英. 一个基于物理不可克隆函数的智能电网设备认证协议[J]. 中南民族大学学报(自然科学版), 2023, 42(3): 382-386. | |
| [21] | CHATTERJEE U, CHAKRABORTY R S, MUKHOPADHYAY D. A PUF-Based Secure Communication Protocol for IoT[J]. ACM Transactions on Embedded Computing Systems (TECS), 2017, 16(3): 1-25. |
| [22] | BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[C]// Springer. Advances in Cryptology—CRYPTO 2001: 21st Annual International Cryptology Conference. Berlin:Springer, 2001: 213-229. |
| [23] | BRAEKEN A. PUF Based Authentication Protocol for IoT[EB/OL]. (2018-08-20)[2023-08-10]. https://www.researchgate.net/publication/327131986_PUF_based_authentication_protocol_for_IoT. |
| [24] |
DOLEV D, YAO A. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208.
doi: 10.1109/TIT.1983.1056650 URL |
| [25] |
CHATTERJEE U, GOVINDAN V, SADHUKHAN R, et al. Building PUF Based Authentication and Key Exchange Protocol for IoT without Explicit CRPs in Verifier Database[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(3): 424-437.
doi: 10.1109/TDSC.8858 URL |
| [26] | LIYANAGE, MADHUSANKA, et al. IoT Security: Advances in Authentication[M]. Hobokon: John Wiley & Sons, 2020. |
| [27] | WANG Li, LI Erxia, JI Yuchen, et al. PUF-Based Anti-Physical Cloning RFID Security Authentication Protocol[J]. Netinfo Security, 2020, 20(8): 89-97. |
| 王利, 李二霞, 纪宇晨, 等. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. | |
| [28] | LI TAO, LIU Yali. A Double PUF-Based RFID Authentication Protocol[J]. Journal of Computer Research and Development, 2021, 58(8): 1801-1810. |
| 李涛, 刘亚丽. 一种基于双 PUF 的 RFID 认证协议[J]. 计算机研究与发展, 2021, 58(8): 1801-1810. | |
| [29] |
BANSAL G, NAREN N, CHAMOLA V, et al. Lightweight Mutual Authentication Protocol for V2G Using Physical Unclonable Function[J]. IEEE Transactions on Vehicular Technology, 2020, 69(7): 7234-7246.
doi: 10.1109/TVT.25 URL |
| [30] |
KAVEH M, MOSAVI M R. A Lightweight Mutual Authentication for Smart Grid Neighborhood Area Network Communications Based on Physically Unclonable Function[J]. IEEE Systems Journal, 2020, 14(3): 4535-4544.
doi: 10.1109/JSYST.4267003 URL |
| [31] | FRIKKEN K, BLANTON M, ATALLAH M. Robust Authentication Using Physically Unclonable Functions[C]// Springer. International Conference on Information Security. Berlin:Springer, 2009: 262-277. |
| [32] |
AMAN M, JAVAID U, SIKDAR B. A Privacy-Preserving and Scalable Authentication Protocol for the Internet of Vehicles[J]. IEEE Internet of Things Journal, 2021, 8(2): 1123-1139.
doi: 10.1109/JIoT.6488907 URL |
| [33] | ZHU Feng, LI Peng, XU He, et al. A Lightweight RFID Mutual Authentication Protocol with PUF[EB/OL]. (2019-07-04)[2023-08-10]. https://doi.org/10.3390/s19132957. |
| [34] |
BARBARESCHI M, DE B, LA M, et al. A PUF-Based Mutual Authentication Scheme for Cloud-Edges IoT Systems[J]. Future Generation Computer Systems, 2019, 101: 246-261.
doi: 10.1016/j.future.2019.06.012 |
| [35] |
GOPE P. PMAKE: Privacy-Aware Multi-Factor Authenticated Key Establishment Scheme for Advance Metering Infrastructure in Smart Grid[J]. Computer Communications, 2020, 152: 338-344.
doi: 10.1016/j.comcom.2019.12.042 URL |
| [1] | . An Improved Scheme of CHAP [J]. , 2014, 14(7): 75-. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||