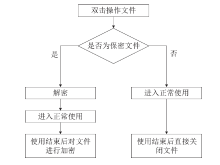
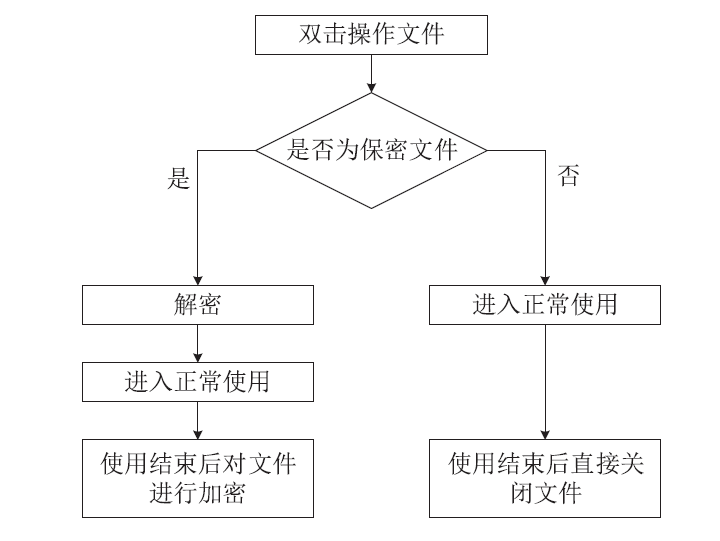
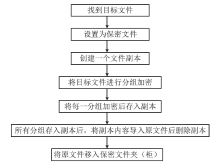
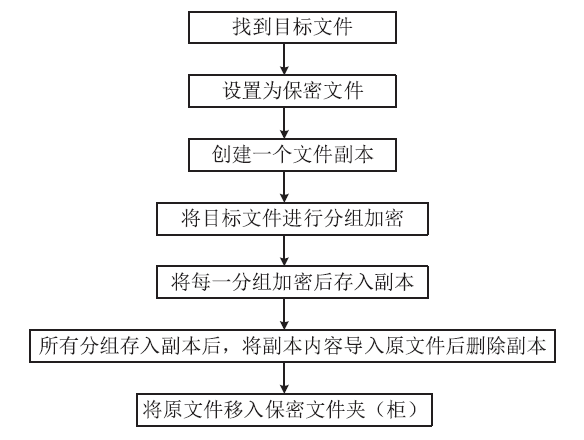
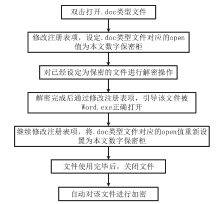
| [1] |
ALBAHDAL A A, ALSOLAMI F, ALSAADI F. Evaluation of Security Supporting Mechanisms in Cloud Storage[C]// IEEE. 11th International Conference on Information Technology: New Generations, April 7-9, 2014, Las Vegas, NV, USA. New York: IEEE, 2014: 285-292.
|
| [2] |
PERIYASAMY P, THENMOZHI E. Data Leakage Detection and Data Prevention Using Algorithm[J]. International Journal of Advanced Research in Computer Science and Software Engineering, 2017, 7(4):251-256.
|
| [3] |
YANG Tengfei, SHEN Peisong, TIAN Xue, et al. Access Control Mechanism for Classified and Graded Object Storage in Cloud Computing[J]. Journal of Software, 2017, 28(9):2334-2353.
|
|
杨腾飞, 申培松, 田雪, 等. 对象云存储中分类分级数据的访问控制方法[J]. 软件学报, 2017, 28(9):2334-2353.
|
| [4] |
SUN Yu, HAN Qingtong, LIU Jianwei. Design of Key Exchange Protocol Based on Short Group Signature[J]. Journal of Computer Research and Development, 2012, 49(12):2619-2622.
|
|
孙钰, 韩庆同, 刘建伟. 基于短群签名的密钥交换协议设计[J]. 计算机研究与发展, 2012, 49(12):2619-2622.
|
| [5] |
LIU Xue. Cloud Storage Security Research and Application[D]. Beijing: North China University of Technology, 2012.
|
|
刘雪. 云存储中的安全问题研究及应用[D]. 北京:北方工业大学, 2012.
|
| [6] |
LAWTON G. New Technology Prevents Data Leakage[J]. Computer, 2008, 9(1):14-17.
|
| [7] |
ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Joumal of Software, 2016, 27(6):1328-1348.
|
|
张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6):1328-1348.
|
| [8] |
HADNAGY C. Social Engineering: The Art of Human Hacking[M]. New Jersey: John Wiley & Sons Inc, 2010.
|
| [9] |
CHEN Rui, TIAN Zhonghe. Research on Data Exchange of GAP Technology[J]. Computer and Digital Engineering, 2005, 33(2):47-49.
|
|
陈睿, 田忠和. 物理隔离网闸数据交换技术的研究[J]. 计算机与数字工程, 2005, 33(2):47-49.
|
| [10] |
WANG Xuehua, ZHANG Binbin. Research on Internal Network Security Technology[J]. Software Guide, 2012, 11(9):131-133.
|
|
王学华, 张彬彬. 内网安全技术研究[J]. 软件导刊, 2012, 11(9):131-133.
|
| [11] |
GUO Feng. Police Network Safety Risk Management Problem Research[D]. Changchun: Jilin University, 2012.
|
|
郭峰. 公安专用网安全风险管理问题研究[D]. 长春:吉林大学, 2012.
|
| [12] |
ZHANG Huanguo, FENG Xiutao, QIN Zhongping, et al. Research on Evolutionary Cryptosystems and Evolutionary DES[J]. Chinese Journal of Computers, 2003, 26(12):1678-1684.
|
|
张焕国, 冯秀涛, 覃中平, 等. 演化密码与DES的演化研究[J]. 计算机学报, 2003, 26(12):1678-1684.
|
| [13] |
COPPERSMITH D. The Data Encryption Standard (DES) and Its Strength Against Attacks[J]. IBM Journal of Research and Development, 1994, 38(3):243-250.
doi: 10.1147/rd.383.0243
URL
|
| [14] |
PATIL P, NARAYANKAR P, NARAYAN D G, et al. A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish[J]. Procedia Computer Science, 2016, 78(1):617-624.
doi: 10.1016/j.procs.2016.02.108
URL
|
| [15] |
GB/T 22239-2019 Information Security Technology-baseline for Classified Protection of Cybersecurity[S]. Beijing: Standards Press of China, 2019.
|
|
GB/T 22239-2019 信息安全技术 网络安全等级保护基本要求[S]. 北京: 标准出版社, 2019.
|
 )
)