信息网络安全 ›› 2024, Vol. 24 ›› Issue (10): 1515-1527.doi: 10.3969/j.issn.1671-1122.2024.10.005
环保大数据在区块链中的隐私计算
王南1,2, 袁也1,2, 杨浩然1,2, 文周之1,2, 苏明1,2,3,4( ), 刘晓光1,2
), 刘晓光1,2
- 1.南开大学计算机学院,天津 300350
2.南开大学网络空间安全学院,天津 300350
3.贵州大学公共大数据国家重点实验室,贵州550025
4.数据与智能系统安全教育部重点实验室,天津300350
-
收稿日期:2024-05-22出版日期:2024-10-10发布日期:2024-09-27 -
通讯作者:苏明,suming@nankai.edu.cn -
作者简介:王南(1999—),女,河北,硕士研究生,主要研究方向为医学图像篡改检测、全同态加密、区块链|袁也(1997—),男,河北,硕士研究生,主要研究方向为区块链、分布式系统|杨浩然(1999—),男,吉林,硕士研究生,主要研究方向为全同态加密、零知识证明|文周之(1999—),男,湖南,硕士研究生,主要研究方向为密码学、区块链技术、零知识证明|苏明(1978—),男,湖北,副研究员,博士,CCF会员,主要研究方向为序列复杂度及相关算法、数字水印、区块链|刘晓光(1974—),男,河北,教授,博士,CCF会员,主要研究方向为搜索引擎、存储系统、GPU计算 -
基金资助:国家自然科学基金(62272253);天津市重点研发计划(19YFZCSF00900);天津市重点研发计划(20JCZDJC00610);公共大数据国家重点实验室开放课题(PBD2022-12)
Privacy Computing in Environmental Big Data on Blockchain
WANG Nan1,2, YUAN Ye1,2, YANG Haoran1,2, WEN Zhouzhi1,2, SU Ming1,2,3,4( ), LIU Xiaoguang1,2
), LIU Xiaoguang1,2
- 1. College of Computer Science, Nankai University, Tianjin 300350, China
2. College of Cyber Science, Nankai University, Tianjin 300350, China
