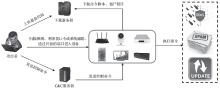
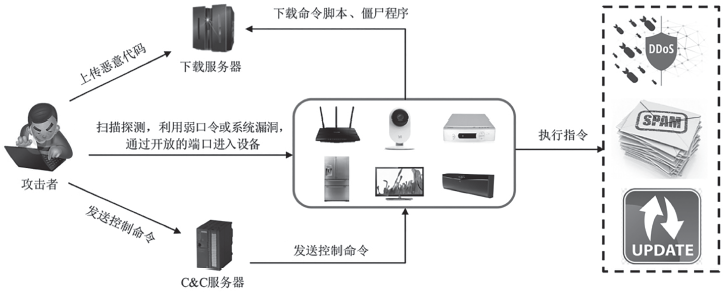
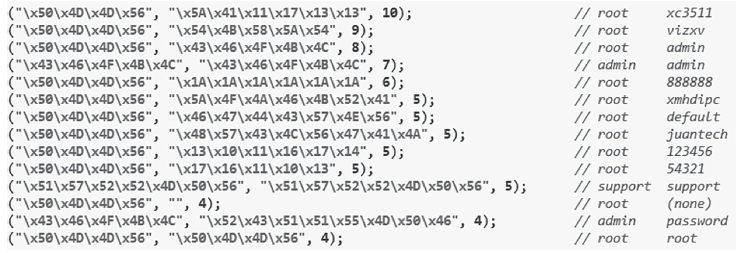
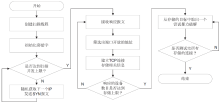
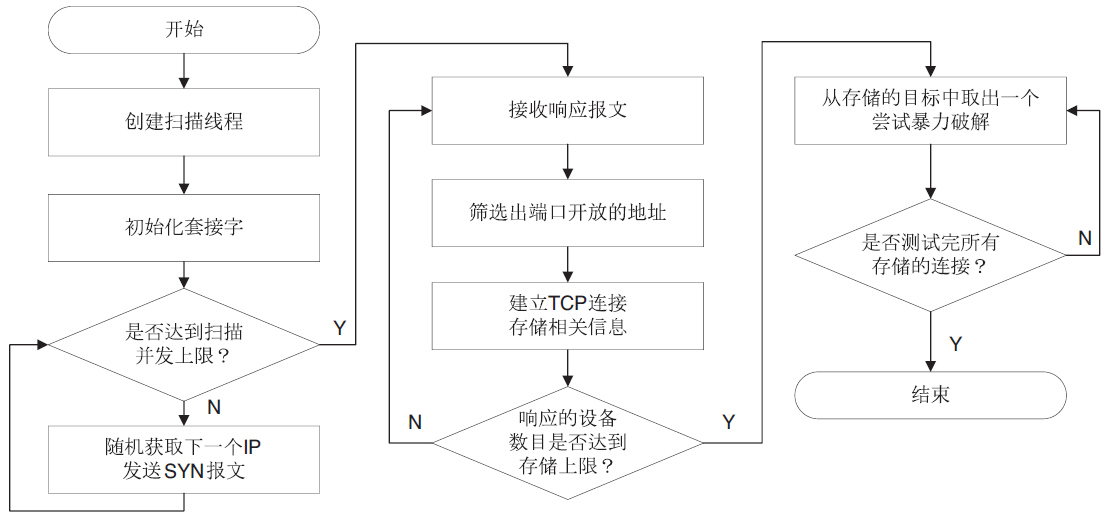
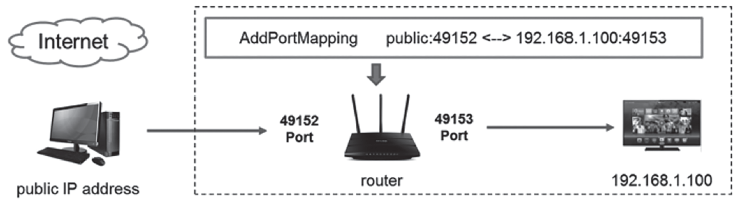
| [1] |
WEISER M.The Computer for the 21st Century[J]. Scientific amer-ican, 1991, 265(3): 94-104.
