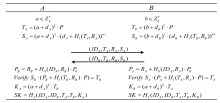
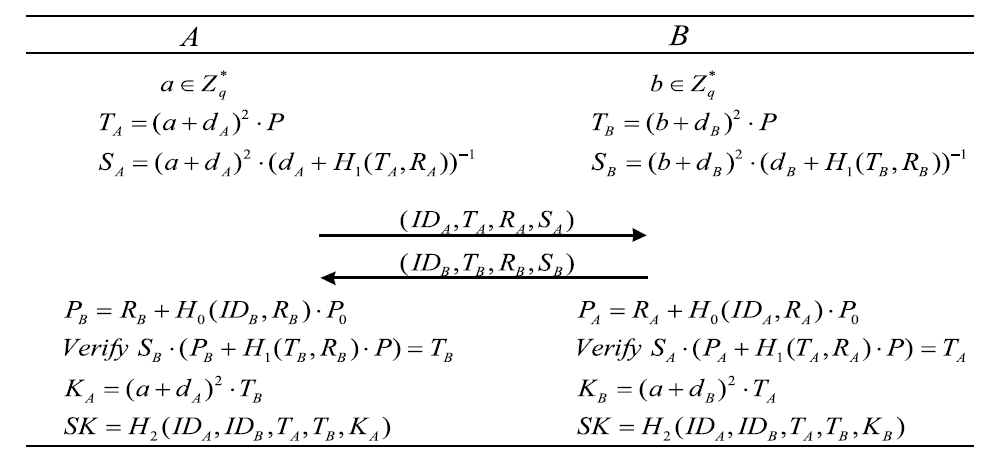
| [1] |
MANDT T K, CHIK H T.Certificateless Authenticated Two-party Key Agreement Protocols[C]// IACR. 11th Asian Computing Science Conference, December 6-8, 2006, Tokyo, Japan. Heidelberg: Springer,2006: 37-44.
|
| [2] |
XIA L,WANG S, SHEN J, et al.Breaking and Repairing the Certificateless Key Agreement Protocol from ASIAN 2006[J]. Wuhan University Journal of Natural Sciences, 2008, 13(5): 562-566.
|
| [3] |
WANG F, ZHANG Y.A New Provably Secure Authentication and Key Agreement Mechanismfor SIP Using Certificateless Public-key Cryptography[J]. Computer Communications,2008, 31(10):2142-2149.
|
| [4] |
GORIPARTHI T, DAS M L, SAXENA A.An Improved Bilinear Pairing Based Remote User Authentication Scheme[J]. Computer Standards and Interfaces, 2009,31(1): 181-185.
|
| [5] |
WU T Y, TSENG Y M.An Efficient User Authentication and Key Exchange Protocol for Mobile Client-server Environment[J]. Computer Networks, 2010, 54(9): 1520-1530.
|
| [6] |
PAN J, LIU X, XIE M, et al.Certificateless-based Two-party Authenticated Key Agreement Protocols in A Multiple PKG Environment[C]//IEEE.1st IEEE International Conference on Computer Science and Network Technology, December 24-26, 2011, Harbin, China. New Jersey: IEEE,2011: 2364-2367.
|
| [7] |
HE D.An Efficient Remote User Authentication and Key Agreement Protocol for Mobile Clientserver Environment from Pairings[J]. Ad Hoc Networks, 2012,10(6), 1009-1016.
|
| [8] |
WANG C, ZHANG Y.New Authentication Scheme for Wireless Body Area Networks Using the Bilinear Pairing[J]. Journal of Medical Systems,2015, 39(11): 1-8.
|
| [9] |
WU L, ZHANG Y, XIE Y, et al.An Efficient and Secure Identity-based Authentication and Key Agreement Protocol With User Anonymity for Mobile Devices[J]. Wireless Personal Communications, 2017, 94(4): 3371-3387.
|
| [10] |
WANG Zhen, MA Zhaofeng, LUO Shoushan.Identity-based Efficient Authentication and Key Agreement Protocol for Mobile Internet[J]. Journal on Communications,2017,38(8):19-27.
|
|
王真,马兆丰,罗守山.基于身份的移动互联网高效认证密钥协商协议[J].通信学报,2017,38(8):19-27.
|
| [11] |
MILLER V S.Use of Elliptic Curves in Cryptography[C]// IACR. 5th Annual International Cryptology Conference, August, 18-22, 1985, Santa Barbara, CA, USA. Heidelberg: Springer,1985: 417-426.
