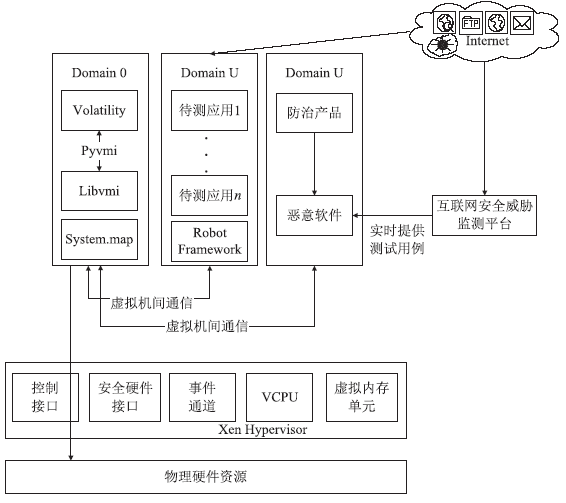
| [1] |
宋好好. 云计算信息系统信息安全等级保护测评关键技术研究[J]. 信息网络安全,2015(9):167-169.
|
| [2] |
吴军,张向丽,张轶君,等. 一种基于xenVMI机制下的蜜网流量异常检测方法[J]. 电子技术应用,2015,41(1):122-124.
|
| [3] |
温志渊,翟健宏,徐径山,等.基于攻击行为树的恶意代码检测平台[J]. 信息网络安全,2013(9):22-25.
|
| [4] |
金海. 计算机系统虚拟化一原理与应用[M].北京:清华大学出版社,2008.
|
| [5] |
虚拟化与云计算小组.虚拟化与云计算[M]. 北京:电子工业出版社,2009.
|
| [6] |
GARFINKEL T, ROSENBLUM M. A Virtual Machine Introspection Based Architecture for Intrusion Detection[EB/OL]. , 2016-4-12.
|
| [7] |
李海威,范博,李文锋. 一种可信虚拟平台构建方法的研究和改进[J]. 信息网络安全,2015(1):1-5.
|
| [8] |
PAYNE B D. Simplifying Virtual Machine Introspection Using Libvmi[EB/OL]. , 2012-1-20.
|
| [9] |
DOLAN-GAVITT B, LEEK T, ZHIVICH M, et al.Virtuoso: Narrowing the Semantic Gap in Virtual Machine Introspection[J]. Security & Privacy IEEE Symposium on, 2011, 42(12): 297-312.
|
| [10] |
杨先强,双锴,王玉龙. 虚拟机内省技术研究[EB/OL]. , 2012-12-18.
|
| [11] |
Gavitt B D, Bryan P, Wenke L. Leveraging Forensic Tools for Virtual Machine Introspection[EB/OL]. , 2016-4-15.
|
| [12] |
ZOLKIPLI M F, JANTAN A.Malware Behavior Analysis: Learning and Understanding Current Malware Threats[C]//Universiti Utara Malaysia. Second International Conference on Network Applications, Protocols and Services, September 22-23, 2010, Alor Setar, Malaysia. New Jersey: IEEE, 2010: 218-221.
|
| [13] |
LENGYEL T K, MARESCA S, PAYNE B D, et al.Scalability, Fidelity and Stealth in the DRAKVUF Dynamic Malware Analysis System[C]//ACSAC. 30th Annual Computer Security Applications Conference, December 8-12, 2014, New Orleans. New York: ACM, 2014: 386-395.
|
| [14] |
HENDERSON A, PRAKASH A, YAN L K, ET AL. Make It Work, Make It Right, Make It Fast: Building a Platform-neutral Whole-system Dynamic Binary Analysis Platform[C]//ACM. 2014 International Symposium on Software Testing and Analysis, July 21-26, 2014, San Jose, CA, USA. New York:ACM, 2014: 248-258.
|
| [15] |
LENGYEL T K, NEUMANN J, MARESCA S, et al.Virtual Machine Introspection in a Hybrid Honeypot Architecture[C]//USENIX. 5th USENIX Conference on Cyber Security Experimentation and Test, August 8-10, 2012, Bellevue, USA. New York: ACM, 2012: 1-8.
|
| [16] |
RILEY R, JIANG Xuxian, XU Dongyan.Multi-aspect Profiling of Kernel Rootkit Behavior[C]//EuroSys. 4th European Conference on Computer Systems, March 31-April 3, 2009, Nuremberg, Germany. New York: ACM, 2009: 47-60.
|
| [17] |
XUAN C, COPELAND J, BEYAH R.Toward Revealing Kernel Malware Behavior in Virtual Execution Environments[C]//RAID. Recent Advances in Intrusion Detection International Symposium, September 23-25, 2009, Saint-Malo, France. Berlin: Springer, 2009: 304-325.
|
| [18] |
DINABURG A, ROYAL P, SHARIF M, et al.Ether: Malware Analysis via Hardware Virtualization Extensions[C]//ACM. 15th ACM Conference on Computer and Communications Security, October 27-31, 2008, Alexandria, Virginia, USA. New York: ACM, 2008: 51-62.
|
| [19] |
WANG Yichuan, MA Jianfeng, LU Di, et al.Game Optimization for Internet DDoS Attack Detection in Cloud Computing[J]. Journal of Computer Research and Development, 2015, 52(8): 1873-1882.
|
| [20] |
李辉,陈兴蜀,张磊,等.一种针对Xen超级调用的入侵防护方法[J]. 信息网络安全,2014(12):43-46.
|
 ), Qing CHANG2, Zhaojun GU3
), Qing CHANG2, Zhaojun GU3