信息网络安全 ›› 2025, Vol. 25 ›› Issue (4): 509-523.doi: 10.3969/j.issn.1671-1122.2025.04.001
面向智能系统的内部威胁多源日志分析与检测方法
- 1.东南大学网络空间安全学院,南京 214135
2.网络通信与安全紫金山实验室,南京 211111
3.东南大学移动信息通信与安全前沿科学中心,南京 214135
-
收稿日期:2025-02-10出版日期:2025-04-10发布日期:2025-04-25 -
通讯作者:毕悦220225029@seu.edu.cn -
作者简介:李涛(1984—),男,江苏,副教授,博士,主要研究方向为信息系统安全、内生安全|毕悦(2000—),女,重庆,硕士研究生,主要研究方向为数据安全、内部威胁检测|胡爱群(1964—),男,江苏,教授,博士,主要研究方向为网络与信息安全、物理层安全技术 -
基金资助:国家自然科学基金(52233003);中央高校基本科研业务费(2242022k60005)
Insider Threat Multi-Source Log Analysis and Detection Method for Intelligent Systems
LI Tao1,2,3, BI Yue1( ), HU Aiqun1,2,3
), HU Aiqun1,2,3
- 1. School of Cyberspace Security, Southeast University, Nanjing 214135, China
2. Purple Mountain Laboratory of Network Communication and Security, Nanjing 211111, China
