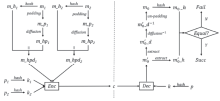
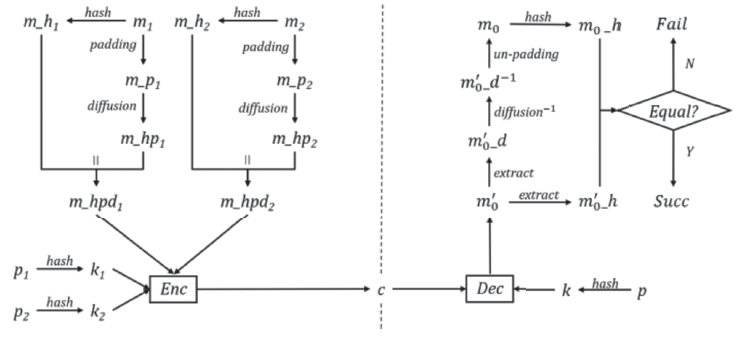
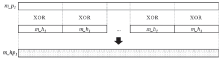
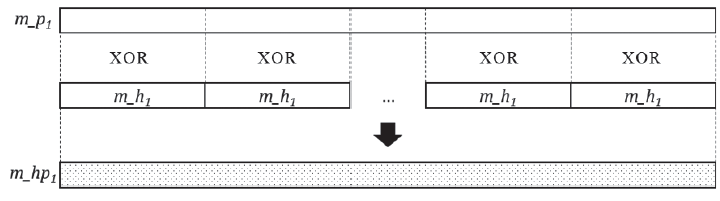
| [1] |
HU Yupu Symmetric Cryptography [M]U Yupu Symmetric Cryptography [M]. Beijing:Mechanical Industry Publishing House, 2002.
|
|
胡予濮. 对称密码学[M]. 北京:机械工业出版社, 2002.
|
| [2] |
FIPSPUB 46-3 Data Encryption Standard(DES)[S]. U.S. DEPARTMENT OF COMMERCE/National Institute of Standards and and Technology(NIST). Federal Information Processing Standards Publication 46-3, 1999-10-25.
|
| [3] |
XU Hongbo, LI Yinghua.The Application of DES Encryption Algorithm to Protect Data Security in the File Transfer[J]. Netinfo Security, 2009,9(6): 24-26, 76.
|
|
徐洪波, 李颖华. DES加密算法在保护文件传输中数据安全的应用[J]. 信息网络安全, 2009,9(6):24-26, 76.
|
| [4] |
KARN P,METAGER P,SIMPSON W.RFC1851[EB/OL]. ,2018-1-15.
|
| [5] |
LAI X.International Data Encryption Algorithm[J]. Hepatology, 2016, 60(6):2125-2126.
|
| [6] |
FIPSPUB 197 Specification for the Advanced Encryption Standard(AES)[S]. New York:Federal Information Processing Standards Publication,2001.
|
| [7] |
ZHANG Jinhui, GUO Xiaobiao, FU Xin.AES Encryption Algorithm Analysis and the Application in Information Security[J]. Netinfo Security, 2011, 11(5): 31-33.
|
|
张金辉, 郭晓彪, 符鑫. AES加密算法分析及其在信息安全中的应用[J]. 信息网络安全, 2011, 11(5): 31-33.
|
| [8] |
FENG Dengguo.Status Quo and Trend of Cryptography[J]. Journal of China Institute of Communications, 2002,23(5):18-26.
|
|
冯登国. 国内外密码学研究现状及发展趋势[J]. 通信学报, 2002, 23(5):18-26.
|
| [9] |
ISO/IEC 9797-1[S].Switzerland:International Organization for Standardization,1999.
|
| [10] |
HOUSLEY R, RFC5652[EB/OL]. ,2018-1-15.
|
| [11] |
ZHANG Xinjuan.Feasible Suggestions of Digital Works Copyright Protection[J]. Published Reference, 2015(8):18-19.
|
|
张新娟. 数字作品版权保护可行性建议[J].出版参考,2015,8:18-19.
|
| [12] |
LI Fagen, ZHONG Di.A Survey of Digital Signcryption[J]. Netinfo Security, 2011, 11(12): 1-8.
|
|
李发根, 钟笛. 数字签密综述[J]. 信息网络安全, 2011,11(12):1-8.
|
| [13] |
LIU Xinyue, LI Hua.A New Digital Copyright Protection Method Based on Digital Certificate and Device: China, CN101714195A [P]. 2010.
|
|
刘辛越, 李华.一种基于数字证书的新型数字版权保护方法和装置:中国,CN101714195A[P]. 2010.
|
| [14] |
LIU Wenlong, LI Hui, JIN Dongxun.Research on Digital Fingerprinting Generation Scheme and Key Algorithm[J]. Netinfo Security, 2015,15(2):66-70.
|
|
刘文龙, 李晖, 金东勋. 数字指纹生成方案及关键算法研究[J]. 信息网络安全, 2015,15(2):66-70.
|
| [15] |
HUANG Qinlong, MA Zhaofeng, FU Jingyi, et al.Privacy-preserving Digital Rights Management Scheme in Cloud Computing[J].Journal on Communications,2014(2):95-103.
|
|
黄勤龙,马兆丰,傅镜艺,等.云计算环境中支持隐私保护的数字版权保护方案[J].通信学报,2014(2):95-103.
|
| [16] |
HUANG TAO, ZHANG Zhiyong, TIAN Weili, et al.A Digital Rights Management System Based on Trusted Computing: China, CN202663435U [P]. 2013.
|
|
黄涛, 张志勇, 田伟莉,等.一种基于可信计算的数字版权管理系统:中国,CN202663435U[P]. 2013.
|
| [17] |
XING Bin, LIU Jiqiang, HAN Zhen.A New Model for Measuring the Integrity of Trusted Computing Platforms[J]. Netinfo Security, 2016,16(6) :8-14.
|
|
邢彬, 刘吉强, 韩臻. 一种可信计算平台完整性度量的新模型[J].信息网络安全,2016,16(6): 8-14.
|
| [18] |
ZHU LEI, JING LEI."Internet +" under the Environment of Digital Copyright Protection Model[J]. Journal of Electronic Technology and Software Engineering, 2017 (20) : 209-211.
|
|
朱磊,荆磊.“互联网+”环境下数字版权保护模式[J].电子技术与软件工程,2017(20):209-211.
|
| [19] |
YU Yinyan, TANG Zhi.A Survey of the Research on Digital Rights Management[J]. Chinese Journal of Computers, 2005, 28(12) :1957-1968.
|
|
俞银燕,汤帜.数字版权保护技术研究综述[J].计算机学,2005 , 28(12) :1957-1968.
|
| [20] |
An XiaoLan Tan Yunming. Amazon E-book Business Model Analysis[J]. Journal of Published Research, 2009 (6) : 49-52.
|
|
安小兰, 谭云明. 亚马逊电子书经营模式分析[J]. 出版发行研究, 2009(6):49-52.
|
 ), Zhiqi SONG2, Tianyu WANG3
), Zhiqi SONG2, Tianyu WANG3