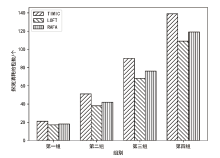
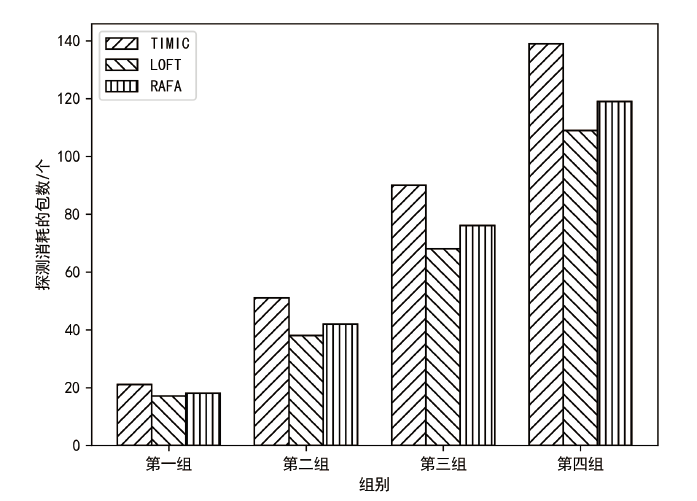
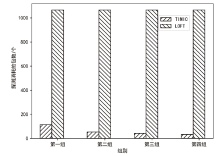
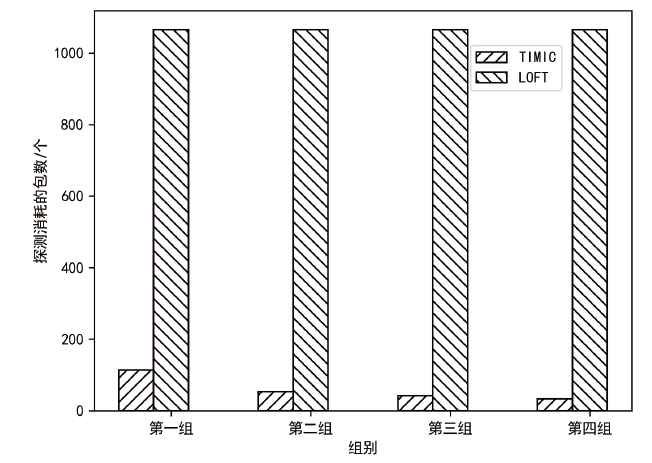
| [1] |
CUI Yunhe, QIAN Qing, GUO Chun, et al. Towards DDoS Detection Mechanisms in Software-Defined Networking[EB/OL]. (2021-07-10)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1084804521001703?via%3Dihub.
|
| [2] |
YAO Xianxian, XIA Hongbin, LIU Yuan. Detection and Mitigation of DDoS Based on Attention Mechanism in SDN Environment[EB/OL]. (2024-05-31)[2024-09-10]. https://kns.cnki.net/kcms/detail/21.1106.TP.20240530.1039.008.html.
|
|
姚纤纤, 夏鸿斌, 刘渊. SDN环境中基于注意力机制的DDoS检测和缓解[EB/OL]. (2024-05-31)[2024-09-10]. https://kns.cnki.net/kcms/detail/21.1106.TP.20240530.1039.008.html.
|
| [3] |
LEI Yuxia. Research on DDoS Anomaly Attack Detection Technology Based on SDN Architecture[J]. Shanxi Electronic Technology, 2024(3): 120-123.
|
|
雷宇霞. 基于SDN架构的DDoS异常攻击检测技术研究[J]. 山西电子技术, 2024(3): 120-123.
|
| [4] |
ZHANG Junrong. Analysis of Software Defined Network (SDN) Technology[J]. Digital Communication World, 2024(6): 115-117.
|
|
张俊茸. 软件定义网络(SDN)技术分析[J]. 数字通信世界, 2024(6): 115-117.
