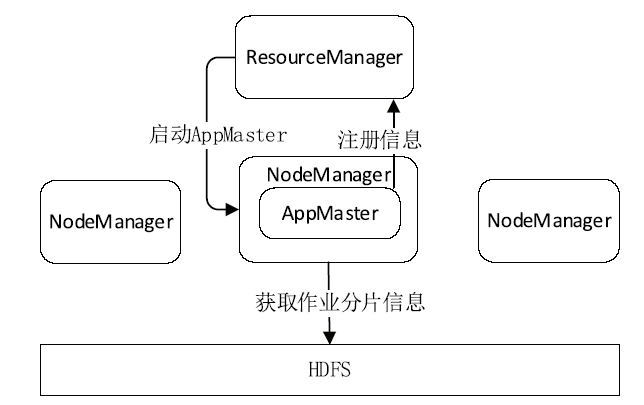
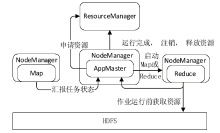
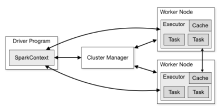
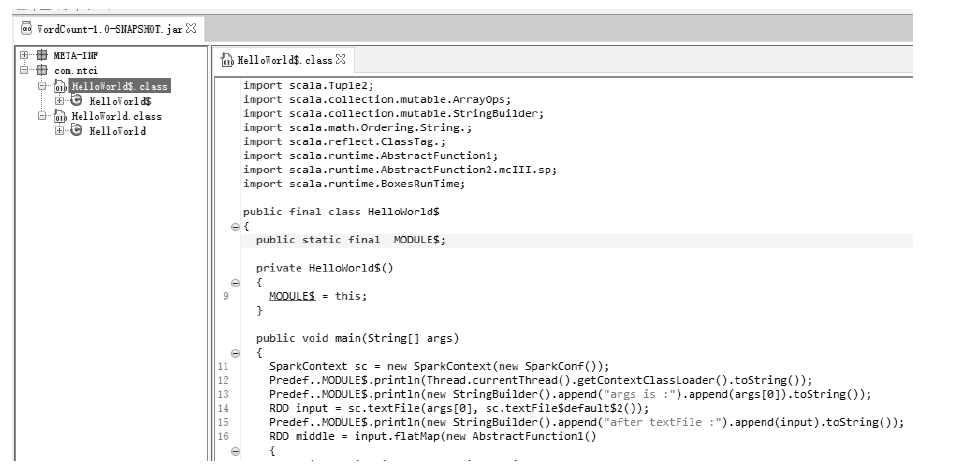
| [1] |
HUANG Kaike.Hadoop Map Reduce Shuffle Process Optimization Solution[D].Wuhan:Huazhong University of Science and Technology,2016.
|
|
黄开科. Hadoop Map Reduce Shuffle过程优化方案研究[D]. 武汉:华中科技大学, 2016.
|
| [2] |
ZAHARIA M, XIN R S, WENDLL P, et al.Apache Spark:a Unified Engine for Big Data Processing[J]. Communications of the Acm, 2016, 59(11):56-65.
|
| [3] |
GONG Yaming. Reinforcement Method and System for Jar Packet:China, CN 106845169 A[P].2017-6-13.
|
| [4] |
ZHAO Hong, GUO Nan.Java Source Code Protection Based on JNI and AES Algorithm[C]// IEEE. 2017 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC),July 21-24,2017,Guangzhou,China. New York:IEEE, 2017:846-849.
|
| [5] |
FENG Dengguo.Computer Communication Network Security [M]. Beijing: Tsinghua University Press, 2001.
|
|
冯登国. 计算机通信网络安全[M].北京:清华大学出版社, 2001.
|
| [6] |
LI Chunhua, WANG Hua, ZHANG Yanzhe, et al.Optimization for Broadcast Encryption in Cloud Using Extended Public Key[J]. Journal of Computer Research and Development, 2017, 54(12): 2741-2747.
|
| [7] |
SONG Jianye, HE Nuan, ZHU Yiming, et al.Design and Implementation of Secure Deduplication System for Ciphertext Data Based on Aliyun[J]. Netinfo Security, 2017 (3) : 39-45.
|
|
宋建业, 何暖, 朱一明, 等. 基于阿里云平台的密文数据安全去重系统的设计与实现[J]. 信息网络安全, 2017, 17(3): 39-45.
|
| [8] |
Tim Lindholm.Java Virtual Machine Specification [M]. Beijing:China Machine Press, 2014.
|
| [9] |
ZHOU Zhiming.Understanding the JVM [M]. Beijing: China Machine Press, 2013.
|
|
周志明. 深入理解Java虚拟机[M].北京:机械工业出版社, 2013.
|
| [10] |
DONG Y,REN K,WANG SY,et al.Construction and Certification of a Bytecode Virtual Machine[J].Journal of Software,2010,21(2):305-317.
|
| [11] |
MA Junyan,ZENG Guosun.Research and Implementation on Parallel Crawl Method for Source Code Based on MapReduce[J].Netinfo Security,2018,19(1):58-66.
|
|
马军岩, 曾国荪. 基于MapReduce的开源代码并行爬取方法研究与实现[J]. 信息网络安全, 2018, 19(1): 58-66.
|
| [12] |
YING Changtian,YU Jiong, BIAN Chen,et al.Criticality Checkpoint Management Strategy Based on RDD Characteristics in Spark. Journal of Computer Research and Development, 2017, 54(12): 2858-2872.
|
| [13] |
LIU Haiqing.DPA Resistant Hardware Implementation of AES Based on Masking[D].Changsha: National University of Defense Technology,2008.
|
|
刘海清. 基于随机掩码的AES算法抗DPA攻击硬件实现[D]. 长沙:国防科技大学, 2008.
|
| [14] |
FEI Liming, ZHENG Xiaojuan, YANG Zhicai, et al.JVMTI-based Implementation of Security Policies Enforcement on java Platform[C]//IEEE. International Conference on Advanced Computer Theory & Engineering,Auguest 20-22,2010,Chengdu China. New York:IEEE, 2010: 210-213.
|
| [15] |
WHITE T.Hadoop: The Definitive Guide[M]. California : O'Reilly Media, 2012.
|
 ), Xingshu CHEN2, Yonggang LUO2
), Xingshu CHEN2, Yonggang LUO2