3. Frontier Science Centre for Mobile Information Communication and Security, Southeast University, Nanjing 214135, China
-
Received:2025-02-10Online:2025-04-10Published:2025-04-25
摘要:
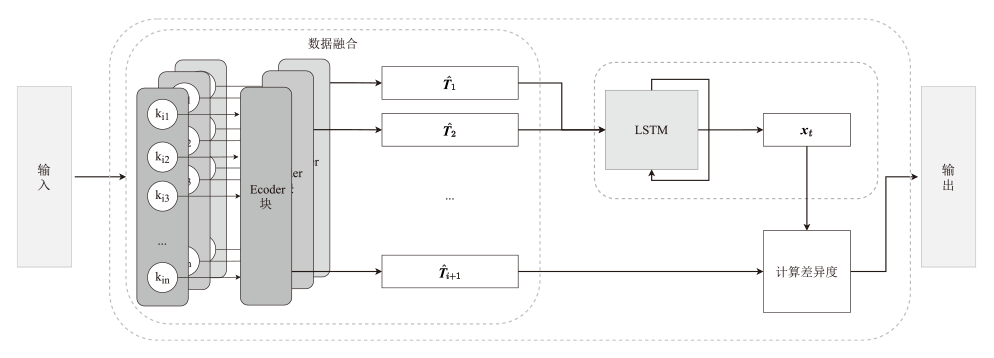
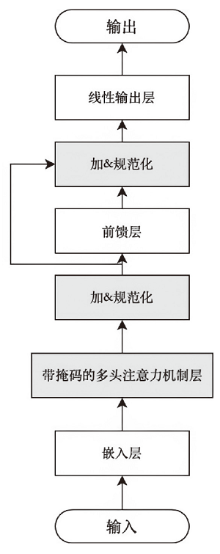
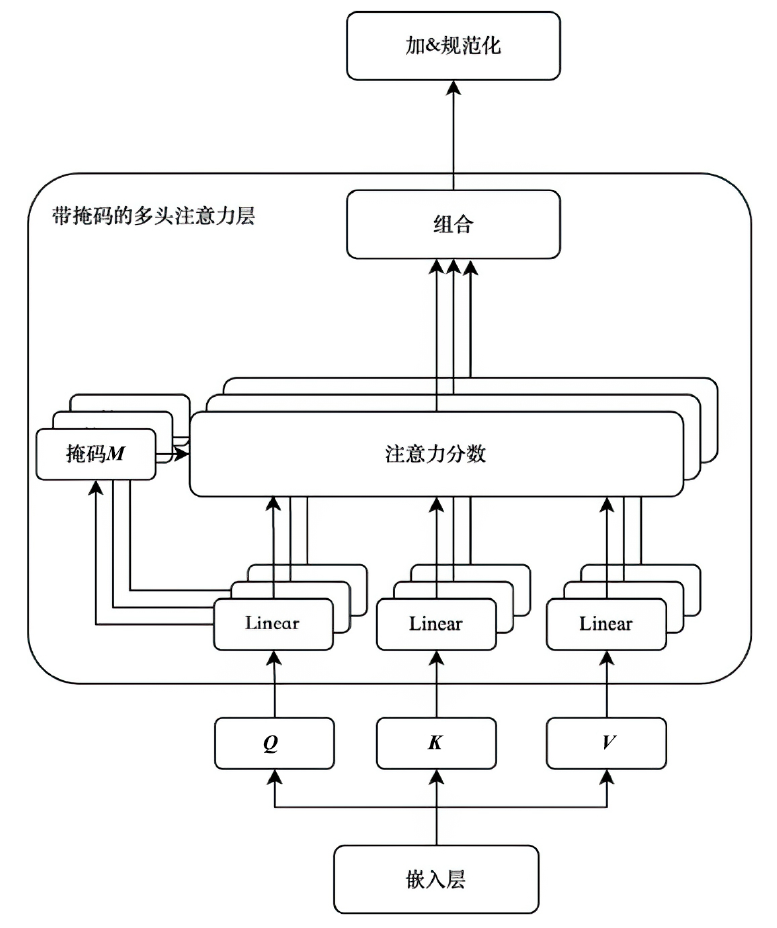
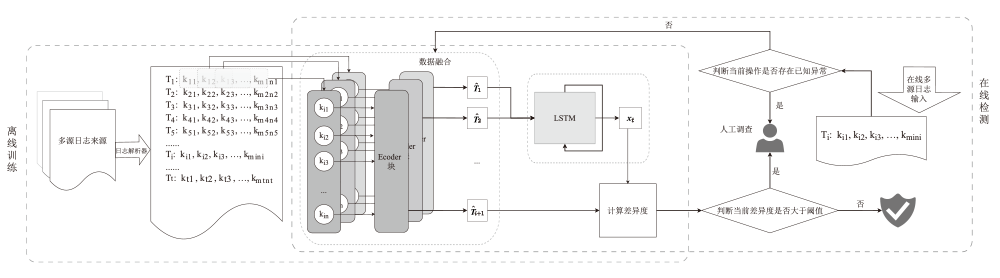
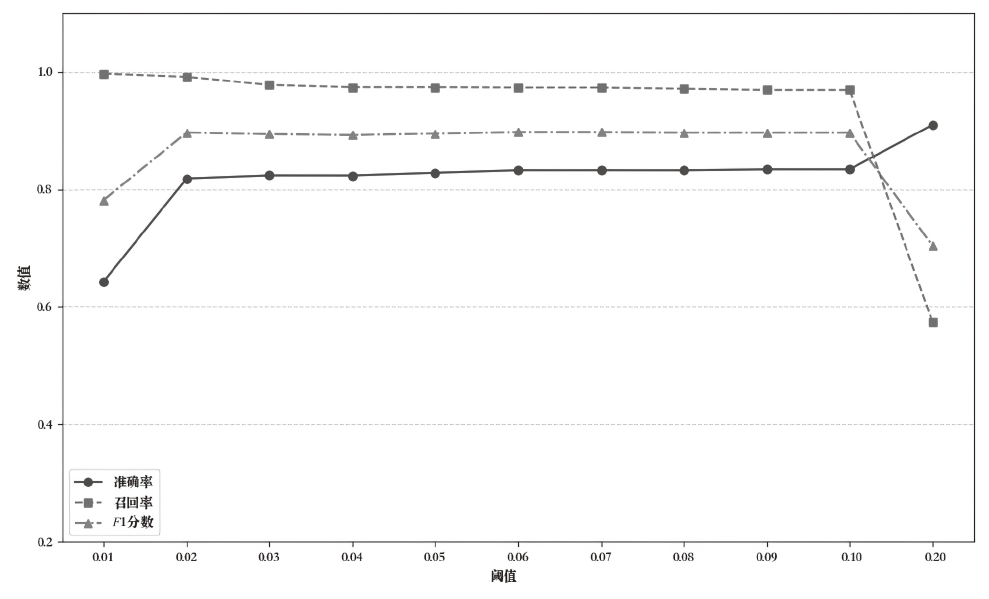
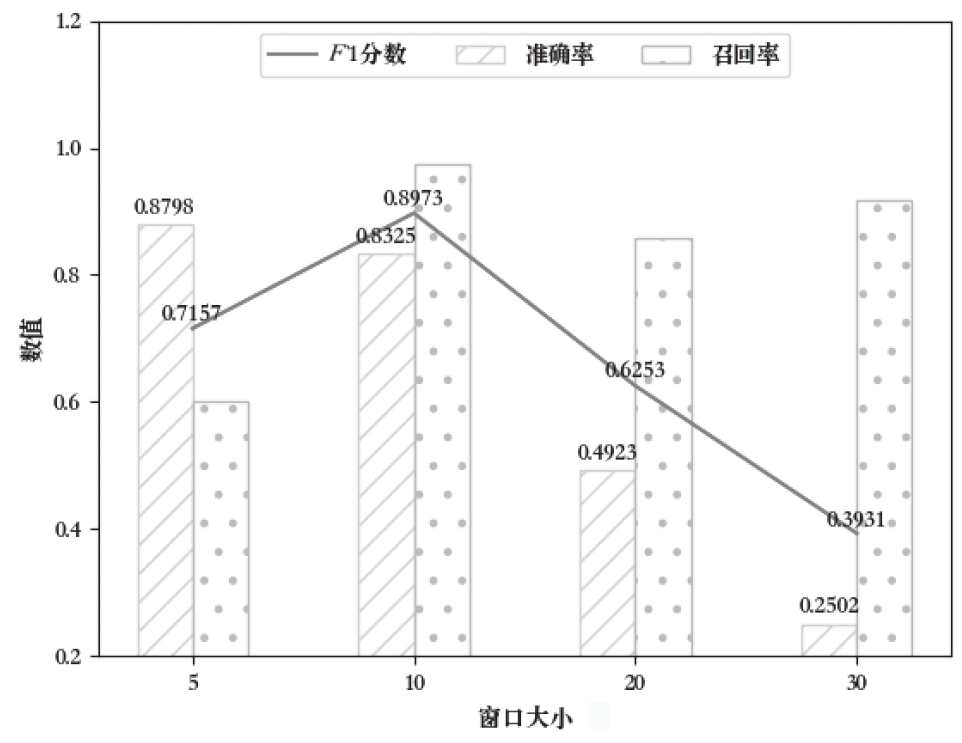
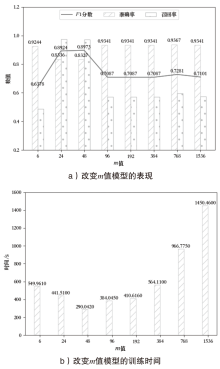
