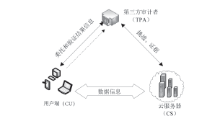
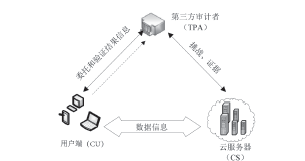
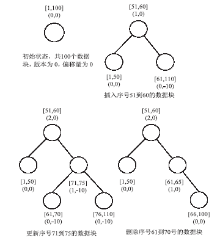
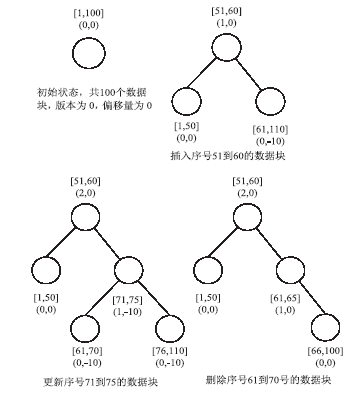
| [1] |
DESWARTE Y, QUISQUATER J J, SAÏDANE A. Remote Integrity Checking[C]//IFIP. Sixth Working Conference on Integrity and Internal Control in Information Systems (IICIS), November 13-14, 2003, Lausanne, Switzerland. US: Springer, 2003: 1-11.
|
| [2] |
OPREA A, REITER M K, YANG K.Space-Efficient Block Storage Integrity[C]//Internet Society. Network and Distributed System Security Symposium, NDSS 2005, February 3-4, 2005, California, USA. USA: NDSS, 2005: 1-12.
|
| [3] |
FILHO D L G, BARRETO P S L M. Demonstrating Data Possession and Uncheatable Data Transfer[EB/OL]. .
|
| [4] |
SEBE F, MARTINEZ-BALLESTE A, DESWARTE Y, et al.Time-bounded Remote File Integrity Checking[R]. Tarragona: UNIVERSITAT ROVIRA I VIRGILI, Tech.Rep.04429, 2004.
|
| [5] |
SCHWARZ T S J, MILLER E L. Store, Forget, and Check: Using Algebraic Signatures to Check Remotely Administered Storage[C]//IEEE. Distributed Computing Systems, ICDCS 2006, 26th IEEE International Conference on, July 4-7, 2006, Lisboa. Washington, USA: IEEE, 2006: 12.
|
| [6] |
ATENIESE G, BURNS R, CURTMOLA R, et al.Provable Data Possession at Untrusted Stores[C]//ACM. 14th ACM Conference on Computer and Communications Security, October 28-31, 2007, Alexandria, Virginia, USA. New York: ACM, 2007: 598-609.
|
| [7] |
ATENIESE G, KAMARA S, KATZ J.Proofs of Storage from Homomorphic Identification Protocols[C]//INTERNATIONAL ASSOCIATION FOR CRYPTOLOGIC RESEARCH. Advances in Cryptology-ASIACRYPT 2009, December 6-10, 2009, Tokyo, Japan. Heidelberg: Springer, 2009: 319-333.
|
| [8] |
JUELS A, KALISKI JR B S. PORs: Proofs of Retrievability for Large Files[C]//ACM. 14th ACM Conference on Computer and Communications Security, October 29-November 2, 2007, Alexandria, Viginia, USA. New York: ACM, 2007: 584-597.
|
| [9] |
ATENIESE G, PIETRO R D, MANCINI L V, et al.Scalable and Efficient Provable Data Possession[C]// IACR. 4th International Conference on Security and Privacy in Communication Networks, September 22-25, 2008, Istanbul, Turkey. New York: ACM, 2008: 9.
|
| [10] |
ERWAY C, KÜPÇÜ A, PAPAMANTHOU C, et al. Dynamic Provable Data Possession[C]//ACM. 16th ACM Conference on Computer and Communications Security, November 9-13, 2009, Chicago. New York: ACM, 2009: 213-222.
|
| [11] |
WANG Qian, WANG Cong, LI Jin, et al.Enabling Public Verifiability and Data Dynamics for Storage Security in Cloud Computing[C]//Information Security Group. 14th European Symposium on Research in Computer Security, September 21-23, 2009, Saint-Malo. Heidelberg: Springer, 2009: 355-370.
|
| [12] |
WANG Cong, WANG Qian, REN Kui, et al.Privacy-preserving Public Auditing for Data Storage Security in Cloud Computing[C]//IEEE. 29th IEEE International Conference on Computer Communications, March 14-19, 2010, San Diego. USA: IEEE, 2010: 1-9.
|
| [13] |
ZHU Yan, WANG Huaixi, HU Zexing, et al.Dynamic Audit Services for Integrity Verification of Outsourced Storages in Clouds[C]//ACM. 2011 ACM Symposium on Applied Computing, March 21-24, 2011, Taiwan. New York: ACM, 2011: 1550-1557.
|
| [14] |
YANG Kan, JIA Xiaohua.An Efficient and Secure Dynamic Auditing Protocol for Data Storage in Cloud Computing[J]. Parallel and Distributed Systems, IEEE Transactions on, 2013, 24(9): 1717-1726.
|
| [15] |
MALKANI P, ELLARD D, LEDLIE J, et al.Passive NFS Tracing of Email and Research Workloads[C]//USENIX. 2nd USENIX Conference on File and Storage Technologies, March 31-April 2, 2003, San Francisco. Berkeley: USENIX, 2003: 203-216.
|
| [16] |
秦志光,包文意,赵洋,等. 云存储中一种模糊关键字搜索加密方案[J]. 信息网络安全,2015(6):7-12.
|
| [17] |
BOWERS K D, JUELS A, OPREA A.Proofs of Retrievability: Theory and Implementation[C]// ACM. 2009 ACM Workshop on Cloud Computing Security, November 13, 2009, Chicago. New York: ACM, 2009: 43-54.
|
| [18] |
唐春明,郑晓龙. 云计算中一种对大群组用户的隐私保护公共审计方案[J]. 信息网络安全,2015(2):19-25.
|
| [19] |
CHANG E C, XU Jia.Remote Integrity Check with Dishonest Storage Server[C]//Information Security Group. 13th European Symposium on Research in Computer Security, October 6-8, 2008, Málaga, Spain. Lodon: Information Security Group, 2008: 223-237.
|
| [20] |
秦志光,吴世坤,熊虎. 云存储服务中数据完整性审计方案综述[J]. 信息网络安全,2014(7):1-6.
|
| [21] |
BOWERS K D, JUELS A, OPREA A.HAIL: A High-availability and Integrity Layer for Cloud Storage[C]//ACM. 16th ACM Conference on Computer and Communications Security,November 9-13, 2009, Chicago. New York: ACM, 2009: 187-198.
|
| [22] |
BONEH D, LYNN B, SHACHAM H.Short Signatures from the Weil Pairing[J]. Journal of Cryptology, 2004, 17(4): 297-319.
|
 ), XIONG Hu, CHEN Yang
), XIONG Hu, CHEN Yang