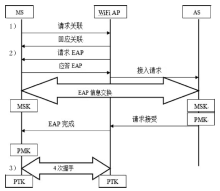
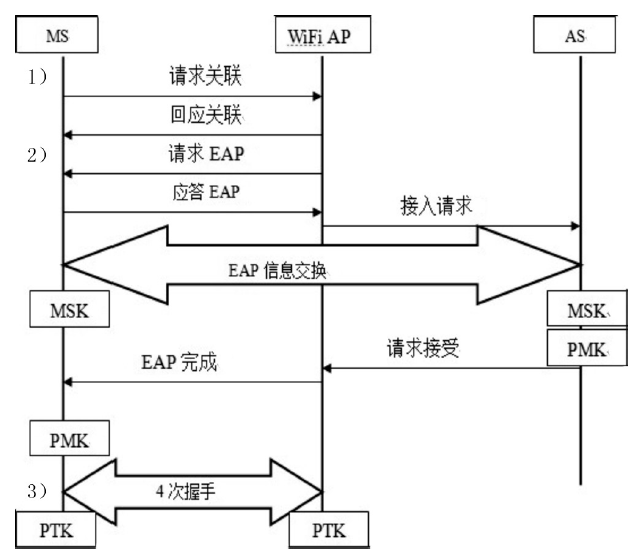
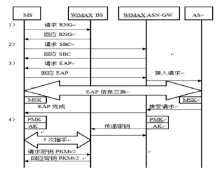
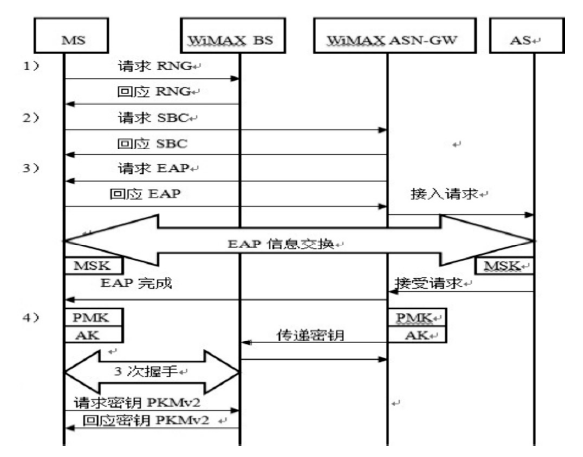
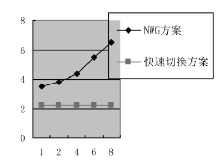
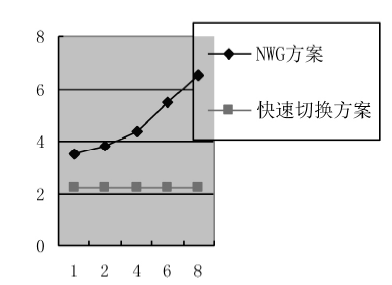
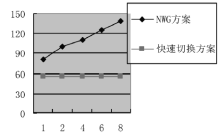
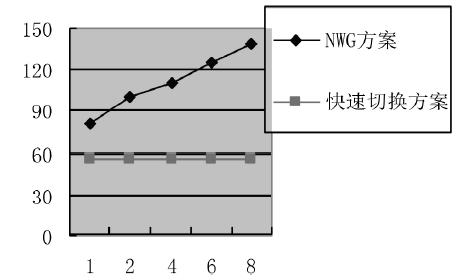
| [1] |
Network Working Group.WiMAX Forum[EB/OL].,2011-11-12.
|
| [2] |
RFC 5191.ProtocolforCarryingAuthentication for Network Access (PANA)FC 5191.ProtocolforCarryingAuthentication for Network Access (PANA)[S]. 2008.
|
| [3] |
Sun H M,chen M S,chen Y.Secure and Efficient Handover Schemes for Heterogeneous Networks[C]//IEEE Asia-Pacific Services Computing Conference (APSCC) 2008: 205-210.
|
| [4] |
Hou L M, Miao K X.A pre-authentication architecture in WiFi&WiMAX integrated system.[C]// ChinaCOM ,2009: 1-5.
|
| [5] |
IEEE Standard for Information technology,telecommunications and information exchange between systems,local and metropolitan area networks,specific requirements (IEEE 802.11-2007)[S]. IEEE: 2007.
|
| [6] |
RFC 3748. Extensible Authentication Protocol(EAP)[S]. 2004
|
| [7] |
WONG D S.Security analysis of two anonymous authentication pro-tocols for distributed wireless networks[C]// PerCom 2005 Work-shops. Kauai Island, Hawaii, 2005.
|
| [8] |
IEEE Standard for Informationtechnology, Telecommunications and information exchange between systems, Local and metropolitan area networks, Specific requirements Part 11(IEEE802.11-2007)[S]. IEEE: 2007.
|
| [9] |
Stoicay I, Morrisz R, Liben -Nowellz D, et al.Chord: A scalablepeer-to-peer lookup protocol for Internet applications[J].IEEE/ACM Transactions on Networking, 2003, 11(1 ) : 17-32.
|
| [10] |
IEEE Standard for local and metorpolition area networks Part 16(IEEE 802.16e-2006)[S] . IEEE: 2007.
|
| [11] |
Xiang yu J.The security routing research for WSN in the applica-tion of intelligent transport system[C]//Mechatronics and Automation, Proceedings of the 2006 IEEE International Conference,2006:2318-2323.
|
| [12] |
Waldburger M, Stiller B.Toward the mobile grid:Service provi-sioning in a mobile dvnamic virtual organization[C]//4th ACS/IEEE Int Conf on Computer Systems and Applications(ALCCSA-06),Dubai/Sharjah,March 2006:579-583.
|
| [13] |
Wood D,Jobn A.Denial of service in sensor networks[J].IEEE Computer,2002.35(10):54-62.
|
 ), SONG Yi-zan1
), SONG Yi-zan1