|
| [2] |
ITU-T Y. Overview of Ubiquitous Networking and of Its Support in NGN[EB/OL]. https://www.itu.int/rec/T-REC-Y.2002-200910-I/en, 2017-7-15.
|
| [3] |
GARTNER. Gartner Says 6.4 Billion Connected "Things" Will Be in Use in 2016, Up 30 Percent From 2015[EB/OL]. .
|
| [4] |
LI Ke, FANG Binxing, CUI Xiang, et al.Study of Botnets Trends[J]. Journal of Computer Research and Development, 2016, 53(10): 2189-2206.
|
|
李可,方滨兴,崔翔,等. 僵尸网络发展研究[J]. 计算机研究与发展, 2016, 53(10): 2189-2206.
|
| [5] |
TRAYNOR P,LIN M,ONGTANG M, et al.On Cellular Botnets: Meas-uring the Impact of Malicious Devices on a Cellular Network Core[C]// ACM.16th ACM conference on Computer and communi-cations security, November 9-13, 2009, Chicago, Illinois, USA. New York: ACM, 2009:223-234.
|
| [6] |
DURFINA L,KROUSTEK J,ZEMEK P. PsybOt Malware: A Step-by-step Decompilation Case Study[EB/OL]. https://retdec.com/web/files/publications/DEC_WCRE_13.pdf, 2017-7-15.
|
| [7] |
INTELLIGENCE B. There will be 24 Billion IoT Devices insTalled on Earth by 2020[EB/OL]. .
|
| [8] |
IDC. Worldwide and Regional Internet of Things (IoT) 2014-2020 Forecast: A Virtuous Circle of Proven Value and Demand[EB/OL].
|
| [9] |
LI Zhicong,ZHOU Zhiping.Enhanced Secure RFID Authentication Protocol in IoT[J].Netinfo Security, 2018, 18(11):80-87.
|
|
李智聪,周治平.物联网中增强安全的RFID认证协议[J].信息网络安全,2018,18(1):80-87.
|
| [10] |
ZILLNER T, STROBL S.ZigBee Exploited: The Good the bad and the Ugly[J].Magdeburger Journal zur Sicherheitsforschung, 2015(12):699-704.
|
| [11] |
QIU Yue.Security Analysis for the Information of Wearable De-vices[J]. Netinfo Security, 2016, 16(9):79-83.
|
|
裘玥. 智能可穿戴设备信息安全分析[J].信息网络安全,2016,16(9):79-83.
|
| [12] |
Wrightwood Surveillance Support. Hikvision Default IP address, user name,password[EB/OL]. , 2017-7-15.
|
| [13] |
CVE. CVE-2015-7755[EB/OL]. , 2017-7-15.
|
| [14] |
SEKURAK. TP-Link http/tftp Backdoor[EB/OL]. , 2017-7-15.
|
| [15] |
HEWLETT PACKARD. Internet of Things Research Study[EB/OL]. , 2017-7-15.
|
| [16] |
HEFFNER C. Exploiting Network Surveillance Cameras Like a Hollywood Hacker [EB/OL]. ,2017-7-15.
|
| [17] |
MACESANU G, CODAS T T, SULIMAN C, et al.Development of GTBoT, A High Performance and Modular Indoor Ro-bot[C]//IEEE.AQTR '10 Proceedings of the 2010 IEEE International Conference on Automation, Quality and Testing, Robotics (AQTR) , May 28 - 30, 2010 ,Cluj-Napoca,Romania.New York: IEEE, 2010: 1-6.
|
| [18] |
ARCE I,LEVY E.An Analysis of the Slapper Worm[J]. IEEE Security & Privacy, 2003, 99(1): 82-87.
|
| [19] |
F-Secure. Bobax Description [EB/OL]. , 2017-7-15.
|
| [20] |
SHIN S,GU G.Conficker and Beyond: A Large-scale Empirical Study[C]//ACM.26th Annual Computer Security Applications Conference, December 6-10, 2010, Austin, Texas, USA. New York: ACM, 2010:151-160.
