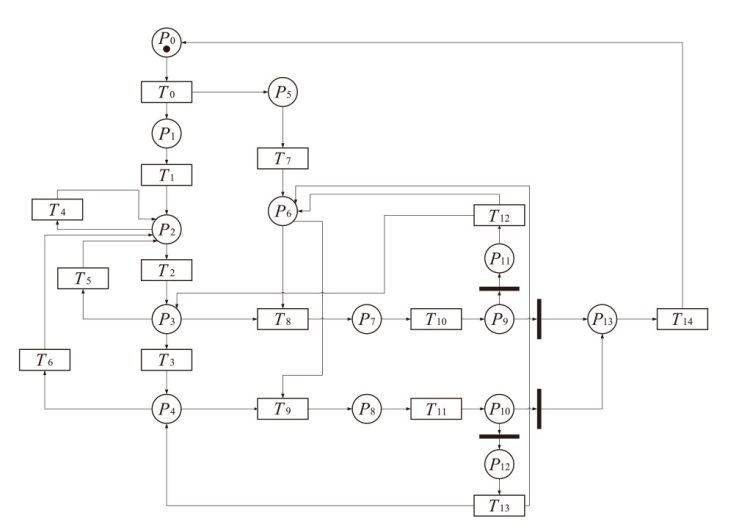
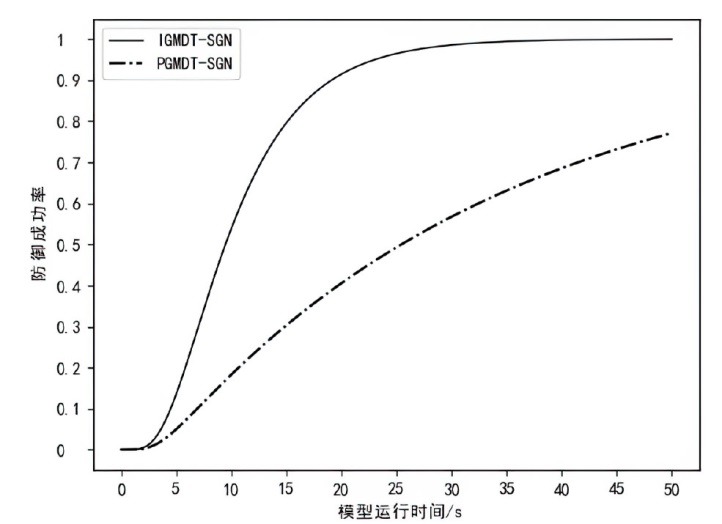
| [1] |
WOODHAMS S. Spyware: An Unregulated and Escalating Threat to Independent Media[M]. Washington: Center for International Media Assistance, 2021.
|
| [2] |
MARCZAK B, SCOTT-RAILTON J, BERDAN K, et al. Hooking Candiru: Another Mercenary Spyware Vendor Comes into Focus[R]. Toronto: University of Toronto, Citizen Lab Research Report No. 139, 2021.
|
| [3] |
MALWAREBYTE. 2022 Threat Review[EB/OL]. (2023-01-28)[2024-04-23]. https://www.malwarebytes.com/wp-content/uploads/sites/2/2023/08/mwb_threatreview_2022_ss_v1.pdf.
|
| [4] |
ALSMADI T, ALQUDAH N. A Survey on Malware Detection Techniques[C]// IEEE. 2021 International Conference on Information Technology (ICIT). New York: IEEE, 2021: 371-376.
|
| [5] |
MANIRIHO P, MAHMOOD A N, CHOWDHURY M J M. A Study on Malicious Software Behaviour Analysis and Detection Techniques: Taxonomy, Current Trends and Challenges[J]. Future Generation Computer Systems, 2022, 130: 1-18.
|
| [6] |
MAO Ting, CHE Shengbing, DENG Wei. Research on the Hidden Technology of Troy Trojan-Horse[C]// Atlantis Press. 2017 2nd International Conference on Modelling, Simulation and Applied Mathematics (MSAM2017). Paris: Atlantis Press, 2017: 304-307.
|
| [7] |
YANG Runqing, CHEN Xutong, XU Haitao, et al. RATScope: Recording and Reconstructing Missing RAT Semantic Behaviors for Forensic Analysis on Windows[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(3): 1621-1638.
|
| [8] |
JAVAHERI D, HOSSEINZADEH M, RAHMANI A M. Detection and Elimination of Spyware and Ransomware by Intercepting Kernel-Level System Routines[J]. IEEE Access, 2018, 6: 78321-78332.
|
| [9] |
LYSENKO S, BOBROVNIKOVA K, POPOV P T, et al. Spyware Detection Technique Based on Reinforcement Learning[C]// RWTH Aachen University. CEUR Workshop Proceedings. Aachen: RWTH Aachen University. 2020: 307-316.
|
| [10] |
HU Guangjun, ZHU Ping. Research on Trojan Detection Strategy Based on Dynamic Game[C]// China Computer Federation Computer Security Professional Committee. Proceedings of the National Computer Security Academic Exchange Conference (Volume 24). China University of Science and Technology Press, 2009: 357-360.
