信息网络安全 ›› 2024, Vol. 24 ›› Issue (10): 1493-1505.doi: 10.3969/j.issn.1671-1122.2024.10.003
基于动态执行日志和反向分析的漏洞成因分析技术
- 1.中国科学院信息工程研究所,北京 100085
2.北京小米移动软件有限公司,北京 100089
-
收稿日期:2024-05-16出版日期:2024-10-10发布日期:2024-09-27 -
通讯作者:梁瑞刚,liangruigang@iie.ac.cn -
作者简介:沈钦涛(1993—),男,河南,博士研究生,主要研究方向为软件安全分析|梁瑞刚(1992—),男,甘肃,高级工程师,博士,CCF会员,主要研究方向为软件与系统安全、AI安全|王宝林(1985—),男,四川,工程师,主要研究方向为系统漏洞挖掘与封堵|张倞诚(1995—),男,辽宁,主要研究方向为系统安全加固、隐私保护|陈恺(1982—),男,江苏,研究员,博士,CCF会员,主要研究方向为软件与系统安全、AI安全 -
基金资助:国家自然科学基金(62302497);国家自然科学基金(62302498);国家自然科学基金(92270204)
Vulnerability Causation Analysis Based on Dynamic Execution Logging and Reverse Analysis
SHEN Qintao1, LIANG Ruigang1( ), WANG Baolin2, ZHANG Jingcheng2, CHEN Kai1
), WANG Baolin2, ZHANG Jingcheng2, CHEN Kai1
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
2. Beijing Xiaomi Mobile Software Co.,Ltd., Beijing 100089, China
-
Received:2024-05-16Online:2024-10-10Published:2024-09-27
摘要:
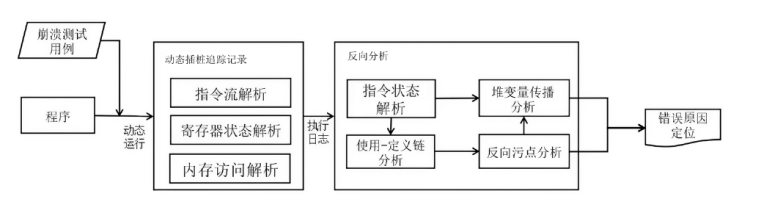
软件漏洞给软件安全带来了巨大的威胁,全球每年因软件漏洞导致的安全事件层出不穷。然而,在实际的开发过程中,因开发人员的安全意识不够、代码和业务逻辑越来越复杂等原因,软件代码中难以避免地存在着安全漏洞。文章针对现有方法面临错误代码定位不准确、分析效率不高等难题,突破指令运行时信息获取和反向分析、错误代码准确定位等挑战,提出一种基于追踪日志和反向执行的程序错误原因定位方法,能够跟踪程序的代码执行流,记录指令在运行状态下的寄存器状态信息以及存储访问状态信息,分析引发执行错误的指针相关联的指针值生成、使用、计算的指令集合,实现高效、准确的漏洞成因分析和定位。
中图分类号:
引用本文
沈钦涛, 梁瑞刚, 王宝林, 张倞诚, 陈恺. 基于动态执行日志和反向分析的漏洞成因分析技术[J]. 信息网络安全, 2024, 24(10): 1493-1505.
SHEN Qintao, LIANG Ruigang, WANG Baolin, ZHANG Jingcheng, CHEN Kai. Vulnerability Causation Analysis Based on Dynamic Execution Logging and Reverse Analysis[J]. Netinfo Security, 2024, 24(10): 1493-1505.
