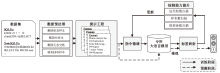
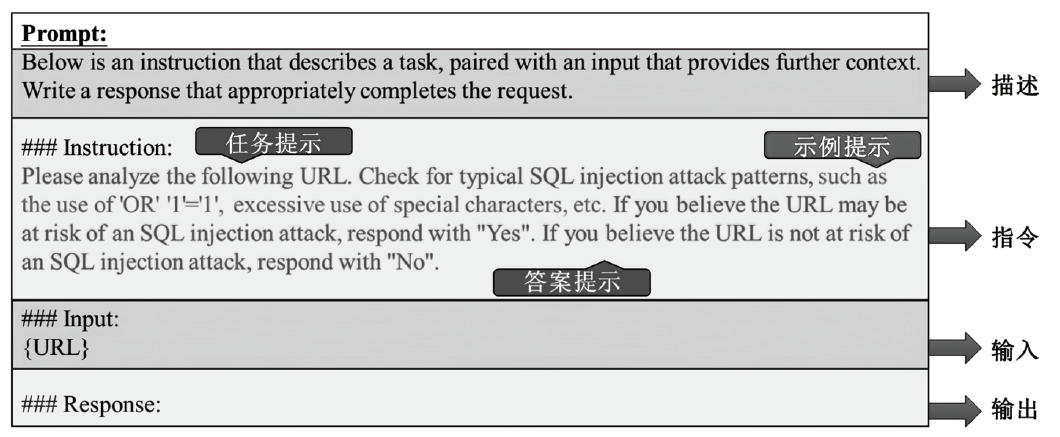
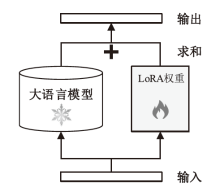
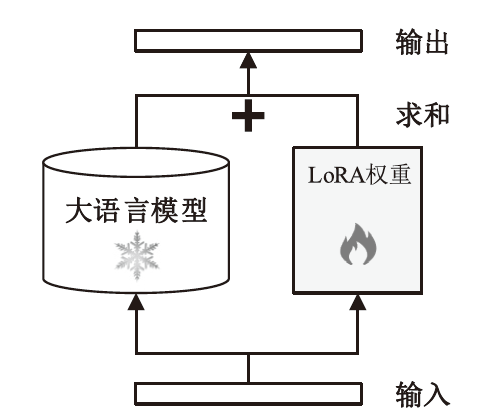
Netinfo Security ›› 2023, Vol. 23 ›› Issue (11): 84-93.doi: 10.3969/j.issn.1671-1122.2023.11.009
Previous Articles Next Articles
A Large Language Model Based SQL Injection Attack Detection Method
HUANG Kaijie, WANG Jian( ), CHEN Jiongyi
), CHEN Jiongyi
- College of Electronic Science and Technology, National University of Defense Technology, Changsha 410073, China
-
Received:2023-08-25Online:2023-11-10Published:2023-11-10
CLC Number:
Cite this article
HUANG Kaijie, WANG Jian, CHEN Jiongyi. A Large Language Model Based SQL Injection Attack Detection Method[J]. Netinfo Security, 2023, 23(11): 84-93.
share this article
| [1] |
LU Dongzhe, FEI Jinlong, LIU Long. A Semantic Learning-Based SQL Injection Attack Detection Technology[J]. Electronics, 2023, 12: 1344-1356.
doi: 10.3390/electronics12061344 URL |
| [2] | CLARKE J, FOWLER K, OFTEDAL E, et al. SQL Injection Attacks and Defense[M]. Ohio: Syngress, 2009. |
| [3] | OWASP. OWASP Top Ten[EB/OL]. (2023-05-25)[2023-08-12]. https://owasp.org/Top10/. |
| [4] | UWAGBOLE S O, BUCHANAN W J, FAN Lu. An Applied Pattern-Driven Corpus to Predictive Analytics in Mitigating SQL Injection Attack[C]// IEEE. Proceedings of the 2017 Seventh International Conference on Emerging Security Technologies (EST). New York: IEEE, 2017: 12-17. |
| [5] | UWAGBOLE S O, BUCHANAN W J, FAN Lu. Applied Machine Learning Predictive Analytics to SQL Injection Attack Detection and Prevention[C]// IEEE. Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM). New York: IEEE, 2017: 1087-1090. |
| [6] |
GU Haifeng, ZHANG Jianning, LIU Tian, et al. DIAVA: A Traffic-Based Framework for Detection of SQL Injection Attacks and Vulnerability Analysis of Leaked Data[J]. IEEE Transactions on Reliability, 2020, 69(1): 188-202.
