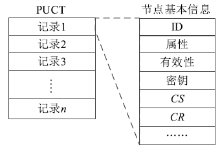
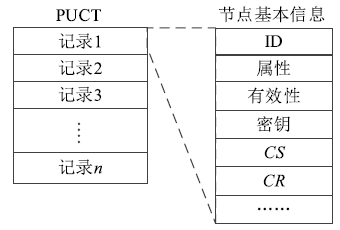
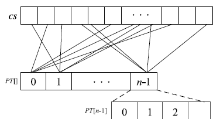
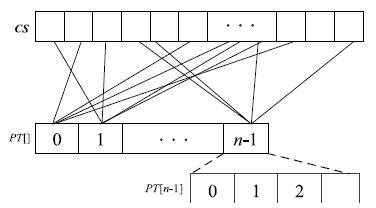
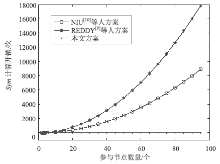
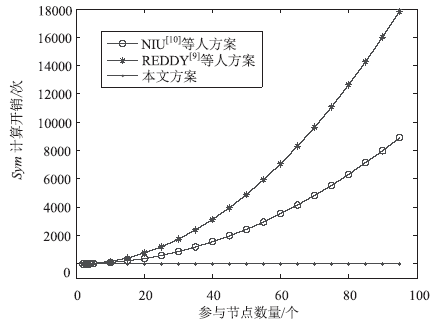
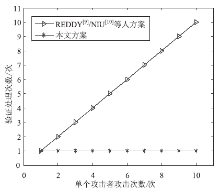
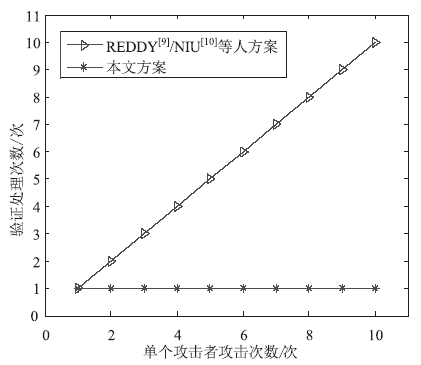
| [1] |
LUO Xun, YAN Chenhua.Research and Design on Security System of Wireless Mesh Network[J]. Netinfo Security, 2015, 15(6): 61-66.
|
|
罗旬,严承华. 无线Mesh网络安全体系研究与设计[J]. 信息网络安全,2015,15(6):61-66.
|
| [2] |
ZHANG Mingde, ZHENG Xuefeng, LV Shuwang, et al.Research on Trust Degree of Authentication[J]. Computer Science, 2011, 38(11): 43.
|
| [3] |
PENG Kunlun, PENG Wei, WANG Dongxia, et al.Research Survey on Security Issues in Cyber-physical Systems[J]. Netinfo Security, 2016, 16(7): 20-28.
|
|
彭昆仑,彭伟,王东霞,等. 信息物理融合系统安全问题研究综述[J]. 信息网络安全,2016,16(7):20-28.
|
| [4] |
MAHALLE N, ANGGOROJATI B, PRASAD N R, et al. Identity Authentication and Capability Based Access Control (IACAC) for the Internet of Things[EB/OL]. , 2018-4-11.
|
| [5] |
ZHANG Yuting, YAN Chenhua, WEI Yuren.Research on Security of IoT Perception Layer Based on Node Authentication[J]. Netinfo Security, 2015, 15(11): 27-32.
|
|
张玉婷,严承华,魏玉人. 基于节点认证的物联网感知层安全性问题研究[J]. 信息网络安全,2015,15(11):27-32.
|
| [6] |
ZHANG Qiyuan, ZHOU Xuehai, YANG Feng.Distributed Node Authentication in Wireless Sensor Networks[C]//IEEE. 5th International Conference on Wireless Communications, Networking and Mobile Computing, September 24-26, 2009, Beijing, China. New Jersey: IEEE, 2009: 1-4.
|
| [7] |
ZHOU Jun, CAO Zhenfu, DONG Xiaolei, et al.Security and Privacy for Cloud-Based IoT: Challenges[J]. IEEE Communications Magazine, 2017, 55(1): 26-33.
|
| [8] |
FARASH M S, TURKANOVIĆ M, KUMARI S, et al.An Efficient User Authentication and Key Agreement Scheme for Heterogeneous Wireless Sensor Network Tailored for the Internet of Things Environment[J]. Ad Hoc Networks, 2016, 36(P1): 152-176.
|
| [9] |
REDDY A G, DAS A K, YOON E J, et al. A Secure Anonymous Authentication Protocol for Mobile Services on Elliptic Curve Cryptography[EB/OL]. , 2018-4-11.
|
| [10] |
NIU Jianwei, LI Xiong.A Novel User Authentication Scheme with Anonymity for Wireless Communications[J]. Security and Communication Networks, 2014, 7(10): 1467-1476.
|
| [11] |
SOOD S K.An Improved and Secure Smart Card Based Dynamic Identity Authentication Protocol[J]. International Journal of Network Security, 2012, 14(1): 39-46.
|
| [12] |
SMART N P.Cryptography Made Simple[J]. Information Security & Cryptography, 2016, 46(12): 96-99.
|
| [13] |
DU Wenliang, ATALLAH M J.Secure Multi-party Computation Problems and Their Applications: a Review and Open Problems[C]//ACM. 2001 Workshop on New Security Paradigms, September 10-13, 2001, Cloudcroft, New Mexico. New York: ACM, 2001: 13-22.
|
| [14] |
DU Wenliang, ZHAN Zhijun.A Practical Approach to Solve Secure Multi-party Computation Problems[C]//ACM. 2002 Workshop on New Security Paradigms, September 23-26, 2002, Virginia Beach, Virginia. New York: ACM, 2002: 127-135.
|
| [15] |
ATALLAH M J, DU Wenliang.Secure Multi-party Computational Geometry[C]//Springer. 2001 Workshop on Algorithms and Data Structures, August 8-10, 2001, Providence, RI, USA. Heidelberg: Springer, 2001: 165-179.
|
| [16] |
LUO Yonglong, HUANG Liusheng, ZHONG Hong.Secure Two-party Point-circle Inclusion Problem[J]. Journal of Computer Science and Technology, 2007, 22(1): 88-91.
|
| [17] |
KILINÇ H, KÜPÇÜ A. Optimally Efficient Multi-party Fair Exchange and Fair Secure Multi-party Computation[EB/OL]. , 2018-4-12.
|
 ), Ziyang ZHANG1,2, Taochun WANG1,2, Dong XIE1,2
), Ziyang ZHANG1,2, Taochun WANG1,2, Dong XIE1,2