表1
漏洞信息列表
| CVE-ID | 程序名称 | 版本 | 大小 | 类型 |
|---|---|---|---|---|
| CVE-2017-12955 | Exiv2 | 7e4fad6 | 9.97 MB | 图片处理程序 |
| CVE-2017-14860 | Exiv2 | f25c9a6 | 9.94 MB | 图片处理程序 |
| CVE-2020-18831 | Exiv2 | c23b305 | 9.40 MB | 图片处理程序 |
| CVE-2019-13108 | Exiv2 | 0.27.1 | 10.69 MB | 图片处理程序 |
| CVE-2020-23879 | pdf2json | cfa8103 | 2.20 MB | pdf 格式转换 |
| CVE-2023-36273 | dwg2dxf | 77a8562 | 35.00 MB | dwg 文件解析 |
| CVE-2022-33033 | dwg2dxf | 0.12.4.4608 | 32.00 MB | dwg 文件解析 |
| CVE-2019-9771 | dwg2dxf | 0.7 | 7.70 MB | dwg 文件解析 |
| CVE-2022-35164 | dwgrewrite | 0.12.4.4608 | 25.00 MB | dwg 文件解析 |
| CVE-2019-19887 | ffjpeg | 0f5c850 | 82 KB | jpeg 编码解析 |
| CVE-2020-23705 | ffjpeg | c31ce5d | 81 KB | jpeg 编码解析 |
| CVE-2021-34122 | ffjpeg | 4ab404e | 78 KB | jpeg 编码解析 |
| CVE-2022-37769 | jpeg(libjpeg) | 250c886 | 6.10 MB | jpeg 协议完整实现 |
| CVE-2021-39515 | jpeg(libjpeg) | e52406 | 6.10 MB | jpeg 协议完整实现 |
| CVE-2023-4683 | MP4Box | 5360a17 | 859 KB | 模块化多媒体框架 |
表2
错误漏洞的成因分析
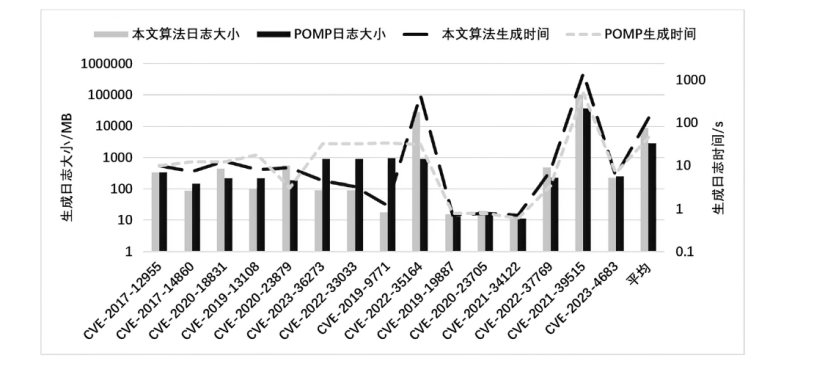
| CVE-ID | 距离崩溃点的 指令数/个 | 崩溃原因 | 报告数 /行 | 是否 正确 | 分析 时间/s |
|---|---|---|---|---|---|
| CVE-2017-12955 | 1425224 | 读取不合法的地址 | 4 | √ | 151.3 |
| CVE-2017-14860 | 1545 | 读取不合法的地址 | 3 | √ | 64.4 |
| CVE-2020-18831 | 8 | 读取不合法的地址 | 1 | √ | 0.1 |
| CVE-2019-13108 | 603 | 分配超大内存 | 1 | √ | 3.0 |
| CVE-2020-23879 | 128026 | 使用空指针 | 3 | √ | 11.9 |
| CVE-2023-36273 | 16 | 使用空指针 | 2 | √ | 0.1 |
| CVE-2022-33033 | 726 | 释放错误 | 1 | √ | 0.1 |
| CVE-2019-9771 | 5879 | 读取不合法的地址 | 2 | √ | 5.4 |
| CVE-2022-35164 | 801 | 释放后使用 | 1 | √ | 0.1 |
| CVE-2019-19887 | 7 | 使用空指针 | 2 | √ | 0.1 |
| CVE-2020-23705 | 39 | 使用空指针 | 2 | √ | 19.5 |
| CVE-2021-34122 | 7 | 使用空指针 | 2 | √ | 0.1 |
| CVE-2022-37769 | 487 | 读取不合法的地址 | 3 | √ | 0.1 |
| CVE-2021-39515 | 259 | 使用空指针 | 2 | √ | 0.1 |
| CVE-2023-4683 | 23 | 使用空指针 | 2 | √ | 0.1 |
| [1] | CNVD. National Information Security Vulnerability Sharing Platform[EB/OL]. (2024-01-09)[2024-02-16]. https://www.cnvd.org.cn/. |
| CNVD. 国家信息安全漏洞共享平台[EB/OL]. (2024-01-09)[2024-02-16]. https://www.cnvd.org.cn/. | |
| [2] | LU Kangjie, PAKKI A, WU Qiushi. Detecting Missing-Check Bugs via Semantic and Context-Aware Criticalness and Constraints Inferences[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley: USENIX, 2019: 1769-1786. |
| [3] | ZOU Daming, LIANG Jingjing, XIONG Yingfei, et al. An Empirical Study of Fault Localization Families and Their Combinations[J]. IEEE Transactions on Software Engineering, 2019, 47(2): 332-347. |