|
| [5] |
WANG Dongbin, WU Dongzhe, ZHI Hui, et al. Preventing Flow Table Overflow against Denial of Service Attack in Software Defined Network[J]. Journal on Communications, 2023, 44(2): 1-11
doi: 10.11959/j.issn.1000-436x.2023036
|
|
王东滨, 吴东哲, 智慧, 等. 软件定义网络抗拒绝服务攻击的流表溢出防护[J]. 通信学报, 2023, 44(2): 1-11.
doi: 10.11959/j.issn.1000-436x.2023036
|
| [6] |
RAN Longyan, CUI Yunhe, GUO Chun, et al. Defending Saturation Attacks on SDN Controller: A Confusable Instance Analysis-Based Algorithm[EB/OL]. (2022-06-17)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1389128622002298?via%3Dihub.
|
| [7] |
LI Jishuai, TU Tengfei, LI Yongsheng, et al. DoSGuard: Mitigating Denial-of-Service Attacks in Software-Defined Networks[EB/OL]. (2021-01-29)[2024-09-10]. https://pubmed.ncbi.nlm.nih.gov/35161800/.
|
| [8] |
CONTI M, GANGWAL A, GAUR M S. A Comprehensive and Effective Mechanism for DDoS Detection in SDN[C]// IEEE. 2017 IEEE 13th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob). New York: IEEE, 2017: 1-8.
|
| [9] |
WANG Zhi, ZHANG Hao, GU Jianjun. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN[J]. Netinfo Security, 2023, 23(10): 1-7.
|
|
王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7.
|
| [10] |
XU Jianfeng, ZHANG Fangtao, XU Zhen, et al. Field Manipulation Attacks Based on Sniffing Techniques[J]. Journal of Electronics & Information Technology, 2020, 42(10): 2342-2349.
|
|
徐建峰, 张方韬, 徐震, 等. 基于嗅探技术的字段操纵攻击研究[J]. 电子与信息学报, 2020, 42(10): 2342-2349.
|
| [11] |
PATWARDHAN A, JAYARAMA D, LIMAYE N, et al. SDN Security: Information Disclosure and Flow Table Overflow Attacks[C]// IEEE. 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6.
|
| [12] |
YIĞIT B, GÜR G, ALAGÖZ F, et al. Network Fingerprinting via Timing Attacks and Defense in Software Defined Networks[EB/OL]. (2023-06-02)[2024-09-10]. https://www.sciencedirect.com/science/article/abs/pii/S1389128623002955?via%3Dihub.
|
| [13] |
CAO Jiahao, XU Mingwei, LI Qi, et al. The LOFT Attack: Overflowing SDN Flow Tables at a Low Rate[J]. IEEE/ACM Transactions on Networking, 2023, 31(3): 1416-1431.
|
| [14] |
CHEN Xingshu, HUA Qiang, WANG Yitong, et al. Research on Low-Rate DDoS Attack of SDN Network in Cloud Environment[J]. Journal on Communications, 2019, 40(6): 210-222.
doi: 10.11959/j.issn.1000-436x.2019120
|
|
陈兴蜀, 滑强, 王毅桐, 等. 云环境下SDN网络低速率DDoS攻击的研究[J]. 通信学报, 2019, 40(6): 210-222.
doi: 10.11959/j.issn.1000-436x.2019120
|
| [15] |
AZZOUNI A, BRAHAM O, TRANG N T M, et al. Fingerprinting OpenFlow Controllers: The First Step to Attack an SDN Control Plane[C]// IEEE. 2016 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2016: 1-6.
|
| [16] |
LENG Junyuan, ZHOU Yadong, ZHANG Junjie, et al. An Inference Attack Model for Flow Table Capacity and Usage: Exploiting the Vulnerability of Flow Table Overflow in Software-Defined Network[EB/OL]. (2015-04-13)[2024-09-10]. https://arxiv.org/abs/1504.03095v1.
|
| [17] |
BENSON T, AKELLA A, MALTZ D A, et al. Network Traffic Characteristics of Data Centers in the Wild[C]// ACM. Proceedings of the 10th ACM SIGCOMM Conference on Internet Measurement. New York: ACM, 2010: 267-280.
|
 ), CHEN Yi1,2,3,4, GUO Chun1,2,3,4
), CHEN Yi1,2,3,4, GUO Chun1,2,3,4