doi: 10.1109/TR.24 URL |
| [7] | LIVSHITS V B, LAM M S. Finding Security Vulnerabilities in Java Applications with Static Analysis[C]// USENIX. Proceedings of the 14th Conference on USENIX Security Symposium. New York: USENIX Association, 2005: 18-29. |
| [8] |
PROKHORENKO V, CHOO K-K R, ASHMAN H. Web Application Protection Techniques: A Taxonomy[J]. Journal of Network and Computer Applications, 2016, 60: 95-112.
doi: 10.1016/j.jnca.2015.11.017 URL |
| [9] | HASAN M, BALBAHAITH Z, TARIQUE M. Detection of SQL Injection Attacks: A Machine Learning Approach[C]// IEEE. Proceedings of the 2019 International Conference on Electrical and Computing Technologies and Applications (ICECTA). New York: IEEE, 2019: 1-6. |
| [10] | LI Hongling, ZOU Jianxin. Research of SQL Injection Detection Based on SVM and Text Feature Extraction[J]. Netinfo Security, 2017, 17(12): 40-46. |
| 李红灵, 邹建鑫. 基于SVM和文本特征向量提取的SQL注入检测研究[J]. 信息网络安全, 2017, 17(12): 40-46. | |
| [11] | FAROOQ U. Ensemble Machine Learning Approaches for Detection of SQL Injection Attack[J]. Tehnicki Glasnik, 2021, 15(1): 112-120. |
| [12] |
GOWTHAM M, PRAMOD H B. Semantic Query-Featured Ensemble Learning Model for SQL-Injection Attack Detection in IoT-Ecosystems[J]. IEEE Transactions on Reliability, 2022, 71(2): 1057-1074.
doi: 10.1109/TR.2021.3124331 URL |
| [13] | TANG Peng, QIU Weidong, HUANG Zheng, et al. Detection of SQL Injection Based on Artificial Neural Network[J]. Knowledge-Based Systems, 2020, 190: 1-12. |
| [14] | BROWN T B, MANN B, RYDER N, et al. Language Models are Few-Shot Learners[EB/OL]. (2020-05-01)[2023-08-12]. https://ui.adsabs.harvard.edu/abs/2020arXiv200514165B. |
| [15] | RADFORD A, WU J, CHILD R, et al. Language Models are Unsupervised Multitask Learners[EB/OL]. (2019-02-27)[2023-08-12]. https://cdn.openai.com/better-language-models/language_models_are_unsupervised_multitask_learners.pdf. |
| [16] | JIAO Wenxiang, WANG Wenxuan, HUANG J, et al. Is ChatGPT a Good Translator? Yes with GPT-4 as The Engine[EB/OL]. (2023-05-19)[2023-08-12]. https://arxiv.org/pdf/2301.08745.pdf. |
| [17] | SANTIAGO E. AI in Content Creation: How Creators and Marketers are Using It Data[EB/OL]. (2023-04-17)[2023-08-12]. https://blog.hubspot.com/marketing/ai-in-content-marketing. |
| [18] | KEARY T. 12 Practical Large Language Model (LLM) Applications[EB/OL]. (2023-07-14)[2023-08-12]. https://www.techopedia.com/12-practical-large-language-model-llm-applications. |
| [19] | LAMB A. A Brief Introduction to Generative Models[EB/OL]. (2021-02-27)[2023-08-12]. https://arxiv.org/abs/2103.00265. |
| [20] | WEI J, BOSMA M, ZHAO V, et al. Finetuned Language Models are Zero-Shot Learners[EB/OL]. (2022-02-08)[2023-08-12]. https://arxiv.org/abs/2109.01652. |
| [21] | SYED S. SQL Injection Dataset[EB/OL]. (2021-09-09)[2023-08-12]. https://www.kaggle.com/datasets/syedsaqlainhussain/sql-injection-dataset. |
| [22] | ZHANG Wei, LI Yueqin, LI Xiaofeng, et al. Deep Neural Network-Based SQL Injection Detection Method[J]. Security and Communication Networks, 2022, 22: 1-9. |
| [23] | ROY P, KUMAR R, RANI P. SQL Injection Attack Detection by Machine Learning Classifier[C]// IEEE. Proceedings of the 2022 International Conference on Applied Artificial Intelligence and Computing (ICAAIC). New York: IEEE, 2022: 394-400. |
| [24] | OpenAI. Completion-OpenAI API[EB/OL]. [2023-08-12]. https://beta.openai.com/docs/guides/completion/prompt-design. |