| [4] | BLAZYTKO T, SCHLOGEL M, ASCHERMANN C, et al. AURORA: Statistical Crash Analysis for Automated Root Cause Explanation[C]// USENIX. 29th USENIX Security Symposium (USENIX Security 20). Berkeley: USENIX, 2020: 235-252. |
| [5] | JIANG Zhiyuan, JIANG Xiyue, HAZIMEH A, et al. Igor: Crash Deduplication through Root-Cause Clustering[C]// ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 3318-3336. |
| [6] | ABREU R, ZOETEWEIJ P, VAN GEMUND A J. On the Accuracy of Spectrum-Based Fault Localization[C]// IEEE. Testing: Academic and Industrial Conference Practice and Research Techniques-MUTATION (TAICPART-MUTATION 2007). New York: IEEE, 2007: 89-98. |
| [7] | WONG E, WEI Tingting, QI Yu, et al. A Crosstab-Based Statistical Method for Effective Fault Localization[C]// IEEE. 2008 1st International Conference on Software Testing, Verification, and Validation. New York: IEEE, 2008: 42-51. |
| [8] | MASRI W. Fault Localization Based on Information Flow Coverage[J]. Software Testing, Verification and Reliability, 2010, 20(2): 121-147. |
| [9] | HONG S, LEE B, KWAK T, et al. Mutation-Based Fault Localization for Real-World Multilingual Programs[C]// IEEE. 30th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2015: 464-475. |
| [10] | LI Xia, ZHANG Lingming. Transforming Programs and Tests in Tandem for Fault Localization[J]. Proceedings of the ACM on Programming Languages, 2017, 1: 1-30. |
| [11] | CUI Weidong, PEINADO M, CHA S K, et al. Retracer: Triaging Crashes by Reverse Execution from Partial Memory Dumps[C]// IEEE. Proceedings of the 38th International Conference on Software Engineering(ICSE). New York: IEEE, 2016: 820-831. |
| [12] | OHMANN P, LIBLIT B. Lightweight Control-Flow Instrumentation and Postmortem Analysis in Support of Debugging[C]// IEEE. 28th IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2017: 865-904. |
| [13] | XU Jun, MU Dongliang, XING Xinyu, et al. Postmortem Program Analysis with Hardware-Enhanced Post-Crash Artifacts[C]// USENIX. 26th USENIX Security Symposium (USENIX Security 17). Berkeley: USENIX, 2017: 17-32. |
| [14] | MU Dongliang, DU Yunlan, XU Jianhao, et al. Pomp++: Facilitating Postmortem Program Diagnosis with Value-Set Analysis[J]. IEEE Transactions on Software Engineering, 2019, 47(9): 1929-1942. |
| [15] | GE Xinyang, NIU Ben, CUI Weidong. Reverse Debugging of Kernel Failures in Deployed Systems[C]// USENIX. 2020 USENIX Annual Technical Conference (USENIX ATC 20). Berkeley: USENIX, 2020: 281-292. |