|
| [21] |
AXELLE A. Symbian Worm Yxes Towards Mobile Botnets[EB/OL]. , 2017-7-15.
|
| [22] |
PORRAS P, SAIDI H,YEGNESWARAN V. An Analysis of the Ikee.B iphone Botnet[EB/OL]. , 2017-7-15.
|
| [23] |
WYATT TIM. Security Alert: Geinimi, Sophisticated New Android Trojan Found in Wild[EB/OL]. , 2017-7-15.
|
| [24] |
INSECURETY RESEARCH. Hydra IRC Bot, the 25 Minute Overview of the Kit[EB/OL]. , 2017-7-15.
|
| [25] |
CELEDA P, KREJCI R,VYKOPAL J, et al.Embedded Malware-an Analysis of the Chuck Norris Botnet[EB/OL]. , 2010.
|
| [26] |
BOTNET C. Internet Census 2012: Port Scanning/0 Using Insecure Embedded Devices[EB/OL]., 2017-7-15.
|
| [27] |
GITHUB. Lightaidra[EB/OL]., 2017-7-15.
|
| [28] |
PROOFPOINT. Proofpoint Uncovers Internet of Things (IoT) CybeRattack[EB/OL]. ,2017-7-15.
|
| [29] |
SYMANTEC. Linux.Darlloz[EB/OL]. , 2017-7-15.
|
| [30] |
AKAMAI. Spike DDoS Toolkit[EB/OL]. , 2017-7-15.
|
| [31] |
ESET. Dissecting Linux/Moose[EB/OL]. , 2017-7-15.
|
| [32] |
SYMANTEC. Is There an Internet-of-Things Vigilante out There?[EB/OL]. , 2017-7-15.
|
| [33] |
ESET. Meet Remaiten-a Linux Bot on Steroids Targeting Routers and Potentially other IoT Devices[EB/OL]. , 2017-7-15.
|
| [34] |
PALOALTO.New IoT/Linux Malware Targets DVRs, Forms Botnet[EB/OL]., 2017-7-15.
|
| [35] |
THREAT Post.BASHLITE Family Of Malware Infects 1 Million IoT Devices [EB/OL]. , 2017-7-15.
|
| [36] |
GITHUB. Mirai-Source-Code[EB/OL]., 2017-7-15.
|
| [37] |
TRENDMICRO. ELF_PERSIRAI.A[EB/OL]., 2017-7-15.
|
| [38] |
TRENDMICRO. Persirai: New Internet of Things (IoT) Botnet Targets IP Cameras[EB/OL]. , 2017-7-15.
|
| [39] |
PERAKOVIC D,PERISA M,CVITIC I. Analysis of the IoT Impact on Volume of DDoS Attacks[EB/OL]. , 2017-7-15.
|
| [40] |
KOLIAS C,KAMBOURAKIS G, STAVROU A, et al.DDoS in the IoT: Mirai and other Botnets[J]. Computer, 2017, 50(7): 80-84.
|
| [41] |
PAGANINI P. More than 900k Routers of Deutsche Telekom German Users Went Offline[EB/OL]. , 2017-7-15.
|
| [42] |
OHARROW J R. Cyber Search Engine Shodan Exposes Industrial Control Systems to New Risks[EB/OL]. , 2017-7-15.
|
| [43] |
RAPID7. R7-2014-18: Hikvision DVR Devices-Multiple Vulnerabilities[EB/OL]. , 2017-7-15.
|
| [44] |
US-CERT. Heightened DDoS Threat Posed by Mirai and Other Botnets[EB/OL]., 2017-7-15.
|
| [45] |
FAN Hong, SHAO Hua, LI Haitao.Implementation and Application of Internet of Things Security Technology[J]. Netinfo Security, 2017,17(9):38-41.
|
|
范红,邵华,李海涛.物联网安全技术实现与应用[J].信息网络安全,2017,17(9):38-41.
|
 ), Fangjiao ZHAGN1,2
), Fangjiao ZHAGN1,2