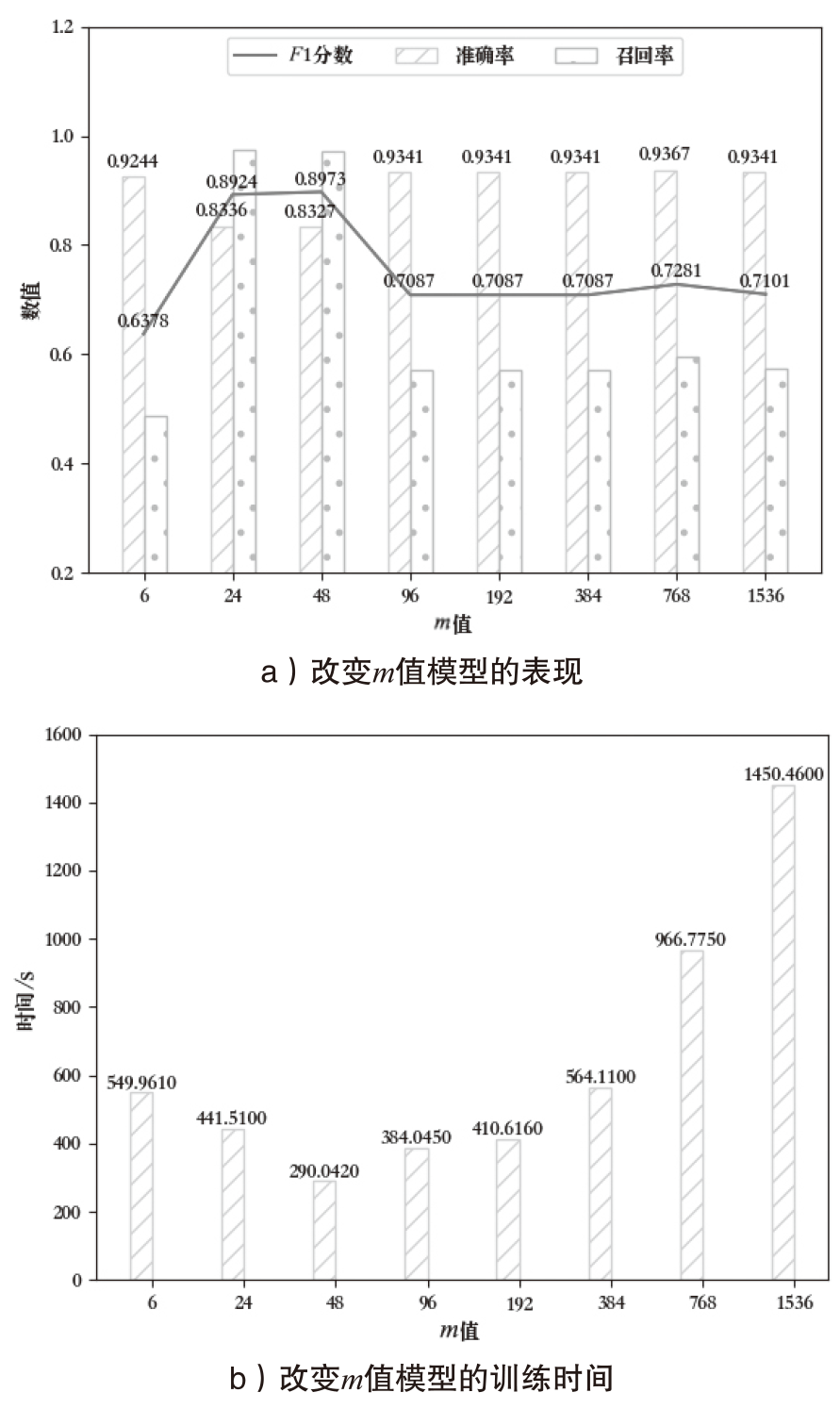
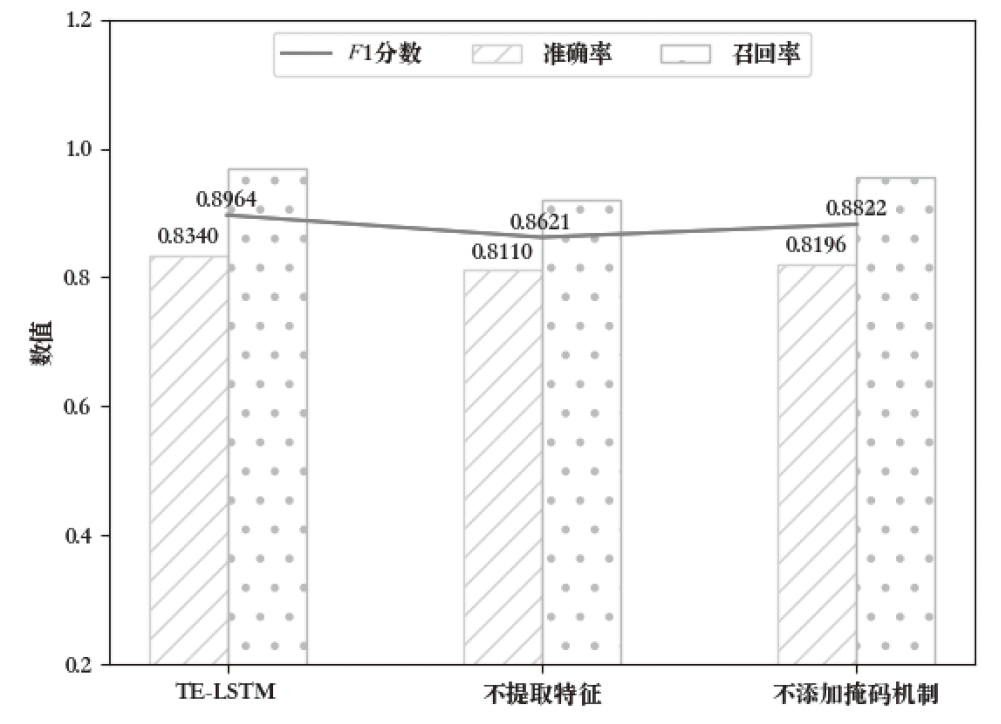
在智能系统安全领域,异常检测尤其是内部威胁的识别是一项极具挑战性的任务。现有方法通常依赖预定义规则或时序建模学习,但在面对未知威胁模式时存在局限,且难以充分挖掘日志数据的深层特征。针对这一问题,文章提出一种基于 Transformer 编码器(Trans-Encoder)与长短期记忆网络(LSTM)融合的内部威胁检测方法,旨在仅使用正常类数据训练实现日志中隐蔽异常的高效识别。首先,文章提出的方法通过改进 Transformer 编码器结构,增加屏蔽机制,从而增强了从多源日志数据中提取特征的能力。然后,应用 LSTM 进行时间序列建模,以捕捉提取特征之间的时间相关性,从而提高模型分析顺序依赖关系的能力。最后,计算预测值与对应特征值的差异度,并与阈值进行对比,以判断是否为异常操作。实验结果表明,该方法在内部威胁检测任务上的性能优于现有方法,其准确率提高1.5%,召回率提高4.8%,F1分数提高1.3%,在仅有10%训练数据的情况下,仍能保持稳定性能。此外,在训练阶段和测试阶段的计算效率都高于MTSAD,验证了其在智能系统安全中的应用潜力,为提升系统防护能力提供了一种高效可靠的解决方案。
中图分类号:
引用本文
李涛, 毕悦, 胡爱群. 面向智能系统的内部威胁多源日志分析与检测方法[J]. 信息网络安全, 2025, 25(4): 509-523.
LI Tao, BI Yue, HU Aiqun. Insider Threat Multi-Source Log Analysis and Detection Method for Intelligent Systems[J]. Netinfo Security, 2025, 25(4): 509-523.
