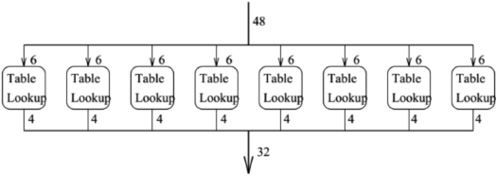
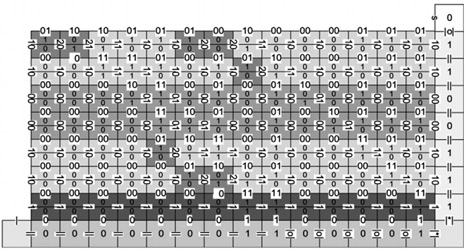
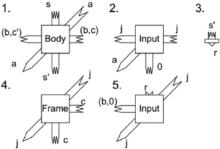
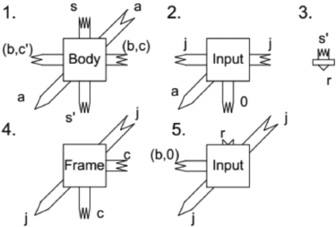
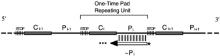
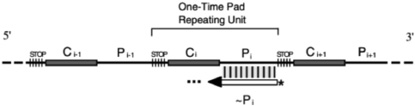
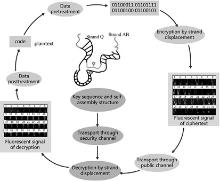
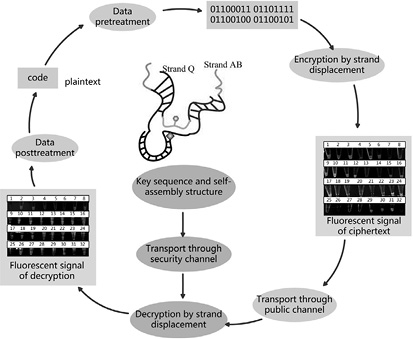
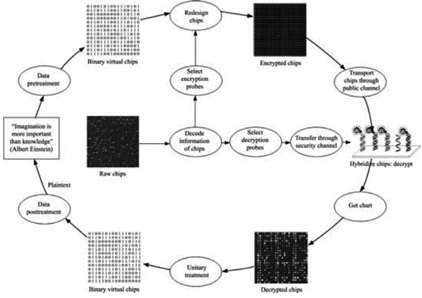
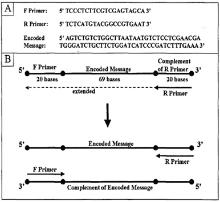
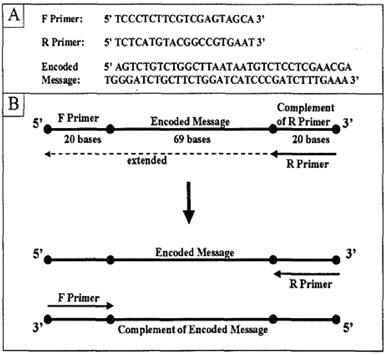
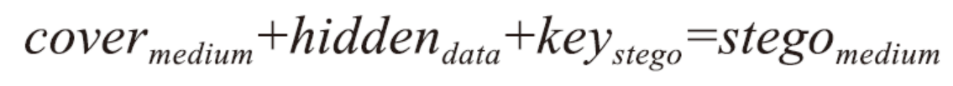| [1] |
Adleman L M.Molecular computation of solutions to combinatorial problems[J]. Science-AAAS-Weekly Paper Edition, 1994, 266(5187): 1021-1023.
|
| [2] |
Mao C, LaBean T H, Reif J H, et al. Logical computation using algorithmic self-assembly of DNA triple-crossover molecules[J]. Nature, 2000, 407(6803): 493-496.
|
| [3] |
Saghatelian A, Völcker N H, Guckian K M, et al.DNA-based photonic logic gates: AND, NAND, and INHIBIT[J]. Journal of the American Chemical Society, 2003, 125(2): 346-347.
|
| [4] |
Yang J, Dong C, Dong Y, et al.Logic nanoparticle beacon triggered by the binding-induced effect of multiple inputs[J]. ACS applied materials & interfaces, 2014, 6(16): 14486-14492.
