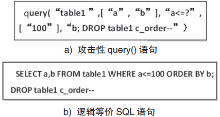
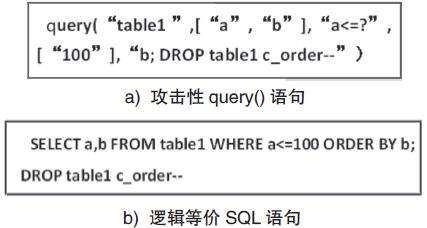
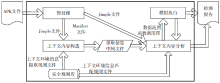
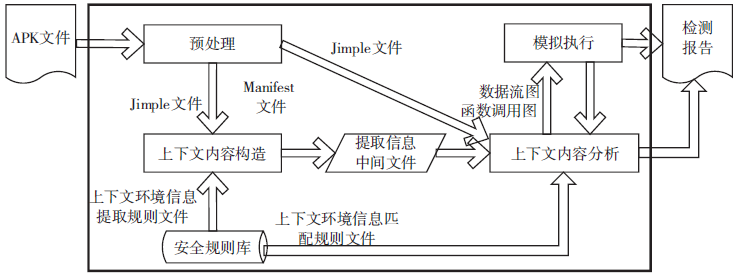
| [1] |
LI Wenyang.Research on Android Malware Detection Technology[J]. Netinfo Security, 2015(9):62-65.
|
|
李汶洋. Android操作系统恶意软件检测技术研究[J]. 信息网络安全, 2015(9):62-65.
|
| [2] |
ZHOU Yajin, JIANG Xuxian. Detecting Passive Content Leaks and Pollution in Android Applications [EB/OL].,2017-11-20.
|
| [3] |
SHAHRIAR H, HADDAD H M, et al.Content Provider Leakage Vulnerability Detection in Android Applications[C]//ACM. Proceedings of the 7th International Conference on Security of Information and Networks, September 9-11, 2014,Glasgow, Scotland, UK. New York: ACM, 2014:359.
|
| [4] |
CHU W, DEHGHAN M, TOWSLEY D, et al.On Allocating Cache Resources to Content Providers[C]// ACM. Proceedings of the 3rd ACM Conference on Information-centric Networking, September 26-28, 2016, Kyoto, Japan. New York:ACM, 2016:154-159.
|
| [5] |
ZHANG Yuan, YANG Min, GU Guofei, et al.Rethinking Permission Enforcement Mechanism on Mobile Systems[J]. IEEE Transactions on Information Forensics & Security, 2017, 11(10):2227-2240.
|
| [6] |
SHAO Xudong, LIU Yang.A Framework Design for Preventing Android from Apps Privilege-escalation Attacks[J]. Netinfo Security, 2015(9): 89-92.
|
|
邵旭东,刘洋. 一个应对Android应用抬权攻击的系统框架设计[J]. 信息网络安全, 2015(9):89-92.
|
| [7] |
ALNABULSI H, ISLAM M R, MAMUN Q.Detecting SQL Injection Attacks Using SNORT IDS[C]// IEEE. The 3rd Asia-Pacific World Congress on Computer Science and Engineering, November 4-5, 2014, Nadi, Fiji. Piscataway: IEEE, 2015:1-7.
|
| [8] |
CUI Zhanqi, WANG Linzhang, LI Xuandong.A Test Method of Target-Guided Hybrid Implementation[J]. Chinese Journal of Computers, 2011,34(6): 953-964.
|
|
崔展齐,王林章,李宣东. 一种目标制导的混合执行测试方法[J]. 计算机学报, 2011,34(6):953-964.
|
| [9] |
BODDEN E. Inter-procedural Data-flow Analysis with IFDS/IDE and Soot[EB/OL].,2017-11-20.
|
| [10] |
LI Yuanling, CHEN Hua, LIU Li.Control Flow Analysis and Graphical Output in Java Program of Soot[J]. Computer Systems Applications, 2009, 18(10): 88-92.
|
|
李远玲, 陈华, 刘丽. Soot的Java程序控制流分析及图形化输出[J]. 计算机系统应用, 2009, 18(10):88-92.
|
| [11] |
WANG Xu.Research on Static Detection Method of Java Program Based on Control Flow Analysis and Data Flow Analysis [D]. Xi'an:Xidian University, 2015.
|
|
王旭. 基于控制流分析和数据流分析的Java程序静态检测方法的研究[D]. 西安:西安电子科技大学, 2015.
|
| [12] |
ZHANG Fan, ZHONG Zhangdui.Detection and Prevention of Mobile Malware Based on the Analysis of Permissions[J]. Netinfo Security, 2015(10): 66-73.
|
|
张帆, 钟章队. 基于权限分析的手机恶意软件检测与防范[J]. 信息网络安全, 2015(10):66-73.
|
| [13] |
ZHAO Yunshan.Research on Static Defect Detection Technology Based on Symbol Analysis[D]. Beijing: Beijing University of Posts and Telecommunications, 2012.
|
|
赵云山. 基于符号分析的静态缺陷检测技术研究[D]. 北京:北京邮电大学, 2012.
|
 ), Yongwen WANG
), Yongwen WANG