|
| [12] |
MENEZES A, QU M, VANSTONE S.Some New Key Agreement Protocols Providing Implicit Authentication[C]//ACM. 2nd Work on Selected Areas in Cryptography, August 17-18, 1995, Ontario, Canada. New York:ACM, 1995: 22-32.
|
| [13] |
ZHU R W, YANG G, WONG D S.An Efficient Identity-based Key Exchange Protocol with KGS Forward Secrecy for Low-power Devices[J]. Theoretical Computer Science, 2007, 378(2): 198-207.
|
| [14] |
CAO X, KOU W, YU Y, SUN R.Identity-based Authenticated Key Agreement Protocols without Bilinear Pairings[J]. IEICE Transactions on Fundamentals of Electronics, 2008, 91(12): 3833-3836.
|
| [15] |
HOU M, XU Q.A Two-party Certificateless Authenticated Key Agreement Protocol without Pairing[C]//IEEE. 2nd IEEE International Conference on Computer Science and Information Technology, August 8-11, 2009, Beijing, China. New Jersey: IEEE,2009: 412-416.
|
| [16] |
CAO X, KOU W, DU X.A Pairing-free Identity-based Authenticated Key Agreement Protocol with Minimal Message Exchanges[J]. Information Sciences, 2010, 180(15): 2895-2903.
|
| [17] |
YANG G, TAN C H.Strongly Secure Certificateless Key Exchange without Pairing[C]//ACM. 6th ACM Symposium on Information, Computer and Communications Security. March 22-24, 2011, Hong Kong, China. New York: ACM, 2011: 71-79.
|
| [18] |
ISLAM S H, BISWAS G P.An Improved Pairing-free Identity-based Authenticated Key Agreement Protocol Based on ECC[J]. Procedia Engineering, 2012, 12(30): 499-507.
|
| [19] |
ZHANG Yanhong, CHEN Ming.Strongly Secure Certificateless Authenticated Key Agreement Protocol in Standard Model[J], Journal of Sichuan University (Engineering Science Edition) ,2013,45(1):125-132.
|
|
张延红,陈明.标准模型下强安全的无证书认证密钥协商协议[J].四川大学学报(工程科学版),2013,45(1):125-132.
|
| [20] |
QIAN Qifeng, CHENG Chunling.Pairing-free Certificateless Group Key Agreement Protocol for Wireless Sensor Network[J]. Computer Science,2015,42(7):186-190.
|
|
钱琦锋,程春玲.WSN中基于非双线性对的无证书群组密钥协商协议[J].计算机科学,2015,42(7):186-190.
|
| [21] |
KIM Y J, KIM Y M, CHOE Y J.An Efficient Bilinear Pairing-free Certificateless Two-party Authenticated Key Agreement Protocol in The ECK Model[J]. Journal of Theoretical Physics and Cryptography, 2013, 16(3): 1-10.
|
| [22] |
ZHANG Quanling, LU Yang.Attack and Improvement of ACertificateless Two-party Authenticated Key Agreement Protocol[J]. Information Technology, 2015, 39(7): 4-8.
|
|
张全领,陆阳. 无证书两方认证密钥协商协议攻击及改进[J]. 信息技术,2015,39(7):4-8.
|
| [23] |
SHI Min, YE Weiwei, OU Qingyu.Identity-based Authenticated Protocol without Bilinear Pairing[J]. Netinfo Security,2016, 15(10):21-27.
|
|
矢敏,叶伟伟,欧庆于.不需双线性对的基于身份的认证密钥协商协议[J].信息网络安全,2016,15(10):21-27.
|
| [24] |
ISLAM S H, BISWAS G P.A Pairing-free Identity-based Two-party Authenticated Key Agreement Protocol for Secure and Efficient Communication[J]. Journal of King Saud University-Computer and Information Sciences, 2017, 29(1): 63-73.
|
| [25] |
SHAN Chun, HU Kangwen, XUE Jingfeng, et al.Improved Pairing-free Constant Round Certificateless Authenticated Group Key Agreement Protocol[J]. Journal of Tsinghua University, 2017, 57(6): 580-585.
|
|
单纯,胡康文,薛静锋,等. 改进的无双线性对固定轮数无证书群组密钥协商协议[J]. 清华大学学报, 2017,57(6):580-585.
|
 ), Zhanjing RUAN1, Ruijie ZHANG1
), Zhanjing RUAN1, Ruijie ZHANG1