Netinfo Security ›› 2016, Vol. 16 ›› Issue (8): 18-23.doi: 10.3969/j.issn.1671-1122.2016.08.004
• Orginal Article • Previous Articles Next Articles
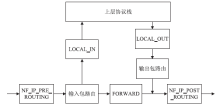
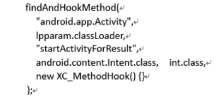
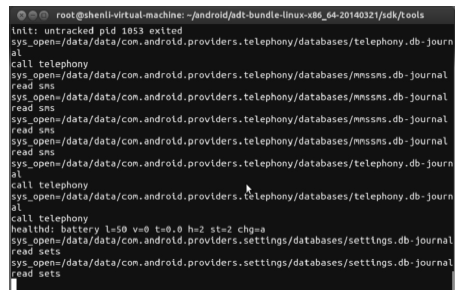
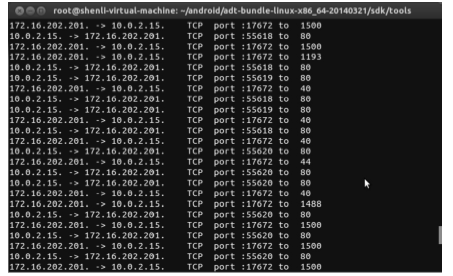
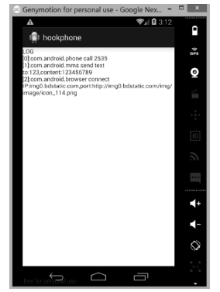
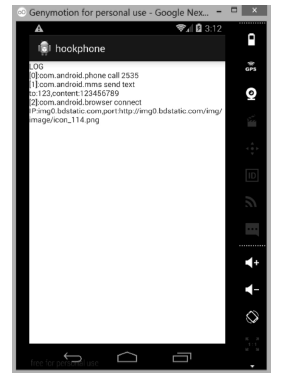
An APP Sensitive Behaviors Detection Method Based on Android Kernel and Its Implementation
Weiping WEN( ), Yang TANG, Li SHEN
), Yang TANG, Li SHEN
- School of Software & Microelectronics, Peking University, Beijing 102600, China