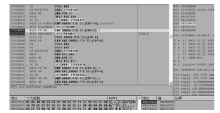
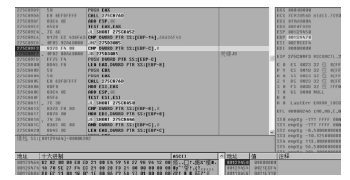
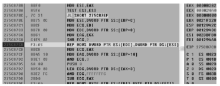
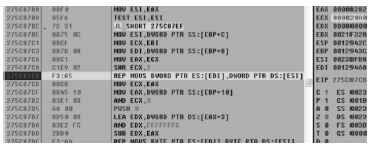
| [1] |
CNCERT. CNCERT Annual Report 2010 [EB/OL]. .
|
| [2] |
Ben Nagy.Generic Anti Exploitation Technology for Windows[C]// Proceedings of the eEye Digital Security White Paper, 2011.
|
| [3] |
Haroon Meer.The Complete History of Memory Corruption Attacks[C]// Thinkst applied research of BlackHat Confidence USA, 2010.
|
| [4] |
David Litchfield. Buffer Underruns, DEP, ASLR and improving the Exploitation Prevention Mechanisms (XPMs) on the Windows platform[R]. Noda City: An NGSSoftware Insight Security Research (NISR) Publication ,curity Software Ltd 2010.
|
| [5] |
Krsul I.Software Vulnerability Analysis [D]. West Lafayette :Purdue University, 1998.
|
| [6] |
Michael Howard, Steve Lipner.The Security Development Lifecycle [M]. Redmond: Microsoft Press, 2006.
|
| [7] |
Oulu University Secure Programming Group. PROTOS Security Testing of Protocol Implementations [EB/OL]. .
|
| [8] |
Aite D. The Advantages of Block-Based Protocol Analysis for Security Testing [EB/OL]. .
|
| [9] |
Wenliang Du, Aditya P.Mathur. Vulnerability Testing of Software System Using Fault Injection [R]. Lafayette: Computer Operations Audit and Security Technology (COAST) Laboratory, 1998.
|
| [10] |
Skape. Improving Software Security Analysis using Exploitation Properties[EB/OL]. .
|
| [11] |
Alpha One. Smashing the Stack for Fun and Profit [EB/OL]. .
|
| [12] |
Dil Dog. The Tao of Windows Buffer Overflow [EB/OL]. .
|
| [13] |
Dark spyrit AKA, Barnaby Jack. Win32 Buffer Over flows (Location, Exploitation and Prevention)[J]. Phrack, 1999,(55):15-19.
|
| [14] |
Matthias Vallentin. On the Evolution of Buffer Overflows [EB/OL]. .
|
| [15] |
Nicolas Waisman. Understanding and Bypassing Windows Heap Protection [EB/OL]. .
|
| [16] |
Adrian Marinescu.Windows Vista Heap Management Enhancements[R]. Las Vegas: Black Hat USA, 2008.
|
| [17] |
Kaempf M. Vudo Malloc Tricks [EB/OL]. .
|
| [18] |
Michael Howard. New NX APIs added to Windows Vista SP1, Windows XP SP3 and Windows Server [EB/OL]. .
|
 ), REN Fu-li, WEN Wei-ping, ZHANG Hao
), REN Fu-li, WEN Wei-ping, ZHANG Hao