Netinfo Security ›› 2014, Vol. 14 ›› Issue (10): 31-37.doi: 10.3969/j.issn.1671-1122.2014.10.006
Previous Articles Next Articles
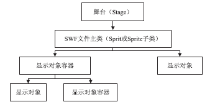
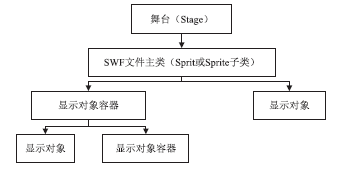
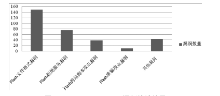
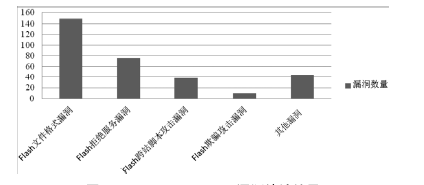
Introduction and Analysis of Adobe Flash Player Vulnerabilities
MENG Zheng, ZENG Tian-ning, MA Yang-yang, WEN Wei-ping
- School of Software&Microelectronics, Peking University, Beijing 102600, China