| [16] | ZUO Guofei, MA Jiacheng, QUINN A, et al. Execution Reconstruction: Harnessing Failure Reoccurrences for Failure Reproduction[C]// ACM. Proceedings of the 42nd ACM SIGPLAN International Conference on Programming Language Design and Implementation. New York: ACM, 2021: 1155-1170. |
| [17] | YAGEMANN C, PRUETT M, CHUNG S P, et al. ARCUS: Symbolic Root Cause Analysis of Exploits in Production Systems[C]// USENIX. 30th USENIX Security Symposium (USENIX Security 21). Berkeley: USENIX, 2021: 1989-2006. |
| [18] | BELL J, SARDA N, KAISER G. Chronicler: Lightweight Recording to Reproduce Field Failures[C]// IEEE. 35th International Conference on Software Engineering (ICSE). New York: IEEE, 2013: 362-371. |
| [19] | HE Liang, HU Hong, SU Purui, et al. FreeWill: Automatically Diagnosing Use-After-Free Bugs via Reference Miscounting Detection on Binaries[C]// USENIX. 31st USENIX Security Symposium (USENIX Security 22). Berkeley: USENIX, 2022: 2497-2512. |
| [20] | CUI Weidong, GE Xinyang, KASIKCI B, et al. REPT: Reverse Debugging of Failures in Deployed Software[C]// USENIX. 13th USENIX Symposium on Operating Systems Design and Implementation (OSDI 18). Berkeley: USENIX, 2018: 17-32. |
| [1] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [2] | 李鹏超, 张全涛, 胡源. 基于双注意力机制图神经网络的智能合约漏洞检测方法[J]. 信息网络安全, 2024, 24(11): 1624-1631. |
| [3] | 陈宝刚, 张毅, 晏松. 民航空管信息系统用户多因子持续身份可信认证方法研究[J]. 信息网络安全, 2024, 24(11): 1632-1642. |
| [4] | 兰浩良, 王群, 徐杰, 薛益时, 张勃. 基于区块链的联邦学习研究综述[J]. 信息网络安全, 2024, 24(11): 1643-1654. |
| [5] | 张志强, 暴亚东. 融合RF和CNN的异常流量检测算法[J]. 信息网络安全, 2024, 24(11): 1655-1664. |
| [6] | 夏玲玲, 马卓, 郭向民, 倪雪莉. 基于改进加权LeaderRank的目标人员重要度排序算法[J]. 信息网络安全, 2024, 24(11): 1665-1674. |
| [7] | 胡文涛, 徐靖凯, 丁伟杰. 基于溯因学习的无监督网络流量异常检测[J]. 信息网络安全, 2024, 24(11): 1675-1684. |
| [8] | 马卓, 陈东子, 何佳涵, 王群. 基于多因素解纠缠的用户—兴趣点联合预测[J]. 信息网络安全, 2024, 24(11): 1685-1695. |
| [9] | 周胜利, 徐睿, 陈庭贵, 蒋可怡. 基于事理图谱的受骗网络行为风险演进研究[J]. 信息网络安全, 2024, 24(11): 1696-1709. |
| [10] | 马如坡, 王群, 尹强, 高谷刚. Modbus TCP协议安全风险分析及对策研究[J]. 信息网络安全, 2024, 24(11): 1710-1720. |
| [11] | 裴炳森, 李欣, 樊志杰, 蒋章涛. 视频监控数据跨域安全共享传输控制系统设计与实现[J]. 信息网络安全, 2024, 24(11): 1721-1730. |
| [12] | 顾海艳, 柳琪, 马卓, 朱涛, 钱汉伟. 基于可用性的数据噪声添加方法研究[J]. 信息网络安全, 2024, 24(11): 1731-1738. |
| [13] | 张鹏, 罗文华. 基于布隆过滤器查找树的日志数据区块链溯源机制[J]. 信息网络安全, 2024, 24(11): 1739-1748. |
| [14] | 栾润生, 蒋平, 孙银霞, 张沁芝. 电子数据取证技术研究进展和趋势分析[J]. 信息网络安全, 2024, 24(11): 1749-1762. |
| [15] | 高光亮, 梁广俊, 洪磊, 高谷刚, 王群. 融合实例和标记相关性增强消歧的偏多标记学习算法[J]. 信息网络安全, 2024, 24(11): 1763-1772. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||