| [25] | TAORI R, GULRAJANI I, ISHAAN G, et al. Stanford Alpaca: An Instruction-Following LLaMA Model[EB/OL]. (2023-05-30)[2023-08-12]. https://github.com/tatsu-lab/stanford_alpaca. |
| [26] | CHEN M, TWOEK J, JUN H, et al. Evaluating Large Language Models Trained on Code[EB/OL]. (2021-07-14)[2023-08-12]. https://arxiv.org/abs/2107.03374. |
| [27] | HU E J, SHEN Yelong, WALLIS P, et al. LoRA: Low-Rank Adaptation of Large Language Models[EB/OL]. (2021-06-17)[2023-08-12]. https://arxiv.org/abs/2106.09685. |
| [28] | NEIL H, ANDREI G, STANISLAW J, et al. Parameter-Efficient Transfer Learning for NLP[EB/OL]. (2019-06-13)[2023-08-12]. https://arxiv.org/pdf/1902.00751.pdf. |
| [29] | XIANG L L, PERCY L. Prefix-Tuning: Optimizing Continuous Prompts for Generation[EB/OL]. (2021-01-01)[2023-08-12]. https://browse.arxiv.org/pdf/2101.00190.pdf. |
| [30] | PEARCE H A, TAN B, AHMAD B, et al. Examining Zero-Shot Vulnerability Repair with Large Language Models[C]// IEEE. 44th IEEE Symposium on Security and Privacy. New York: IEEE, 2023: 2339-2356. |
| [31] | GRORGI G. Llama. cpp.[2023-08-12]. https://github.com/ggerganov/llama.cpp. |
| [32] | CARLOS M, ADRIAN W, LUCA A, et al. Lightning-AI/lit-llama: Implementation of the LLaMA Language Model Based on NanoGPT[EB/OL]. (2023-07-19)[2023-08-12]. https://github.com/Lightning-AI/lit-llama. |
| [33] | RAFFEL C, SHAZEER N, ROBERTS A, et al. Exploring the Limits of Transfer Learning with a Unified Text-to-Text Transformer[J]. Juornal of Machine Learning Research, 2020, 21(1): 1-53. |
| [34] | HUGO T, THUBAUT L, GATIER I, et al. LLaMA: Open and Efficient Foundation Language Models[EB/OL]. (2023-02-27)[2023-08-12]. https://arxiv.org/pdf/2302.13971.pdf. |
| [35] |
LI Qi, LI Weishi, WANG Junfeng, et al. A SQL Injection Detection Method Based on Adaptive Deep Forest[J]. IEEE Access, 2019, 7: 145385-145394.
doi: 10.1109/ACCESS.2019.2944951 |
| [36] | GUO Chun, CAI Wenyan, SHEN Guowei, et al. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload[J]. Netinfo Security, 2021, 21(7): 43-53. |
| 郭春, 蔡文艳, 申国伟, 等. 基于关键载荷截取的SQL注入攻击检测方法[J]. 信息网络安全, 2021, 21(7): 43-53. |
| [1] | ZHANG Dongxin, LANG Bo, YAN Hanbing. Attack Detection Method Based on Flow Behavior Graph [J]. Netinfo Security, 2022, 22(1): 72-79. |
| [2] | Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [3] | ZHANG Xuebo, LIU Jinghao, FU Xiaomei. Design and Implementation of Anti Web DDoS Attack Model Based on Improved Logistic Regression Algorithm [J]. 信息网络安全, 2017, 17(6): 62-67. |
| [4] | Yuming XIA, Shaoyong HU, Shaomin ZHU, Lili LIU. Research on the Method of Network Attack Detection Based on Convolution Neural Network [J]. Netinfo Security, 2017, 17(11): 32-36. |
| [5] | Wen-sheng LIU, De-guang LE, Wei LIU. Research on SQL Injection Attack and Defense Technology [J]. Netinfo Security, 2015, 15(9): 129-134. |
| [6] | Yu-jie TIAN, Ze-mao ZHAO, Li-jun WANG, Ke LIAN. Research on Double Layer Defense Model for SQL Injection Attack Based on Classification [J]. Netinfo Security, 2015, 15(6): 1-6. |
| [7] | . The Design and Implementation for the Detection System of the SQL Injection Attack based on the Windows Environment [J]. , 2014, 14(7): 16-. |
| [8] | . Second-order SQL Injection Attack Defense Model [J]. , 2014, 14(11): 70-. |
| [9] | Yu-jie TIAN, Ze-mao ZHAO, Hai-chuan ZHANG, Xue-shuang LI. Second-order SQL Injection Attack Defense Model [J]. Netinfo Security, 2014, 15(11): 70-73. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||