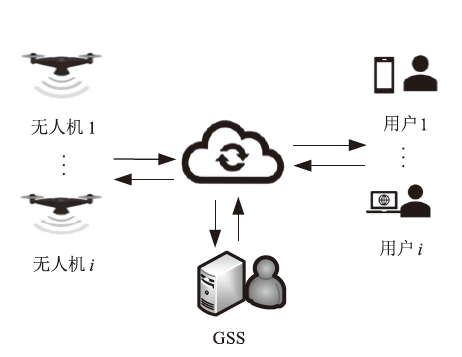
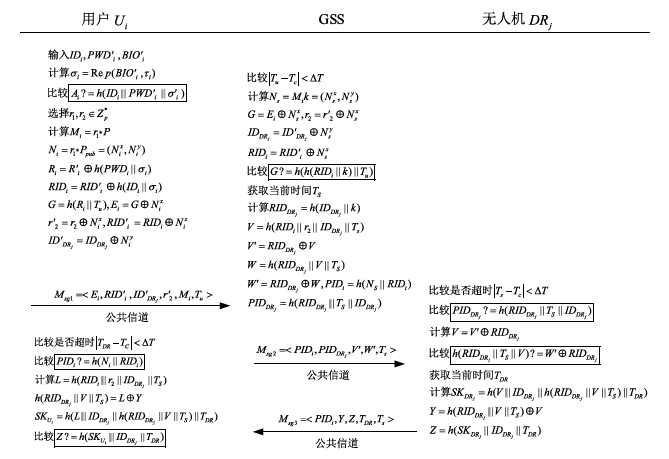
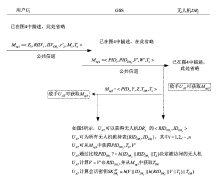
| [1] |
ABUALIGAH L, DIABAT A, SUMARI P, et al. Applications, Deployments, and Integration of Internet of Drones(IoD): A Review[J]. IEEE Sensors Journal, 2021, 21(2): 25532-25546.
|
| [2] |
LIN Chao, HE Debiao, KUMAR N, et al. Security and Privacy for the Internet of Drones: Challenges and Solutions[J]. IEEE Communications Magazine, 2018, 56(1): 64-69.
|
| [3] |
YAHUZA M, IDRIS M Y I, AHMEDY I B, et al. Internet of Drones Security and Privacy Issues: Taxonomy and Open Challenges[J]. IEEE Access, 2021, 9: 57243-57270.
|
| [4] |
SRINIVAS J, DAS A K, KUMAR N, et al. TCALAS: Temporal Credential-Based Anonymous Lightweight Authentication Scheme for Internet of Drones Environment[J]. IEEE Transactions on Vehicular Technology, 2019, 68(7): 6903-6916.
|
| [5] |
ALI Z, CHAUDHRY S A, RAMZAN M S, et al. Securing Smart City Surveillance: A Lightweight Authentication Mechanism for Unmanned Vehicles[J]. IEEE Access, 2020, 8: 43711-43724.
|
| [6] |
WAZID M, DAS A K, KUMAR N, et al. Design and Analysis of Secure Lightweight Remote User Authentication And Key Agreement Scheme in Internet of Drones Deployment[J]. IEEE Internet of Things Journal, 2018, 6(2): 3572-3584.
|
| [7] |
BERA B, CHATTARAJ D, DAS A K. Designing Secure Blockchain-Based Access Control Scheme in IoT-Enabled Internet of Drones deployment[J]. Computer Communications, 2020, 153: 229-249.
|
| [8] |
HUSSAIN S, CHAUDHRY S A, ALOMARI O A, et al. Amassing the Security: An ECC-Based Authentication Scheme for Internet of Drones[J]. IEEE Systems Journal, 2021, 15(3): 4431-4438.
|
| [9] |
ZHANG Min, XU Chunxiang, LI Shanshan, et al. On the Security of an ECC-Based Authentication Scheme for Internet of Drones[J]. IEEE Systems Journal, 2022, 4(2): 1-4.
|
| [10] |
ZHANG Min, XU Chunxiang, HUANG Minying. Research on Multi-Server Lightweight Multifactor Authentication Protocol in Telemedicine Environment[J]. Netinfo Security, 2019, 19(10): 42-49.
|
|
张敏, 许春香, 黄闽英. 远程医疗环境下面向多服务器的轻量级多因子身份认证协议研究[J]. 信息网络安全, 2019, 19(10):42-49.
|
| [11] |
ZHANG Min, ZHANG Jiashu, TAN Wenrong. A Secure Sketch-Based Authentication Scheme for Telecare Medicine Information Systems[J]. Journal of Information Science and Engineering, 2016, 32: 395-408.
|
| [12] |
DOLEV D, YAO A. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208.
|
| [13] |
LAMACCHIA B, LAUTER K, MITYAGIN A. Stronger Security of Authenticated Key Exchange[C]// Springer. International Conference on Provable Security. Heidelberg: Springer, 2007: 1-16.
|
| [14] |
MESSERGES T S, DABBISH E A, SLOAN R H. Examining Smart-Card Security under the Threat of Power Analysis Attacks[J]. IEEE Transactions on Computers, 2002, 51(5): 541-552.
|
| [15] |
HANKERSON D, MENEZES A J, VANSTONE S. Guide to Elliptic Curve Cryptography[M]. Berlin: Springer Science & Business Media, 2006.
|
| [16] |
NESSETT D M. A Critique of the Burrows, Abadi and Needham Logic[J]. ACM SIGOPS Operating Systems Review, 1990, 24(2): 35-38.
|
 )
)