3. State Key Laboratory of Public Big Data, Guizhou 550025, China
4. Key Laboratory of Data and Intelligent System Security, Ministry of Education, Tianjin 300350, China
-
Received:2024-05-22Online:2024-10-10Published:2024-09-27
摘要:
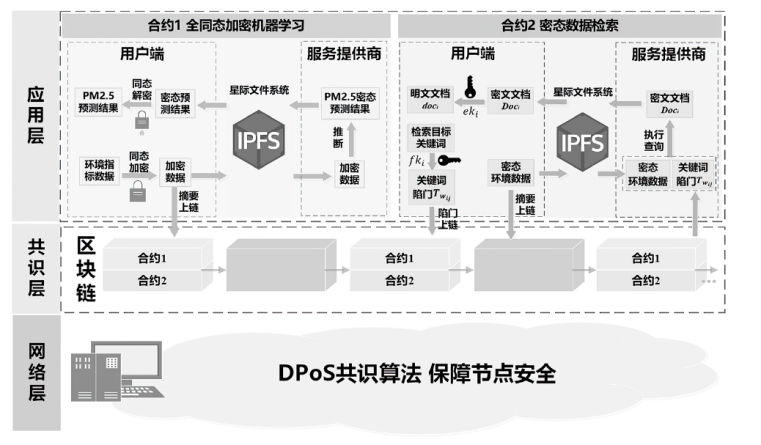
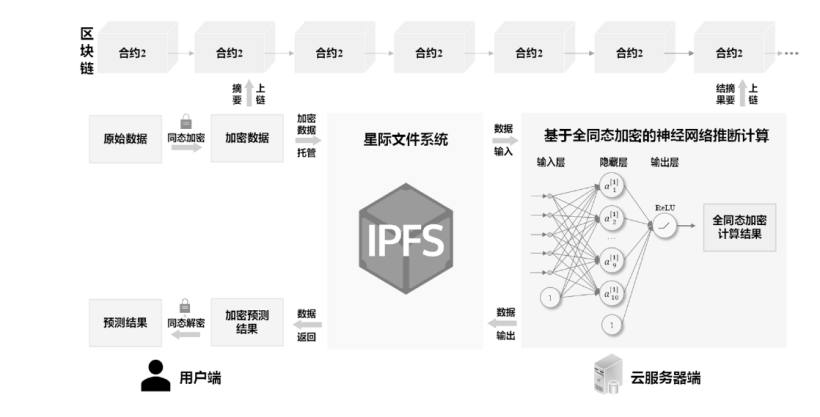
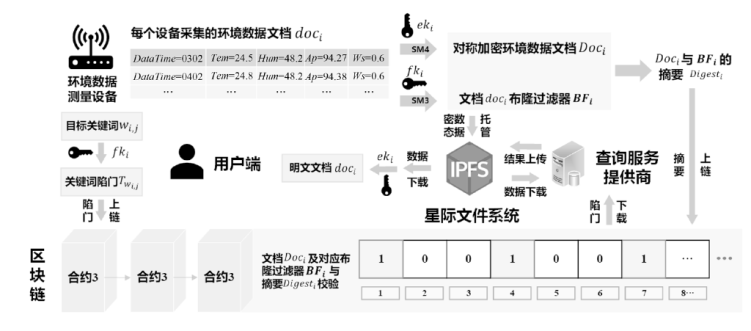
近年来,随着我国网络安全、医疗及环保相关政策的先后出台,环境数据的价值与日俱增。但我国对于环境数据的科学管理与安全共享仍处于起步阶段,具有隐私保护需求的环境数据数量急剧增加,但在数据共享上却面临数据孤岛化、泄露风险高等诸多难题。针对环境数据共享场景,为从根本上满足用户数据云存储和云计算的隐私保护需求,文章将区块链和隐私计算相结合,采用国密算法构建了一个基于全同态加密和可搜索加密技术的数据密态管理系统。依托区块链部署和云服务存储、隐私计算支持,系统可实现全同态加密机器学习和可搜索加密两种功能。文章基于全同态加密技术实现了神经网络预测模型,并完成了密态数据的云计算;同时,文章采用对称可搜索加密方案,支持数据在全程密态下的远程托管,能够实现密文检索并保护查询关键词的隐私。在保护隐私安全前提下,该方案有效打通了各方数据流通通道,保证数据可用不可见。
中图分类号:
引用本文
王南, 袁也, 杨浩然, 文周之, 苏明, 刘晓光. 环保大数据在区块链中的隐私计算[J]. 信息网络安全, 2024, 24(10): 1515-1527.
WANG Nan, YUAN Ye, YANG Haoran, WEN Zhouzhi, SU Ming, LIU Xiaoguang. Privacy Computing in Environmental Big Data on Blockchain[J]. Netinfo Security, 2024, 24(10): 1515-1527.