表4
不同方法的性能比较
| 数据集 | 方法 | Deeplog | USAD | UCAD | MTSAD | TE-LSTM |
|---|---|---|---|---|---|---|
| HDFS | Precision | 0.8110 | 0.7945 | 0.7751 | 0.8191 | 0.8340 |
| Recall | 0.9199 | 0.8692 | 0.9181 | 0.9206 | 0.9689 | |
| F1-score | 0.8621 | 0.8503 | 0.8406 | 0.8833 | 0.8964 | |
| BGL | Precision | 0.8974 | 0.7697 | 0.9045 | 0.8843 | 0.9104 |
| Recall | 0.8278 | 0.9831 | 0.9583 | 0.9154 | 0.9778 | |
| F1-score | 0.8612 | 0.8186 | 0.9306 | 0.9097 | 0.9314 |
| [1] | LIANG Xiao, GUI Xiaolin, DAI Haojun, et al. Research on Cache Side Channel Attack Technology of Virtual Machines in Cloud Environment[J]. Chinese Journal of Computers, 2017, 40(2): 317-336. |
| [2] | Verizon. 2023 Data Breach Investigations Report[EB/OL]. [2025-01-20]. https://www.verizon.com/business/resources/T2b1/reports/2023-data-breach-investigations-report-dbir.pdf. |
| [3] | AKASH T, JAYAN A, GAUR N, et al. Identifying Insider Cyber Threats Using Behaviour Modelling and Analysis[C]// IEEE. 2023 OITS International Conference on Information Technology (OCIT). New York: IEEE, 2023: 35-40. |
| [4] | LE D C, ZINCIR-HEYWOOD A N. Evaluating Insider Threat Detection Workflow Using Supervised and Unsupervised Learning[C]// IEEE. 2018 IEEE Security and Privacy Workshops (SPW). New York: IEEE, 2018: 270-275. |
| [5] | MENG Fanzhi, LU Peng, LI Junhao, et al. GRU and Multi-Autoencoder Based Insider Threat Detection for Cyber Security[C]// IEEE. 2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC). New York: IEEE, 2021: 203-210. |
| [6] | TIAN Zhihong, SHI Wei, TAN Zhiyuan, et al. Deep Learning and Dempster-Shafer Theory Based Insider Threat Detection[J]. Mobile Networks and Applications, 2020: 1-10. |
| [7] | YUAN Shuhan, WU Xintao. Deep Learning for Insider Threat Detection: Review, Challenges and Opportunities[EB/OL]. (2021-05-01)[2025-01-20]. https://doi.org/10.1016/j.cose.2021.102221. |
| [8] | TUOR A, KAPLAN S, HUTCHINSON B, et al. Deep Learning for Unsupervised Insider Threat Detection in Structured Cybersecurity Data Streams[EB/OL]. (2017-10-02)[2025-01-20]. https://arxiv.org/abs/1710.00811. |
| [9] | ELDARDIRY H, BART E, LIU Juan, et al. Multi-Domain Information Fusion for Insider Threat Detection[C]// IEEE. 2013 IEEE Security and Privacy Workshops. New York: IEEE, 2013: 45-51. |
| [10] | ZHANG Lili, XIE Yuxiang, LUAN Xidao, et al. Multi-Source Heterogeneous Data Fusion[C]// IEEE. 2018 International Conference on Artificial Intelligence and Big Data (ICAIBD). New York: IEEE, 2018: 47-51. |
| [11] | LEE S, PARK S, HONG K. RDFNet: RGB-D Multi-Level Residual Feature Fusion for Indoor Semantic Segmentation[C]// IEEE. 2017 IEEE International Conference on Computer Vision (ICCV). New York: IEEE, 2017: 4990-4999. |
| [12] | BILINSKI P, PRISACARIU V. Dense Decoder Shortcut Connections for Single-Pass Semantic Segmentation[C]// IEEE. 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 6596-6605. |
| [13] | LE V H, ZHANG Hongyu. Log-Based Anomaly Detection without Log Parsing[C]// IEEE. 2021 36th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2021: 492-504. |
| [14] | LIU Shuo, XU Liwen, WANG Jinru, et al. LCR-GAN: Learning Crucial Representation for Anomaly Detection[C]// ACM. 2021 5th International Conference on Computer Science and Artificial Intelligence. New York: ACM, 2021: 162-167. |