|
|
胡光俊, 朱平. 基于动态博弈的木马检测策略研究[C]// 中国计算机学会计算机安全专业委员会.全国计算机安全学术交流会论文集(第二十四卷).中国科学技术大学出版社, 2009: 357-360.
|
| [11] |
GAO He, WANG Yuanzhuo, WANG Li, et al. Trojan Characteristics Analysis Based on Stochastic Petri Nets[C]// IEEE. Proceedings of 2011 IEEE International Conference on Intelligence and Security Informatics. New York: IEEE, 2011: 213-215.
|
| [12] |
FAN Lejun, WANG Yuanzhuo, CHENG Xueqi, et al. Privacy Theft Malware Multi-Process Collaboration Analysis[J]. Security and Communication Networks, 2015, 8(1): 51-67.
|
| [13] |
YU Min, LIU Chao, QIU Xinliang, et al. Modeling and Analysis of Information Theft Trojan Based on Stochastic Game Nets[C]// IEEE. 2015 2nd International Conference on Information Science and Control Engineering. New York: IEEE, 2015: 318-322.
|
| [14] |
YAN Qing, SONG Lipeng. Modelling and Control of Trojan Propagation via Online Game Accelerators[J]. Mathematical Problems in Engineering, 2021, 2021(10): 1-10.
|
| [15] |
PENG Jiaxin, GUO Chun, PING Yuan, et al. SNDMI: Spyware Network Traffic Detection Method Based on Inducement Operations[EB/OL]. (2024-03-13)[2024-04-23]. https://www.sciencedirect.com/science/article/abs/pii/S016740482400107X?via%3Dihub.
|
| [16] |
MI Yan, ZHANG Hengwei, HU Hao, et al. Optimal Network Defense Strategy Selection Method: A Stochastic Differential Game Model[EB/OL]. (2021-08-24)[2024-04-23]. https://www.xueshufan.com/publication/3195737479.
|
| [17] |
WANG Yuanzhuo, LIN Chuang, CHENG Xueqi, et al. Analysis for Network Attack-Defense Based on Stochastic Game Model[J]. Chinese Journal of Computers, 2010, 33(9): 1748-1762.
|
|
王元卓, 林闯, 程学旗, 等. 基于随机博弈模型的网络攻防量化分析方法[J]. 计算机学报, 2010, 33(9): 1748-1762.
|
| [18] |
NOURREDINE O, MENOUAR B, CAMPO E, et al. A New Generalized Stochastic Petri Net Modeling for Energy-Harvesting-Wireless Sensor Network Assessment[J]. International Journal of Communication Systems, 2023, 36(11): 1-25.
|
| [19] |
LIU Shuanglei, LI Weijun, GAO Peng, et al. Modeling and Performance Analysis of Gas Leakage Emergency Disposal Process in Gas Transmission Station Based on Stochastic Petri Nets[EB/OL]. (2022-07-02)[2024-04-23]. https://www.sciencedirect.com/science/article/abs/pii/S0951832022003337?via%3Dihub.
|
| [20] |
WU Zenan, TIAN Liqin, CHEN Nan. Research on Quantitative Analysis of System Security Based on Stochastic Petri Net[J]. Netinfo Security, 2020, 20(9): 27-31.
|
|
毋泽南, 田立勤, 陈楠. 基于随机Petri网的系统安全性量化分析研究[J]. 信息网络安全, 2020, 20(9): 27-31.
|
| [21] |
HO E, RAJAGOPALAN A, SKVORTSOV A, et al. Game Theory in Defence Applications: A Review[EB/OL]. (2022-01-28)[2024-04-23]. tps://www.xueshufan.com/publication/3210652180.
|
| [22] |
ZIMMERMANN A. Modeling and Evaluation of Stochastic Petri Nets with TimeNET 4.1[C]// IEEE. Proceedings of the 6th International Conference on Performance Evaluation Methodologies and Tools. New York: IEEE, 2012: 54-63.
|
| [23] |
ZIMMERMANN A. Modelling and Performance Evaluation with TimeNET 4.4[C]// Springer. International Conference on Quantitative Evaluation of Systems. Heidelberg: Springer, 2017: 300-303.
|
| [24] |
SUN Xiaoyun, YU Zhenhua, GAO Hongxia, et al. Trustworthiness Analysis and Evaluation for Command and Control Cyber-Physical Systems Using Generalized Stochastic Petri Nets[EB/OL]. (2023-04-23)[2024-04-23]. https://www.sciencedirect.com/science/article/abs/pii/S002002552300511X?via%3Dihub#preview-section-cited-by.
|
| [25] |
CHEN Xiaohui, HAO Zhiyu, LI Lun, et al. CruParamer: Learning on Parameter-Augmented API Sequences for Malware Detection[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 788-803.
|
| [26] |
LI Ce, LYU Qiujian, LI Ning, et al. A Novel Deep Framework for Dynamic Malware Detection Based on API Sequence Intrinsic Features[EB/OL]. (2022-03-08)[2024-04-23]. https://www.sciencedirect.com/science/article/abs/pii/S0167404822000840.
|
 ), CUI Yunhe1,2, LI Xianchao1
), CUI Yunhe1,2, LI Xianchao1