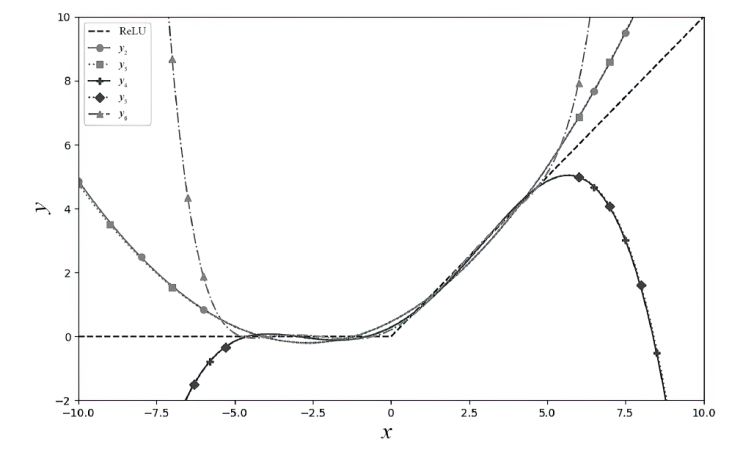
表3
多项式函数拟合ReLU函数
| 多项式次数 | 多项式函数表达式 |
|---|---|
| 2 | y2=0.09401488x2+0.49922105x+0.46555915 |
| 3 | y3=0.000118167887x3+0.0940148772x2+0.497444982x+0.46555915 |
| 4 | y4=-0.00324432116x4+0.000118167487x3+0.163675005x2+0.497444995x+0.291060996 |
| 5 | y5=0.0000042x5-0.003244x4+0.00000122x3+0.163675005x2+0.498072743x+0.291060996 |
| 6 | y6=0.0002379x6+0.0000042x5-0.01137x4+0.00000122x3+0.2315x2+0.4981x+0.210103044 |
| [1] | YANG Jin. Research on Problems and Solutions in the Monitoring and Management of Environmental Impact Assessment Status[J]. Environment and Development, 2020, 32(5): 12-14. |
| 杨晋. 环境影响评价现状监测管理中存在的问题及解决对策研究[J]. 环境与发展, 2020, 32(5): 12-14. | |
| [2] | RAMACHANDRAN M, CHANG V. Towards Performance Evaluation of Cloud Service Providers for Cloud Data Security[J]. International Journal of Information Management, 2016, 36(4): 618-625. |
| [3] | DONG Qiuxiang, GUAN Zhi, CHEN Zhong. A Survey on Computational Cryptography Techniques for Encrypted Data[J]. Computer Applications Research, 2016, 33(9): 9-12. |
| 董秋香, 关志, 陈钟. 加密数据上的计算密码学技术研究综述[J]. 计算机应用研究, 2016, 33(9): 9-12. | |
| [4] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[J]. Iacr Cryptology Eprint Archive, 2012: 1-19. |
| [5] | GOH E J. Secure Indexes[D]. Stanford: Stanford University, 2003. |
| [6] | SCHUH F, LARIMER D. Bitshares 2.0: General Overview[EB/OL]. [2024-04-23]. https://pdfs.semanticscholar.org/c5c6/eefc414d32637890dbe40a1440e46f68e10f.pdf. |
| [7] | RIVEST R L, ADLEMAN L, DERTOUZOS M L. On Data Banks and Privacy Homomorphisms[J]. Foundations of Secure Computation, 1978, 4(11): 169-180. |
| [8] | RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126. |
| [9] | ELGAMAL T. A Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms[J]. IEEE Transactions on Information Theory, 1985, 31(4): 469-472. |
| [10] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// IACR. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 1999: 223-238. |
| [11] | BONEH D, GOH E J, NISSIM K. Evaluating 2-DNF Formulas on Ciphertexts[C]// IACR. Theory of Cryptography Conference. Heidelberg: Springer, 2005: 325-341. |
| [12] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. (Leveled)Fully Homomorphic Encryption without Bootstrapping[J]. ACM Transactions on Computation Theory (TOCT), 2014, 6(3): 1-36. |
| [13] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate Numbers[C]// IACR. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2017: 409-437. |
| [14] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. Proceeding of IEEE Symposium on Security and Privacy(S&P 2000). New York: IEEE, 2000: 44-55. |
| [15] | BLOOM B H. Spacetime Tradeoffs in Hash Coding with Allowable Errors[J]. Communications of the ACM, 1970, 13(7): 422-426. |
| [16] | XU Peng, SUSILO W, WANG Wei, et al. ROSE: Robust Searchable Encryption with Forward and Backward Security[J]. IEEE Transactions on Information Forensics and Security, 2022, 17: 1115-1130. |
| [17] | BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// IACR. EUROCRYPT 2004:International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2004: 506-522. |