| [15] | WU Shuguang, WANG Hongyan, WANG Yu, et al. Technology Analysis of Network Anomalous Behavior Detection Based on Machine Learning[C]// IEEE. Proceedings of the 2022 3rd International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering (ICBAIE). New York: IEEE, 2022: 730-737. |
| [16] | MAO Sheng, GUO Jiansheng, GU Taoyong, et al. Dis-AE-LSTM: Generative Adversarial Networks for Anomaly Detection of Time Series Data[C]// IEEE. 2020 International Conference on Artificial Intelligence and Computer Engineering (ICAICE). New York: IEEE, 2020: 330-336. |
| [17] | SAID E M, LE-KHAC N A, DEV S, et al. Network Anomaly Detection Using LSTM Based Autoencoder[C]// ACM. Proceedings of the 16th ACM Symposium on QoS and Security for Wireless and Mobile Networks. New York: ACM, 2020: 37-45. |
| [18] | XUE Yapeng. Research on Time Series Anomaly Detection Based on Graph Neural Network[C]// IEEE. 2023 IEEE International Conference on Electrical, Automation and Computer Engineering (ICEACE). New York: IEEE, 2023: 1670-1674. |
| [19] | VASWANI A, SHAZEER N, PARMAR N, et al. Attention is All you Need[J]. Neural Information Processing Systems, 2017, 30: 5998-6008. |
| [20] | YIN Chuanlong, ZHU Yuefei, FEI Jinlong, et al. A Deep Learning Approach for Intrusion Detection Using Recurrent Neural Networks[J]. IEEE Access, 2017, 5: 21954-21961. |
| [21] | XU Wei, HUANG Ling, FOX A, et al. Detecting Large-Scale System Problems by Mining Console Logs[C]// ACM. Proceedings of the ACM SIGOPS 22nd Symposium on Operating Systems Principles. New York: ACM, 2009: 117-132. |
| [22] | XU Wei, HUANG Ling, FOX A, et al. Online System Problem Detection by Mining Patterns of Console Logs[C]// IEEE. 2009 Ninth IEEE International Conference on Data Mining. New York: IEEE, 2009: 588-597. |
| [23] | LOU Jianguang, FU Qiang, YANG Shengqi, et al. Mining Invariants from Console Logs for System Problem Detection[J]. IEEE Transactions on Computers, 2010, 59(6): 759-774. |
| [24] | OLINER A, STEARLEY J. What Supercomputers Say: A Study of Five System Logs[C]// IEEE. The 37th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN’07). New York: IEEE, 2007: 575-584. |
| [25] | DU Min, LI Feifei, ZHENG Guineng, et al. DeepLog: Anomaly Detection and Diagnosis from System Logs through Deep Learning[C]// ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1285-1298. |
| [26] | AUDIBERT J, MICHIARDI P, GUYARD F, et al. USAD: UnSupervised Anomaly Detection on Multivariate Time Series[C]// ACM. Proceedings of the 26th ACM SIGKDD International Conference on Knowledge Discovery & Data Mining. New York: ACM, 2020: 3395-3404. |
| [27] | LI Sainan, YIN Qilei, LI Guoliang, et al. Unsupervised Contextual Anomaly Detection for Database Systems[C]// ACM. Proceedings of the 2022 International Conference on Management of Data. New York: ACM, 2022: 788-802. |
| [28] | SOWMYA K, RAMESH K. Enhancing Anomaly Detection in Multivariate Time Series with Stacked Transformer Encoders and Adaptive Positional Embeddings[EB/OL]. (2024-12-06)[2025-01-20]. https://doi.org/10.1007/s13369-024-09821-w. |
| [1] | 杨梦华, 易军凯, 朱贺军. 基于CNN-LSTM算法的内部威胁检测方法[J]. 信息网络安全, 2025, 25(2): 327-336. |
| [2] | 张光华, 闫风如, 张冬雯, 刘雪峰. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. |
| [3] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [4] | 黄娜, 何泾沙, 吴亚飚, 李建国. 基于LSTM回归模型的内部威胁检测方法[J]. 信息网络安全, 2020, 20(9): 17-21. |
| [5] | 王媛媛, 范潮钦, 苏玉海. 面向聊天记录的语义分析研究[J]. 信息网络安全, 2017, 17(9): 89-92. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||