|
| [5] |
Karl L.DNA computing: arrival of biological mathematics[J]. The mathematical intelligencer, 1997, 19(2): 9-22.
|
| [6] |
Chang W.Fast parallel DNA-based algorithms for molecular computation: the set-partition problem[J]. IEEE Transactions on Nanobioscience, 2007, 6(4): 346.
|
| [7] |
Chang W L, Guo M, Ho M S H. Fast parallel molecular algorithms for DNA-based computation: factoring integers[J]. NanoBioscience, IEEE Transactions on, 2005, 4(2): 149-163.
|
| [8] |
Elbaz J, Lioubashevski O, Wang F, et al.DNA computing circuits using libraries of DNAzyme subunits[J]. Nature nanotechnology, 2010, 5(6):417-422.
|
| [9] |
Xiao G, Lu M, Qin L, et al.New field of cryptography: DNA cryptography[J]. Chinese Science Bulletin, 2006, 51(12): 1413-1420.
|
| [10] |
Dan Boneh, Christopher Dunworth, Lipton R J.Breaking DES Using a Molecular Computer[J]. DNA based computers, 1996, (27): 37.
|
| [11] |
Pelletier O, Weimerskirch A.Algorithmic Self-assembly Of DNA Tiles And Its Application To Cryptanalysis [C]//Proceedings of the Genetic and Evolutionary Computation Conference. Morgan Kaufmann Publishers Inc., 2002: 139-146.
|
| [12] |
Singh H, Chugh K, Dhaka H, et al.DNA based Cryptography: an Approach to Secure Mobile Networks[J]. DNA, 2010, 1 (19):77-80.
|
| [13] |
Wang X, Zhang Q. DNA computing-based cryptography[C]//Bio-Inspired Computing, 2009. BIC-TA'09. Fourth International Conference on. IEEE, 2009: 1-3.
|
| [14] |
Adleman L M, Rothemund P W K, Roweis S, et al. On applying molecular computation to the data encryption standard[J]. Journal of Computational Biology, 1999, 6(1): 53-63.
|
| [15] |
Beaver D.Factoring: the DNA solution[C]//Advances in Cryptology—ASIACRYPT'94. Berlin,Heidelberg:Springer ,1995: 419-423.
|
| [16] |
Brun Y.Arithmetic computation in the tile assembly model: Addition and multiplication[J]. Theoretical Computer Science, 2007, 378(1): 17-31.
|
| [17] |
Brun Y.Nondeterministic polynomial time factoring in the tile assembly model[J]. Theoretical Computer Science, 2008, 395(1): 3-23.
|
| [18] |
张勋才,牛莹,崔光照,等. 基于自组装DNA计算的NTRU密码系统破译方案[J].计算机学报, 2009, 31(12): 2129-2137.
|
| [19] |
Gehani A, LaBean T, Reif J. DNA-based cryptography[C]//Aspects of Molecular Computing. Berlin,Heidelberg:Springer, 2004: 167-188.
|
| [20] |
Yang J, Ma J, Liu S, et al.A molecular cryptography model based on structures of DNA self-assembly[J]. Chinese Science Bulletin, 2014, 59(11): 1192-1198.
|
| [21] |
Lu M X, Lai X J, Xiao G Z, et al.Symmetric-key cryptosystem with DNA technology[J]. Science in China Series F: Information Sciences, 2007, 50(3): 324-333.
|
| [22] |
Risca V I.DNA-based steganography[J]. Cryptologia, 2001, 25(1): 37-49.
|
| [23] |
Leier A, Richter C, Banzhaf W, et al.Cryptography with DNA binary strands[J]. BioSystems, 2000, 57(1): 13-22.
|
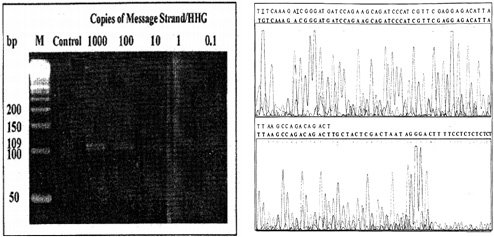
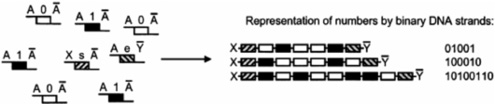
 ), ZHANG Cheng2
), ZHANG Cheng2