| [18] | ABDALLA M, BELLARE M, CATALANO D, et al. Searchable Encryption Revisited: Consistency Properties, Relation to Anonymous IBE, and Extensions[J]. Journal of cryptology, 2008, 21: 350-391. |
| [19] | TONG Qiuyun, MIAO Yinbin, WENG Jian, et al. Verifiable Fuzzy Multi-Keyword Search over Encrypted Data with Adaptive Security[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(5): 5386-5399. |
| [20] | TONG Qiuyun, LI Xinghua, MIAO Yinbin, et al. Privacy-Preserving Boolean Range Query with Temporal Access Control in Mobile Computing[J]. IEEE Transactions on Knowledge and Data Engineering, 2022, 35(5): 5159-5172. |
| [21] | HUANG Qinlong, YAN Guanyu, WEI Qinglin. Attribute-Based Expressive and Ranked Keyword Search Over Encrypted Documents in Cloud Computing[J]. IEEE Transactions on Services Computing, 2023, 16(2): 957-968. |
| [22] | SALEH F. Blockchain without Waste: Proof-of-Stake[J]. The Review of Financial Studies, 2021, 34(3): 1156-1190. |
| [23] | LAMPORT L. The Part-Time Parliament[J]. ACM Transactions on Computer Systems, 1998, 16(2): 133-169. |
| [24] | GM/T 0004-2012 SM3 Cryptographic Hash Algorithm[S]. Beijing: National Cryptography Administration, 2012. |
| GM/T 0004-2012 SM3密码杂凑算法[S]. 北京: 国家密码管理局, 2012. | |
| [25] | GB/T 32907-2016 Information Security Technology: SM4 Block Cipher Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 32907-2016 信息安全技术 SM4分组密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [26] | CHEN Zhigang, WANG Jian, SONG Xinxia. Research on Fully Homomorphic Encryption[J]. Computer Applications Research, 2014, 31(6): 1624-1631. |
| 陈智罡, 王箭, 宋新霞. 全同态加密研究[J]. 计算机应用研究, 2014, 31(6): 1624-1631. | |
| [27] | XU Shicong. Research on Privacy-Preserving Convolutional Neural Network Forward Propagation Method[D]. Xi’an: Xidian University, 2019. |
| 许世聪. 隐私保护卷积神经网络前向传播方法研究[D]. 西安: 西安电子科技大学, 2019. | |
| [28] | Microsoft. Microsoft SEAL[EB/OL]. (2019-12-30)[2023-05-01]. https://github.com/microsoft/SEAL. |
| [29] | GILAD-BACHRACH R, DOWLIN N, LAINE K, et al. Cryptonets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[C]// IMLS. International Conference on Machine Learning. New York: PMLR, 2016: 201-210. |
| [30] | CHEN Song. Beijing PM2.5[EB/OL]. (2017-01-18)[2024-05-06]. https://archive.ics.uci.edu/dataset/381/beijing+pm2+5+data. |
| [1] | 温金明, 刘庆, 陈洁, 吴永东. 基于错误学习的全同态加密技术研究现状与挑战[J]. 信息网络安全, 2024, 24(9): 1328-1351. |
| [2] | 余礼苏, 李彪, 姚元志, 温家进, 黎子鹏, 王振. 区块链辅助无人机移动边缘计算系统的性能优化[J]. 信息网络安全, 2024, 24(9): 1432-1443. |
| [3] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [4] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [5] | 问闻, 刘钦菊, 邝琳, 任雪静. 隐私保护体系下网络威胁情报共享的研究现状和方案设计[J]. 信息网络安全, 2024, 24(7): 1129-1137. |
| [6] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [7] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [8] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [9] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [10] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| [11] | 戚晗, 王敬童, 拱长青. 基于随机量子层的变分量子卷积神经网络鲁棒性研究[J]. 信息网络安全, 2024, 24(3): 363-373. |
| [12] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [13] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [14] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [15] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||